Category:I804 Linux Windows administration: Difference between revisions
| (49 intermediate revisions by the same user not shown) | |||
| Line 8: | Line 8: | ||
sharing document: https://onedrive.live.com/?authkey=%21AFAxtpKI_r5cX6c&id=93040B43356F2D88%21116648&cid=93040B43356F2D88 | sharing document: https://onedrive.live.com/?authkey=%21AFAxtpKI_r5cX6c&id=93040B43356F2D88%21116648&cid=93040B43356F2D88 | ||
Instructor: Belgin TAŞTAN | |||
Exam Dates: | |||
26 May 2017 Lab Exam %50 Mendatory | |||
29 May 2017 Lab Exam %50 People who failed previous examination | |||
Windows: | Windows: | ||
| Line 82: | Line 91: | ||
-Disk Management ( Dynamic Disk, Master Boot Record, GUID Partition Table, Spanned Volume, Stripped Volume, Mirrored Volume, RAID-5 Volume, Extending a Volume, Shrinking a Volume, Adding a Mirror to a Volume ) | -Disk Management ( Dynamic Disk, Master Boot Record, GUID Partition Table, Spanned Volume, Stripped Volume, Mirrored Volume, RAID-5 Volume, Extending a Volume, Shrinking a Volume, Adding a Mirror to a Volume ) | ||
1. Assignment; Windows Server 2008 R2 Disk Configuration and Hyper-V Configuration. | 1. Assignment; Windows Server 2008 R2 Disk Configuration and Hyper-V Configuration. | ||
Implement Disk and Hyper-V Configurations with explanations and screen captures. | Implement Disk and Hyper-V Configurations with explanations and screen captures. | ||
Disk Configuration ( Dynamic Disk, Master Boot Record, GUID Partition Table, Spanned Volume, Stripped Volume, Mirrored Volume, RAID-5 Volume, Extending a Volume, Shrinking a Volume, Adding a Mirror to a | Disk Configuration ( Dynamic Disk, Master Boot Record, GUID Partition Table, Spanned Volume, Stripped Volume, Mirrored Volume, RAID-5 Volume, Extending a Volume, Shrinking a Volume, Adding a Mirror to a volume ). | ||
Hyper-V Configuration ( Cluster Shared Volumes, Live Migration ) | Hyper-V Configuration ( Cluster Shared Volumes, Live Migration ) | ||
Email to belgin.tastan@itcollege.ee | Email to belgin.tastan@itcollege.ee | ||
| Line 112: | Line 121: | ||
-Files or Volumes | -Files or Volumes | ||
* Backup resources | |||
- Shared folders | |||
- Removable media | |||
- Internal hard disk | |||
- External hard disk | |||
* Fail Over Cluster | * Fail Over Cluster | ||
| Line 134: | Line 155: | ||
- RAID 6 | - RAID 6 | ||
- RAID 00 | |||
- RAID 50 | |||
- RAID 60 | |||
| Line 141: | Line 167: | ||
-Adding 1 more disk and take Full Backup in to this location. | -Adding 1 more disk and take Full Backup in to this location. | ||
Exercises | |||
- Local Admin Password changing with PowerShell.exe | |||
Instructions | |||
From a computer : | |||
1.open Powershell as administrator | |||
2.make sure that executionpolicy allow script execution | |||
3.Type : resetlocalAdminpassword.ps1 -newpassword <password> | |||
where <password> is the new value of your password | |||
https://gallery.technet.microsoft.com/Reset-Local-Administrator-e3023c3a | |||
- Firewall should disabled in Group Policy Object Editor | |||
- Windows Defender should disabled in Group Policy Object Editor | |||
- Windows Update should disabled in Group Policy Object Editor | |||
- Smart Screen should disabled in Group Policy Object Editor | |||
- User Account Control Settings should force to low level | |||
- IPV6 should force to Up and Running in Group Policy Object Editor | |||
- Audit Logs should force to disabled in Group Policy Object Editor | |||
- C$ Restriction. User Configuration > Administrative Templates > Windows Components > Windows Explorer - "Hide these specified drives in My Computer" and "Prevent access to drives from My Computer". Both are set to "Enabled" with the option "Restrict C drive only". | |||
* DNS Configuration | * DNS Configuration | ||
- Understanding and Managing DNS | |||
- Introduction to the DNS | |||
- DNS Components; | |||
The name space, | |||
The servers, | |||
The resolvers. | |||
- DNS Structure and Hierarchy | |||
- The DNS in Context | |||
NOTE: Everyone will bring an example of Amplification attacks to talk about. | |||
Resource Records and Records Types | |||
Forward and Reverse Lookup Zone | |||
DNS Replication | |||
* Active Directory | * Active Directory | ||
- AD DS Physical Components | |||
Domain Controllers, | |||
Global Catalog Servers, | |||
Data Store, | |||
Replication, | |||
Sites. | |||
- AD DS Logical Components | |||
AD DS Schema, | |||
The Basics, | |||
Trusts, | |||
AD DS Objects. | |||
- Protocol | |||
- What is Authentication? | |||
- What is Authorization? | |||
- Why Deploy AD DS? | |||
- Centralized Network Management | |||
- Requirements for Installing AD DS | |||
- Overview of AD DS and DNS | |||
- Overview of AD DS Components | |||
Installation and Management AD | |||
Observe the installation of AD DS | |||
Active Directory Users and Computers | |||
Active Directory Administrative Center | |||
Active Directory Sites and Services | |||
- Creating new user accounts | |||
- To join computers running Windows Server 2008 R2 | |||
* Setting up GPO-s | * Setting up GPO-s | ||
* | |||
* | - GPO Components | ||
* | |||
- GPO Work Steps | |||
- Modifying Group Policy Processing | |||
- WMI Filter | |||
- Loopback Processing | |||
- Backup and Restore GPO | |||
- Fine-grained passwords | |||
* Installing and Configuring Active Directory on Server 2012 R2, Server 2016. | |||
- Creating Organizational Units and users. | |||
2. Assignment; Grading criteria for each assignment will be provided with the instructions | |||
for the assignment. If the assignment is not delivered by the deadline, the assignment is | |||
considered to be failed. Plagiarism is not allowed. Deadline is 24 th of April | |||
Name_Surname.pdf format email it as an attachment to belgin.tastan@itcollege.ee | |||
Active Directory runs on Windows Server 2012 R2, Domain Name suppose to be surname of student. There should be Central, Tartu and Parnu | |||
OUs. There should be at least 2 users in each OUs. There has to be at least one pc in this domain. Group Policy settings; Reset Local | |||
Administrator Password, Windows Firewall with Advanced Security for client machine. User Account Control (UAC), Password Policy settings | |||
for users. Password Policy; Central OU is with 13 characters and complex. Tartu OU is with 10 characters and complex. Parnu OU is with 8 | |||
characters and not complex. Users of Tartu and Parnu OUs should logon to their computers during work time which is 09:00-18:00 instead of | |||
this time users have to log off. | |||
* Active Directory | |||
Groups; Global Groups, Universal Groups, Domain Local Groups. | |||
Organizational Units; Geographicall or Business Based. | |||
One way - Two way Trust. | |||
Sites | |||
Forest - wide operations Master Roles (FSMO); Schema and Domain Naming Master Roles. | |||
Domain - wide Operations Master Roles; Primary Domain Controller (PDC), Relative ID (RID), Infrastructure master role. | |||
* Domain Controller | |||
* Additional Domain Controller | |||
* Read Only Domain Controller; Read Only Active Directory Database and GC PASS, Only allowed user passwords are stored on RODC, Uniderectional Replication, Role Seperation. | |||
Increase security for remote Domain Controllers where physical security cannot be guaranteed. | |||
* Child Domain Controller; Child domains can represent geographical entities (for example, the United States and Europe), administrative entities within the organization (for example, sales and marketing departments), or other organization-specific boundaries, according to the needs of the organization. Domains are created below the root domain to minimize Active Directory replication and to provide a means for creating domain names that do not change. | |||
* DHCP: Dynamic Host Configuration Protocol | |||
What is DHCP, and when & where is it used? | |||
Components of DHCP | |||
BOOTP and DHCP relation | |||
DHCP message format | |||
DHCP procedures | |||
-allocating new address | |||
-lease renewal | |||
State machine | |||
Questions & answers re. DHCP | |||
Benefits of DHCP | |||
Installation and Configuration DHCP | |||
* Installing and Configuring WDS (Windows Deployment Services): Full Images Deployment | |||
* Installing and Configuring Microsoft Deployment Toolkit (MDT): Deploying Windows 7 + Office 2010 | |||
* Deploying Software Using Group Policy : MSI Packages | |||
3. Assignment; | |||
Grading criteria for each assignment will be provided with the instructions for the assignment. If the assignment is not delivered | |||
by the deadline, the assignment is considered to be failed. Plagiarism is not allowed. Deadline is 15 th of May at 24:00 | |||
Homework suppose to include screen capture and explanation with your own words in pdf format. | |||
Name_Surname.zip format email it as an attachment to belgin.tastan@itcollege.ee | |||
Deploy Windows 7 with Office 2010 | |||
- Deployment Share folder is with student name. | |||
- Task Sequence ID is with student (ID) number. | |||
- Internet explorer name is with student blog-web name. | |||
- User credentials is with student name. | |||
Deploy an MSI Package with GPO | |||
- OU name is with student name_OU | |||
- MSI Package is 7 zip or winrar | |||
Total: Please add your both Windows 7 with Office 2010 and MSI Package file in to zip folder. | |||
* Exchange Server | * Exchange Server | ||
Exchange Server Installation | |||
Configure Exchange Server to Send and Receive Outside Email | |||
Configuring Outlook for Users | |||
Edge Transport Server Role—Establishing Perimeter Security | |||
Client Access Server Role—Providing User Connectivity | |||
Hub Transport Servers—Routing the Mail | |||
Unified Messaging Servers—Combining All the Data | |||
Mailbox Servers—What It’s All About | |||
Mailbox High Availability | |||
Disaster Recovery | |||
Storage Options | |||
* Printer Configuration | |||
How to Configure a Printer in Windows | |||
Setting up Printers via Group Policy | |||
Setting as a default printer | |||
How to use Group Policy settings to control printers in Active Directory | |||
* | * Virtual Private Network | ||
Configure VPN in Windows Server | |||
Configure DHCP Relay Agent | |||
Configure and Enable Routing and Remote Access | |||
Creating VPN Connection | |||
Client Connectivity Testing | |||
4. Assignment; | |||
Grading criteria for each assignment will be provided with the instructions for the assignment. If the assignment is not delivered by | |||
the deadline, the assignment is considered to be failed. Plagiarism is not allowed. Deadline is 24th of May at 24:00 Homework suppose | |||
to include screen capture and explanation with your own words in pdf format. Name_Surname.pdf format email it as an attachment | |||
to belgin.tastan@itcollege.ee | |||
Install and configure VPN in Windows Server and show client connectivity. | |||
* Mimikatz | |||
One of the most interesting tools in a penetration tester’s arsenal is mimikatz. Mimikatz is a tool that scrapes the memory of the process responsible for Windows authentication(LSASS) and reveals cleartext passwords and NTLM hashes that an attacker can use to pivot around a network. From that point they escalate privilege either by authenticating with the clear text credentials or passing the hash. | |||
- | https://www.itcollege.ee/tudengile/oppehoone/tehnika-kasutamine/#Microsoft | ||
=Linux:= | =Linux:= | ||
Latest revision as of 11:50, 9 November 2017
Linux/Windows administration
General information
In this course we will take a look at how Linux and Windows machines are administered.
Assume that from previous courses there is familiarity with: basic virtualization, networks, partitions, filesystems, BIND9.
sharing document: https://onedrive.live.com/?authkey=%21AFAxtpKI_r5cX6c&id=93040B43356F2D88%21116648&cid=93040B43356F2D88
Instructor: Belgin TAŞTAN
Exam Dates:
26 May 2017 Lab Exam %50 Mendatory
29 May 2017 Lab Exam %50 People who failed previous examination
Windows:
- IP Configuration & Subnetting
-IP Adresses and Classes
-Subnet Mask
-Subnetting
-Loopback IP Adress
-Public and Private IP Adresses
- Windows Client Configuration
-Introduction to Editions & Features
-Create John, Elena and Steve users. John suppose to logon same computer Monday-Friday at 08:00-18:00, Elena Saturday-Sunday at 08:00-18:00, Steve Monday-Friday at 18:00-02:00.
-Group Policy Object Editor Examples; All users can't configure IP. Password Length must be 7 characters. Password must meet complexity requirements. Internet home page must be www.itcollege.ee . No more USB drivers. No usage of Control Panel. No CMD. I want to see as an Administrator who logged into my computer and when with different user credentials. No changes in system time.
-Sharing Folder Examples; Create a new folder name with "Sharing Folder" John and Elena Read Permission, Steve Read/Write Permission. Back Up Operating System chose target as "Sharing Folder".
-Bitlocker to Go USB drive increption.
-Bitdefender virus/malware protection configuration.
-Powershell code examples; Get-Service, Get-Process, Get-ExecutionPolicy, ping www.google.com , Get-Process | Format-List, Get-Job, Get-ScheduledJob, Get-Module –ListAvailable, Test-Connection localhost, Get-EventLog system, Clear-EventLog.
-Direct Access Configuration.
-Hyper-V Installing.
- Windows Server Configuration
-Introduction to Editions & Features ( 2008 R2, 2012 R2, 2016 )
-Initial Configuration with Task Wizard ( Time, Name, IP, Update )
- Hyper-V Configuration
-Introduction of Hyper-V Manager ( Create New Machine, Import Virtual Machine, Edit Disk, Import Disk, Virtual Network Manager, Save&Pause States, Hyper-V Settings )
-Live Migration Process
-Fail over Cluster Manager ( Cluster Shared Volume, Cluster Storage )
-Overview of System Center Virtual Machine Manager
-Disk Configuration ( Fixed Size, Dynamically Expanding, Differencing )
-PowerShell codes for managing Hyper-V objects, including VMs, network adapters and VHDs.
-Hyper-V Replica
- Virtualization
-Introduction to Server and Network Virtualization
- Disk Configuration
-Disk Management ( Dynamic Disk, Master Boot Record, GUID Partition Table, Spanned Volume, Stripped Volume, Mirrored Volume, RAID-5 Volume, Extending a Volume, Shrinking a Volume, Adding a Mirror to a Volume )
1. Assignment; Windows Server 2008 R2 Disk Configuration and Hyper-V Configuration. Implement Disk and Hyper-V Configurations with explanations and screen captures.
Disk Configuration ( Dynamic Disk, Master Boot Record, GUID Partition Table, Spanned Volume, Stripped Volume, Mirrored Volume, RAID-5 Volume, Extending a Volume, Shrinking a Volume, Adding a Mirror to a volume ).
Hyper-V Configuration ( Cluster Shared Volumes, Live Migration )
Email to belgin.tastan@itcollege.ee
- Server Back-up
-Full Back Up
-Incremental Backup
-Differential Backup
- Items in Backup
-Bare Metal
-System State
-Full
-Individuals Volumes
-Files or Volumes
- Backup resources
- Shared folders
- Removable media
- Internal hard disk
- External hard disk
- Fail Over Cluster
-Creating Fail Over Cluster
-Adding Disks to a Cluster
-Creating a Cluster Shared Volume ( CSV )
- Redundant Array of Independent Disks ( RAID ) Types
- RAID 0
- RAID 1
- RAID 5
- RAID 10 ( 1+0 )
- RAID 6
- RAID 00
- RAID 50
- RAID 60
Exercises
-Adding 2 more disks and make it mirror disk. Take Bare Metal Backup in to this location.
-Adding 1 more disk and take Full Backup in to this location.
Exercises
- Local Admin Password changing with PowerShell.exe
Instructions From a computer :
1.open Powershell as administrator
2.make sure that executionpolicy allow script execution
3.Type : resetlocalAdminpassword.ps1 -newpassword <password> where <password> is the new value of your password
https://gallery.technet.microsoft.com/Reset-Local-Administrator-e3023c3a
- Firewall should disabled in Group Policy Object Editor
- Windows Defender should disabled in Group Policy Object Editor
- Windows Update should disabled in Group Policy Object Editor
- Smart Screen should disabled in Group Policy Object Editor
- User Account Control Settings should force to low level
- IPV6 should force to Up and Running in Group Policy Object Editor
- Audit Logs should force to disabled in Group Policy Object Editor
- C$ Restriction. User Configuration > Administrative Templates > Windows Components > Windows Explorer - "Hide these specified drives in My Computer" and "Prevent access to drives from My Computer". Both are set to "Enabled" with the option "Restrict C drive only".
- DNS Configuration
- Understanding and Managing DNS
- Introduction to the DNS
- DNS Components; The name space, The servers, The resolvers.
- DNS Structure and Hierarchy
- The DNS in Context
NOTE: Everyone will bring an example of Amplification attacks to talk about.
Resource Records and Records Types
Forward and Reverse Lookup Zone
DNS Replication
- Active Directory
- AD DS Physical Components
Domain Controllers, Global Catalog Servers, Data Store, Replication, Sites.
- AD DS Logical Components
AD DS Schema, The Basics, Trusts, AD DS Objects.
- Protocol
- What is Authentication?
- What is Authorization?
- Why Deploy AD DS?
- Centralized Network Management
- Requirements for Installing AD DS
- Overview of AD DS and DNS
- Overview of AD DS Components
Installation and Management AD
Observe the installation of AD DS Active Directory Users and Computers Active Directory Administrative Center Active Directory Sites and Services
- Creating new user accounts
- To join computers running Windows Server 2008 R2
- Setting up GPO-s
- GPO Components
- GPO Work Steps
- Modifying Group Policy Processing
- WMI Filter
- Loopback Processing
- Backup and Restore GPO
- Fine-grained passwords
- Installing and Configuring Active Directory on Server 2012 R2, Server 2016.
- Creating Organizational Units and users.
2. Assignment; Grading criteria for each assignment will be provided with the instructions for the assignment. If the assignment is not delivered by the deadline, the assignment is considered to be failed. Plagiarism is not allowed. Deadline is 24 th of April Name_Surname.pdf format email it as an attachment to belgin.tastan@itcollege.ee
Active Directory runs on Windows Server 2012 R2, Domain Name suppose to be surname of student. There should be Central, Tartu and Parnu OUs. There should be at least 2 users in each OUs. There has to be at least one pc in this domain. Group Policy settings; Reset Local Administrator Password, Windows Firewall with Advanced Security for client machine. User Account Control (UAC), Password Policy settings for users. Password Policy; Central OU is with 13 characters and complex. Tartu OU is with 10 characters and complex. Parnu OU is with 8 characters and not complex. Users of Tartu and Parnu OUs should logon to their computers during work time which is 09:00-18:00 instead of this time users have to log off.
- Active Directory
Groups; Global Groups, Universal Groups, Domain Local Groups.
Organizational Units; Geographicall or Business Based.
One way - Two way Trust.
Sites
Forest - wide operations Master Roles (FSMO); Schema and Domain Naming Master Roles.
Domain - wide Operations Master Roles; Primary Domain Controller (PDC), Relative ID (RID), Infrastructure master role.
- Domain Controller
- Additional Domain Controller
- Read Only Domain Controller; Read Only Active Directory Database and GC PASS, Only allowed user passwords are stored on RODC, Uniderectional Replication, Role Seperation.
Increase security for remote Domain Controllers where physical security cannot be guaranteed.
- Child Domain Controller; Child domains can represent geographical entities (for example, the United States and Europe), administrative entities within the organization (for example, sales and marketing departments), or other organization-specific boundaries, according to the needs of the organization. Domains are created below the root domain to minimize Active Directory replication and to provide a means for creating domain names that do not change.
- DHCP: Dynamic Host Configuration Protocol
What is DHCP, and when & where is it used?
Components of DHCP
BOOTP and DHCP relation
DHCP message format
DHCP procedures
-allocating new address
-lease renewal
State machine
Questions & answers re. DHCP
Benefits of DHCP
Installation and Configuration DHCP
- Installing and Configuring WDS (Windows Deployment Services): Full Images Deployment
- Installing and Configuring Microsoft Deployment Toolkit (MDT): Deploying Windows 7 + Office 2010
- Deploying Software Using Group Policy : MSI Packages
3. Assignment;
Grading criteria for each assignment will be provided with the instructions for the assignment. If the assignment is not delivered
by the deadline, the assignment is considered to be failed. Plagiarism is not allowed. Deadline is 15 th of May at 24:00
Homework suppose to include screen capture and explanation with your own words in pdf format.
Name_Surname.zip format email it as an attachment to belgin.tastan@itcollege.ee
Deploy Windows 7 with Office 2010
- Deployment Share folder is with student name.
- Task Sequence ID is with student (ID) number.
- Internet explorer name is with student blog-web name.
- User credentials is with student name.
Deploy an MSI Package with GPO
- OU name is with student name_OU
- MSI Package is 7 zip or winrar
Total: Please add your both Windows 7 with Office 2010 and MSI Package file in to zip folder.
- Exchange Server
Exchange Server Installation
Configure Exchange Server to Send and Receive Outside Email
Configuring Outlook for Users
Edge Transport Server Role—Establishing Perimeter Security
Client Access Server Role—Providing User Connectivity
Hub Transport Servers—Routing the Mail
Unified Messaging Servers—Combining All the Data
Mailbox Servers—What It’s All About
Mailbox High Availability
Disaster Recovery
Storage Options
- Printer Configuration
How to Configure a Printer in Windows
Setting up Printers via Group Policy
Setting as a default printer
How to use Group Policy settings to control printers in Active Directory
- Virtual Private Network
Configure VPN in Windows Server
Configure DHCP Relay Agent
Configure and Enable Routing and Remote Access
Creating VPN Connection
Client Connectivity Testing
4. Assignment;
Grading criteria for each assignment will be provided with the instructions for the assignment. If the assignment is not delivered by
the deadline, the assignment is considered to be failed. Plagiarism is not allowed. Deadline is 24th of May at 24:00 Homework suppose
to include screen capture and explanation with your own words in pdf format. Name_Surname.pdf format email it as an attachment
to belgin.tastan@itcollege.ee
Install and configure VPN in Windows Server and show client connectivity.
- Mimikatz
One of the most interesting tools in a penetration tester’s arsenal is mimikatz. Mimikatz is a tool that scrapes the memory of the process responsible for Windows authentication(LSASS) and reveals cleartext passwords and NTLM hashes that an attacker can use to pivot around a network. From that point they escalate privilege either by authenticating with the clear text credentials or passing the hash.
https://www.itcollege.ee/tudengile/oppehoone/tehnika-kasutamine/#Microsoft
Linux:
- Configuration management using Puppet
- Setting up fileserver using Samba, identity mapping
- Setting up Samba as domain controller and/or joining Samba to AD domain
- Using samba-tool to manage user accounts and DNS records on domain controller
- Interacting with domain controller using LDAP
- Configuring Postfix and Dovecot servers for sending e-mail via SMTP and receiving e-mail over IMAP
- Creating service accounts and authenticating network services (gogs, wiki, etc) with LDAP
- Guidelines for hardening Ubuntu installation
Linux
Interacting with domain controller
Video recording of the lecture/lab here: https://echo360.e-ope.ee/ess/echo/presentation/a5a41d62-f6b3-4a6a-9a3b-6049dfbea5c9
If you're attempting to run these commands on a blank Ubuntu box you need to install couple packages:
apt install nmap dnsutils krb5-user ldap-utils libsasl2-modules-gssapi-mit samba-common cifs-utils pip install pyldap
Figure out what are the host name(s) of the domain controller(s) for INTRA.ITCOLLEGE.EE realm:
dig -t SRV _ldap._tcp.intra.itcollege.ee
Figure out which ports are open on the domain controller?
nmap ...
Attempt to query information about your user account from the domain controller. Where is the e-mail being forwarded to? What is the security identifier for the user? What script is being executed when the user logs in to Windows workstation?
ldapsearch -H ldap://... -W -D your-username@itcollege.ee -b ... samaccountname=target-username
Download and install Apache Directory Studio. Configure connection to the domain controller for browsing graphically.
Kerberos client commands
List Kerberos tickets:
klist
Flush credentials:
kdestroy
Obtain new credentials. What is the error message returned upon incorrect password? What tickets were initialized by the command? What is the lifetime of the tickets?
kinit your-username@INTRA.ITCOLLEGE.EE
Try to renew:
krenew
Attempt same LDAP queries as you did before but now with Kerberos credentials by substituing -W -D ... flags with -Y GSSAPI:
ldapsearch -H ldap://... -Y GSSAPI -b ... samaccountname=target-username
List Kerberos tickets again. What changed? Query the same information from another domain controller. What changed now?
Attempt the same query using Python, make modifications as necessary:
import ldap, ldap.sasl
l = ldap.initialize('ldap://...')
l.set_option(ldap.OPT_REFERRALS, 0)
l.sasl_interactive_bind_s('', ldap.sasl.gssapi())
filter = '(&(objectClass=user)(objectCategory=person)(samaccountname=target-username))'
r = l.search_s('dc=...,dc=...,dc=...',ldap.SCOPE_SUBTREE,filter,['cn','mail'])
for dn,entry in r:
if not dn: continue
full_name, = entry["cn"]
mail, = entry["mail"]
print full_name, mail
Browsing file shares
Using Samba client tools list filesystem shares from domain controller:
smbclient -k ... -L
List Kerberos tickets again. What changed?
List files in the NETLOGON share:
smbclient -k //.../netlogon -c ls
Download the login script whose filename was previously figured out with LDAP query.
smbclient -k //.../netlogon -c "get ..."
What commands are executed when Windows workstation logs in?
Attempt to browse shares from the fileserver using smbclient.
Open graphical filesystem browser of Ubuntu (nautilus). Press Ctrl-L to open up address bar. Attemp to browse shares at domain controller using smb:// scheme at fileserver.
Setting up domain controller
Video recording available here: https://echo360.e-ope.ee/ess/echo/presentation/9c28f070-0aee-4d34-930b-b043938beca8?ec=true
Samba 4.x is a software suite that provides functionality very close to Microsoft's Active Directory. This allows you to centrally manage user accounts, DNS records and Windows workstations. Samba is integral part of several Linux distributions such as Zentyal, Uninvention Corporate Server which are specifically targeted to small/medium sized enterprises.
Samba can also be installed on any other Linux distribution in which case some manual configuration is necessary and this is what following is about.
In this case domain controller is set up at dc1.mycorp.lan Make sure /etc/hosts and /etc/hostname correspond to your setup. Change arguments as necessary.
Set up a blank Ubuntu 16.04 server machine.
Install packages:
apt-get install samba samba-vfs-modules smbclient winbind krb5-user ldap-utils
Provision domain controller using Samba, note that capitalization matters:
rm -fv /etc/samba/smb.conf samba-tool domain provision --server-role=dc --domain=MYCORP --realm=MYCORP.LAN
Reconfigure Kerberos client configuration:
rm -fv /etc/krb5.conf ln -s /var/lib/samba/private/krb5.conf /etc/krb5.conf
Set domain administrator account password:
samba-tool user setpassword administrator
Reconfigure password expiration, in this case password expiration is disabled:
samba-tool domain passwordsettings set --max-pwd-age=0 samba-tool domain passwordsettings set --min-pwd-age=0
Open /etc/samba/smb.conf and in the [global] section specify upstream DNS server:
dns forwarder = 8.8.8.8
Start services:
service smbd stop service nmbd stop service samba-ad-dc stop service samba-ad-dc start
Reconfiguring DHCP options
Now usually at this point you would reconfigure your router to serve:
- the IP address of the domain controller as the DNS server (DHCP option 6)
- the correct domain suffix, which in this case is mycorp.lan (DHCP option 15)
- the correct search domain, again in this case mycorp.lan (DHCP option 119)
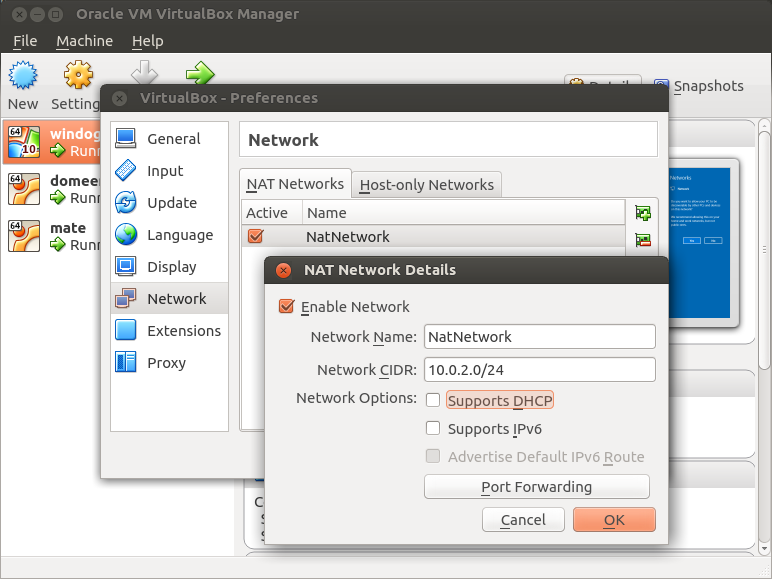
When working with VirtualBox and not wanting to set up a whole virtual machine for routing you can use VirtualBox's NatNetwork feature with DHCP disabled and install DHCP server on the domain controller instead. In VirtualBox main menu click Preferences and create a new NATNetwork with DHCP disabled:
Configure a static IP address for the domain controller in /etc/network/interfaces and reboot the box:
auto lo iface lo inet loopback auto enp0s3 iface enp0s3 inet static address 10.0.2.15 netmask 255.255.255.0 gateway 10.0.2.2 dns-nameservers 127.0.0.1 dns-domain mycorp.lan dns-search mycorp.lan
At the domain controller install ISC DHCP server package:
apt install isc-dhcp-server
Remove existing configuration file:
rm /etc/dhcp/dhcpd.conf
In the same file configure the DHCP server:
subnet 10.0.2.0 netmask 255.255.255.0 {
range 10.0.2.100 10.0.2.200;
option domain-name "mycorp.lan";
option domain-search "mycorp.lan";
option domain-name-servers 10.0.2.15;
option routers 10.0.2.2;
}
Save the file and restart service:
systemctl restart isc-dhcp-server
Joining workstations to domain
Download Windows 10 ISO, install it and join it to domain. Proceed to install Microsoft Remote Server Administration Tools to manage your domain controller. Log in with Other user and specify either mycorp\administrator or administrator@mycorp.lan as username. Verify that file shares at \\dc1.mycorp.lan are browseable.
Boot Ubuntu MATE LiveCD and install Ubuntu on the harddisk. Join it to domain using realmd and afterwards try to interact with the domain controller as shown in previous session:
apt install realmd realm --verbose join mycorp.lan pam-auth-update # Tick "Create home directory on login" and press enter
Try to log out and log in with administrator@mycorp.lan and the domain administrator password.
This category currently contains no pages or media.