Improve security with Zabbix-Monitor-Server: Difference between revisions
| (21 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[File:zabbix_logo.png|thumb|300px| Zabbix monitoring system]] | |||
Author: | Author: | ||
Mohanad Aly | Mohanad Aly | ||
Cyber Security Engineering (C21) | Cyber Security Engineering (C21) | ||
| Line 6: | Line 8: | ||
Page Created: 19 November 2017 | Page Created: 19 November 2017 | ||
Last modified: | Last modified: 25 November 2017 | ||
| Line 27: | Line 28: | ||
Zabbix is an Open Source, high-level enterprise software designed to monitor and keep track of networks, servers and applications in real time. Build in a server-client model, Zabbix can collect different type of data than are used to create historical graphics and output performance or load trends of the monitored targets. | Zabbix is an Open Source, high-level enterprise software designed to monitor and keep track of networks, servers and applications in real time. Build in a server-client model, Zabbix can collect different type of data than are used to create historical graphics and output performance or load trends of the monitored targets. | ||
Zabbix is based on the following components: | |||
| Line 116: | Line 117: | ||
==== Prerequisites ==== | ==== Prerequisites ==== | ||
Ubuntu Linux machine, sudo access and some Linux beginner skills are needed. | Ubuntu Linux machine, sudo access and some Linux beginner skills are needed. | ||
| Line 186: | Line 186: | ||
*Open your web browser and YOURIPADDRESS/zabbix | *Open your web browser and YOURIPADDRESS/zabbix | ||
[[File:Screenshot from 2017-11-25 21-26-14.png|thumb|center| Zabbix monitoring system]] | |||
=Zabbix-Agent= | |||
Before start to install the Zabbbix-agent update the machine | |||
<code> apt-get update </code> | |||
Zabbix-Agent is easy to install, just one command and it installed into the machine. | |||
<code> apt-get install zabbix-agent </code> | |||
User need to go to the configuration folder to start edit the agent config file | |||
<code> cd /etc/zabbix </code> | |||
Start to edit the file to make the correct configuration to send all the checks to Zabbix-server | |||
<code> nano -c zabbix_agentd.conf </code> | |||
Checking the configuration file | |||
*Uncomment line 43 | |||
*If user need to enable the debugging mode uncomment line 57 | |||
*Enable the remote command uncomment line 73 | |||
*Enable the log remote command uncomment line 82 | |||
*Server IP address line 95 | |||
*Listen-port 10050 uncomment line 103 | |||
*Enable the server-active uncomment line 136 | |||
*Hostname depends on the user configuration | |||
=Enable the encryption Front-end Web= | |||
SSL support actually comes standard in the Ubuntu 16.04 Apache package. We simply need to enable it to take advantage of SSL on our system. | |||
Enable the module by typing: | |||
<code> sudo a2enmod ssl </code> | |||
Creating a subdirectory within Apache's configuration hierarchy to place the certificate files that we will be making | |||
sudo mkdir /etc/apache2/ssl | |||
Now that we have a location to place our key and certificate, we can create them both in one step by typing | |||
<code> sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/apache.key -out /etc/apache2/ssl/apache.crt </code> | |||
Country Name (2 letter code) [AU]:EE | |||
State or Province Name (full name) [Some-State]:Harjumaa | |||
Locality Name (eg, city) []:Tallinn | |||
Organization Name (eg, company) [Internet Widgits Pty Ltd]: Incorporated Company | |||
Organizational Unit Name (eg, section) []:Head | |||
Common Name (e.g. server FQDN or YOUR name) []: domain.com | |||
Email Address []: | |||
Please enter the following 'extra' attributes | |||
to be sent with your certificate request | |||
A challenge password []: | |||
An optional company name []: | |||
*openssl: This is the basic command line tool provided by OpenSSL to create and manage certificates, keys, signing requests, etc. | |||
*req: This specifies a subcommand for X.509 certificate signing request (CSR) management. X.509 is a public key infrastructure standard that SSL adheres to for its key and certificate managment. Since we are wanting to create a new X.509 certificate, this is what we want. | |||
*-x509: This option specifies that we want to make a self-signed certificate file instead of generating a certificate request. | |||
*-nodes: This option tells OpenSSL that we do not wish to secure our key file with a passphrase. Having a password protected key file would get in the way of Apache starting automatically as we would have to enter the password every time the service restarts. | |||
*-days 365: This specifies that the certificate we are creating will be valid for one year. | |||
*-newkey rsa:2048: This option will create the certificate request and a new private key at the same time. This is necessary since we didn't create a private key in advance. The rsa:2048 tells OpenSSL to generate an RSA key that is 2048 bits long. | |||
*-keyout: This parameter names the output file for the private key file that is being created. | |||
*-out: This option names the output file for the certificate that we are generating. | |||
Open the file with root privileges now: | |||
<code> sudo nano /etc/apache2/sites-available/default-ssl.conf </code> | |||
<pre> | |||
<IfModule mod_ssl.c> | |||
<VirtualHost _default_:443> | |||
ServerAdmin admin@example.com | |||
ServerName your_domain.com | |||
ServerAlias www.your_domain.com | |||
DocumentRoot /var/www/html | |||
ErrorLog ${APACHE_LOG_DIR}/error.log | |||
CustomLog ${APACHE_LOG_DIR}/access.log combined | |||
SSLEngine on | |||
----> SSLCertificateFile /etc/apache2/ssl/apache.crt | |||
----> SSLCertificateKeyFile /etc/apache2/ssl/apache.key | |||
<FilesMatch "\.(cgi|shtml|phtml|php)$"> | |||
SSLOptions +StdEnvVars | |||
</FilesMatch> | |||
<Directory /usr/lib/cgi-bin> | |||
SSLOptions +StdEnvVars | |||
</Directory> | |||
BrowserMatch "MSIE [2-6]" \ | |||
nokeepalive ssl-unclean-shutdown \ | |||
downgrade-1.0 force-response-1.0 | |||
BrowserMatch "MSIE [17-9]" ssl-unclean-shutdown | |||
</VirtualHost> | |||
</IfModule> | |||
</pre> | |||
SSL-enabled virtual host | |||
<code> sudo a2ensite default-ssl.conf </code> | |||
Restart Apache to load our new virtual host file | |||
<code> service apache2 restart </code> | |||
Test the configuration by visiting the server's domain name or public IP address after specifying the https:// protocol, like this: | |||
<code> https://server_domain_name_or_IP </code> | |||
This to solve the problem to enable the ssl | |||
<code> nano 000-default.conf </code> | |||
<pre> | |||
# Special virtulhost only for redirecting | |||
<VirtualHost *:80> | |||
ServerName | |||
Redirect "/" "https://Zabbix-server/" | |||
</VirtualHost> | |||
</pre> | |||
=Summary= | =Summary= | ||
Latest revision as of 14:11, 9 January 2018

Author: Mohanad Aly
Cyber Security Engineering (C21)
Page Created: 19 November 2017
Last modified: 25 November 2017
Introduction
This article introduces the Monitoring application called Zabbix.
Monitoring
Monitoring is the process of keep tracking of system resources.
Monitoring is the process of observing and checking the progress or quality of something over a period of time; keep under systematic review.[1] Monitoring cannot be achieved without logging. That is the reason integrated solutions combine the two processes. Monitoring is used to:
- Check performance
- Detect if something worth noticing happened
- Prevent something to happen
- Detect whether a system is under attack and that is the most important part for the cyber security
Zabbix Monitoring system
Zabbix is an Open Source, high-level enterprise software designed to monitor and keep track of networks, servers and applications in real time. Build in a server-client model, Zabbix can collect different type of data than are used to create historical graphics and output performance or load trends of the monitored targets.
Zabbix is based on the following components:
| Software | Version | Comments |
|---|---|---|
| Apache | 1.3.12 or later | |
| PHP | 5.0 or later | |
| PHP modules: php-gd | GD 2.0 or later | PHP GD module must support PNG images. |
| PHP TrueType support | with-ttf | |
| PHP bc support | php-bcmath, --enable-bcmath | |
| PHP XML support | php-xml or php5-dom, if provided as a separate package by the distributor | |
| PHP session support | php-session, if provided as a separate package by the distributor | |
| PHP socket support | php-net-socket, --enable-sockets. Required for user script support. | |
| PHP multibyte support | php-mbstring, --enable-mbstring | |
| IBM DB2 ibm_db2 | Required if IBM DB2 is used as Zabbix back end database. | |
| MySQL php-mysql | 3.22 or later | Required if MySQL is used as Zabbix back end database. |
| Oracle oci8 | Required if Oracle is used as Zabbix back-end database. | |
| PostgreSQL php-pgsql | 7.0.2 or later if Zabbix < 1.8.9, 7.4 or later if Zabbix >= 1.8.9 | Required if PostgreSQL is used as Zabbix back-end database. Consider using PostgreSQL 8.x or later for much better performance. It is suggested to use at least PostgreSQL 8.3, performance which introduced much better VACUUM. |
| SQLite php-sqlite3 | 3.3.5 or later | Required if SQLite is used as Zabbix back-end database. |
The main advantages of Zabbix
- Open-source
- Customized Dashboards
- Ease of Use
- Monitor everything
- Network Security
- Performance
- Agentless Monitoring
- Hardware Monitoring
Why monitoring is important for cyber security
- First thing is important for the cyber security professional is the CIA (Confidentiality, Integrity and Availability)What is CIA, and to get to the standards we need to implement the tools that provides the security for our data and servers that hosting the data.
- Second system administrator need tools to react when something happened to the server, so system administrator need real time checks to make sure that everything is working in order.
- Third Monitoring tools alerts should be readable for the administrator and fast, when something happened to the server or the service the monitoring tool should send the alerts in the exact time to give the administrator the time to fix it.
- Fourth the attacks and threats which is more difficult to the system administrator to figure out what is going in the server, and the monitoring tools should has the detection solution for the common attacks.
- Fifth the debugging, when system have error the monitor tool should have a readable debugging..
Setting up Zabbix
In the following tutorial, Ubuntu 16.04 64-bit distribution will be used LTS.
Prerequisites
Ubuntu Linux machine, sudo access and some Linux beginner skills are needed.
This tutorial describes the commands and configuration to make the services work together Zabbix.
- It is important to have the latest package lists to update them to get info on the newest versions of packages and their dependencies. So we need to run the following command to update them:
Command
sudo apt update
sudo apt upgrade
Installing the prerequisites
- The server has the ability to check standard networking services (HTTP, FTP, SMTP, IMAP etc) without the need to install extra software on the monitored hosts.
Begin with the commands:
sudo apt install mysql-server
dpkg -i zabbix-release_3.2-1+xenial_all.deb
apt-get update
apt-get install zabbix-server-mysql zabbix-frontend-php zabbix-agent zabbix-get zabbix-sender snmp snmpd snmp-mibs-downloader php7.0-bcmath php7.0-xml php7.0-mbstring
mysql -u root -p your password
create database zabbix character set utf8 collate utf8_bin;
grant all privileges on zabbix.* to zabbix@localhost identified by 'zabbix';
exit;
cd /usr/share/doc/zabbix-server-mysql/
zcat create.sql.gz | mysql -u root -p zabbix
mysql -u root -p your password
show databases;
use zabbix;
show tables;
exit;
cd /etc/zabbix/
- And copy evenhandler directory to the nagios directory:
timedatectl list-timezones
Or
timedatectl
nano apache.conf
nano zabbix_server.conf
service apache2 restart
service zabbix-server restart
cd nagios-plugins-2.1.2/
service zabbis-server status
ifconfig
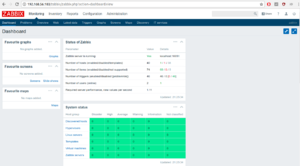
- Open your web browser and YOURIPADDRESS/zabbix
Zabbix-Agent
Before start to install the Zabbbix-agent update the machine
apt-get update
Zabbix-Agent is easy to install, just one command and it installed into the machine.
apt-get install zabbix-agent
User need to go to the configuration folder to start edit the agent config file
cd /etc/zabbix
Start to edit the file to make the correct configuration to send all the checks to Zabbix-server
nano -c zabbix_agentd.conf
Checking the configuration file
- Uncomment line 43
- If user need to enable the debugging mode uncomment line 57
- Enable the remote command uncomment line 73
- Enable the log remote command uncomment line 82
- Server IP address line 95
- Listen-port 10050 uncomment line 103
- Enable the server-active uncomment line 136
- Hostname depends on the user configuration
Enable the encryption Front-end Web
SSL support actually comes standard in the Ubuntu 16.04 Apache package. We simply need to enable it to take advantage of SSL on our system.
Enable the module by typing:
sudo a2enmod ssl
Creating a subdirectory within Apache's configuration hierarchy to place the certificate files that we will be making
sudo mkdir /etc/apache2/ssl
Now that we have a location to place our key and certificate, we can create them both in one step by typing
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/apache.key -out /etc/apache2/ssl/apache.crt
Country Name (2 letter code) [AU]:EE State or Province Name (full name) [Some-State]:Harjumaa Locality Name (eg, city) []:Tallinn Organization Name (eg, company) [Internet Widgits Pty Ltd]: Incorporated Company Organizational Unit Name (eg, section) []:Head Common Name (e.g. server FQDN or YOUR name) []: domain.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
- openssl: This is the basic command line tool provided by OpenSSL to create and manage certificates, keys, signing requests, etc.
- req: This specifies a subcommand for X.509 certificate signing request (CSR) management. X.509 is a public key infrastructure standard that SSL adheres to for its key and certificate managment. Since we are wanting to create a new X.509 certificate, this is what we want.
- -x509: This option specifies that we want to make a self-signed certificate file instead of generating a certificate request.
- -nodes: This option tells OpenSSL that we do not wish to secure our key file with a passphrase. Having a password protected key file would get in the way of Apache starting automatically as we would have to enter the password every time the service restarts.
- -days 365: This specifies that the certificate we are creating will be valid for one year.
- -newkey rsa:2048: This option will create the certificate request and a new private key at the same time. This is necessary since we didn't create a private key in advance. The rsa:2048 tells OpenSSL to generate an RSA key that is 2048 bits long.
- -keyout: This parameter names the output file for the private key file that is being created.
- -out: This option names the output file for the certificate that we are generating.
Open the file with root privileges now:
sudo nano /etc/apache2/sites-available/default-ssl.conf
<IfModule mod_ssl.c>
<VirtualHost _default_:443>
ServerAdmin admin@example.com
ServerName your_domain.com
ServerAlias www.your_domain.com
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLEngine on
----> SSLCertificateFile /etc/apache2/ssl/apache.crt
----> SSLCertificateKeyFile /etc/apache2/ssl/apache.key
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-6]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
BrowserMatch "MSIE [17-9]" ssl-unclean-shutdown
</VirtualHost>
</IfModule>
SSL-enabled virtual host
sudo a2ensite default-ssl.conf
Restart Apache to load our new virtual host file
service apache2 restart
Test the configuration by visiting the server's domain name or public IP address after specifying the https:// protocol, like this:
https://server_domain_name_or_IP
This to solve the problem to enable the ssl
nano 000-default.conf
# Special virtulhost only for redirecting
<VirtualHost *:80>
ServerName
Redirect "/" "https://Zabbix-server/"
</VirtualHost>
Summary
Zabbix is an open source application for monitoring a system. Zabbix has been widely used because of the ease of configuration. Zabbix also in support by various plugins. Look here for more information zabbix-main-documentation.
See also
Zabbix installation by Cyber-Tect-Tips
2- Zabbix-Agent
References
2- CIA
5- Requirements table reference