Onions can make people cry: Difference between revisions
No edit summary |
No edit summary |
||
| Line 43: | Line 43: | ||
In order to understand Tor and it works, the term and working principles of traffic analysis must be understood. | In order to understand Tor and it works, the term and working principles of traffic analysis must be understood. | ||
Traffic analysis is a form of Internet surveillance used to monitor and inspect network traffic from an end device to another over a public network. This technique can let people and services listen on a network to discover the user’s source and destination traffic, leading to the tracking of personal interests and behavior, even when the connection is encrypted. This is possible due to the structure of Internet data packets: data payload, which contains the content of what is being sent over the network such as an email or an image, and a header that is used for routing. Of these two parts data payload can be encrypted, but since traffic analysis focuses on the header rather than the content of the message, it still can disclose key information about the user, such as source and destination, size of the payload, and timing. This enables unauthorized parties as well as authorized intermediaries (e.g Internet Service Providers) to view a user’s information not from the content of the data itself but from the Internet headers. Very simple forms of traffic analysis may allow a middle man to sit in between the sender and the receiver and inspect on the travelling data. | Traffic analysis is a form of Internet surveillance used to monitor and inspect network traffic from an end device to another over a public network. This technique can let people and services listen on a network to discover the user’s source and destination traffic, leading to the tracking of personal interests and behavior, even when the connection is encrypted. This is possible due to the structure of Internet data packets: data payload, which contains the content of what is being sent over the network such as an email or an image, and a header that is used for routing. Of these two parts data payload can be encrypted, but since traffic analysis focuses on the header rather than the content of the message, it still can disclose key information about the user, such as source and destination, size of the payload, and timing. This enables unauthorized parties as well as authorized intermediaries (e.g Internet Service Providers) to view a user’s information not from the content of the data itself but from the Internet headers. Very simple forms of traffic analysis may allow a middle man to sit in between the sender and the receiver and inspect on the travelling data. <ref name="work">https://2019.www.torproject.org/about/overview.html.en | ||
</ref> | |||
===Tor's working principles=== | ===Tor's working principles=== | ||
The main purpose of Tor is to protect its users against traffic analysis. To do so the onion router distributes any of the user’s transactions over several nodes on the Internet, also called relays, making it impossible to link back a crossed point to a person’s information. What Tor does to obtain anonymity is sending data packets through several randomly chosen relays instead of choosing the direct route from source to destination. Using this technique no observer waiting at any of the relays can surely know where the data came from or where it is going. The circuit data takes is built incrementally one hop at a time. The user’s software encrypts all of the connections existing between relays on the network, where each of the relays knows only about the node it is taking data from and the node it is sending data to. To ensure that each hop cannot trace previous or further connections, a new pair of encryption keys is negotiated at every relay. Doing so neither an eavesdropper, nor a compromised node, nor any software, can use traffic analysis techniques to find the user’s connection source and destination. Since Tor aims for reliability it only works on TCP streams and for efficiency it uses the same circuit for connections that happen within more or less the same ten minutes. All of the later requests are assigned new circuits. | The main purpose of Tor is to protect its users against traffic analysis. To do so the onion router distributes any of the user’s transactions over several nodes on the Internet, also called relays, making it impossible to link back a crossed point to a person’s information. What Tor does to obtain anonymity is sending data packets through several randomly chosen relays instead of choosing the direct route from source to destination. Using this technique no observer waiting at any of the relays can surely know where the data came from or where it is going. The circuit data takes is built incrementally one hop at a time. The user’s software encrypts all of the connections existing between relays on the network, where each of the relays knows only about the node it is taking data from and the node it is sending data to. To ensure that each hop cannot trace previous or further connections, a new pair of encryption keys is negotiated at every relay. Doing so neither an eavesdropper, nor a compromised node, nor any software, can use traffic analysis techniques to find the user’s connection source and destination. Since Tor aims for reliability it only works on TCP streams and for efficiency it uses the same circuit for connections that happen within more or less the same ten minutes. All of the later requests are assigned new circuits. <ref name="work">https://2019.www.torproject.org/images/htw1.png</ref> | ||
Tor’s working principles can be summarized in three steps: | Tor’s working principles can be summarized in three steps: | ||
#The user’s Tor client obtains a list of relays from a directory server. | #The user’s Tor client obtains a list of relays from a directory server. <ref>https://2019.www.torproject.org/images/htw1.png</ref> | ||
#The user’s Tor client selects a random path from source to destination, where the path is chosen one hop at a time. | #The user’s Tor client selects a random path from source to destination, where the path is chosen one hop at a time. <ref>https://2019.www.torproject.org/images/htw2.png</ref> | ||
#If a different site from the previous one is at a later time visited, the user’s Tor client picks a second random path. | #If a different site from the previous one is at a later time visited, the user’s Tor client picks a second random path. <ref>https://2019.www.torproject.org/images/htw3.png</ref> | ||
===The onion services=== | ===The onion services=== | ||
Tor is not used just to browse the Internet anonymously, but to also access “special” services that together make up the dark web. These services are called the onion services and can only be accessed over Tor. | Tor is not used just to browse the Internet anonymously, but to also access “special” services that together make up the dark web. These services are called the onion services and can only be accessed over Tor. <ref name="service">https://community.torproject.org/onion-services/overview/</ref> | ||
Onion services benefit from many advantages that some other non-onion services may lack such as end-to-end encryption, end-to-end authentication, location hiding, and NAT punching (instead of using ports services punch through NAT). To achieve all this, Tor uses a special protocol called the Onion Service Protocol. Instead of consisting of a 32 or 128 bit IP address (depending on the IP version) an onion service makes use of its identity public key with a .onion extension. With the help of the Tor network the Onion Service Protocol allows a client to firstly introduce himself to the onion service and then together establish a meeting point, where the client will access the service. | Onion services benefit from many advantages that some other non-onion services may lack such as end-to-end encryption, end-to-end authentication, location hiding, and NAT punching (instead of using ports services punch through NAT). To achieve all this, Tor uses a special protocol called the Onion Service Protocol. Instead of consisting of a 32 or 128 bit IP address (depending on the IP version) an onion service makes use of its identity public key with a .onion extension. With the help of the Tor network the Onion Service Protocol allows a client to firstly introduce himself to the onion service and then together establish a meeting point, where the client will access the service. <ref name="service"/> | ||
An onion service’s address may look like this: | An onion service’s address may look like this: | ||
vww6ybal4bd7szmgncyruucpgfkqahzddi37ktceo3ah7ngmcopnpyyd.onion | vww6ybal4bd7szmgncyruucpgfkqahzddi37ktceo3ah7ngmcopnpyyd.onion <ref name="service"/> | ||
Onion services do not work nor act as Tor relays, while they behave as any other Tor clients. Every time an onion service needs to become available in the Tor network, it connects through relays as any other client would. This is the same for any device that wants to access an onion service. Connections from the client to the server never leave the Tor network and in contrast to a relay, an onion service never results in the user’s IP address. | Onion services do not work nor act as Tor relays, while they behave as any other Tor clients. Every time an onion service needs to become available in the Tor network, it connects through relays as any other client would. This is the same for any device that wants to access an onion service. Connections from the client to the server never leave the Tor network and in contrast to a relay, an onion service never results in the user’s IP address. <ref name="service2">https://community.torproject.org/onion-services/talk/</ref> | ||
===Anonimity problems=== | ===Anonimity problems=== | ||
| Line 67: | Line 68: | ||
====The final part of the communication is unencrypted==== | ====The final part of the communication is unencrypted==== | ||
Tor focuses on encrypting data moving between the user’s device and servers in and within the Tor network, leaving the final part of the connection between the exit relay and the destination unencrypted. This can make it possible for authorized and non-authorized parties to eavesdrop on traffic between the last relay and the server. The full list of Tor exit nodes is available publicly and unencrypted traffic can happen to be closely monitored. | Tor focuses on encrypting data moving between the user’s device and servers in and within the Tor network, leaving the final part of the connection between the exit relay and the destination unencrypted. This can make it possible for authorized and non-authorized parties to eavesdrop on traffic between the last relay and the server. The full list of Tor exit nodes is available publicly and unencrypted traffic can happen to be closely monitored. <ref name="anon">https://cybernews.com/privacy/what-is-tor-and-how-does-it-work/</ref> | ||
====User’s traffic can be deanonymized because of timing-based statistical techniques==== | ====User’s traffic can be deanonymized because of timing-based statistical techniques==== | ||
Timing-based statistical techniques may allow the network operator such as an ISP to determine from which computer the traffic is coming. This technique is usually hard to pull off and can also be expensive. This vulnerability may happen if both the entry relay and the exit relay exist on the same Internet Autonomous System or share the same address. | Timing-based statistical techniques may allow the network operator such as an ISP to determine from which computer the traffic is coming. This technique is usually hard to pull off and can also be expensive. This vulnerability may happen if both the entry relay and the exit relay exist on the same Internet Autonomous System or share the same address. <ref name="anon"/> | ||
====The onion router will not protect the user against more complex fingerprinting methods==== | ====The onion router will not protect the user against more complex fingerprinting methods==== | ||
If a user happens to be browsing a website with JavaScript enabled, the attacker can determine the identity of the person browsing by his mouse movements. Mouse movements can be used to correlate a Tor browsing session with a non-Tor browsing session. | If a user happens to be browsing a website with JavaScript enabled, the attacker can determine the identity of the person browsing by his mouse movements. Mouse movements can be used to correlate a Tor browsing session with a non-Tor browsing session. <ref name="anon"/> | ||
====Tor disposes of bugs that can be exploited==== | ====Tor disposes of bugs that can be exploited==== | ||
Even though Tor includes a good exploit protection, it still can be exploited due to security related bugs. In order to reduce the possibility of being exploited, a Tor user should always follow some safety guidelines. When using Tor the user is recommended to not log into usual accounts such as Gmail, to not follow unique browsing patterns, to turn the browser’s security to the max level (disables JavaScript on all sites), to use the HTTPS Everywhere extension, and never use BitTorrent over Tor. | Even though Tor includes a good exploit protection, it still can be exploited due to security related bugs. In order to reduce the possibility of being exploited, a Tor user should always follow some safety guidelines. When using Tor the user is recommended to not log into usual accounts such as Gmail, to not follow unique browsing patterns, to turn the browser’s security to the max level (disables JavaScript on all sites), to use the HTTPS Everywhere extension, and never use BitTorrent over Tor. <ref name="anon"/> | ||
==Legal and illegal activities in Tor== | ==Legal and illegal activities in Tor== | ||
| Line 84: | Line 85: | ||
===Legal activities=== | ===Legal activities=== | ||
Since social media and forums are not illegal, they are also legal in the dark web. Users will not be committing anything criminal if they use the dark web to participate in forums or to read hidden blog posts. Users have to be careful because visiting certain sites or purchasing certain items through the dark web is illegal. There is a change that participating in certain forums is illegal, especially if the forum has posts about threats, hate speech or is inciting and encouraging criminal behaviour. | Since social media and forums are not illegal, they are also legal in the dark web. Users will not be committing anything criminal if they use the dark web to participate in forums or to read hidden blog posts. Users have to be careful because visiting certain sites or purchasing certain items through the dark web is illegal. There is a change that participating in certain forums is illegal, especially if the forum has posts about threats, hate speech or is inciting and encouraging criminal behaviour. <ref name="isIllegal">https://us.norton.com/internetsecurity-privacy-is-the-dark-web-illegal.html</ref> | ||
Dark web also has its own social media sites like Blackbook and Torbook. These sites let you create a completely anonymous profile. More and more legitimate companies are making themselves available on the dark web (e.g Facebook). | Using the dark web itself is not illegal. Many people prefer to use it to keep their personal data safe while doing normal things, as in the regular web, like sending emails, chatting on social media, and browsing forums. Since Google and Bing might sell personal data, the dark web has its own search engines. These alternatives will keep people's data private, which makes them a better option for those who want to keep their personal information to themselves.<ref name="isIllegal/> | ||
Dark web also has its own social media sites like Blackbook and Torbook. These sites let you create a completely anonymous profile. More and more legitimate companies are making themselves available on the dark web (e.g Facebook). <ref name="isIllegal/> | |||
Dark web is a way out for people living in places where the regime is not that allowing. People can safely access information that their government tries to hide and provides a source for communication free of censorship. It is also important for whistleblowers and journalists within the government and large companies, giving them a safe place for sharing information without losing their anonymity. <ref name="vs">https://www.onestopit.com/a-quick-guide-to-legal-vs-illegal-activity-on-the-dark-web/</ref> | |||
===Illegal activities=== | ===Illegal activities=== | ||
With many Tor-based sites being suspended by police authorities across the globe, there is a clear danger of becoming a government target for simply visiting a dark website. | With many Tor-based sites being suspended by police authorities across the globe, there is a clear danger of becoming a government target for simply visiting a dark website. | ||
Illegal drug marketplaces like the Silk Road have been followed by police surveillance in the past. By utilizing custom software to infiltrate and analyze activity, this has allowed law officials to discover user identities of patrons. Even without actually making a purchase, there is still a chance to be watched by law enforcement which might incriminate for other activities later in life. | Illegal drug marketplaces like the Silk Road have been followed by police surveillance in the past. By utilizing custom software to infiltrate and analyze activity, this has allowed law officials to discover user identities of patrons. Even without actually making a purchase, there is still a chance to be watched by law enforcement which might incriminate for other activities later in life. <ref name="criminal">https://www.kaspersky.com/resource-center/threats/deep-web</ref> | ||
Using the dark web might put users at risk of monitoring for other types of activity as well. Evading government restrictions to explore new political ideologies can be an imprisonable offense in certain countries. China uses what is known as the “Great Firewall” to limit access to popular sites for this exact reason. The risk of visiting this type of content could lead to being placed on a watchlist or even put in jail. <ref name="criminal"/> | |||
Reports have suggested the dark web offers many illegal services, from paid assassinations to trafficking for sex and weapons. Some services like professional “hitmen” may just be scams designed to profit from gullible customers. When ordering a killer on someone and the person is still walking after the deadline, there is nothing to do. Going to the police to make a claim on a scam does not seem like a good idea. They may be taking advantage of the dark web’s reputation to trick users out of large sums of money. Also, some users on the dark web may attempt phishing scams to steal peoples identity or personal information for extortion. <ref name="criminal"/> | |||
Searching the dark web will likely give access to online marketplaces that sell everything from Netflix passwords to stolen credit card accounts. Other sites offer illegal software, prepaid debit cards, and hackers for hire. <ref name="how">https://www.csoonline.com/article/3249765/what-is-the-dark-web-how-to-access-it-and-what-youll-find.html</ref> | |||
====Black markets==== | ====Black markets==== | ||
Due to the bitcoin, the dark web has flourished. This helps the customer and the seller to have a trusted transaction while being anonymous. Nearly all dark web commerce sites conduct transactions in bitcoin. Dark web marketplaces have the same features as any e-retail operation, including reviews, shopping carts and forums. This means that sellers need to keep their good ratings, or they will not find any clients. But also, when both buyers and sellers are anonymous, the credibility of any ratings system is uncertain. When completing a transaction there is no guarantee that the items will arrive. When ordering illegal items, the package must make it through customs, making the route more difficult. | Due to the bitcoin, the dark web has flourished. This helps the customer and the seller to have a trusted transaction while being anonymous. Nearly all dark web commerce sites conduct transactions in bitcoin. Dark web marketplaces have the same features as any e-retail operation, including reviews, shopping carts and forums. This means that sellers need to keep their good ratings, or they will not find any clients. But also, when both buyers and sellers are anonymous, the credibility of any ratings system is uncertain. When completing a transaction there is no guarantee that the items will arrive. When ordering illegal items, the package must make it through customs, making the route more difficult. <ref name="how"/> | ||
One of the better-known illegal sites on the dark web was Silk Road, an online trading site that sold fake IDs, drugs, and other illegal materials, that became a booming business after its founding in 2011. The site's operator, using the pseudonym Dread Pirate Roberts, became a sort of folk hero of the dark web, offering the chance to buy illegal goods anonymously using bitcoin. It is estimated that the creator of Silk Road received over $13 million in commissions from allowing vendors to use the platform. The FBI shut down Silk Road in late 2013. The agency also arrested Ross Ulbricht, the real person behind the Dread Pirate Roberts fake name. Ulbricht is now serving life in prison without the possibility of parole. As part of the investigation, it was determined that over $1.2 billion sales had occurred involving 150,000 customers and 4000 vendors. This shows how much activity is taking place in the dark web. | One of the better-known illegal sites on the dark web was Silk Road, an online trading site that sold fake IDs, drugs, and other illegal materials, that became a booming business after its founding in 2011. The site's operator, using the pseudonym Dread Pirate Roberts, became a sort of folk hero of the dark web, offering the chance to buy illegal goods anonymously using bitcoin. It is estimated that the creator of Silk Road received over $13 million in commissions from allowing vendors to use the platform. The FBI shut down Silk Road in late 2013. The agency also arrested Ross Ulbricht, the real person behind the Dread Pirate Roberts fake name. Ulbricht is now serving life in prison without the possibility of parole. As part of the investigation, it was determined that over $1.2 billion sales had occurred involving 150,000 customers and 4000 vendors. This shows how much activity is taking place in the dark web. <ref name="isIllegal"/> | ||
Two more examples of thriving criminal enterprises on the dark web were AlphaBay and Hansa. The FBI, U.S. Drug Enforcement Agency and the Dutch National Police, along with Europol, shut down these online marketplaces in 2017. According to Europol, AlphaBay and Hansa were responsible for the trading of more than 350,000 illegal commodities. | Two more examples of thriving criminal enterprises on the dark web were AlphaBay and Hansa. The FBI, U.S. Drug Enforcement Agency and the Dutch National Police, along with Europol, shut down these online marketplaces in 2017. According to Europol, AlphaBay and Hansa were responsible for the trading of more than 350,000 illegal commodities. <ref name="isIllegal"/> | ||
The marketplaces sold illegal drugs, firearms and malware. AlphaBay hosted more than 250,000 online listings for illegal drugs and more than 100,000 listings for stolen IDs, malware, firearms and counterfeit goods. Europol estimated that $1 billion of sales were made through AlphaBay since its founding in 2014. Hansa was not quite so busy but ranked as the third-largest marketplace on the dark web as of its takedown in 2017, according to law-enforcement agencies. | The marketplaces sold illegal drugs, firearms and malware. AlphaBay hosted more than 250,000 online listings for illegal drugs and more than 100,000 listings for stolen IDs, malware, firearms and counterfeit goods. Europol estimated that $1 billion of sales were made through AlphaBay since its founding in 2014. Hansa was not quite so busy but ranked as the third-largest marketplace on the dark web as of its takedown in 2017, according to law-enforcement agencies. <ref name="isIllegal"/> | ||
====Illegal pornography==== | ====Illegal pornography==== | ||
One of the most popular type of content on the dark web is illegal pornography - child pornography. In 2015 about 80% of web traffic was related to websites that offered child pornography. A popular site for said content was Lolita City, which contained over 100 GB of child pornographic media and had around 15,000 members. | One of the most popular type of content on the dark web is illegal pornography - child pornography. In 2015 about 80% of web traffic was related to websites that offered child pornography. A popular site for said content was Lolita City, which contained over 100 GB of child pornographic media and had around 15,000 members. <ref name="arst">https://arstechnica.com/tech-policy/2015/07/feds-bust-through-huge-tor-hidden-child-porn-site-using-questionable-malware/</ref> | ||
In 2015 FBI took down a website called Playpen, which was the biggest child pornography website with over 210,000 user accounts and 50,000 images and videos. With the result of the Playpen bust, hundreds of people have been arrested in the US and more than 500 associated people overseas. | In 2015 FBI took down a website called Playpen, which was the biggest child pornography website with over 210,000 user accounts and 50,000 images and videos. With the result of the Playpen bust, hundreds of people have been arrested in the US and more than 500 associated people overseas. <ref name="prison">https://arstechnica.com/tech-policy/2017/05/creator-of-infamous-playpen-website-sentenced-to-30-years-in-prison/</ref> | ||
==Conclusion== | ==Conclusion== | ||
Revision as of 11:56, 30 April 2021
This wiki will cover the most important aspects of Tor: the free and open-source software that enables anyone to communicate anonymously on the internet. The article will contain a little about the deep, dark and surface web, why use Tor and what is for, the history of Tor, a closer look on how Tor actually works and the legal and illegal aspects of the web browser.
The three webs
The World Wide Web (WWW) consists of multiple parts named: deep, dark and surface web.
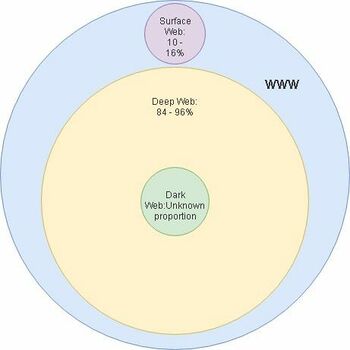
Surface web
The surface web is the easiest to explain as that is the part of the web that all of us use to browse the internet, even right now as you are reading this wiki you are browsing the surface web. The different areas of the web are defined by if they are indexed and if the user needs to authenticate himself to access the webpage. The surface web mostly consists of web pages that do not need user authentication. The web pages are indexed, meaning that a user can find the pages from using a search engine. The surface web contains about 10-16% of all of the information on the WWW. [1]
Deep web
Everything except the surface makes up the deep web part of the WWW. This means that the dark web is also a part of the deep web. Most of the deep web is inaccessible to normal search engines since the pages are not indexed or they require authentication to access. To access the deep web users need to use a special browser like Tor. Users also need to use the Hidden Wiki to get the urls for the different webpages, so the Hidden Wiki is kind of like a gateway into the deep web. The deep web contains about 84-90% of all of the information on the WWW. [1]
Dark web
And now finally, the dark web. The dark web is a part of the deep web and it’s full size is not actually known. Security experts estimate that there are about 10,000 to 100,000 active sites in the dark web at any given moment. Since the dark web is a part of the deep web it’s pages are not indexed and cannot be found by search engines. The dark web is also the part of the web where most illegal drugs, guns and human trafficking happens, but governments and the UN has also used the dark web to protect political dissidents and hunt down criminals. A great example of this is how the US government tracked down the owner of Silk Road (an underground black market primarily for drugs), Ross Ulbricht in 2013. [1]
Why use Tor
So after all of that why would you use The Onion Router (Tor)? So using Tor is similar to any other web browser, except your real IP address and any other system information is obscured when browsing the web. It also hides the user’s activity from their internet service provider.
The primary uses of Tor are:
- Bypassing censorship and surveillance
- Visiting websites anonymously
- Accessing Tor hidden services (.onion sites)
We will get into more detail about Tor and how it works later on. [1]
History
The 1990s
So, now that we have the basics covered let’s look at an overview of the history of The Onion Router (Tor). The idea of onion routing began in the mid 1990s and the developers of the project believed that internet users should have private access to an uncensored web. In the 1990s internet security was a really big issue and its ability to be used for tracking and surveillance was becoming clear. Therefore, 3 US Naval Research Lab (NRL) employees: Paul Sysverson, David Goldschlag and Mike Reed decided to create and deploy the first research designs and prototypes of onion routing. From its inception in the 1990s, onion routing relied on a decentralized network that used nodes that were operated by different entities with diverse interests and trust assumptions. Also the software needed to be free and open-source to maximize transparency and separation. [2]
The 2000s
In the early 2000s, Roger Dingledine, a MIT graduate, started working on a NRL onion routing project with Paul Syverson. Other onion routing efforts were already made, so to make this project special, they decided to call it Tor - The Onion Router. The Electronic Frontier Foundation (EFF) recognized the benefit of Tor for digital rights and began funding the project in 2004 and in 2006 the Tor Project was founded to maintain Tor’s development. In 2007, the organization began to connect to the Tor network to address censorship, such as the need to get around government firewalls, in order for its users to access the open web. Tor was mostly popular with tech-savvy people and it was hard for less technically knowledgeable people to use, so in 2005, development of tools for the Tor proxy began and in 2008, development of the Tor browser began. [2]
The 2010s
With the Tor browser complete and it being more accessible to everyday internet users, it greatly influenced the beginning of the Arab Spring in late 2010. It did not only protect people’s identity online, but it also helped access critical resources, social media and other websites which were blocked at the time. After the 2013 Snowden revelations, it became clear that the need for tools against mass surveillance would become a mainstream concern. Tor was used for Snowden’s whistleblowing and the documents posted online also assured that Tor could not be cracked. [2]
The onion router - A closer look
In order to give a clearer picture of what Tor is and how it works, this part will cover what traffic analysis is, how the onion router operates, problems related to anonymity when using Tor and what onion services are.
Traffic analysis: the art of tracking users
In order to understand Tor and it works, the term and working principles of traffic analysis must be understood.
Traffic analysis is a form of Internet surveillance used to monitor and inspect network traffic from an end device to another over a public network. This technique can let people and services listen on a network to discover the user’s source and destination traffic, leading to the tracking of personal interests and behavior, even when the connection is encrypted. This is possible due to the structure of Internet data packets: data payload, which contains the content of what is being sent over the network such as an email or an image, and a header that is used for routing. Of these two parts data payload can be encrypted, but since traffic analysis focuses on the header rather than the content of the message, it still can disclose key information about the user, such as source and destination, size of the payload, and timing. This enables unauthorized parties as well as authorized intermediaries (e.g Internet Service Providers) to view a user’s information not from the content of the data itself but from the Internet headers. Very simple forms of traffic analysis may allow a middle man to sit in between the sender and the receiver and inspect on the travelling data. [3]
Tor's working principles
The main purpose of Tor is to protect its users against traffic analysis. To do so the onion router distributes any of the user’s transactions over several nodes on the Internet, also called relays, making it impossible to link back a crossed point to a person’s information. What Tor does to obtain anonymity is sending data packets through several randomly chosen relays instead of choosing the direct route from source to destination. Using this technique no observer waiting at any of the relays can surely know where the data came from or where it is going. The circuit data takes is built incrementally one hop at a time. The user’s software encrypts all of the connections existing between relays on the network, where each of the relays knows only about the node it is taking data from and the node it is sending data to. To ensure that each hop cannot trace previous or further connections, a new pair of encryption keys is negotiated at every relay. Doing so neither an eavesdropper, nor a compromised node, nor any software, can use traffic analysis techniques to find the user’s connection source and destination. Since Tor aims for reliability it only works on TCP streams and for efficiency it uses the same circuit for connections that happen within more or less the same ten minutes. All of the later requests are assigned new circuits. [3]
Tor’s working principles can be summarized in three steps:
- The user’s Tor client obtains a list of relays from a directory server. [4]
- The user’s Tor client selects a random path from source to destination, where the path is chosen one hop at a time. [5]
- If a different site from the previous one is at a later time visited, the user’s Tor client picks a second random path. [6]
The onion services
Tor is not used just to browse the Internet anonymously, but to also access “special” services that together make up the dark web. These services are called the onion services and can only be accessed over Tor. [7]
Onion services benefit from many advantages that some other non-onion services may lack such as end-to-end encryption, end-to-end authentication, location hiding, and NAT punching (instead of using ports services punch through NAT). To achieve all this, Tor uses a special protocol called the Onion Service Protocol. Instead of consisting of a 32 or 128 bit IP address (depending on the IP version) an onion service makes use of its identity public key with a .onion extension. With the help of the Tor network the Onion Service Protocol allows a client to firstly introduce himself to the onion service and then together establish a meeting point, where the client will access the service. [7]
An onion service’s address may look like this: vww6ybal4bd7szmgncyruucpgfkqahzddi37ktceo3ah7ngmcopnpyyd.onion [7]
Onion services do not work nor act as Tor relays, while they behave as any other Tor clients. Every time an onion service needs to become available in the Tor network, it connects through relays as any other client would. This is the same for any device that wants to access an onion service. Connections from the client to the server never leave the Tor network and in contrast to a relay, an onion service never results in the user’s IP address. [8]
Anonimity problems
While Tor can be superb in protecting the transport of data, it does not solve all of the problems that might be related to anonymity, so when using it the user should pay attention to four key points.
The final part of the communication is unencrypted
Tor focuses on encrypting data moving between the user’s device and servers in and within the Tor network, leaving the final part of the connection between the exit relay and the destination unencrypted. This can make it possible for authorized and non-authorized parties to eavesdrop on traffic between the last relay and the server. The full list of Tor exit nodes is available publicly and unencrypted traffic can happen to be closely monitored. [9]
User’s traffic can be deanonymized because of timing-based statistical techniques
Timing-based statistical techniques may allow the network operator such as an ISP to determine from which computer the traffic is coming. This technique is usually hard to pull off and can also be expensive. This vulnerability may happen if both the entry relay and the exit relay exist on the same Internet Autonomous System or share the same address. [9]
The onion router will not protect the user against more complex fingerprinting methods
If a user happens to be browsing a website with JavaScript enabled, the attacker can determine the identity of the person browsing by his mouse movements. Mouse movements can be used to correlate a Tor browsing session with a non-Tor browsing session. [9]
Tor disposes of bugs that can be exploited
Even though Tor includes a good exploit protection, it still can be exploited due to security related bugs. In order to reduce the possibility of being exploited, a Tor user should always follow some safety guidelines. When using Tor the user is recommended to not log into usual accounts such as Gmail, to not follow unique browsing patterns, to turn the browser’s security to the max level (disables JavaScript on all sites), to use the HTTPS Everywhere extension, and never use BitTorrent over Tor. [9]
Legal and illegal activities in Tor
The dark web has gained a reputation of being illegal, a place where criminals operate. Dark web itself is not actually illegal. There are social media sites, blogs and forums like on the regular web. What is illegal is some of the activity that occurs on the dark web. There are sites that sell illegal drugs, firearms and distribute child pornography.
When browsing the dark web, users need to be careful because visiting certain sites or purchasing certain items through the dark web is illegal.
Legal activities
Since social media and forums are not illegal, they are also legal in the dark web. Users will not be committing anything criminal if they use the dark web to participate in forums or to read hidden blog posts. Users have to be careful because visiting certain sites or purchasing certain items through the dark web is illegal. There is a change that participating in certain forums is illegal, especially if the forum has posts about threats, hate speech or is inciting and encouraging criminal behaviour. [10]
Using the dark web itself is not illegal. Many people prefer to use it to keep their personal data safe while doing normal things, as in the regular web, like sending emails, chatting on social media, and browsing forums. Since Google and Bing might sell personal data, the dark web has its own search engines. These alternatives will keep people's data private, which makes them a better option for those who want to keep their personal information to themselves.[10]
Dark web also has its own social media sites like Blackbook and Torbook. These sites let you create a completely anonymous profile. More and more legitimate companies are making themselves available on the dark web (e.g Facebook). [10]
Dark web is a way out for people living in places where the regime is not that allowing. People can safely access information that their government tries to hide and provides a source for communication free of censorship. It is also important for whistleblowers and journalists within the government and large companies, giving them a safe place for sharing information without losing their anonymity. [11]
Illegal activities
With many Tor-based sites being suspended by police authorities across the globe, there is a clear danger of becoming a government target for simply visiting a dark website.
Illegal drug marketplaces like the Silk Road have been followed by police surveillance in the past. By utilizing custom software to infiltrate and analyze activity, this has allowed law officials to discover user identities of patrons. Even without actually making a purchase, there is still a chance to be watched by law enforcement which might incriminate for other activities later in life. [12]
Using the dark web might put users at risk of monitoring for other types of activity as well. Evading government restrictions to explore new political ideologies can be an imprisonable offense in certain countries. China uses what is known as the “Great Firewall” to limit access to popular sites for this exact reason. The risk of visiting this type of content could lead to being placed on a watchlist or even put in jail. [12]
Reports have suggested the dark web offers many illegal services, from paid assassinations to trafficking for sex and weapons. Some services like professional “hitmen” may just be scams designed to profit from gullible customers. When ordering a killer on someone and the person is still walking after the deadline, there is nothing to do. Going to the police to make a claim on a scam does not seem like a good idea. They may be taking advantage of the dark web’s reputation to trick users out of large sums of money. Also, some users on the dark web may attempt phishing scams to steal peoples identity or personal information for extortion. [12]
Searching the dark web will likely give access to online marketplaces that sell everything from Netflix passwords to stolen credit card accounts. Other sites offer illegal software, prepaid debit cards, and hackers for hire. [13]
Black markets
Due to the bitcoin, the dark web has flourished. This helps the customer and the seller to have a trusted transaction while being anonymous. Nearly all dark web commerce sites conduct transactions in bitcoin. Dark web marketplaces have the same features as any e-retail operation, including reviews, shopping carts and forums. This means that sellers need to keep their good ratings, or they will not find any clients. But also, when both buyers and sellers are anonymous, the credibility of any ratings system is uncertain. When completing a transaction there is no guarantee that the items will arrive. When ordering illegal items, the package must make it through customs, making the route more difficult. [13]
One of the better-known illegal sites on the dark web was Silk Road, an online trading site that sold fake IDs, drugs, and other illegal materials, that became a booming business after its founding in 2011. The site's operator, using the pseudonym Dread Pirate Roberts, became a sort of folk hero of the dark web, offering the chance to buy illegal goods anonymously using bitcoin. It is estimated that the creator of Silk Road received over $13 million in commissions from allowing vendors to use the platform. The FBI shut down Silk Road in late 2013. The agency also arrested Ross Ulbricht, the real person behind the Dread Pirate Roberts fake name. Ulbricht is now serving life in prison without the possibility of parole. As part of the investigation, it was determined that over $1.2 billion sales had occurred involving 150,000 customers and 4000 vendors. This shows how much activity is taking place in the dark web. [10]
Two more examples of thriving criminal enterprises on the dark web were AlphaBay and Hansa. The FBI, U.S. Drug Enforcement Agency and the Dutch National Police, along with Europol, shut down these online marketplaces in 2017. According to Europol, AlphaBay and Hansa were responsible for the trading of more than 350,000 illegal commodities. [10]
The marketplaces sold illegal drugs, firearms and malware. AlphaBay hosted more than 250,000 online listings for illegal drugs and more than 100,000 listings for stolen IDs, malware, firearms and counterfeit goods. Europol estimated that $1 billion of sales were made through AlphaBay since its founding in 2014. Hansa was not quite so busy but ranked as the third-largest marketplace on the dark web as of its takedown in 2017, according to law-enforcement agencies. [10]
Illegal pornography
One of the most popular type of content on the dark web is illegal pornography - child pornography. In 2015 about 80% of web traffic was related to websites that offered child pornography. A popular site for said content was Lolita City, which contained over 100 GB of child pornographic media and had around 15,000 members. [14]
In 2015 FBI took down a website called Playpen, which was the biggest child pornography website with over 210,000 user accounts and 50,000 images and videos. With the result of the Playpen bust, hundreds of people have been arrested in the US and more than 500 associated people overseas. [15]
Conclusion
Onion routing and The Onion Router have come a long way in a couple of decades - many journalists, cyber criminals, law enforcement and other people who want or need to publish or find information without the fear of censorship use Tor as their helpful tool, bringing together the legal and illegal sides of the dark web with a technologically advanced web browser.
References
- ↑ 1.0 1.1 1.2 1.3 1.4 https://resources.infosecinstitute.com/topic/what-is-the-difference-between-the-surface-web-tjahe-deep-web-and-the-dark-web/
- ↑ 2.0 2.1 2.2 https://www.torproject.org/about/history/
- ↑ 3.0 3.1 https://2019.www.torproject.org/about/overview.html.en
Cite error: Invalid
<ref>tag; name "work" defined multiple times with different content - ↑ https://2019.www.torproject.org/images/htw1.png
- ↑ https://2019.www.torproject.org/images/htw2.png
- ↑ https://2019.www.torproject.org/images/htw3.png
- ↑ 7.0 7.1 7.2 https://community.torproject.org/onion-services/overview/
- ↑ https://community.torproject.org/onion-services/talk/
- ↑ 9.0 9.1 9.2 9.3 https://cybernews.com/privacy/what-is-tor-and-how-does-it-work/
- ↑ 10.0 10.1 10.2 10.3 10.4 10.5 https://us.norton.com/internetsecurity-privacy-is-the-dark-web-illegal.html
- ↑ https://www.onestopit.com/a-quick-guide-to-legal-vs-illegal-activity-on-the-dark-web/
- ↑ 12.0 12.1 12.2 https://www.kaspersky.com/resource-center/threats/deep-web
- ↑ 13.0 13.1 https://www.csoonline.com/article/3249765/what-is-the-dark-web-how-to-access-it-and-what-youll-find.html
- ↑ https://arstechnica.com/tech-policy/2015/07/feds-bust-through-huge-tor-hidden-child-porn-site-using-questionable-malware/
- ↑ https://arstechnica.com/tech-policy/2017/05/creator-of-infamous-playpen-website-sentenced-to-30-years-in-prison/