User:Eocakovs: Difference between revisions
| (28 intermediate revisions by 3 users not shown) | |||
| Line 58: | Line 58: | ||
! Threats | ! Threats | ||
|- | |- | ||
| Innovative - no | | Innovative - no direct competitors | ||
| No brand recognition | | No brand recognition | ||
| Globally extending | | Globally extending | ||
| Larger company might sprint past with a similar program | | Larger company might sprint past with a similar program | ||
|- | |- | ||
| Strong team - well | | Strong team - well organised and motivated | ||
| Small company not a lot of financial backup | | Small company, not a lot of financial backup | ||
| Expand the team for faster development | | Expand the team for faster development | ||
| Sustainable financial backing | | Sustainable financial backing | ||
| Line 71: | Line 71: | ||
| Development slow due to the size of the company | | Development slow due to the size of the company | ||
| Targeting industries | | Targeting industries | ||
| Customer | | Customer skepticism - might not want to give access to scan their computer | ||
|- | |- | ||
| User-friendly interface | | User-friendly interface | ||
| Line 91: | Line 91: | ||
====Short Information System Description==== | ====Short Information System Description==== | ||
Information System will provide Windows OS users with detailed information on their installed packages and applications. Provided information will include trustworthiness / rating / availability / checksum / developer details of the application. System will incentivize users and developers to submit descriptions of applications, which would go through a review process before publication. Companies can become verified by us through a paid application verification process thereby granting "trust-ability" to these applications and their developers. Users can subscribe to a live-scanning service which will notify them when any installed packages are compromised or need to be updated. | Information System will provide Windows OS users with detailed information on their installed packages and applications. Provided information will include trustworthiness / rating / availability / checksum / developer | ||
details of the application. System will incentivize users and developers to submit descriptions of applications, which would go through a review process before publication. Companies can become verified by us | |||
through a paid application verification process thereby granting "trust-ability" to these applications and their developers. Users can subscribe to a live-scanning service which will notify them when any installed packages | |||
are compromised or need to be updated. | |||
==Requirements== | ==Requirements== | ||
| Line 121: | Line 127: | ||
==User Stories== | ==User Stories== | ||
* | * As a user I need to find specific information on an installed application, so I enter my name into the search bar and press the search-button. | ||
* | * As a user I find an application, select it and press the "view detailed information"-button. | ||
* | * As a user I don't see any specific details about an application so I press "request additional information"-button. | ||
* | * As a user I look through provided information because I want to remove the application and thus press the "uninstall"-button, a confirmation dialogue appears and I confirm my decision. | ||
* | * As a user I want to find possible similar applications so I press "similar apps"-button. | ||
* | * As a premium user I see a notification press it which opens up a tab with an active analysis of host system. | ||
* | * As a non-premium user I want to get premium-features, so I switch to the premium-features section which displays features and payment information. | ||
* | * As a user I select a preferred amount and payment method from premium-features section which opens up an external browser with preferred payment method's website. | ||
* | * As a user I want to change how the application updates, I open the update options from the settings menu and select the "ask-for-confirmation-before-update" method. | ||
* | * As a user I want to install a program and check whether the developer is verified or not so I search for the verification signature in the application details. | ||
* | * As a user I want to leave feedback on a specific application so I click the "leave feedback" button in the application information details tab which opens up a text-box, I enter feedback and press the submit button. | ||
====Use-Case High Level Overview==== | ====Use-Case High Level Overview==== | ||
[[File:High-lvl-overview-3.png]] | [[File:High-lvl-overview-3.png]] | ||
==Data Flow Diagrams== | ==Data Flow Diagrams== | ||
| Line 164: | Line 169: | ||
| User | | User | ||
| E-mail | | E-mail | ||
| Submit requests / Access Premium Features / Inspect Installed Applications / Give Feedback / Submit Descriptions on Applications | | Submit requests / Access Premium Features / Inspect Installed Applications / | ||
Give Feedback / Submit Descriptions on Applications | |||
| Verified / Unverified / Registered / Unregistered / Premium / Standard | | Verified / Unverified / Registered / Unregistered / Premium / Standard | ||
|- | |- | ||
| Line 206: | Line 212: | ||
1. As a customer I want to order premium features. | 1. As a customer I want to order premium features. | ||
Standard User wants to buy premium features, clicks on the premium feature section, enters required client details in fields, clicks on make payment button, redirected to payment site where payment finalization is taken care of, verification email sent, order details saved in database. | Standard User wants to buy premium features, clicks on the premium feature section, enters required client details in fields, clicks on make payment button, redirected to payment site where payment | ||
finalization is taken care of, verification email sent, order details saved in database. | |||
2. As a Premium User I want to see alternative applications | 2. As a Premium User I want to see alternative applications | ||
| Line 213: | Line 221: | ||
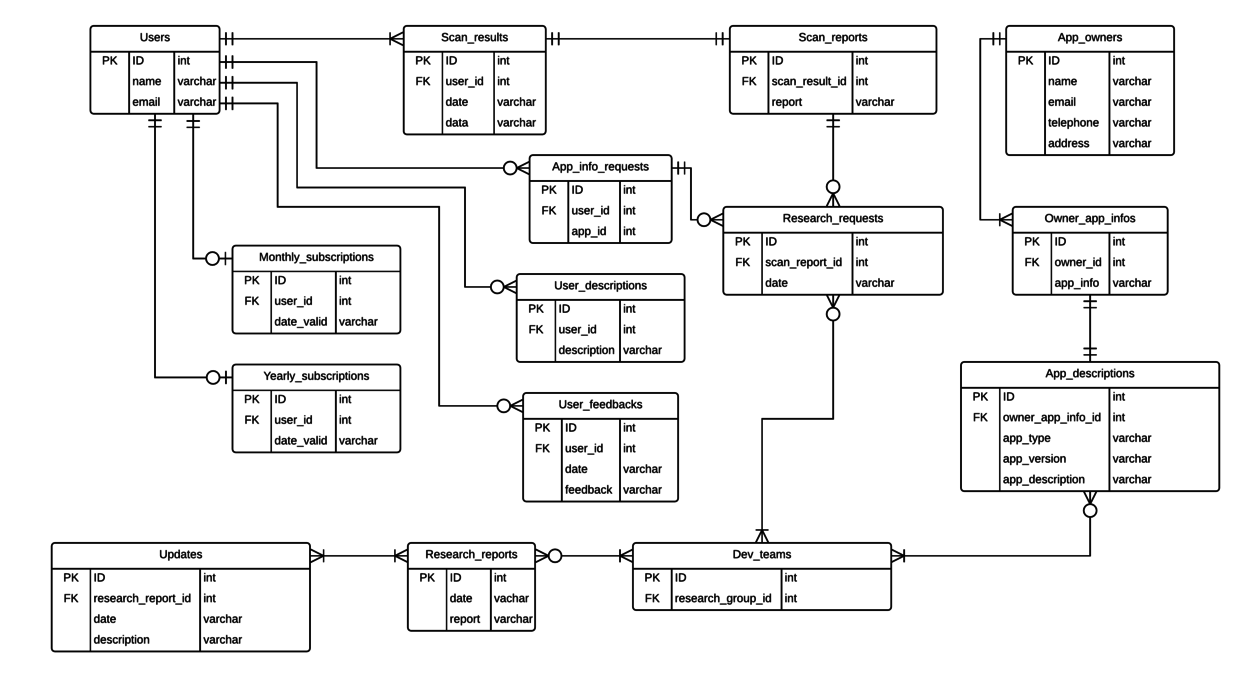
===ERD=== | ===ERD=== | ||
[[File: | [[File:ERD_WPE1.png |1240px|]] | ||
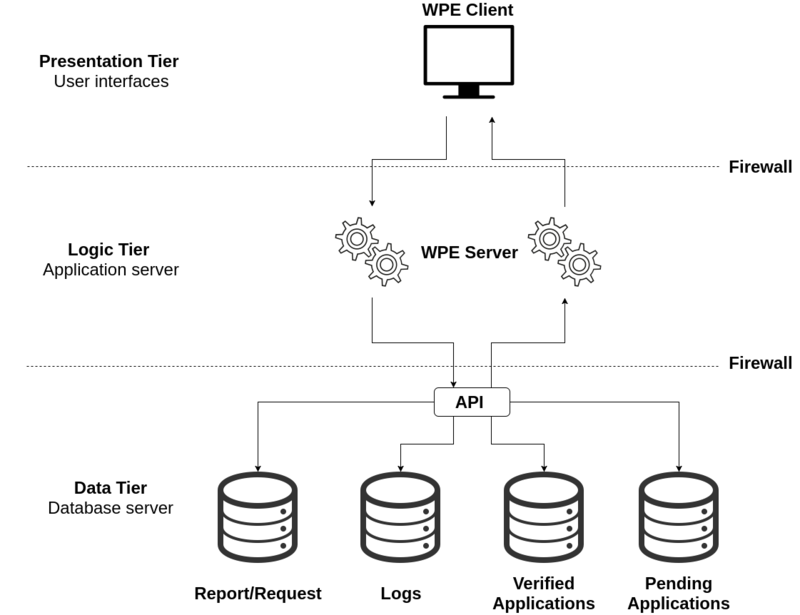
==Architectural Model== | ==Architectural Model== | ||
[[File:Architectural_model_WPE1.png |800px|]] | |||
==UI - User Experience== | ==UI - User Experience== | ||
The main goal is to create an application that would be easily operated by the end user. | The main goal is to create an application that would be easily operated by the end user. | ||
Since the application is mainly meant for the average home user, it cannot require any specific knowledge about computers, or computer related terminology. | Since the application is mainly meant for the average home user, it cannot require any specific knowledge about computers, | ||
or computer related terminology. | |||
All aformentioned points (additionally see non-functional requirements) need to be kept in mind when designing the UI. | All aformentioned points (additionally see non-functional requirements) need to be kept in mind when designing the UI. | ||
| Line 244: | Line 255: | ||
* Unforseeable constraints we have to deal with using Agile Approach | * Unforseeable constraints we have to deal with using Agile Approach | ||
==Risks and Countermeasures== | ==Risks and Countermeasures== | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| Line 274: | Line 285: | ||
* Create intuitive user experience | * Create intuitive user experience | ||
|} | |} | ||
In this section we identify the major risks and countermeasures to these risks. Implementing a proper standard for service management like ISO-20000 or similar frameworks concerning risk management | |||
(assessment / mitigation) are an essential part of this process. | |||
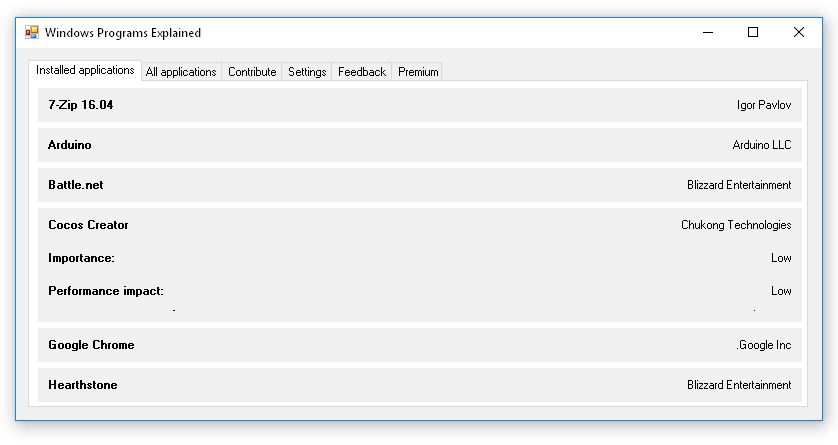
==Prototype== | |||
[[File:Prototype_wpe.JPG]] | |||
* Currently application dependencies are not displayed in our prototype, however this feature is accounted for considering our full implementation. In future prototypes this should also be implemented. | |||
==Recommendations and Conclusion== | ==Recommendations and Conclusion== | ||
Our group identified a need for an information system that would explain to users applications that either are or could be installed. However after careful analysis we have to come to the conclusion that the application will become obsolete due to an increasing push by Microsoft for Windows 10+ and their native Store. For this application to have a future it should integrate with the native Windows store. Therefore we do not proceed to full development and await further action by Microsoft until project becomes viable. | Our group identified a need for an information system that would explain to users applications that either are or could be installed. However after careful analysis we have to come to the conclusion that | ||
the application will become obsolete due to an increasing push by Microsoft for Windows 10+ and their native Store. For this application to have a future it should integrate with the native Windows store. | |||
Therefore we do not proceed to full development and await further action by Microsoft until project becomes viable. | |||
It is suitable for agile since we can identify Minimum Viable Product requirements | It is suitable for agile since we can identify Minimum Viable Product requirements | ||
but due to constantly evolving application market and Windows platform, | but due to constantly evolving application market and Windows platform, | ||
we cannot create a full analysis which lists all requirements from the beginning. | we cannot create a full analysis which lists all | ||
requirements from the beginning. | |||
Latest revision as of 20:42, 26 May 2017
I701 - Information System Analysis
Group Project
Members
- Ardi Vaba
- Pascal Tietjen
- Peep Kuulme
- Nika Ptskialadze
- Erik Ocakovskih
- Frank Korving
Organization
WPE (Windows Programs Explained)
Daily Operations:
We are a software development company. Our current major project consists of providing and supporting an application with simple interface to analyze currently installed programs on the system.
Example Information Systems:
Accounting Information System
Customer Support Information System
Sales Information System
Developer Daily-Work Information System
Transaction Processing Information System
Value Chain Analysis
Primary Activities:
Direct
- Software Development [Getting the software to working state]
- Software Delivery [Getting the product to the market]
- Sales [Selling a product to current customers and new customer aquisition]
- Marketing [Providing product information to target group]
Indirect
- Scheduling [Optimizing work and workload assignments]
- Support / Service [Maintenance of existing software and customer assistance]
- Marketing [Customer Management]
Quality Assurance
- Testing [Functionality verification of the developed working software]
Support Activities:
Direct
- Infrastructure [Providing Legal, Administrative and Accounting support]
- Procurement [Acquisition of external services]
Indirect
- HR Management [Human Resource Management]
IT SWOT
| Strength | Weakness | Opportunities | Threats |
|---|---|---|---|
| Innovative - no direct competitors | No brand recognition | Globally extending | Larger company might sprint past with a similar program |
| Strong team - well organised and motivated | Small company, not a lot of financial backup | Expand the team for faster development | Sustainable financial backing |
| Competitively priced | Development slow due to the size of the company | Targeting industries | Customer skepticism - might not want to give access to scan their computer |
| User-friendly interface | Organic growth - no outside funding |
Improvements
Problems:
- Application Information
- Due to lack of program information / Methods of updating
- Trustworthiness / Unknown Sources
- Customer Perception of the Products [Solution should provide: Transparency for customers / Awareness of Application]
- Market access / interactions
Short Information System Description
Information System will provide Windows OS users with detailed information on their installed packages and applications. Provided information will include trustworthiness / rating / availability / checksum / developer
details of the application. System will incentivize users and developers to submit descriptions of applications, which would go through a review process before publication. Companies can become verified by us
through a paid application verification process thereby granting "trust-ability" to these applications and their developers. Users can subscribe to a live-scanning service which will notify them when any installed packages
are compromised or need to be updated.
Requirements
Functional
'Users'
- Users should be able to subscribe to paid services
- Users should be able to scan their computer and check for installed programs
- Users should be able to gain information on these installed programs through us (WPE)
- Users should be able to delete the application
- Users should be able to request suggestions on alternative
- Users should be able to search for similar applications
- Users should be able to search for any application
- Users should be able to submit their rating/opinion to be reviewed by us
'Companies'
- Companies should be able to apply for verification
- Companies should be able to submit their own description after verification
Non-Functional
- Application shall be operable in offline environment
- All the application details shall be as transparent to user as possible
- Every aspect of the software shall be testable
- User experience of the software shall be as responsive as possible
- User privacy shall be completely protected
- Documentation of software shall be easily understood by new developers
- Backend infrastructure should be scalable
- Software shall be safe to operate by non technical people
- Application shall be intuitively operable by 70 year old with minimal technical knowledge
User Stories
- As a user I need to find specific information on an installed application, so I enter my name into the search bar and press the search-button.
- As a user I find an application, select it and press the "view detailed information"-button.
- As a user I don't see any specific details about an application so I press "request additional information"-button.
- As a user I look through provided information because I want to remove the application and thus press the "uninstall"-button, a confirmation dialogue appears and I confirm my decision.
- As a user I want to find possible similar applications so I press "similar apps"-button.
- As a premium user I see a notification press it which opens up a tab with an active analysis of host system.
- As a non-premium user I want to get premium-features, so I switch to the premium-features section which displays features and payment information.
- As a user I select a preferred amount and payment method from premium-features section which opens up an external browser with preferred payment method's website.
- As a user I want to change how the application updates, I open the update options from the settings menu and select the "ask-for-confirmation-before-update" method.
- As a user I want to install a program and check whether the developer is verified or not so I search for the verification signature in the application details.
- As a user I want to leave feedback on a specific application so I click the "leave feedback" button in the application information details tab which opens up a text-box, I enter feedback and press the submit button.
Use-Case High Level Overview
Data Flow Diagrams
Context diagram
Lvl0-DFD
Lvl1-DFD
Object Oriented Approach
Objects
| Object | Class | Identifier | Actions | States |
|---|---|---|---|---|
| Bob | User | Submit requests / Access Premium Features / Inspect Installed Applications /
Give Feedback / Submit Descriptions on Applications |
Verified / Unverified / Registered / Unregistered / Premium / Standard | |
| Notepad | Application | Name + Version | Text Editing | Installed / Uninstalled / Running |
| Peep | Development Team | Company ID | Verify Application Descriptions and Issue updates | Working / On Holiday |
| Microsoft | Application Owners | Company Name | Submit detailed on owned Application | Verified/Unverified/Bankrupt |
| Request detail on Notepad | Request | Unique Request ID | Query internal App database / Query Windows / Contact server | Pending / Idle / Denied / Accepted / Finalized |
| Report on Notepad | Report | Unique Report ID | Return application detailed information | Delivery Origin/Successful/Failed |
Actors
- Customer -> Obtain detailed app information / Pay subscription / (Un-)Install application / Find applications
- Developer -> Develop features / write code / Analyze / Design
- Application Owner -> Get verified / Provide information on Application(s) / Gain users
Scenario
1. As a customer I want to order premium features.
Standard User wants to buy premium features, clicks on the premium feature section, enters required client details in fields, clicks on make payment button, redirected to payment site where payment
finalization is taken care of, verification email sent, order details saved in database.
2. As a Premium User I want to see alternative applications
Premium User wants to see alternative applications, selects the relevant application, clicks on the search for alternatives button, gets a list of alternatives application.
ERD
Architectural Model
UI - User Experience
The main goal is to create an application that would be easily operated by the end user. Since the application is mainly meant for the average home user, it cannot require any specific knowledge about computers,
or computer related terminology. All aformentioned points (additionally see non-functional requirements) need to be kept in mind when designing the UI.
Measurable Key Performance Indicators
- Success rate (how many of the user requests come back with a positive responce. i.e. - if a user requests for additional app info, can we provide that information, or will the user get back nothing).
- Time on task (e.g. how long does it take for the user to upgrade from standard user to premium user. Does it take too much time, and is the process too complicated).
- Amount of installations.
- Time user spends in app (active time).
User feedback
- In-app feedback tab (option to select how satisfied the user is with the program in a 1-10 point scale, and a comment box)
- Post service survey. For instance after a user upgrades from standard user to premium user, an email will be sent out with questions about the process and an option to leave feedback and suggestions.
- Email survey. An email will be sent out with a user satisfaction survey, asking users to rate different parts of the process.
- In-app survey before uninstalling/downgrading the WPE (With in-app monetary incentive).
Constraints
- Competitors (like 'Revo uninstaller' / Windows native Store)
- Investors / Venture Capital
- Performance (DB / Network / Program Design)
- Balance of team (developers vs testers)
- Time
- Unforseeable constraints we have to deal with using Agile Approach
Risks and Countermeasures
| Hackers and data Breaches | Hardware failure | Power outages | Force majeures | Software Issues | User errors |
|---|---|---|---|---|---|
|
|
|
|
|
|
In this section we identify the major risks and countermeasures to these risks. Implementing a proper standard for service management like ISO-20000 or similar frameworks concerning risk management
(assessment / mitigation) are an essential part of this process.
Prototype
- Currently application dependencies are not displayed in our prototype, however this feature is accounted for considering our full implementation. In future prototypes this should also be implemented.
Recommendations and Conclusion
Our group identified a need for an information system that would explain to users applications that either are or could be installed. However after careful analysis we have to come to the conclusion that
the application will become obsolete due to an increasing push by Microsoft for Windows 10+ and their native Store. For this application to have a future it should integrate with the native Windows store.
Therefore we do not proceed to full development and await further action by Microsoft until project becomes viable.
It is suitable for agile since we can identify Minimum Viable Product requirements
but due to constantly evolving application market and Windows platform,
we cannot create a full analysis which lists all
requirements from the beginning.