5G technology and it's development in Estonia: Difference between revisions
| (20 intermediate revisions by 4 users not shown) | |||
| Line 32: | Line 32: | ||
</ref> | </ref> | ||
'''MEC''' | |||
5G architecture has an important element named Multi-Access Edge Computing (MEC) which task is to shift traffic and services from a centralized cloud to the edge of the network and closer to the customer. It does not send all data to a cloud for processing, but the network edge analyzes, processes, and stores the data instead of that. This is beneficial because data collection that happens closer to the customer diminishes latency and provides real-time performance to high-bandwidth applications. Although this technology may be avoided or substituted, it provides necessary effectiveness for the work of 5G because MEC has special characteristics like low latency, high bandwidth and real-time access to RAN information <ref>What is multi-access edge computing?. Available at: https://www.juniper.net/us/en/research-topics/what-is-multi-access-edge-computing.html | 5G architecture has an important element named Multi-Access Edge Computing (MEC) which task is to shift traffic and services from a centralized cloud to the edge of the network and closer to the customer. It does not send all data to a cloud for processing, but the network edge analyzes, processes, and stores the data instead of that. This is beneficial because data collection that happens closer to the customer diminishes latency and provides real-time performance to high-bandwidth applications. Although this technology may be avoided or substituted, it provides necessary effectiveness for the work of 5G because MEC has special characteristics like low latency, high bandwidth and real-time access to RAN information <ref>What is multi-access edge computing?. Available at: https://www.juniper.net/us/en/research-topics/what-is-multi-access-edge-computing.html | ||
- Accessed 25-04-2022.</ref> | - Accessed 25-04-2022.</ref> | ||
| Line 39: | Line 41: | ||
Some time ago fast data exchange speed was only possible to reach with cable connections, but with cellular network expansion in Estonia people's growing data needs can be fulfilled with 5G technologies. One of the main technological improvements achieved in 5G is new radio frequencies, Beamforming, multiple-input and multiple-output (MIMO) technologies. 5G technology offers a very low latency rate, the delay between the sending and receiving information. While 4G was capable of having a speed of 200 milliseconds, with 5G technology 1 millisecond can be achieved. <ref>5G technology and networks (speed, use cases, rollout). Available at: https://www.thalesgroup.com/en/markets/digital-identity-and-security/mobile/inspired/5G - Accessed 25-04-2022. </ref> | Some time ago fast data exchange speed was only possible to reach with cable connections, but with cellular network expansion in Estonia people's growing data needs can be fulfilled with 5G technologies. One of the main technological improvements achieved in 5G is new radio frequencies, Beamforming, multiple-input and multiple-output (MIMO) technologies. 5G technology offers a very low latency rate, the delay between the sending and receiving information. While 4G was capable of having a speed of 200 milliseconds, with 5G technology 1 millisecond can be achieved. <ref>5G technology and networks (speed, use cases, rollout). Available at: https://www.thalesgroup.com/en/markets/digital-identity-and-security/mobile/inspired/5G - Accessed 25-04-2022. </ref> | ||
'''5G NR''' | |||
New Radio (NR) is a new technology invented to replace the 4G wireless communications standard with 5G. It features wireless communication by enhancing electromagnetic radiation spectrum efficiency for mobile broadband and its diversity of spectrum ranging from several hundred kilohertz to millimetre waves is designed for different types of transmissions <ref>5G New Radio (NR). Available at: https://www.techtarget.com/whatis/definition/5G-New-Radio-NR - Accessed 25-04-2022.</ref>. The general purpose of 5G is to use standards and protocols for mobile telecommunications to describe how 5G NR edge devices and 5G NR network infrastructure wirelessly transmit data and communicate<ref>What is 5G NR (New Radio)?. Available at: https://www.sierrawireless.com/iot-blog/what-is-5g-nr/ - Accessed 25-04-2022.</ref>. Edge devices manage the entry point to networks and include routers, gateways, multiplexers or routing switches. Network infrastructure refers to mostly Radio Access Network devices. New Radio may use the same band of the spectrum as LTE because of Dynamic Spectrum Sharing (DSS) technology. That makes NR capable of being rolled out without shutting down LTE or other networks that may support existing LTE smartphones or IoT devices<ref>How Private LTE can help with construction optimisation. Available at: https://www.iotcentral.io/blog/Connectivity - Accessed 25-04-2022.</ref>. | New Radio (NR) is a new technology invented to replace the 4G wireless communications standard with 5G. It features wireless communication by enhancing electromagnetic radiation spectrum efficiency for mobile broadband and its diversity of spectrum ranging from several hundred kilohertz to millimetre waves is designed for different types of transmissions <ref>5G New Radio (NR). Available at: https://www.techtarget.com/whatis/definition/5G-New-Radio-NR - Accessed 25-04-2022.</ref>. The general purpose of 5G is to use standards and protocols for mobile telecommunications to describe how 5G NR edge devices and 5G NR network infrastructure wirelessly transmit data and communicate<ref>What is 5G NR (New Radio)?. Available at: https://www.sierrawireless.com/iot-blog/what-is-5g-nr/ - Accessed 25-04-2022.</ref>. Edge devices manage the entry point to networks and include routers, gateways, multiplexers or routing switches. Network infrastructure refers to mostly Radio Access Network devices. New Radio may use the same band of the spectrum as LTE because of Dynamic Spectrum Sharing (DSS) technology. That makes NR capable of being rolled out without shutting down LTE or other networks that may support existing LTE smartphones or IoT devices<ref>How Private LTE can help with construction optimisation. Available at: https://www.iotcentral.io/blog/Connectivity - Accessed 25-04-2022.</ref>. | ||
[[File:Beam forming.jpg|350px|thumb|right|baseline|Photo: Beamforming schematic representation]] | [[File:Beam forming.jpg|350px|thumb|right|baseline|Photo: Beamforming schematic representation<ref>What is Beamforming?. Available at: https://www.everythingrf.com/community/what-is-beamforming - Accessed 25-04-2022.</ref>]] | ||
In Estonia, Ericsson Spectrum Sharing solutions with Telia are using both LTE and New Radio units to expand 5G technology influence. At present Telia has intentions to expand its low-band 5G commercial services with additional improved nationwide 5G coverage, including mid- and high-bands<ref>Telia and Ericsson switch on Estonia’s first commercial 5G network. Available at: https://www.ericsson.com/en/news/2020/11/estonia-switches-on-5g - Accessed 25-04-2022.</ref>. Since 2016 the partnership of Estonia and Sweden to develop 5G technologies has made 5G available on Estonian territory. On December 20, 2018, the first 5G network was opened at Tallinn University of Technology (TalTech) and is used now for innovation and research purposes. University has the goals to improve 5G network solutions in the country and create an environment where companies and start-ups can develop and test new products and services together with the university<ref>Estonia’s first 5G network opens. Available at: https://estonianworld.com/technology/estonias-first-5g-network-opens/ - Accessed 25-04-2022.</ref> With the usage of this technology, TalTech University has launched a self-driving car, which may interact with the surrounding environment at high-speed communication thanks to 5G<ref>ISEAUTO. Available at: https://iseauto.taltech.ee/en/ - Accessed 25-04-2022.</ref>. The autonomous car must react fast in case of vehicle-to-vehicle and vehicle-to-infrastructure communications. 5G NR provides a suitable environment for that with extremely low latency. | In Estonia, Ericsson Spectrum Sharing solutions with Telia are using both LTE and New Radio units to expand 5G technology influence. At present Telia has intentions to expand its low-band 5G commercial services with additional improved nationwide 5G coverage, including mid- and high-bands<ref>Telia and Ericsson switch on Estonia’s first commercial 5G network. Available at: https://www.ericsson.com/en/news/2020/11/estonia-switches-on-5g - Accessed 25-04-2022.</ref>. Since 2016 the partnership of Estonia and Sweden to develop 5G technologies has made 5G available on Estonian territory. On December 20, 2018, the first 5G network was opened at Tallinn University of Technology (TalTech) and is used now for innovation and research purposes. University has the goals to improve 5G network solutions in the country and create an environment where companies and start-ups can develop and test new products and services together with the university<ref>Estonia’s first 5G network opens. Available at: https://estonianworld.com/technology/estonias-first-5g-network-opens/ - Accessed 25-04-2022.</ref> With the usage of this technology, TalTech University has launched a self-driving car, which may interact with the surrounding environment at high-speed communication thanks to 5G<ref>ISEAUTO. Available at: https://iseauto.taltech.ee/en/ - Accessed 25-04-2022.</ref>. The autonomous car must react fast in case of vehicle-to-vehicle and vehicle-to-infrastructure communications. 5G NR provides a suitable environment for that with extremely low latency. | ||
'''Beamforming''' | |||
Beamforming is a method used in 5G antennas signal processing to filter the reception and transmission of radio signals in different directions. Beamforming antennas are made to send a stronger signal in a specified direction while others have low-quality signals or their absence<ref>What is Beamforming?. Available at: https://www.everythingrf.com/community/what-is-beamforming - Accessed 25-04-2022.</ref>. As a result, the connection between devices can be done faster and data transmission speed is higher. | Beamforming is a method used in 5G antennas signal processing to filter the reception and transmission of radio signals in different directions. Beamforming antennas are made to send a stronger signal in a specified direction while others have low-quality signals or their absence<ref>What is Beamforming?. Available at: https://www.everythingrf.com/community/what-is-beamforming - Accessed 25-04-2022.</ref>. As a result, the connection between devices can be done faster and data transmission speed is higher. | ||
| Line 75: | Line 79: | ||
*'''Authentication:''' The user equipment must authenticate the network identifier through key authentication. | *'''Authentication:''' The user equipment must authenticate the network identifier through key authentication. | ||
*'''Confidentiality of user and signaling data:''' User equipment can support confidentiality of data through cipher algorithms for encryption. User equipment must use the NEA0 (Null ciphering algorithm), 128-NEA1 (128-bit SNOW 3G based algorithm), 128-NEA2 (128-bit AES based algorithm), and 128-NEA3 (128-bit ZUC based algorithm) cipher algorithms. | *'''Confidentiality of user and signaling data:''' User equipment can support confidentiality of data through cipher algorithms for encryption. User equipment must use the NEA0 (Null ciphering algorithm), 128-NEA1 (128-bit SNOW 3G based algorithm), 128-NEA2 (128-bit AES based algorithm), and 128-NEA3 (128-bit ZUC based algorithm) cipher algorithms.<ref>5G Security Standard. Available at: https://www.etsi.org/deliver/etsi_ts/133500_133599/133501/15.01.00_60/ts_133501v150100p.pdf - Accessed 25-04-2022.</ref><ref>5G Security Standards. Available at: https://www.ericsson.com/en/standardization/network-security - Accessed 25-04-2022.</ref> | ||
*'''Integrity of user and signaling data:''' The cipher algorithms NIA0, 128-NIA1, and 128-NIA2 are used for integrity protection. User equipment must support integrity protection and replay protection of user data between it and the network nodes. Integrity protection is done to ensure a program runs properly and prevent data disruption or change by malicious entities. An optional element of integrity of user data is integrity protection of the data between the user equipment and the network node. It is optional because it increases the processing on the user equipment and network node. | *'''Integrity of user and signaling data:''' The cipher algorithms NIA0, 128-NIA1, and 128-NIA2 are used for integrity protection. User equipment must support integrity protection and replay protection of user data between it and the network nodes. Integrity protection is done to ensure a program runs properly and prevent data disruption or change by malicious entities. An optional element of integrity of user data is integrity protection of the data between the user equipment and the network node. It is optional because it increases the processing on the user equipment and network node. | ||
| Line 93: | Line 97: | ||
*'''Access network authorization:''' Access network must be authorized by the serving network to provide services to user equipment. | *'''Access network authorization:''' Access network must be authorized by the serving network to provide services to user equipment. | ||
*'''Confidentiality of user and signaling data:''' The 5G gNB must support the encryption of user data in transit and for radio resource control (RRC) signaling. The gNB should activate the user data encryption process based on security policy. Such encryption algorithms are NEA0, 128-NEA1, 128-NEA2, 128-NEA3. | *'''Confidentiality of user and signaling data:''' The 5G gNB must support the encryption of user data in transit and for radio resource control (RRC) signaling. The gNB should activate the user data encryption process based on security policy. Such encryption algorithms are NEA0, 128-NEA1, 128-NEA2, 128-NEA3.<ref>What is 5G Security? Available at: https://cybersecurity.att.com/blogs/security-essentials/what-is-5g-security - Accessed 25-04-2022.</ref> | ||
*'''Integrity of user and signaling data:''' The nodes, like the user equipment, must support integrity protection and replay protection of user data going between the user equipment and the gNB. The encryption algorithms are the same as the ones used by the user equipment for integrity protection. However, NIA0 isn’t recommended for integrity protection since it does not encrypt and therefore adds unnecessary overhead and increases load on user equipment and network node. 5G network nodes must also support integrity protection and replay protection of RRC. For context, RRC exists in the control plane and controls configuration between radio interface Layer 2 and Layer 3.<ref>Integrity of user and signaling data Available at: https://www.ericsson.com/en/security/a-guide-to-5g-network-security#securityarchitecture - Accessed 25-04-2022.</ref> | |||
*'''Setup and configuration requirements:''' When operations and management (O&M) systems setup and configure gNBs must be authenticated and authorized by registration authority and a certification authority (RA/CA) so attackers won’t be able to modify the gNB settings and software configurations. Communication between the O&M systems and the gNB must be confidentially-, integrity-, and replay-protected from unauthorized entities. Additionally, software and data changes must be authorized before installation and use, the software and data itself must be authorized, and transferring the software to the gNB must be confidential and have integrity protection. The bootup process must be done in a secure environment to protect its sensitive elements. | *'''Setup and configuration requirements:''' When operations and management (O&M) systems setup and configure gNBs must be authenticated and authorized by registration authority and a certification authority (RA/CA) so attackers won’t be able to modify the gNB settings and software configurations. Communication between the O&M systems and the gNB must be confidentially-, integrity-, and replay-protected from unauthorized entities. Additionally, software and data changes must be authorized before installation and use, the software and data itself must be authorized, and transferring the software to the gNB must be confidential and have integrity protection. The bootup process must be done in a secure environment to protect its sensitive elements. | ||
| Line 103: | Line 108: | ||
*'''Handling user plane and control plane data requirements:''' The requirements for key management are similar to those for handling user plane and control plane data for the gNB. Unencrypted data must be protected from physical attacks, placed in a physically secure location, and the unencrypted data is stored and processed in a secure environment. | *'''Handling user plane and control plane data requirements:''' The requirements for key management are similar to those for handling user plane and control plane data for the gNB. Unencrypted data must be protected from physical attacks, placed in a physically secure location, and the unencrypted data is stored and processed in a secure environment. | ||
*'''Requirements for a secure environment:''' The secure environment that all of this unencrypted data is running in has requirements as well. It must support secure storage through, for example, long-term cryptographic secrets and vital configuration data. The environment must be able to execute sensitive functions and protocols that use long-term secrets. Executive sensitive functions include encryption and decryption of user data. An example of a protocol using long-term secrets is an authentication protocol. This part of the 3GPP 5G security standard requires the secure environment to have integrity. Finally, only those with authorized access can access the secure environment. | *'''Requirements for a secure environment:''' The secure environment that all of this unencrypted data is running in has requirements as well. It must support secure storage through, for example, long-term cryptographic secrets and vital configuration data. The environment must be able to execute sensitive functions and protocols that use long-term secrets. Executive sensitive functions include encryption and decryption of user data. An example of a protocol using long-term secrets is an authentication protocol. This part of the 3GPP 5G security standard requires the secure environment to have integrity. Finally, only those with authorized access can access the secure environment.<ref>5G Security. Available at: https://www.sdxcentral.com/5g/definitions/5g-security-standards/ - Accessed 25-04-2022.</ref> | ||
<ref>5G Security. Available at: https://www.sdxcentral.com/5g/definitions/5g-security-standards/ | |||
==Use cases== | ==Use cases== | ||
| Line 116: | Line 118: | ||
[[File:Arvr.jpg|450px|thumb|right|Photo: AR and VR <ref>Photo: AR and VR Available at: https://www.kaspersky.com/resource-center/threats/security-and-privacy-risks-of-ar-and-vr - Accessed 27-04-2022.</ref>]] | [[File:Arvr.jpg|450px|thumb|right|Photo: AR and VR <ref>Photo: AR and VR Available at: https://www.kaspersky.com/resource-center/threats/security-and-privacy-risks-of-ar-and-vr - Accessed 27-04-2022.</ref>]] | ||
===Enhanced Mobile Broadband (eMBB)=== | ===Enhanced Mobile Broadband (eMBB)=== | ||
| Line 126: | Line 129: | ||
* Support for large numbers of subscribers in a single location | * Support for large numbers of subscribers in a single location | ||
[[File:Self-driving-car.jpg|350px|thumb|left|Photo: TTÜ Self-driving car <ref>Photo: TTÜ Self-driving car Available at: https://iot.ttu.ee/projects/iseauto/ - Accessed 27-04-2022.</ref>]] | [[File:Self-driving-car.jpg|350px|thumb|left|Photo: TTÜ Self-driving car <ref>Photo: TTÜ Self-driving car Available at: https://iot.ttu.ee/projects/iseauto/ - Accessed 27-04-2022.</ref>]] | ||
===Ultra-Reliable and Low-Latency Communications (URLLC)=== | ===Ultra-Reliable and Low-Latency Communications (URLLC)=== | ||
| Line 135: | Line 139: | ||
* Remote control of industrial processes | * Remote control of industrial processes | ||
[[File:Smartcity.webp|450px|thumb|right|Photo: Smart city <ref>Photo: Smart city Available at: https://www.5gradar.com/features/what-is-5g-these-use-cases-reveal-all - Accessed 27-04-2022.</ref>]] | [[File:Smartcity.webp|450px|thumb|right|Photo: Smart city <ref>Photo: Smart city Available at: https://www.5gradar.com/features/what-is-5g-these-use-cases-reveal-all - Accessed 27-04-2022.</ref>]] | ||
===Massive Machine-Type Communications (mMTC)=== | ===Massive Machine-Type Communications (mMTC)=== | ||
| Line 150: | Line 155: | ||
The previous generations of mobile networks are 1G, 2G, 3G, and 4G. | The previous generations of mobile networks are 1G, 2G, 3G, and 4G. | ||
[[File:Evolution5G.png|600px|thumb|right|Photo: 5G evolution]] | [[File:Evolution5G.png|600px|thumb|right|Photo: 5G evolution <ref>Photo: 5G evolution Available at: https://www.digitalrealty.com/blog/5g-how-we-got-here-and-its-impact-on-data-center-infrastructure - Accessed 27-04-2022.</ref>]] | ||
===First generation - 1G=== | ===First generation - 1G=== | ||
| Line 194: | Line 199: | ||
* telcos must bring 5G service packages to market.<ref>5G in Estonia. Available at: https://5geestis.ee/ - Accessed 25-04-2022.</ref> | * telcos must bring 5G service packages to market.<ref>5G in Estonia. Available at: https://5geestis.ee/ - Accessed 25-04-2022.</ref> | ||
[[File:5G_Station.jpg| | [[File:5G_Station.jpg|350px|thumb|left|Photo: 5G base station<ref>Photo: 5G base station https://digi.geenius.ee/app/uploads/sites/7/2020/04/cfd565de8e74abc925e2dba97eedc7c9-770x513.jpg</ref>]] | ||
At first, the technological revolution in Estonia was slowed down, in Estonia, frequency auctions were postponed, and a number of operators decided to approach the construction of 5G networks without haste - this was due to the Covid-19 pandemic, which had a very impact on the development of 5G networks. | At first, the technological revolution in Estonia was slowed down, in Estonia, frequency auctions were postponed, and a number of operators decided to approach the construction of 5G networks without haste - this was due to the Covid-19 pandemic, which had a very impact on the development of 5G networks. | ||
Nevertheless, on November 10, 2020, Telia opened the first 5G network in Estonia. Telia decided to smartly launch 5G services and started offering 5G on existing 4G frequencies using Ericsson DSS (Dynamic Spectrum Sharing) technology. In other words, we dynamically use the 4G radio frequency band to serve 5G network customers.<ref>Only three companies will receive 5G mobile licenses in Estonia. Available at: https://rus.err.ee/1608438122/licenzii-na-mobilnuju-svjaz-5g-v-jestonii-poluchat-tolko-tri-firmy - Accessed 25-04-2022.</ref> | Nevertheless, on November 10, 2020, Telia opened the first 5G network in Estonia. Telia decided to smartly launch 5G services and started offering 5G on existing 4G frequencies using Ericsson DSS (Dynamic Spectrum Sharing) technology. In other words, we dynamically use the 4G radio frequency band to serve 5G network customers.<ref>Only three companies will receive 5G mobile licenses in Estonia. Available at: https://rus.err.ee/1608438122/licenzii-na-mobilnuju-svjaz-5g-v-jestonii-poluchat-tolko-tri-firmy - Accessed 25-04-2022.</ref> | ||
| Line 202: | Line 207: | ||
So far (04.05.2022), four bids have been submitted in the 5G license auction, the Consumer Protection and Technical Regulation Authority (TTJA) said. According to TTJA forecasts, the licenses submitted for the competition will be issued in June this year, after which telecommunications companies will be able to start building 5G networks in Estonia.<ref>5G competition draws four bids. Available at: https://news.err.ee/1608554782/5g-competition-draws-four-bids - Accessed 25-04-2022.</ref> | So far (04.05.2022), four bids have been submitted in the 5G license auction, the Consumer Protection and Technical Regulation Authority (TTJA) said. According to TTJA forecasts, the licenses submitted for the competition will be issued in June this year, after which telecommunications companies will be able to start building 5G networks in Estonia.<ref>5G competition draws four bids. Available at: https://news.err.ee/1608554782/5g-competition-draws-four-bids - Accessed 25-04-2022.</ref> | ||
The development of 5G infrastructure in Estonia is in full swing, although it has not yet been decided which 3 companies will develop this technology in Estonia, the largest telecommunications companies have already begun active preparation and implementation. 5G technology surpasses its 4G predecessor in many ways, offering up to 10 times faster connection speeds, up to 10 times lower latency, up to 100 times more IoT devices served, and up to 90% lower power consumption, which should lead to a new idea of the Internet.<ref>Only three companies will receive 5G mobile licenses in Estonia. Available at: https://rus.err.ee/1608438122/licenzii-na-mobilnuju-svjaz-5g-v-jestonii-poluchat-tolko-tri-firmy - Accessed 25-04-2022.</ref> | The development of 5G infrastructure in Estonia is in full swing, although it has not yet been decided which 3 companies will develop this technology in Estonia, the largest telecommunications companies have already begun active preparation and implementation. 5G technology surpasses its 4G predecessor in many ways, offering up to 10 times faster connection speeds, up to 10 times lower latency, up to 100 times more IoT devices served, and up to 90% lower power consumption, which should lead to a new idea of the Internet. | ||
<ref>Only three companies will receive 5G mobile licenses in Estonia. Available at: https://rus.err.ee/1608438122/licenzii-na-mobilnuju-svjaz-5g-v-jestonii-poluchat-tolko-tri-firmy - Accessed 25-04-2022.</ref> | |||
==The future is not far off== | ==The future is not far off== | ||
Latest revision as of 17:11, 29 April 2022
5G technology and it's development in Estonia
Overview
Mobile networks, which have a 40-year history that parallels the Internet’s, have undergone significant change. The first two generations supported voice and then text, with 3G defining the transition to broadband access, supporting data rates measured in hundreds of kilobits-per-second. 4G supporting data rates typically measured in the few megabits-per-second. Today, the industry is at 5G, with the promise of a tenfold increase in data rates. But 5G is about much more than increased bandwidth. 5G represents a fundamental rearchitecting of the access network in a way that leverages several key technology trends and sets it on a path to enable much greater innovation. In the same way that 3G defined the transition from voice to broadband, 5G’s promise is primarily about the transition from a single access service (broadband connectivity) to a richer collection of edge services and devices. [1]

What is 5G?
5G (acronym of 5th Generation) indicates the set of fifth-generation mobile telephony technologies, which allow much higher performance and speed than current 4G technology. 5G enables a new kind of network that is designed to connect virtually everyone and everything together including machines, objects, and devices like smartphones, smartwatches and who knows what else… 5G wireless technology is meant to deliver higher multi-Gbps peak data speeds, ultra low latency, more reliability, massive network capacity, increased availability, and a more uniform user experience to more users. Beyond speed improvement, the technology is expected to unleash a massive 5G IoT (Internet of Things) ecosystem where networks can serve communication needs for billions of connected devices. [3] 5G networks are designed to account for such diverse needs. They can provide superfast access with minimal latency. At the same time, they retain the flexibility to provision slower speeds with lower device resource requirements.
How does 5G work?
Wireless communications systems use radio frequencies (also known as spectrum) to carry information through the air. 5G operates in the same way, but uses higher radio frequencies that are less cluttered. This allows for it to carry more information at a much faster rate. These higher bands are called 'millimeter waves' (mmwaves). They were previously unused but have been opened up for licensing by regulators. They had been largely untouched by the public as the equipment to use them was largely inaccessible and expensive. While higher bands are faster at carrying information, there can be problems with sending over large distances. They are easily blocked by physical objects such as trees and buildings. In order to circumvent this challenge, 5G will utilise multiple input and output antennae to boost signals and capacity across the wireless network. [4]
Architecture
5G is a wireless cellular network whose architecture can be generally explained as the main user 5G terminal and autonomous radio access technologies (RAT) in devices like Bluetooth, Wi-Fi, or GSM, which are connected to that terminal. Smartphones, IoT or applications connect to 5G with the help of RAT that has an IP link to access the internet. [5] It was designed like this to keep the data transmission under control and maintain the correct routing of IP packets related to different application connections. If the previous mobile networks aimed only to provide efficient and secure connection service, 5G must also be flexible to support many technologies with different types of applications. Therefore, 5G uses another architecture with Radio Access Networks (RAN) as part of a mobile network. It is the component of a wireless mobile network which connects devices like smartphones or tablets to the cloud.[6] It is made when information is being sent from end-user devices to a RAN’s transceivers through radio waves.
3GPP supplies the architecture of a 5G network with complete specifications covering telecommunication technologies like RAN, core transport networks and service capabilities Additional design improvements like modularity, reusability and self-containment are taken into account and added to the design for a 5G network architecture.[7]
MEC
5G architecture has an important element named Multi-Access Edge Computing (MEC) which task is to shift traffic and services from a centralized cloud to the edge of the network and closer to the customer. It does not send all data to a cloud for processing, but the network edge analyzes, processes, and stores the data instead of that. This is beneficial because data collection that happens closer to the customer diminishes latency and provides real-time performance to high-bandwidth applications. Although this technology may be avoided or substituted, it provides necessary effectiveness for the work of 5G because MEC has special characteristics like low latency, high bandwidth and real-time access to RAN information [8]
Technology
Some time ago fast data exchange speed was only possible to reach with cable connections, but with cellular network expansion in Estonia people's growing data needs can be fulfilled with 5G technologies. One of the main technological improvements achieved in 5G is new radio frequencies, Beamforming, multiple-input and multiple-output (MIMO) technologies. 5G technology offers a very low latency rate, the delay between the sending and receiving information. While 4G was capable of having a speed of 200 milliseconds, with 5G technology 1 millisecond can be achieved. [9]
5G NR
New Radio (NR) is a new technology invented to replace the 4G wireless communications standard with 5G. It features wireless communication by enhancing electromagnetic radiation spectrum efficiency for mobile broadband and its diversity of spectrum ranging from several hundred kilohertz to millimetre waves is designed for different types of transmissions [10]. The general purpose of 5G is to use standards and protocols for mobile telecommunications to describe how 5G NR edge devices and 5G NR network infrastructure wirelessly transmit data and communicate[11]. Edge devices manage the entry point to networks and include routers, gateways, multiplexers or routing switches. Network infrastructure refers to mostly Radio Access Network devices. New Radio may use the same band of the spectrum as LTE because of Dynamic Spectrum Sharing (DSS) technology. That makes NR capable of being rolled out without shutting down LTE or other networks that may support existing LTE smartphones or IoT devices[12].
In Estonia, Ericsson Spectrum Sharing solutions with Telia are using both LTE and New Radio units to expand 5G technology influence. At present Telia has intentions to expand its low-band 5G commercial services with additional improved nationwide 5G coverage, including mid- and high-bands[14]. Since 2016 the partnership of Estonia and Sweden to develop 5G technologies has made 5G available on Estonian territory. On December 20, 2018, the first 5G network was opened at Tallinn University of Technology (TalTech) and is used now for innovation and research purposes. University has the goals to improve 5G network solutions in the country and create an environment where companies and start-ups can develop and test new products and services together with the university[15] With the usage of this technology, TalTech University has launched a self-driving car, which may interact with the surrounding environment at high-speed communication thanks to 5G[16]. The autonomous car must react fast in case of vehicle-to-vehicle and vehicle-to-infrastructure communications. 5G NR provides a suitable environment for that with extremely low latency.
Beamforming
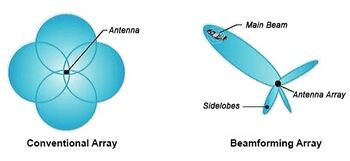
Beamforming is a method used in 5G antennas signal processing to filter the reception and transmission of radio signals in different directions. Beamforming antennas are made to send a stronger signal in a specified direction while others have low-quality signals or their absence[17]. As a result, the connection between devices can be done faster and data transmission speed is higher.
In Estonia, beamforming is also used for wireless communications to increase the signal in a specified direction. However, in some cases, beamforming may shorten the coverage area and possibilities of wireless network expansion in some directions. In addition, some laboratory findings state that beamformed waves may have unpredictable movement as the signal levels and patterns interact as a closed-loop system. Although millimetre waves have low penetration depth into the body, Estonian authorities say that more people are concerned about the health risks that 5G may bring[18].
5G Infrastructure
There are two options for 5G network infrastructure, non-standalone and standalone.
Non-standalone infrastructure partly relys on existing 4G LTE infrastructure and core network. This means while only LTE services are supported, the network has the capabilities offered by 5G NewRadio, like lower latency.
Standalone infrastructure uses its own cloud-native and doesn't rely on LTE services. It is expected that network carriers will arrive at a standalone infrastructure after moving through an NSA infrastructure. Using an NSA approach allows carriers to offer 5G-like experiences while they build out the needed physical infrastructure of a 5G network.
The main hardware components of 5G are small cell and RAN towers.
Small cell take up less real place and are used in device-dense areas. Small cell antennas use millimeter wave frequencys, which helps to increase amount of information carried, but reduces effective range. To increase reach beamforming is used.
The 5G RAN is used in less densely populated areas, where it is not needed to transmiti big amounts of data. Lower-band radio frequencies, used by 5G RAN, carry less information , but cover greater areas.
The 5G Core Network infrastructure is being redesigned to efficiently integrate with Internet and cloud-based 5G services, and include distributed servers across the network to reduce latency.[19][20]
5G Security
User Equipment Security Features
- Authentication: The user equipment must authenticate the network identifier through key authentication.
- Confidentiality of user and signaling data: User equipment can support confidentiality of data through cipher algorithms for encryption. User equipment must use the NEA0 (Null ciphering algorithm), 128-NEA1 (128-bit SNOW 3G based algorithm), 128-NEA2 (128-bit AES based algorithm), and 128-NEA3 (128-bit ZUC based algorithm) cipher algorithms.[21][22]
- Integrity of user and signaling data: The cipher algorithms NIA0, 128-NIA1, and 128-NIA2 are used for integrity protection. User equipment must support integrity protection and replay protection of user data between it and the network nodes. Integrity protection is done to ensure a program runs properly and prevent data disruption or change by malicious entities. An optional element of integrity of user data is integrity protection of the data between the user equipment and the network node. It is optional because it increases the processing on the user equipment and network node.
- Secure storage and processing of subscription credentials: These credentials and their long-term keys are to be integrity protected within the user equipment with a tamper-resistant piece of hardware. The long-term keys are to never be available unencrypted outside of the tamper-resistant hardware. Any authentication algorithm that uses subscription credentials must be run in this hardware.
- Subscriber privacy: In order to meet the 3GPP 5G security standard, user equipment must support what 3GPP calls the globally unique temporary UE identity (GUTI). The GUTI provides an unambiguous identification of the user equipment but does not reveal the UE or the user’s permanent identity in the 5G network. The subscription permanent identifier (SUPI) must not be transferred unencrypted over next-generation radio access networks. The universal subscriber identity module is where the home network public key, protection scheme identifier, home network (is a network the user is primarily subscribed to) public key identifier, and the subscription concealed identifier (SUCI), are all stored. The SUCI in turn contains the SUPI. The 5G network provider is in charge of subscriber privacy as well as provisioning and updating the home network public key and that key’s identifier. In the 3GPP 5G security standard, a home network refers to the network the user is primarily subscribed to.
Network Security Features
- Subscription authentication: The network is required to authenticate the SUPI when authenticating and performing key agreements with the user equipment.
- User equipment authorization: The serving network has to authorize the user equipment by using the subscription profile obtained from the home network. Essentially serving network should provide connection to home network for user. User equipment authorization depends on the SUPI being authenticated.
- Serving network authorization by the home network: The user equipment must be assured it is connected to a serving network authorized by the home network.
- Access network authorization: Access network must be authorized by the serving network to provide services to user equipment.
- Confidentiality of user and signaling data: The 5G gNB must support the encryption of user data in transit and for radio resource control (RRC) signaling. The gNB should activate the user data encryption process based on security policy. Such encryption algorithms are NEA0, 128-NEA1, 128-NEA2, 128-NEA3.[23]
- Integrity of user and signaling data: The nodes, like the user equipment, must support integrity protection and replay protection of user data going between the user equipment and the gNB. The encryption algorithms are the same as the ones used by the user equipment for integrity protection. However, NIA0 isn’t recommended for integrity protection since it does not encrypt and therefore adds unnecessary overhead and increases load on user equipment and network node. 5G network nodes must also support integrity protection and replay protection of RRC. For context, RRC exists in the control plane and controls configuration between radio interface Layer 2 and Layer 3.[24]
- Setup and configuration requirements: When operations and management (O&M) systems setup and configure gNBs must be authenticated and authorized by registration authority and a certification authority (RA/CA) so attackers won’t be able to modify the gNB settings and software configurations. Communication between the O&M systems and the gNB must be confidentially-, integrity-, and replay-protected from unauthorized entities. Additionally, software and data changes must be authorized before installation and use, the software and data itself must be authorized, and transferring the software to the gNB must be confidential and have integrity protection. The bootup process must be done in a secure environment to protect its sensitive elements.
- Requirements for key management inside the gNB: There is a need to protect the different elements of encryption keys provided by the 5G network core to the gNBs. The elements are the subscription-specific session keying material, which holds long term keys used for security association setup and authentication purposes. The first element of this requirement is that any part of a gNB deployment storing or processing unencrypted keys must be protected from physical attacks. If it isn’t protected physically then the gNB is placed in a physically secure location.
- Handling user plane and control plane data requirements: The requirements for key management are similar to those for handling user plane and control plane data for the gNB. Unencrypted data must be protected from physical attacks, placed in a physically secure location, and the unencrypted data is stored and processed in a secure environment.
- Requirements for a secure environment: The secure environment that all of this unencrypted data is running in has requirements as well. It must support secure storage through, for example, long-term cryptographic secrets and vital configuration data. The environment must be able to execute sensitive functions and protocols that use long-term secrets. Executive sensitive functions include encryption and decryption of user data. An example of a protocol using long-term secrets is an authentication protocol. This part of the 3GPP 5G security standard requires the secure environment to have integrity. Finally, only those with authorized access can access the secure environment.[25]
Use cases
5G technology will not only usher in a new era of improved network performance and speed but also new connected experiences for users. [26]
5G promises to be the standard for communication between billions of devices. At the moment, these devices and associated services fall into three main 5G use cases:

Enhanced Mobile Broadband (eMBB)
eMBB is a natural evolution to existing 4G networks that will provide faster data rates and therefore a better user experience than current mobile broadband services. However, it will go beyond merely faster downloads to provide an increasingly seamless user experience that will eclipse the quality of service we currently enjoy from fixed broadband technologies. Ultimately it will enable 360o video streaming, truly immersive VR and AR applications and much more.[28]
Examples:
- High-speed Internet access
- HD video streaming
- AR and VR services
- Support for large numbers of subscribers in a single location

Ultra-Reliable and Low-Latency Communications (URLLC)
Quick and consistent data transmission is attractive to manufacturing, transport, healthcare, and other industries. URLLC services have strict requirements regarding network reliability and quality, prioritizing low latency, reliability, and low probability of error. In particular, URLLC will give mobile connectivity to mission-critical applications that have been discussed for many years but are just now coming to fruition.[30] URLLS is one of the fourth industrial revolution’s technological drivers, alongside other technologies such as artificial intelligence, genetic engineering, 3D printing, quantum computing, the Internet of Things, and robotics. [31]
Examples:
- Self-driving vehicles
- Telemedicine, including remote diagnostics and robotic surgery
- Remote control of industrial processes
Massive Machine-Type Communications (mMTC)
mMTC supports connection densities of up to one million devices per square kilometre. This is over ten times higher than 4G LTE network capability. With this ability, 5G can provide the infrastructure needed to support huge networks of cellular-connected sensors. The mMTC service area is designed for massive IoT deployments using large numbers of low-power devices to regularly transmit small amounts of data. These IoT devices need to have a long battery life, potentially for up to 10 years.[33]
Examples:
- Smart City systems
- Transport and logistics
- Production and staff monitoring
- Other scenarios with exceptionally high concentrations of IoT sensors
What are the differences between the previous generations of mobile networks and 5G?
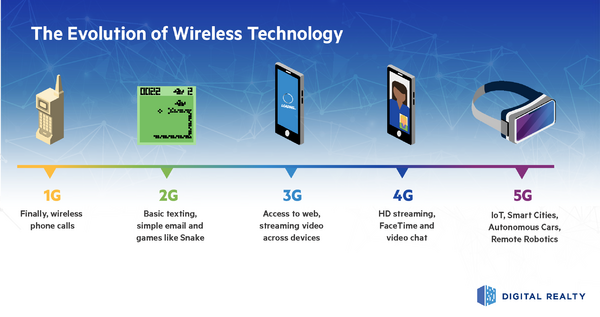
The previous generations of mobile networks are 1G, 2G, 3G, and 4G.
First generation - 1G
1980s: 1G delivered analog voice—the ability to use a phone in a car, or away from home
Second generation - 2G
Early 1990s: 2G introduced digital voice (e.g. CDMA- Code Division Multiple Access). short-messaging layer—pieces of which can still be seen in today’s texting features
Third generation - 3G
Early 2000s: 3G brought mobile data (e.g. CDMA2000). The move to 3G provided the core network speeds needed to launch smartphones.
Fourth generation - 4G LTE
2010s: 4G LTE ushered in the era of mobile broadband. And 4G, with its high data-transfer rates, gave us video with minimal buffering and gave rise to many of the connected devices and services that we rely on and enjoy today.
Now, people are beginning to experience 5G and its transformative capabilities. [36]
1G, 2G, 3G, and 4G all led to 5G, and now, people are beginning to experience 5G and its transformative capabilities. [37]
While earlier generations of cellular technology (such as 4G LTE) focused on ensuring connectivity, 5G takes connectivity to the next level by delivering connected experiences from the cloud to clients. 5G networks are virtualized and software-driven, and they exploit cloud technologies. [38] 5G is a unified, more capable air interface. It has been designed with an extended capacity to enable next-generation user experiences, empower new deployment models and deliver new services. [39]
Controversial moments
Is 5G Really Powerful Radiation?
This is a fairly popular conspiracy theory. Let's look at her key message: is 5G radiation really so powerful that it can cause any disease or harm health in any way?

To this question, would answer this way all electromagnetic radiation, from radio waves to X-rays, according to its energy (not power, these are different things) is divided into two types: ionizing, that is, capable of destroying molecules and turning them into ions, and non-ionizing - incapable on this. All 5G bands belong to the non-ionizing type of radiation, such radiation can only heat the living tissue through which it passes, but does not harm its molecules in any way and, as a result, does not affect the chemical processes in living organisms.[41]

As a result, studies on the possible, hypothetical, potential and imaginary effects of non-ionizing radiation on living cells are constantly being conducted, but they have never yet given an unambiguous reproducible effect and have not presented a mechanism that would explain this effect. In short, today there is no reason to believe that 5G or any other radio emission can bring any significant harm to human health.[43]
The 5G network spreads the coronavirus and leads to malignant tumors and other diseases. Could this be true?
Perhaps a repetition, but still. 5G refers to non-ionizing radiation, which cannot harm humans. Only ionizing radiation is dangerous: it penetrates the body and destroys cells, causes mutations and malignant tumors. For example, such radiation appears during the explosion of an atomic bomb.[44]
In conclusion, to stop the spread of similar myths in the future, experts need to consistently and clearly correct common misconceptions. And better transparency from both government bodies and researchers could prevent misinformation from ever taking root.[45]
5G development in Estonia
Let's start from the very beginning, for the development of new generation networks in Estonia, the following aspects must be fulfilled:
- the state should allocate telecommunications enterprises the frequencies necessary for 5G;
- in turn, telecommunications enterprises must build a 5G network (radio and core network);
- working 5G terminals (smartphones and routers) should appear on the client device market;
- telcos must bring 5G service packages to market.[46]

At first, the technological revolution in Estonia was slowed down, in Estonia, frequency auctions were postponed, and a number of operators decided to approach the construction of 5G networks without haste - this was due to the Covid-19 pandemic, which had a very impact on the development of 5G networks. Nevertheless, on November 10, 2020, Telia opened the first 5G network in Estonia. Telia decided to smartly launch 5G services and started offering 5G on existing 4G frequencies using Ericsson DSS (Dynamic Spectrum Sharing) technology. In other words, we dynamically use the 4G radio frequency band to serve 5G network customers.[48]
On 16.12.2021, the government approved a decree on the security of communication networks, on the basis of which the Ministry of Economic Affairs and Communications will tender three licenses for the construction of fifth generation (5G) mobile networks in Estonia in February. The use of frequencies in the range of 3410-3800 megahertz will be divided into three equal parts with an interval of 130 megahertz. The starting price of each license is 1,597,000 euros.[49]
So far (04.05.2022), four bids have been submitted in the 5G license auction, the Consumer Protection and Technical Regulation Authority (TTJA) said. According to TTJA forecasts, the licenses submitted for the competition will be issued in June this year, after which telecommunications companies will be able to start building 5G networks in Estonia.[50]
The development of 5G infrastructure in Estonia is in full swing, although it has not yet been decided which 3 companies will develop this technology in Estonia, the largest telecommunications companies have already begun active preparation and implementation. 5G technology surpasses its 4G predecessor in many ways, offering up to 10 times faster connection speeds, up to 10 times lower latency, up to 100 times more IoT devices served, and up to 90% lower power consumption, which should lead to a new idea of the Internet. [51]
The future is not far off
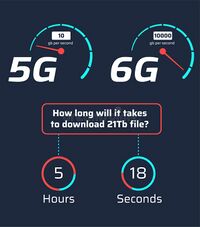
6G is the sixth generation mobile communication standard, which is distinguished by the highest possible data transfer rate. It exists only as a concept. 6G networks will be able to transfer data hundreds of times faster than 5G: data transfer rates can reach one terabit per second.
Another important difference from previous standards will be the transition from the gigahertz to the terahertz range. Thanks to this, 6G will expand coverage areas by several hundred times. For example, communication will be possible underwater, at great heights and even in space. At the same time, transmitters and other network equipment will have low power consumption. According to preliminary forecasts, the 6G standard will spread around the 2030s.[53]
6G technologies make it possible to operate in real time with such volumes of data and at such a speed that it will be comparable to the work of the human brain.
The sixth generation of communication will provide new opportunities for creating a connection between the brain and the computer. One example of such a development is an electronic chip that is implanted into the brains of people with disorders in the central nervous system. Such technologies will require three orders of magnitude higher data rates compared to 5G networks.
Thanks to 6G, quadcopters, which are used to monitor forest fires and search for missing people, will be able to immediately report their coordinates (if there is network coverage in places where the drones are located). Now all coordinates are recorded on the memory card. Significant changes are also expected in healthcare. It is planned that 6G will allow the practice of remote surgery and streamline healthcare workflows.
6G networks will be able to provide high-quality connection when a user moves in space at speeds up to 1,000 km/h, both when traveling by high-speed train and when traveling by plane.[54]
References
- ↑ Chapter 1: Introduction. Available at: https://5g.systemsapproach.org/intro.html - Accessed 25-04-2022.
- ↑ Photo: 5G Available at: https://sunburstafrica.co.za/nokia-and-tpg-telecom-deploy-asia-pacifics-first-live-5g-femtocell/ - Accessed 27-04-2022.
- ↑ Everything you need to know about 5G. Available at: https://www.qualcomm.com/5g/what-is-5g - Accessed 25-04-2022.
- ↑ How Does 5G Work? Available at: https://www.twi-global.com/technical-knowledge/faqs/what-is-5g#WhoInventedtheFifthGenerationNetwork - Accessed 25-04-2022.
- ↑ 5G - Architecture. Available at: https://www.tutorialspoint.com/5g/5g_architecture.htm - Accessed 25-04-2022.
- ↑ What is a radio access network (RAN)?. Available at: https://www.redhat.com/en/topics/5g-networks/what-is-radio-access-network - Accessed 25-04-2022.
- ↑ What is a radio access network (RAN)?. Available at: https://www.redhat.com/en/topics/5g-networks/what-is-radio-access-network - Accessed 25-04-2022.
- ↑ What is multi-access edge computing?. Available at: https://www.juniper.net/us/en/research-topics/what-is-multi-access-edge-computing.html - Accessed 25-04-2022.
- ↑ 5G technology and networks (speed, use cases, rollout). Available at: https://www.thalesgroup.com/en/markets/digital-identity-and-security/mobile/inspired/5G - Accessed 25-04-2022.
- ↑ 5G New Radio (NR). Available at: https://www.techtarget.com/whatis/definition/5G-New-Radio-NR - Accessed 25-04-2022.
- ↑ What is 5G NR (New Radio)?. Available at: https://www.sierrawireless.com/iot-blog/what-is-5g-nr/ - Accessed 25-04-2022.
- ↑ How Private LTE can help with construction optimisation. Available at: https://www.iotcentral.io/blog/Connectivity - Accessed 25-04-2022.
- ↑ What is Beamforming?. Available at: https://www.everythingrf.com/community/what-is-beamforming - Accessed 25-04-2022.
- ↑ Telia and Ericsson switch on Estonia’s first commercial 5G network. Available at: https://www.ericsson.com/en/news/2020/11/estonia-switches-on-5g - Accessed 25-04-2022.
- ↑ Estonia’s first 5G network opens. Available at: https://estonianworld.com/technology/estonias-first-5g-network-opens/ - Accessed 25-04-2022.
- ↑ ISEAUTO. Available at: https://iseauto.taltech.ee/en/ - Accessed 25-04-2022.
- ↑ What is Beamforming?. Available at: https://www.everythingrf.com/community/what-is-beamforming - Accessed 25-04-2022.
- ↑ Notes on parliament hearing in Tallinn, Estonia June 4, 2019 as regards the deployment of the fifth generation, 5G, of wireless communication. Available at: https://www.spandidos-publications.com/10.3892/wasj.2019.28# - Accessed 25-04-2022.
- ↑ 5G Infrastructure Available at: https://www.heavy.ai/technical-glossary/5g-infrastructure - Accessed 25-04-2022.
- ↑ 5G Infrastructure Available at: https://www.sdxcentral.com/5g/definitions/5g-network-infrastructure/ - Accessed 25-04-2022.
- ↑ 5G Security Standard. Available at: https://www.etsi.org/deliver/etsi_ts/133500_133599/133501/15.01.00_60/ts_133501v150100p.pdf - Accessed 25-04-2022.
- ↑ 5G Security Standards. Available at: https://www.ericsson.com/en/standardization/network-security - Accessed 25-04-2022.
- ↑ What is 5G Security? Available at: https://cybersecurity.att.com/blogs/security-essentials/what-is-5g-security - Accessed 25-04-2022.
- ↑ Integrity of user and signaling data Available at: https://www.ericsson.com/en/security/a-guide-to-5g-network-security#securityarchitecture - Accessed 25-04-2022.
- ↑ 5G Security. Available at: https://www.sdxcentral.com/5g/definitions/5g-security-standards/ - Accessed 25-04-2022.
- ↑ What is the real-world impact of 5G technology? Available at: https://www.cisco.com/c/en/us/solutions/what-is-5g.html#~faqs - Accessed 25-04-2022.
- ↑ Photo: AR and VR Available at: https://www.kaspersky.com/resource-center/threats/security-and-privacy-risks-of-ar-and-vr - Accessed 27-04-2022.
- ↑ What is enhanced Mobile Broadband (eMBB) Available at: https://5g.co.uk/guides/what-is-enhanced-mobile-broadband-embb/ - Accessed 27-04-2022.
- ↑ Photo: TTÜ Self-driving car Available at: https://iot.ttu.ee/projects/iseauto/ - Accessed 27-04-2022.
- ↑ URLLC: What it is and how it works Available at: https://blog.antenova.com/urllc-what-it-is-and-how-it-works - Accessed 27-04-2022.
- ↑ Ultra-Reliable Low-Latency Communication Available at: https://www.section.io/engineering-education/five-real-life-use-cases-of-5g-ultra-reliable-low-latency-communication-urllc/ - Accessed 27-04-2022.
- ↑ Photo: Smart city Available at: https://www.5gradar.com/features/what-is-5g-these-use-cases-reveal-all - Accessed 27-04-2022.
- ↑ What is mMTC in 5G? Available at: https://blog.antenova.com/what-is-mmtc-in-5g-how-does-it-work - Accessed 27-04-2022.
- ↑ Use cases. Available at: https://www.gsma.com/membership/wp-content/uploads/2019/11/5G-Research_A4.pdf - Accessed 25-04-2022.
- ↑ Photo: 5G evolution Available at: https://www.digitalrealty.com/blog/5g-how-we-got-here-and-its-impact-on-data-center-infrastructure - Accessed 27-04-2022.
- ↑ What is 5G and why does it matter? Available at: https://www.verizon.com/about/our-company/5g/what-5g - Accessed 25-04-2022.
- ↑ What are the differences between the previous generations of mobile networks and 5G? Available at: https://www.qualcomm.com/5g/what-is-5g - Accessed 25-04-2022.
- ↑ What is 5G technology? Available at: https://www.cisco.com/c/en/us/solutions/what-is-5g.html#~faqs - Accessed 25-04-2022.
- ↑ 5G is a unified, more capable air interface. Available at: https://www.qualcomm.com/5g/what-is-5g - Accessed 25-04-2022.
- ↑ Photo: 5G Protests in California https://ca-times.brightspotcdn.com/dims4/default/f867e53/2147483647/strip/true/crop/2048x1401+0+0/resize/1024x701!/quality/90/?url=https%3A%2F%2Fcalifornia-times-brightspot.s3.amazonaws.com%2Faf%2F4c%2F55584c285872b3346967555705f3%2Fla-tn-blr-me-att-5g-protest-004
- ↑ Is 5G technology bad for our health? Available at: https://www.medicalnewstoday.com/articles/326141 - Accessed 25-04-2022.
- ↑ Photo: 5G mobile networks DO NOT spread COVID-19 https://pbs.twimg.com/media/EVJeS5EUYAEgRLE?format=jpg&name=medium
- ↑ We Have No Reason to Believe 5G Is Safe. Available at: https://blogs.scientificamerican.com/observations/we-have-no-reason-to-believe-5g-is-safe/ - Accessed 25-04-2022.
- ↑ 5G technology does not cause or spread coronavirus. Available at: https://www.unicef.org/montenegro/en/stories/5g-technology-does-not-cause-or-spread-coronavirus - Accessed 25-04-2022.
- ↑ 5G doesn’t cause COVID-19, but the rumor it does spread like a virus. Available at: https://www.bu.edu/hic/2021/01/04/5g-doesnt-cause-covid-19-but-the-rumor-it-does-spread-like-a-virus/ - Accessed 25-04-2022.
- ↑ 5G in Estonia. Available at: https://5geestis.ee/ - Accessed 25-04-2022.
- ↑ Photo: 5G base station https://digi.geenius.ee/app/uploads/sites/7/2020/04/cfd565de8e74abc925e2dba97eedc7c9-770x513.jpg
- ↑ Only three companies will receive 5G mobile licenses in Estonia. Available at: https://rus.err.ee/1608438122/licenzii-na-mobilnuju-svjaz-5g-v-jestonii-poluchat-tolko-tri-firmy - Accessed 25-04-2022.
- ↑ Where is Estonia in terms of its 5G developments compared to the rest of the world? Available at: https://www.telia.ee/uudised/kus-asub-eesti-oma-5g-arengutelt-vorreldes-muu-maailmaga - Accessed 25-04-2022.
- ↑ 5G competition draws four bids. Available at: https://news.err.ee/1608554782/5g-competition-draws-four-bids - Accessed 25-04-2022.
- ↑ Only three companies will receive 5G mobile licenses in Estonia. Available at: https://rus.err.ee/1608438122/licenzii-na-mobilnuju-svjaz-5g-v-jestonii-poluchat-tolko-tri-firmy - Accessed 25-04-2022.
- ↑ Photo: Speed comparison 5G vs 6G https://thumbs.dreamstime.com/b/g-vs-network-comparison-infographic-vector-157269709.jpg
- ↑ What is 6G, how fast will it be, and when is it coming? Available at: https://www.digitaltrends.com/mobile/what-is-6g/ - Accessed 25-04-2022.
- ↑ 6G: What It Is & When to Expect It. Available at: https://www.lifewire.com/6g-wireless-4685524 - Accessed 25-04-2022.