Famous malware attacks: Difference between revisions
| (48 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
== Introduction == | == Introduction == | ||
Malware is malicious software that can enter, and stay on your computer, and then perform actions without your consent, giving hackers full access to your data, and systems. The malware initially appeared as a form of cybervandalism. So it was used to change the computer's background tasks and access your personal information. Since then, these methods, adopted by cybercriminals, have begun to be used to track information and steal valuable business or personal data. | Malware is malicious software that can enter, and stay on your computer, and then perform actions without your consent, giving hackers full access to your data, and systems. The malware initially appeared as a form of cybervandalism. So it was used to change the computer's background tasks and access your personal information. Since then, these methods, adopted by cybercriminals, have begun to be used to track information and steal valuable business or personal data. <ref>Definition for Malware from Cisco https://www.cisco.com/c/en/us/products/security/advanced-malware-protection/what-is-malware.html </ref> | ||
== Petya == | |||
Petya is a file-encrypting Trojan that was first discovered in 2016, according to information on 2SpyWare, which was launched as a project to help people learn more about cybersecurity issues and malware. <ref>Available at https://www.bbc.com/news/technology-40497026 </ref>It has continued to appear in various variants with several different updates until today. Among its derivatives are PetrWrap, GoldenEye, Mamba virus, Mischa, Diskcoder.D, and Bad Rabbit. Petya has been one of the classic ransomware attacks in which the files on victims' computers are encrypted to make them inaccessible and then demand a ransom to give the encryption key. Ransoms are also typically demanded in bitcoin or other cryptocurrencies.<ref>Available at https://fortune.com/2017/06/27/petya-ransomware-ukraine-medoc/ </ref> Its beginnings were similar to WannaCry; The epidemic was not noticed from anywhere and spread rapidly. However, unlike WannaCry, this malware spread via spam e-mails, immediately after restarting the computer, it displayed the following message on the screen.<ref>Available at https://www.proofpoint.com/us/threat-reference/petya </ref> | |||
[[File:Petya 1.PNG]] | |||
Although this screen may seem like a system error at first glance, users In fact, Petya software silently performed file encryption in the background of the system. If the user tries to reboot the system or the file encryption operation is performed, a flashing red skeleton appears on the screen, and “Press any key” appears. After pressing the key, a new window is opened with the ransom note | Although this screen may seem like a system error at first glance, users In fact, Petya software silently performed file encryption in the background of the system. If the user tries to reboot the system or the file encryption operation is performed, a flashing red skeleton appears on the screen, and “Press any key” appears. After pressing the key, a new window is opened with the ransom note | ||
<ref> Available at https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/petya.html</ref> | |||
[[File:Petya2.PNG]] | |||
One of the email domains associated with the perpetrators of the attack was revoked in the process, thus giving a victim's computer a specific code to help retrieve the matching decoder data recovery has become impossible. It has been effective in countries such as Russia, England, France, Denmark, Iran, Brazil, and Mexico, especially in Ukraine. Spain, Netherlands, and India also confirmed the attack. Ukraine has suffered the most from the attack. Petya malware also envelops various public institutions of the country; In addition, it affected a wide area such as Kyiv Airport, metro systems, power plants, and nuclear power plants, bringing the systems to a standstill and causing many disruptions. MeDoc, a Ukrainian software company, was held responsible for the attack that brought life to a standstill in Ukraine. Although MeDoc denies these allegations, many cybersecurity experts have claimed to have evidence that the firm was the first source. 55 Public authorities stated that the affected institutions had difficulties in carrying out customer service and banking transactions, it was observed that most of the ATMs were out of service or Petya's ransomware message was displayed on their screens. | One of the email domains associated with the perpetrators of the attack was revoked in the process, thus giving a victim's computer a specific code to help retrieve the matching decoder data recovery has become impossible.<ref> Available at https://www.theguardian.com/technology/2017/jun/27/petya-ransomware-cyber-attack-who-what-why-how </ref> It has been effective in countries such as Russia, England, France, Denmark, Iran, Brazil, and Mexico, especially in Ukraine. Spain, Netherlands, and India also confirmed the attack. Ukraine has suffered the most from the attack. Petya malware also envelops various public institutions of the country; In addition, it affected a wide area such as Kyiv Airport, metro systems, power plants, and nuclear power plants, bringing the systems to a standstill and causing many disruptions. <ref> Available at https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/petya-ransomware-wiper </ref> MeDoc, a Ukrainian software company, was held responsible for the attack that brought life to a standstill in Ukraine. Although MeDoc denies these allegations, many cybersecurity experts have claimed to have evidence that the firm was the first source. 55 Public authorities stated that the affected institutions had difficulties in carrying out customer service and banking transactions, it was observed that most of the ATMs were out of service or Petya's ransomware message was displayed on their screens. <ref> Available at http://services.nwu.ac.za/it-news/latest-cyber-attack-petya-ransomware </ref> | ||
Considering that it is also exposed to similar attacks, it is understood that it is a political attack aimed at creating confusion in the country rather than for a financial purpose. It has been understood that many systems do not have enough defense against ransomware. The extent of such attacks has also revealed the widespread inadequacy of awareness of cyber security, vulnerability scanning, testing, use of correct cyber security applications, and taking backups. It can also be said that Petya, which aims to render the system unusable rather than encrypting the files, aims to have a devastating effect rather than money. | Considering that it is also exposed to similar attacks, it is understood that it is a political attack aimed at creating confusion in the country rather than for a financial purpose.<ref> Available at https://www.inverse.com/article/33469-petya-ransomware-attack-united-states </ref> It has been understood that many systems do not have enough defense against ransomware. The extent of such attacks has also revealed the widespread inadequacy of awareness of cyber security, vulnerability scanning, testing, use of correct cyber security applications, and taking backups. It can also be said that Petya, which aims to render the system unusable rather than encrypting the files, aims to have a devastating effect rather than money. <ref> Available at https://thehackernews.com/2017/06/petya-ransomware-decryption-key.html </ref> | ||
== SamSam == | |||
The most comprehensive research report on ransomware named SamSam, which was first seen in December 2015 and started to spread in 2016, belongs to the global cyber security company Sophos. <ref>Available at https://www.nomios.com/resources/what-is-samsam-ransomware/ </ref> According to the report published in April 2018, unlike most of the well-known ransomware families that randomly attack, SamSam has been used against certain organizations that are predicted to be most likely to pay to get their data back, such as hospitals or schools. Instead of spam campaigns, the cybercriminals behind SamSam exploited vulnerabilities to access victims' networks or use brute-force tactics against weak passwords of the Remote Desktop Protocol (RDP). <ref>Available at </ref>This is the main feature that distinguishes SamSam from other ransomware attacks. <ref>Available at https://blog.malwarebytes.com/cybercrime/2018/05/samsam-ransomware-need-know/ </ref> The process, which is designed to cause the highest level of damage to the IT infrastructure of the victim selected institution in the shortest time, is based on the fact that a person or group who is skilled in infiltrating the systems detects the weaknesses in the infiltrating network and manually runs the malware there. After potential targets were discovered, attackers manually deployed SamSam malware to selected systems using tools such as PSEXEC and batch scripts. The first victim of the attack was Atlanta. <ref>Available at https://heimdalsecurity.com/blog/samsam-ransomware/ </ref>The attack resulted in severe digital blackouts in five of the city's 13 local government units. The attack had far-reaching effects, including disrupting the court system, preventing residents from paying their water bills, limiting vital communications such as sewer infrastructure requests, and forcing the Atlanta Police Department to work with pen and paper instead of computers. <ref>Available at https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/samsam-targeted-ransomware-attacks </ref> The ransom amount demanded is around $50,000. It was reported in the press that over 2.6 million dollars were spent at the first stage to eliminate these attacks. The majority of the spending is related to emergency response to systems recovery, forensics, and additional staffing. <ref>Available at https://blogs.blackberry.com/en/2018/11/pro-tips-on-how-to-avoid-a-samsam-ransomware-infection </ref> In addition, it was reported in the press that he spent an additional $650 thousand on a crisis communication center and emergency response consultancy. exceeded the dollar. <ref>Available at https://www.securityweek.com/dhs-says-samsam-ransomware-targeting-critical-infrastructure-entities </ref> | |||
Some striking data from this report are as follows: | Some striking data from this report are as follows: | ||
* 74 percent of known victims are located in the USA. Canada, the United Kingdom, and the Middle East countries are among the countries most affected by the attack. | * 74 percent of known victims are located in the USA. Canada, the United Kingdom, and the Middle East countries are among the countries most affected by the attack. <ref>Available at https://www.tzcert.go.tz/wp-content/uploads/2018/12/SamSam-Ransomware-Security-Notice.pdf </ref> | ||
* According to transfers made in Bitcoin, SamSam attackers managed to extort ransoms of up to 64 thousand dollars from individual victims at once. | * According to transfers made in Bitcoin, SamSam attackers managed to extort ransoms of up to 64 thousand dollars from individual victims at once. | ||
* Following the emergence of the SamSam attack, new versions were also developed, more complex attack methods were used in each new version, and it was observed that more competent measures were taken to protect from operational security measures in order not to leave traces. | * Following the emergence of the SamSam attack, new versions were also developed, more complex attack methods were used in each new version, and it was observed that more competent measures were taken to protect from operational security measures in order not to leave traces. <ref>Available at https://blog.knowbe4.com/samsam-ransomware-infected-thousands-of-labcorp-systems-via-brute-force-rdp </ref> | ||
* SamSam attackers targeted medium to large-sized public sector institutions in the fields of health, education and government at 50 percent, and private sector companies at 50 percent. | * SamSam attackers targeted medium to large-sized public sector institutions in the fields of health, education and government at 50 percent, and private sector companies at 50 percent. | ||
* The attackers' preparation for the attack is meticulous. SamSam attackers waited for the opportune moment; they initiated encryption commands at midnight when most users were asleep, or in the early morning hours of the victim's local time zone. In the SamSam example, after attackers had successfully infected a server, they also created additional victimization by stealing network mapping and credentials. It would be appropriate to interpret this attack as a professional diamond theft rather than a simple theft. Because both the attack method and the targeted critical institutions are the basic foundations of this determination. | * The attackers' preparation for the attack is meticulous. SamSam attackers waited for the opportune moment; they initiated encryption commands at midnight when most users were asleep, or in the early morning hours of the victim's local time zone. In the SamSam example, after attackers had successfully infected a server, they also created additional victimization by stealing network mapping and credentials. It would be appropriate to interpret this attack as a professional diamond theft rather than a simple theft. Because both the attack method and the targeted critical institutions are the basic foundations of this determination. | ||
<ref>Available at https://www.lepide.com/blog/how-can-hospitals-protect-themselves-from-samsam-ransomware-attacks/ </ref> | |||
== Stuxnet == | == Stuxnet == | ||
| Line 45: | Line 46: | ||
The link file automatically executes the copies the worm, which exploits a vulnerability in the way Windows displays the icons of shortcut files. | The link file automatically executes the copies the worm, which exploits a vulnerability in the way Windows displays the icons of shortcut files. | ||
The worm executes all routines related to the main payload of the attack. It implements a Microsoft Remote Procedure Call to execute certain functions, effectively enabling affected systems to communicate with one another. With the inclusion of tests, that check for an active Internet connection on the affected system to communicate with a remote server, which holds the copies of the worm. | The worm executes all routines related to the main payload of the attack. It implements a Microsoft Remote Procedure Call to execute certain functions, effectively enabling affected systems to communicate with one another. With the inclusion of tests, that check for an active Internet connection on the affected system to communicate with a remote server, which holds the copies of the worm. <ref>Available at https://www.wired.com/2014/11/countdown-to-zero-day-stuxnet/ </ref> | ||
The rootkit is the main component responsible for hiding all the malicious files and processes, to stay undetected by the user and anti-virus software. | The rootkit is the main component responsible for hiding all the malicious files and processes, to stay undetected by the user and anti-virus software. | ||
| Line 51: | Line 52: | ||
==== Use of P2P ==== | ==== Use of P2P ==== | ||
Stuxnet installs both server and client components for a Microsoft Remote Procedure Call in all infected systems and versions. After connecting to a system, it would do the following procedure: Getting malware version, receiving module and injecting it, send the malware file, create a process that would be command shell or a file, create a file, delete a file and then read a file. | Stuxnet installs both server and client components for a Microsoft Remote Procedure Call in all infected systems and versions. After connecting to a system, it would do the following procedure: Getting malware version, receiving module and injecting it, send the malware file, create a process that would be command shell or a file, create a file, delete a file and then read a file. <ref>Available at https://spectrum.ieee.org/the-real-story-of-stuxnet/ </ref> | ||
All affected systems would have a UUID (Universally Unique Identifier) to use for communication between systems for updating each other. | All affected systems would have a UUID (Universally Unique Identifier) to use for communication between systems for updating each other. | ||
==== The remote server ==== | ==== The remote server ==== | ||
Firstly it tries to connect with a URL: www.windowsupdate.com or www.msn.com. Then after it has identified that internet connection is available, it would connect with a user with a URL: | Firstly it tries to connect with a URL: "www.windowsupdate.com" or "www.msn.com". Then after it has identified that internet connection is available, it would connect with a user with a URL: "www.{BLOCKED}erfutbol.com" or "www.{BLOCKED}futbol.com". After it has connected with the malicious user, a URL is generated “http://www.{BLOCKED}erfutbol.com/index.php?data={data}”, where {data} is an encrypted hex value that contains the IP address of the machine, computer name, and domain. | ||
=== History === | === History === | ||
The earlier versions of Stuxnet could spread only by infecting Step7 project files, which were the files that were used to program the PLCs, but later versions could also spread via USB flash drives, using a Windows feature called “Autorun” or through a local network with print-spooler exploit. The reasoning for adding increased spreadability of Stuxnet by the creators was to increase the odds of a successful attack on companies related to Iran’s nuclear production, from manufacture to installment side of things. The companies provided a gateway via infected employees for the worm to enter Natanz, which was the location of the Iran’s uranium-enrichment plant or Būshehr, which was the location of a nuclear reactor. The attack took place in June 2009, with the first company to get infected was Follad Technic, then a week after Behpajooh was hit and then another nine days for Neda Industrial Group to also get struck. The size of the worm was 500KB and infected the software of at least 14 industrial sites. The reason for the virus to be unnoticed for about a year after the initial attack was due to the fact that it was also giving false data, in the sense that the data indicated that everything was running fine and smoothly, when in truth it was not. While there were early notifications about the Step 7.DLL file producing errors and that the problem was consistent when using a flash drive to transfer files, when before it was a clean computer, there were no errors. The biggest giveaway was when new machines were being installed about five months after the early notifications, none of the newer machines were being fed gas as they were in the process of being installed, but the systems monitors SCADA (Supervisory Control and Data Acquisition), were showing data, as if gas was being fed into the machines. While the Iranian nuclear program continued to suffer technical difficulties, people were speculating that the worm originated as a co-op program by United States and Israel, called “Olympic Games”. The virus started spreading on a global scale via employees and the general public, targeting industrial control systems and causing massive damages, data showed that approximately 100k computers were infected by the end of 2010, with more than 60% allocated in Iran. The damages were only increasing, due to the sheer number of people plugging USB flash drivers into multiple storage devices, effectively re-infecting and spreading systems around the globe. No infrastructure was safe and targets were any and all industrial control systems. | The earlier versions of Stuxnet could spread only by infecting Step7 project files, which were the files that were used to program the PLCs, but later versions could also spread via USB flash drives, using a Windows feature called “Autorun” or through a local network with print-spooler exploit. The reasoning for adding increased spreadability of Stuxnet by the creators was to increase the odds of a successful attack on companies related to Iran’s nuclear production, from manufacture to installment side of things. The companies provided a gateway via infected employees for the worm to enter Natanz, which was the location of the Iran’s uranium-enrichment plant or Būshehr, which was the location of a nuclear reactor. The attack took place in June 2009, with the first company to get infected was Follad Technic, then a week after Behpajooh was hit and then another nine days for Neda Industrial Group to also get struck. The size of the worm was 500KB and infected the software of at least 14 industrial sites. <ref>Available at https://www.britannica.com/technology/Stuxnet </ref> The reason for the virus to be unnoticed for about a year after the initial attack was due to the fact that it was also giving false data, in the sense that the data indicated that everything was running fine and smoothly, when in truth it was not. While there were early notifications about the Step 7.DLL file producing errors and that the problem was consistent when using a flash drive to transfer files, when before it was a clean computer, there were no errors. The biggest giveaway was when new machines were being installed about five months after the early notifications, none of the newer machines were being fed gas as they were in the process of being installed, but the systems monitors SCADA (Supervisory Control and Data Acquisition), were showing data, as if gas was being fed into the machines. While the Iranian nuclear program continued to suffer technical difficulties, people were speculating that the worm originated as a co-op program by United States and Israel, called “Olympic Games”. The virus started spreading on a global scale via employees and the general public, targeting industrial control systems and causing massive damages, data showed that approximately 100k computers were infected by the end of 2010, with more than 60% allocated in Iran. The damages were only increasing, due to the sheer number of people plugging USB flash drivers into multiple storage devices, effectively re-infecting and spreading systems around the globe. No infrastructure was safe and targets were any and all industrial control systems. | ||
===Stuxnet family=== | ===Stuxnet family=== | ||
In the following years after the initial attack in 2009 and the continuous damages throughout until late 2010, many related malwares were developed from the same type of worm virus as the original Stuxnet. | In the following years after the initial attack in 2009 and the continuous damages throughout until late 2010, many related malwares were developed from the same type of worm virus as the original Stuxnet. <ref>Available at https://www.britannica.com/technology/Stuxnet </ref> | ||
======Duqu (2011)====== | ======Duqu (2011)====== | ||
| Line 72: | Line 73: | ||
======Flame (2012)====== | ======Flame (2012)====== | ||
Flame module exploits the same vulnerabilities for spreading as Stuxnet did. It was a sophisticated spyware that logged keystrokes, recorded conversations (e.g. Skype), gathered screenshots and many other data collection activities. Main targets of Flame were government and educational organizations and some private individuals mostly in Iran and other Middle Eastern countries. | Flame module exploits the same vulnerabilities for spreading as Stuxnet did. It was a sophisticated spyware that logged keystrokes, recorded conversations (e.g. Skype), gathered screenshots and many other data collection activities. Main targets of Flame were government and educational organizations and some private individuals mostly in Iran and other Middle Eastern countries. <ref> Available at https://arstechnica.com/tech-policy/2012/06/confirmed-us-israel-created-stuxnet-lost-control-of-it/ </ref> | ||
======Havex (2013) ====== | ======Havex (2013) ====== | ||
Havex was used in a widespread espionage campaign targeting energy, aviation, pharmaceutical, defense and petrochemical sectors, with the primary targets being in the United States, Europe and Canadian organizations. | Havex was used in a widespread espionage campaign targeting energy, aviation, pharmaceutical, defense and petrochemical sectors, with the primary targets being in the United States, Europe and Canadian organizations. <ref> Available at https://web.archive.org/web/20170904015230/https://www.mac-solutions.net/en/news/129-sheep-dip-your-removable-storage-devices-to-reduce-the-threat-of-cyber-attacks </ref> | ||
====== Industroyer (2016)====== | ====== Industroyer (2016)====== | ||
| Line 88: | Line 89: | ||
======Stuxnet 2.0 (2018)====== | ======Stuxnet 2.0 (2018)====== | ||
The target was Iran, as with original Stuxnet, but this time the target was the telecom infrastructure. | The target was Iran, as with original Stuxnet, but this time the target was the telecom infrastructure. <ref> Available at https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/what-is-stuxnet.html </ref> | ||
“Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon”, written by Kim Zetter, explains the events regarding Stuxnet in further detail. | “Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon”, written by Kim Zetter, explains the events regarding Stuxnet in further detail. | ||
== Melissa == | == Melissa == | ||
Back in the day, not much information was known to an average computer user about computer viruses and their methods of spreading. However, in March 1999, that would be changed forever. A programmer named David Lee Smith hacked into an America Online (AOL) account and used it to post a file on a newsgroup page, named “alt.sex”, which promised a list of many passwords for otherwise fee-based websites with adult content. This was one of the first massive scale phishing | Back in the day, not much information was known to an average computer user about computer viruses and their methods of spreading. However, in March 1999 <ref> Available at https://en.wikipedia.org/wiki/Portal:Current_events/March_1999 </ref>, that would be changed forever. A programmer named David Lee Smith <ref> Available at https://en-academic.com/dic.nsf/enwiki/732114 </ref> hacked into an America Online (AOL) <ref> Available at https://www.aol.com/?guccounter=1&guce_referrer=aHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS8&guce_referrer_sig=AQAAAEqgHrJ4kQ8wKq0IQkqZlaGRluN3Lm_hIyBY_2QCZT9cZQCtb2P0IlngfiR4QtSx3jEM3QhUkBDsFtj-04EKUviBY2qVuM_5HP7AFxB8F5YzBYidTYosRJ7xlQcZJoWwl0NMdSjNaVmdlzqPvLAiirBg3A0ukMHaARtVHZu9oFdM </ref> account and used it to post a file on a newsgroup page, named “alt.sex”, which promised a list of many passwords for otherwise fee-based websites with adult content. This was one of the first massive-scale phishing <ref> https://csrc.nist.gov/glossary/term/phishing </ref> attacks that are known to us today. When a user | ||
took the bait by downloading the attached file, it unleashed a virus into their computers. The Melissa virus, reportedly named by Smith after the name of a stripper he met in Florida, begun by taking over victims’ Microsoft Word program. It at that point utilized a macro Microsoft Outlook mail framework and sent messages to the first 50 addresses in their mailing records. Those messages, in turn, tempted receivers to open an attachment with a virus. The message of the e-mail read “Here is the document you requested ... don’t show anyone else ;-):” people trusted the sender and thus were willing to download the attachment, but the senders had no idea that their mail contacts had received the message. The virus was not aiming to steal money or data, but it damaged systems, nonetheless. E-mail servers at more than 300 organizations and government agencies around the world got to be overloaded, and a few had to be closed down totally, including Microsoft. Within a few days, cybersecurity specialists had for the most part contained the spread of the virus and reestablished the functionality of their networks, in spite of the fact that it took some time to remove the contaminations totally. Still, the collective damage was colossal: an evaluated $80 million for the cleanup and repair of affected computer frameworks. | took the bait by downloading the attached file, it unleashed a virus into their computers. The Melissa virus, reportedly named by Smith after the name of a stripper he met in Florida, begun by taking over victims’ Microsoft Word program. It at that point utilized a macro Microsoft Outlook mail framework and sent messages to the first 50 addresses in their mailing records. Those messages, in turn, tempted receivers to open an attachment with a virus. The message of the e-mail read “Here is the document you requested ... don’t show anyone else ;-):” people trusted the sender and thus were willing to download the attachment, but the senders had no idea that their mail contacts had received the message. The virus was not aiming to steal money or data, but it damaged systems, nonetheless. E-mail servers at more than 300 organizations and government agencies around the world got to be overloaded, and a few had to be closed down totally, including Microsoft. Within a few days, cybersecurity specialists had for the most part contained the spread of the virus and reestablished the functionality of their networks, in spite of the fact that it took some time to remove the contaminations totally. Still, the collective damage was colossal: an evaluated $80 million for the cleanup and repair of affected computer frameworks. | ||
| Line 101: | Line 101: | ||
==== The Legacy Of Melissa Worm==== | ==== The Legacy Of Melissa Worm==== | ||
* Love Bug (2000) - The Love Bug, also known as ILOVEYOU, LoveLetter or VBS/LoveLet, spread itself via email using the subject line “ILOVEYOU” and the message body “Kindly check the attached LOVELETTER coming from me”. It overwrote files and hid some Mp3 files as well. | * Love Bug (2000) <ref> Available at https://www.wired.com/story/the-20-year-hunt-for-the-man-behind-the-love-bug-virus/ </ref> - The Love Bug, also known as ILOVEYOU, LoveLetter or VBS/LoveLet, spread itself via email using the subject line “ILOVEYOU” and the message body “Kindly check the attached LOVELETTER coming from me”. It overwrote files and hid some Mp3 files as well. | ||
* Anna Kournikova (2001) - The Anna Kournikova worm wasn’t especially sophisticated in design. It was a standard e-mail worm composed in Visual Basic Script (VBS), which sent itself through emails utilizing details it collected from your Microsoft Outlook address book. | * Anna Kournikova (2001) <ref> Available at https://nakedsecurity.sophos.com/2011/02/11/memories-anna-kournikova-worm/ </ref> - The Anna Kournikova worm wasn’t especially sophisticated in design. It was a standard e-mail worm composed in Visual Basic Script (VBS), which sent itself through emails utilizing details it collected from your Microsoft Outlook address book. | ||
* Netsky (2004) - The worm was sent out as an e-mail, enticing recipients to open an attachment. Once opened, the attached program would scan the computer for e-mail addresses and e-mail itself to all addresses found. It contained a 22,016 byte file attachment and was reportedly causing Denial of Service (DoS) attacks because networks got clogged and couldn’t handle the traffic | * Netsky (2004) <ref> Available at https://malwiki.org/index.php?title=Netsky </ref> - The worm was sent out as an e-mail, enticing recipients to open an attachment. Once opened, the attached program would scan the computer for e-mail addresses and e-mail itself to all addresses found. It contained a 22,016 byte file attachment and was reportedly causing Denial of Service (DoS) attacks because networks got clogged and couldn’t handle the traffic | ||
== Zeus Trojan == | == Zeus Trojan == | ||
While talking about the top malware attacks in history, the Zeus Malware is one of those which cannot be omitted. The Zeus Trojan is a malicious software aiming to harm the gadgets having the operating system Microsoft Windows by stealing financial data. Its first detection dates back to 2007. This virus is also known for its other name, Zbot. The Zeus Trojan has obtained great success in terms of thieving information. According to the researches, millions of systems have been damaged by this Trojan, and billions of dollars were stolen. After providing this primary information about the above-mentioned malware, it’s time to dive deeper and learn much more. | While talking about the top malware attacks in history, the Zeus Malware is one of those which cannot be omitted. The Zeus Trojan is a malicious software aiming to harm the gadgets having the operating system Microsoft Windows by stealing financial data. Its first detection dates back to 2007. This virus is also known for its other name, Zbot. <ref> Available at https://www.digitaldefense.com/blog/zeus-trojan-what-it-is-how-to-prevent-it-digital-defense/ </ref> The Zeus Trojan has obtained great success in terms of thieving information. According to the researches, millions of systems have been damaged by this Trojan, and billions of dollars were stolen. <ref> Available at https://blog.malwarebytes.com/101/2021/07/the-life-and-death-of-the-zeus-trojan/ </ref> After providing this primary information about the above-mentioned malware, it’s time to dive deeper and learn much more. | ||
Initially, let’s take a look at what it executes on the gadgets. The 2 main features of the Zeus Trojan are always underlined; the creation of Botnets and thieving financial data. To begin with, The Zbot establishes botnets. The Botnet is considered the network of the infected nodes. By setting up such botnets, the Zbot owner obtains control over all those nodes. More precisely, with the help of Botnets, their owner becomes capable of collecting data and operating attacks. Secondly, the Zbot is counted as also a Trojan being able to steal the banking credentials. Keylogging and Monitoring are the methods it uses to reach to having stolen the banking data. Acting as a financial Trojan makes Zbot a Crimeware. | Initially, let’s take a look at what it executes on the gadgets. The 2 main features of the Zeus Trojan are always underlined; the creation of Botnets and thieving financial data. To begin with, The Zbot establishes botnets. The Botnet is considered the network of the infected nodes. By setting up such botnets, the Zbot owner obtains control over all those nodes. More precisely, with the help of Botnets, their owner becomes capable of collecting data and operating attacks. Secondly, the Zbot is counted as also a Trojan being able to steal the banking credentials. Keylogging and Monitoring are the methods it uses to reach to having stolen the banking data. Acting as a financial Trojan makes Zbot a Crimeware. <ref> Available at https://usa.kaspersky.com/resource-center/threats/zeus-virus </ref> | ||
==== ZBOT Spreading Methods ==== | ==== ZBOT Spreading Methods ==== | ||
Time to explore how Zbot works. There are 2 main ways that the Zbot uses for spreading; spam messages, and drive-by downloads. Likewise the other malware forms, spam messages are preferred also by the Zbot. The hackers send thousands of spam e-mails or compose social media campaigns that redirect the users to websites in which the Trojan is automatically installed on the user’s computer. Despite the fact that the Zbot had mainly been used for obtaining banking credentials, its ability to steal can also be used to hijack other users’ social media accounts and e-mails. As mentioned above, there is another method called “Drive-by downloads” that the Zbot uses to spread. The hackers can infect some legitimate and quite reliable websites by inserting the Trojan into them. In case of visiting or downloading a file from such websites, the malware would be installed on the user gadget. | Time to explore how Zbot works. There are 2 main ways that the Zbot uses for spreading; spam messages, and drive-by downloads. Likewise the other malware forms, spam messages are preferred also by the Zbot. The hackers send thousands of spam e-mails or compose social media campaigns that redirect the users to websites in which the Trojan is automatically installed on the user’s computer. Despite the fact that the Zbot had mainly been used for obtaining banking credentials, its ability to steal can also be used to hijack other users’ social media accounts and e-mails. As mentioned above, there is another method called “Drive-by downloads” that the Zbot uses to spread. The hackers can infect some legitimate and quite reliable websites by inserting the Trojan into them. In case of visiting or downloading a file from such websites, the malware would be installed on the user gadget. <ref> Available at https://usa.kaspersky.com/resource-center/threats/zeus-virus </ref> | ||
==== Famous Zeus Variants ==== | ==== Famous Zeus Variants ==== | ||
| Line 121: | Line 121: | ||
Although there are thousands of Zeus Trojan variants, some of them are more popular due to their characteristics and the damage they caused. Floki Bot, Gameover Zeus, and Zeus Atmos are some of those noteworthy variations. | Although there are thousands of Zeus Trojan variants, some of them are more popular due to their characteristics and the damage they caused. Floki Bot, Gameover Zeus, and Zeus Atmos are some of those noteworthy variations. | ||
Floki Bot takes its name from a Brazilian hacker with the username “flokibot”. This form of Zeus was detected for the first time in 2016. Evasion techniques, and using of the Tor browser are some features that Floki Bot obtained while it was gradually developing in its first months. The foremost factor making Floki Bot irregular is its ability to target the POS (Point of Sale) systems. It is reported that the malware has been targeting the Canadian, American and Brazilian banks, and insurance companies. | Floki Bot takes its name from a Brazilian hacker with the username “flokibot”. This form of Zeus was detected for the first time in 2016. Evasion techniques, and using of the Tor browser are some features that Floki Bot obtained while it was gradually developing in its first months. The foremost factor making Floki Bot irregular is its ability to target the POS (Point of Sale) systems. It is reported that the malware has been targeting the Canadian, American and Brazilian banks, and insurance companies. <ref> Available at https://www.cyber.nj.gov/threat-center/threat-profiles/trojan-variants/floki-bot </ref> | ||
Gameover or Gameover P2P is another Zeus variant to study. As its name suggests, this Zeus variation is mainly famous for using P2P (peer-to-peer) connections. Once it finds out what it is looking for in the infected computers, it shares that data with the other nodes, and of course the control server too. Apart from the data transmission, Gameover is also able to install other malwares, and interrupt some operations. | Gameover or Gameover P2P is another Zeus variant to study. As its name suggests, this Zeus variation is mainly famous for using P2P (peer-to-peer) connections. Once it finds out what it is looking for in the infected computers, it shares that data with the other nodes, and of course the control server too. Apart from the data transmission, Gameover is also able to install other malwares, and interrupt some operations. <ref> Available at https://www.ryadel.com/en/zeus-malware-what-how-prevent/ </ref> | ||
Citadel is also quite a dangerous variation of the Zeus Trojan. It is even able to create an IoT botnet. This variant mainly targets Password managers. In most cases, Citadel is installed through drive-by-downloads. It was first detected in 2011 and has infected about 11 million systems in the next 6 years. The total damage it brought about is approximately 500 million dollars. | Citadel is also quite a dangerous variation of the Zeus Trojan. It is even able to create an IoT botnet. This variant mainly targets Password managers. In most cases, Citadel is installed through drive-by-downloads. It was first detected in 2011 and has infected about 11 million systems in the next 6 years. The total damage it brought about is approximately 500 million dollars. <ref> Available at https://www.wallarm.com/what/what-is-citadel-malware </ref> | ||
The recent years have witnessed a new variant of Zeus, called Atmos. This is a pretty new version of Zeus and has deployed a feature – dropping Ransomware. Just after this Zeus variant steals the data, it installs Ransomware. Like the other Zeus forms, it also majorly aimed at stealing banking credentials. Despite the fact that Atmos attacks were operated against banks, this is also expected that other industries be subjected to similar attacks in the future. | The recent years have witnessed a new variant of Zeus, called Atmos. This is a pretty new version of Zeus and has deployed a feature – dropping Ransomware. Just after this Zeus variant steals the data, it installs Ransomware. Like the other Zeus forms, it also majorly aimed at stealing banking credentials. Despite the fact that Atmos attacks were operated against banks, this is also expected that other industries be subjected to similar attacks in the future. <ref> Available at https://www.kaspersky.com/blog/atmos-yet-another-zeus-variant-is-threatening-businesses/5476/ </ref> | ||
==== Damage of the ZBOT ==== | ==== Damage of the ZBOT ==== | ||
While analyzing the damage Zbot has caused, it’s better to study the periods in which the malware has obtained its peak performance – from its first detection (2007) to the times its source code was leaked out (2011). According to the data, approximately 44% of the malware attacks in the banking sector in 2010 were Zeus-based. The same report says a total of 960 banks were subjected to Zbot attacks. In addition, over 3.6 million computers were infected only in the USA. This is estimated that in the first 3 years of Zbot, the damage it caused was approximately 100 million US dollars. The anti-malware tools used at these times were mainly ineffective against the Zbot. So that they could block Zbot only in 23% of total cases. | While analyzing the damage Zbot has caused, it’s better to study the periods in which the malware has obtained its peak performance – from its first detection (2007) to the times its source code was leaked out (2011). According to the data, approximately 44% of the malware attacks in the banking sector in 2010 were Zeus-based. The same report says a total of 960 banks were subjected to Zbot attacks. In addition, over 3.6 million computers were infected only in the USA. This is estimated that in the first 3 years of Zbot, the damage it caused was approximately 100 million US dollars. The anti-malware tools used at these times were mainly ineffective against the Zbot. So that they could block Zbot only in 23% of total cases.<ref> Available at https://botnetlegalnotice.com/citadel/files/Guerrino_Decl_Ex1.pdf </ref> | ||
==== Prevention methods from the Zeus Trojan ==== | ==== Prevention methods from the Zeus Trojan ==== | ||
| Line 139: | Line 139: | ||
Secondly, considering the fact that the Zeus Trojan has generally been developed for stealing banking data, this is also recommended to use 2-factor authentication for banking logins. In such cases, a confirmation code is sent to the smartphone having a pre-registered sim card. This feature is today offered by many bank websites and definitely increases security against such financial malwares. | Secondly, considering the fact that the Zeus Trojan has generally been developed for stealing banking data, this is also recommended to use 2-factor authentication for banking logins. In such cases, a confirmation code is sent to the smartphone having a pre-registered sim card. This feature is today offered by many bank websites and definitely increases security against such financial malwares. | ||
Next and most importantly, there have to be installed antiviruses on the computer. In case of being infected, such antimalware tools are able to contribute throughout the whole life span of malware. Initially, antiviruses do not allow the user to visit malicious websites. If the user somehow does, then the antiviruses halt the malware to be downloaded and installed, and even if it infects the gadget, then the antivirus detects and removes the malware. Hence, making use of antivirus must be a foremost option for an end-user in the terms of protecting their own gadget. | Next and most importantly, there have to be installed antiviruses on the computer. In case of being infected, such antimalware tools are able to contribute throughout the whole life span of malware. Initially, antiviruses do not allow the user to visit malicious websites. If the user somehow does, then the antiviruses halt the malware to be downloaded and installed, and even if it infects the gadget, then the antivirus detects and removes the malware. Hence, making use of antivirus must be a foremost option for an end-user in the terms of protecting their own gadget. <ref> Available at https://usa.kaspersky.com/resource-center/threats/zeus-virus </ref> | ||
==== Is Zeus till a threat? ==== | ==== Is Zeus till a threat? ==== | ||
In fact, the developer who created Zbot is not currently making use of it. However, since its source code is on the internet, it is gradually upgraded by the other hackers and newer variations continue emerging. Hence, it can be said that the Zeus Malware is alive. Despite the fact that Ransomware has gained more popularity in recent years, Zbot and its variants are still active. Taking the threats that may potentially stem from the above-mentioned malwares into consideration, it again becomes clear why measurement actions, like safe Internet practices, and implementing Safeguards play a vital role in the prevention of such malware attacks. | In fact, the developer who created Zbot is not currently making use of it. However, since its source code is on the internet, it is gradually upgraded by the other hackers and newer variations continue emerging. Hence, it can be said that the Zeus Malware is alive. Despite the fact that Ransomware has gained more popularity in recent years, Zbot and its variants are still active. <ref> Available at https://blog.malwarebytes.com/101/2021/07/the-life-and-death-of-the-zeus-trojan/ </ref> Taking the threats that may potentially stem from the above-mentioned malwares into consideration, it again becomes clear why measurement actions, like safe Internet practices, and implementing Safeguards play a vital role in the prevention of such malware attacks. | ||
== | == WannaCry == | ||
On May 12, 2017, the WannaCry ransomware (also known as Wana Decrypt0r, WCry, WannaCry, WannaCrypt, and WanaCrypt0r) was discovered during a large-scale assault affecting numerous nations. WannaCry is a crypto worm cyber-attack that was targeted to computer, laptops, and devices running the Microsoft Windows operating system. | On May 12, 2017, the WannaCry ransomware (also known as Wana Decrypt0r, WCry, WannaCry, WannaCrypt, and WanaCrypt0r) was discovered during a large-scale assault affecting numerous nations. WannaCry is a crypto worm cyber-attack that was targeted to computer, laptops, and devices running the Microsoft Windows operating system. | ||
On 13 May, 2017 hackers started to spread a ransomware to computers around the globe. According to Europol, more than 300,000 computers in 150 countries have been victims of the cyberattack, which involved the request of a 300$ ransom in order to return control of the encrypted files. The WannaCry ransomware took advantage of an inherent vulnerability. <ref> Available at https://ieeexplore.ieee.org/document/8260673 </ref> | |||
====How does it considered as a crypto–worm?==== | |||
It is considered as a worm because it included a transport mechanism to automatically spread itself. Wannacry malware could spread from computer to computer and from network to network. That’s how it was spread over the world. <ref> Available at https://asia.nikkei.com/Politics-Economy/International-Relations/North-Korea-capable-of-hacking-with-WannaCry-ransomware </ref> | |||
====How does transport mechanism worked?==== | |||
The transport mechanism used transport code which scans for vulnerable systems, and then it uses the EternalBlue exploit to gain the access. After that it used DoublePulsar tool to install and copy itself. | The transport mechanism used transport code which scans for vulnerable systems, and then it uses the EternalBlue exploit to gain the access. After that it used DoublePulsar tool to install and copy itself. | ||
What is EternalBlue and DoublePulsar? | |||
====What is EternalBlue and DoublePulsar?==== | |||
EternalBlue is a Windows exploit created by the US National Security Agency. The main function of EternalBlue was to exploit a vulnerabilities in the Microsoft implementation of the Server Message Block (SMB) Protocol. The SMB protocol is a standard, generally secure system that creates a connection between servers and end users by sending responses and requests. | EternalBlue is a Windows exploit created by the US National Security Agency. The main function of EternalBlue was to exploit a vulnerabilities in the Microsoft implementation of the Server Message Block (SMB) Protocol. The SMB protocol is a standard, generally secure system that creates a connection between servers and end users by sending responses and requests. | ||
Doublestar is a backdoor tool. IT runs in kernel mode, which grants cybercriminals a high level of control over the computer system. Once it is installed, it uses three commands: ping – which sends a request to a server and checks it’s response, kill and exec, the latter of which can be used to load malware onto the server. | |||
WannaCry Static Analysis: | Doublestar is a backdoor tool. IT runs in kernel mode, which grants cybercriminals a high level of control over the computer system. Once it is installed, it uses three commands: ping – which sends a request to a server and checks it’s response, kill and exec, the latter of which can be used to load malware onto the server. <ref> Available at https://www.sciencedirect.com/science/article/pii/S0045790618323164 </ref> | ||
We present our discoveries, which are based on our static assessment of WannaCry. The host system has an Intel Core i7-4700MQ 2.40 GHz processor and 16 GB of RAM. The first VM was infected with WannaCry and ran Windows 7 SP1. The second virtual machine was set up to run REMnux, a free Linux toolset for reverse engineering and malware assessment. WannaCry samples were gathered from VirusShare. The worm component and the encryption component were both examined as executable files (Table I). | |||
===WannaCry Static Analysis:=== | |||
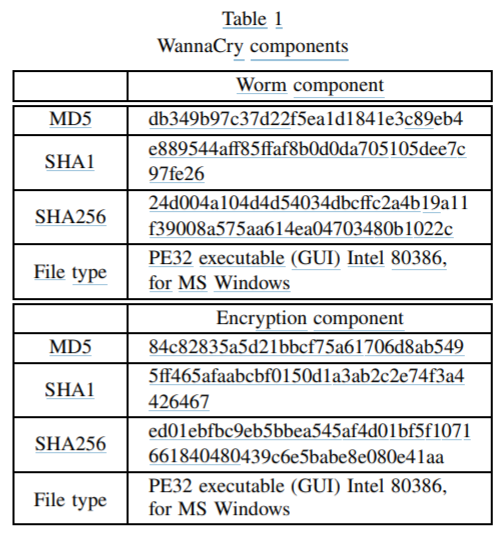
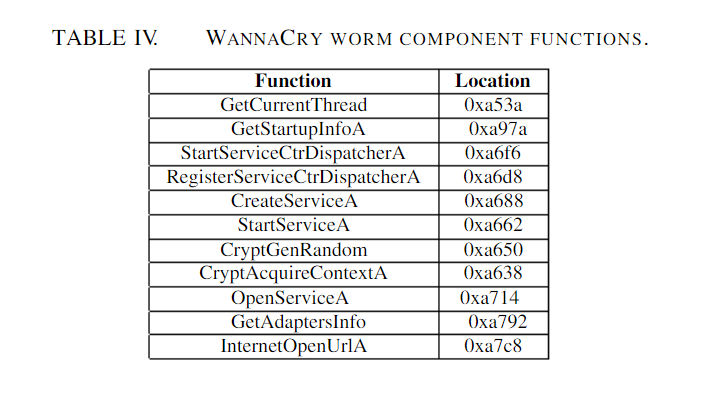
We present our discoveries, which are based on our static assessment of WannaCry. The host system has an Intel Core i7-4700MQ 2.40 GHz processor and 16 GB of RAM. The first VM was infected with WannaCry and ran Windows 7 SP1. The second virtual machine was set up to run REMnux, a free Linux toolset for reverse engineering and malware assessment. WannaCry samples were gathered from VirusShare. The worm component and the encryption component were both examined as executable files '''(Table I)'''. | |||
[[File:Wanna.PNG]] | |||
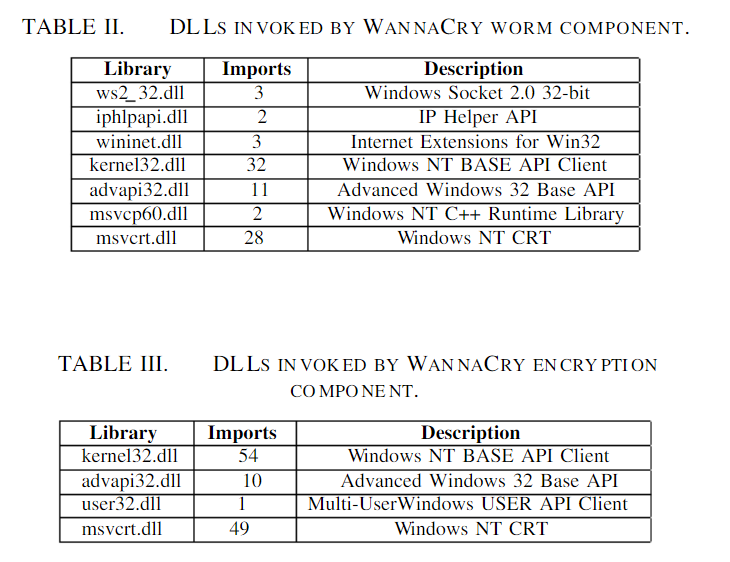
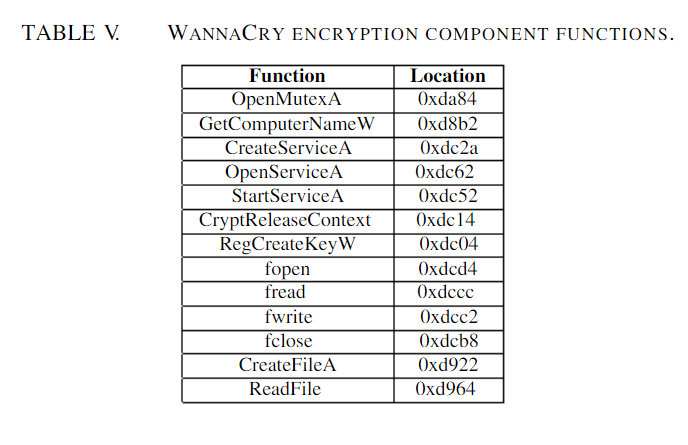
'''Tables II and III''' indicate that the worm and encryption components comprise dynamic-link libraries (DLLs), as determined by the Pestudio tool. During its execution, the worm accesses iphlpapi.dll to get the infected host's network configuration details. The encryption component uses the kernel32.dll and msvcrt.dll libraries the most. This might mean that these two libraries implemented the primary WannaCry encryption mechanism. The imported functions of the libraries were inspected using Pestudio to confirm this. WannaCry utilizes Microsoft's encryption, file management, and C runtime file application programming interfaces in general, as revealed in '''Tables IV and V'''. (APIs). To produce and maintain random symmetric and asymmetric cryptographic keys, the Crypto API library is utilized. | |||
[[File:Table2 3.PNG]] | |||
[[File:Table4.PNG]] | |||
[[File:Table5.PNG]] | |||
===WannaCry dynamic analysis:=== | |||
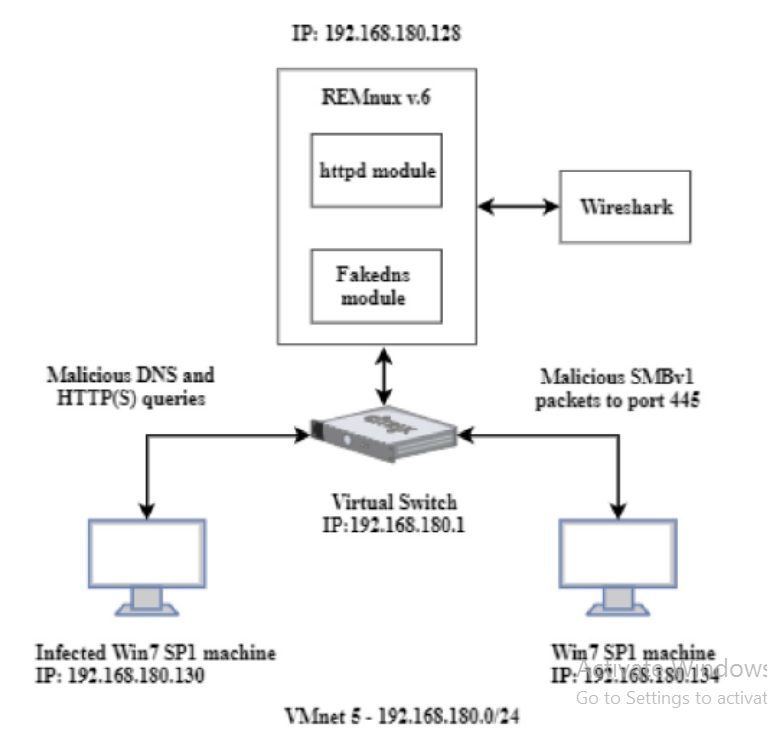
In this part, we provide the results of our WannaCry dynamic analysis. To this goal, the Fig.1 virtual test bed was created. With the Virtual Network Editor function in VMWare hypervisor, a custom network VMnet 5 -192.168.180.0/24 was established. This approach allows the worm component of WannaCry to monitor domain name system (DNS) requests made by WannaCry throughout the infection and replication phase via port 445 of the SMBv1 protocol across internal and external networks. | |||
[[File:Fig 1.PNG]] | |||
The REMnux system serves as a DNS and HTTP server, as well as intercepting all network traffic with Wireshark. The FakeDNS and HTTP Daemon tools were used to enable DNS and HTTP services in REMnux, respectively. Our dynamic analysis has revealed that, upon startup, the worm component tries to connect to the following domain, using the InernetOpenUrl function: | |||
'''''www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com''''' | |||
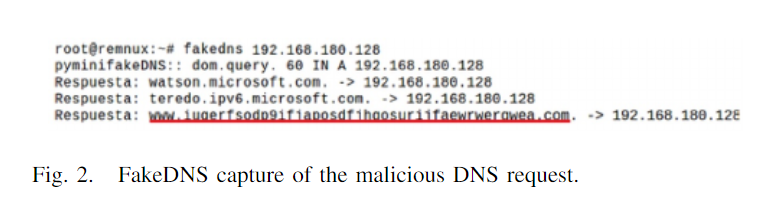
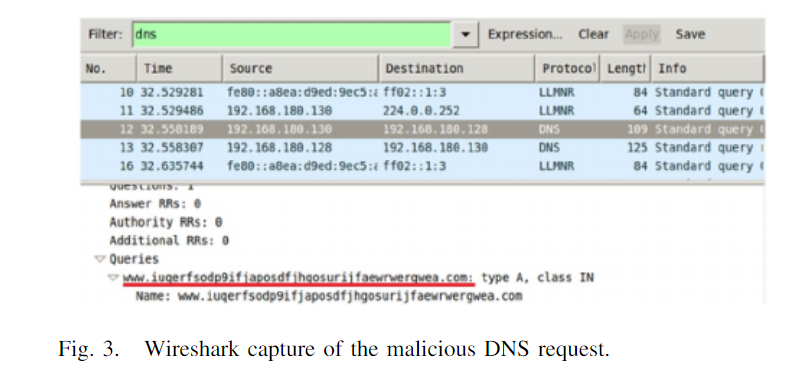
The domain in question is a kill-switch domain. The worm component stops executing if the domain is active. If the worm component is unable to connect to this domain (for example, if the domain is not operational or if connectivity is unavailable), it continues to operate and registers itself as a "Microsoft Security Center (2.0) Service" mssecsvs2.0 process on the infected computer. The malicious DNS request on port 80 is captured by the FakeDNS software at REMnux '''(Fig. 2)''', while the DNS packet query field from the infected computer (IP 192.168.180.130) to the REMnux DNS server is shown by Wireshark '''(Fig. 3)'''. (IP192.168.180.128). The worm component extracts the hardcoded R resource and transfers it to ''C:Windowstaskche.exe'' after installing itself as a service. The R resource represents the binary of the WannaCry encryption component. During its execution the encryption component checks if one of the following mutual exclusion objects (mutexes) exists: | |||
''GlobalnM sW inZ onesCacheC ounterM utexA'' | |||
''GlobalnM sW inZ onesCacheC ounterM utexW'' | |||
''M sW inZonesC acheCounterM utexA'' | |||
If the mutex is present on the system, the encryption component will freeze working and will not take any further actions. The encryption procedure will begin if this is not the case. The CryptGenRandom method is used to produce a unique 16-byte symmetric AES key for each file. Then, starting with the "WANACRY!" text value, each produced AES key is encrypted using the public RSA key (which is part of the encryption component) and saved within the file header. Encrypted files are renamed and given the extension .WNCRY. A password-protected ZIP archive is included in the encryption component. By dissecting the encrypter using the IDA Pro program, we were able to retrieve the password, <ref> Available at https://www.researchgate.net/publication/332144343_Static_and_Dynamic_Analysis_of_WannaCry_Ransomware </ref> ''"WNcry@2ol7."'' '''(Fig.4)''' | |||
[[File:Fig 2.PNG]] | |||
[[File:Fig 3.PNG]] | |||
[[File:Fig 4.PNG]] | |||
== References == | |||
{{Reflist}} | |||
Latest revision as of 18:18, 2 May 2022
Introduction
Malware is malicious software that can enter, and stay on your computer, and then perform actions without your consent, giving hackers full access to your data, and systems. The malware initially appeared as a form of cybervandalism. So it was used to change the computer's background tasks and access your personal information. Since then, these methods, adopted by cybercriminals, have begun to be used to track information and steal valuable business or personal data. [1]
Petya
Petya is a file-encrypting Trojan that was first discovered in 2016, according to information on 2SpyWare, which was launched as a project to help people learn more about cybersecurity issues and malware. [2]It has continued to appear in various variants with several different updates until today. Among its derivatives are PetrWrap, GoldenEye, Mamba virus, Mischa, Diskcoder.D, and Bad Rabbit. Petya has been one of the classic ransomware attacks in which the files on victims' computers are encrypted to make them inaccessible and then demand a ransom to give the encryption key. Ransoms are also typically demanded in bitcoin or other cryptocurrencies.[3] Its beginnings were similar to WannaCry; The epidemic was not noticed from anywhere and spread rapidly. However, unlike WannaCry, this malware spread via spam e-mails, immediately after restarting the computer, it displayed the following message on the screen.[4]
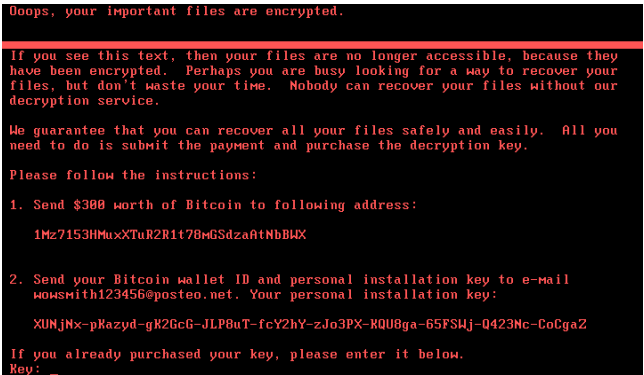
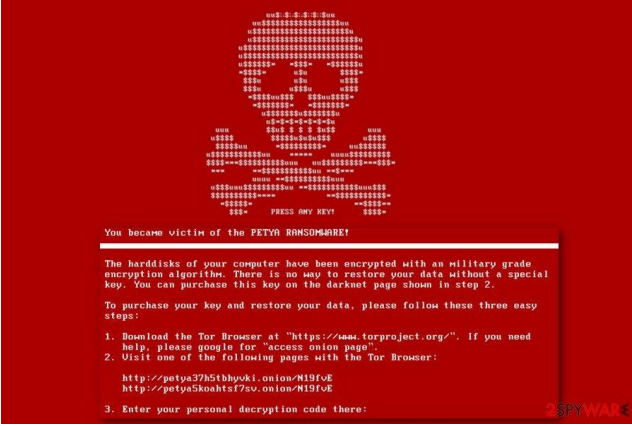
Although this screen may seem like a system error at first glance, users In fact, Petya software silently performed file encryption in the background of the system. If the user tries to reboot the system or the file encryption operation is performed, a flashing red skeleton appears on the screen, and “Press any key” appears. After pressing the key, a new window is opened with the ransom note [5]
One of the email domains associated with the perpetrators of the attack was revoked in the process, thus giving a victim's computer a specific code to help retrieve the matching decoder data recovery has become impossible.[6] It has been effective in countries such as Russia, England, France, Denmark, Iran, Brazil, and Mexico, especially in Ukraine. Spain, Netherlands, and India also confirmed the attack. Ukraine has suffered the most from the attack. Petya malware also envelops various public institutions of the country; In addition, it affected a wide area such as Kyiv Airport, metro systems, power plants, and nuclear power plants, bringing the systems to a standstill and causing many disruptions. [7] MeDoc, a Ukrainian software company, was held responsible for the attack that brought life to a standstill in Ukraine. Although MeDoc denies these allegations, many cybersecurity experts have claimed to have evidence that the firm was the first source. 55 Public authorities stated that the affected institutions had difficulties in carrying out customer service and banking transactions, it was observed that most of the ATMs were out of service or Petya's ransomware message was displayed on their screens. [8]
Considering that it is also exposed to similar attacks, it is understood that it is a political attack aimed at creating confusion in the country rather than for a financial purpose.[9] It has been understood that many systems do not have enough defense against ransomware. The extent of such attacks has also revealed the widespread inadequacy of awareness of cyber security, vulnerability scanning, testing, use of correct cyber security applications, and taking backups. It can also be said that Petya, which aims to render the system unusable rather than encrypting the files, aims to have a devastating effect rather than money. [10]
SamSam
The most comprehensive research report on ransomware named SamSam, which was first seen in December 2015 and started to spread in 2016, belongs to the global cyber security company Sophos. [11] According to the report published in April 2018, unlike most of the well-known ransomware families that randomly attack, SamSam has been used against certain organizations that are predicted to be most likely to pay to get their data back, such as hospitals or schools. Instead of spam campaigns, the cybercriminals behind SamSam exploited vulnerabilities to access victims' networks or use brute-force tactics against weak passwords of the Remote Desktop Protocol (RDP). [12]This is the main feature that distinguishes SamSam from other ransomware attacks. [13] The process, which is designed to cause the highest level of damage to the IT infrastructure of the victim selected institution in the shortest time, is based on the fact that a person or group who is skilled in infiltrating the systems detects the weaknesses in the infiltrating network and manually runs the malware there. After potential targets were discovered, attackers manually deployed SamSam malware to selected systems using tools such as PSEXEC and batch scripts. The first victim of the attack was Atlanta. [14]The attack resulted in severe digital blackouts in five of the city's 13 local government units. The attack had far-reaching effects, including disrupting the court system, preventing residents from paying their water bills, limiting vital communications such as sewer infrastructure requests, and forcing the Atlanta Police Department to work with pen and paper instead of computers. [15] The ransom amount demanded is around $50,000. It was reported in the press that over 2.6 million dollars were spent at the first stage to eliminate these attacks. The majority of the spending is related to emergency response to systems recovery, forensics, and additional staffing. [16] In addition, it was reported in the press that he spent an additional $650 thousand on a crisis communication center and emergency response consultancy. exceeded the dollar. [17]
Some striking data from this report are as follows:
- 74 percent of known victims are located in the USA. Canada, the United Kingdom, and the Middle East countries are among the countries most affected by the attack. [18]
- According to transfers made in Bitcoin, SamSam attackers managed to extort ransoms of up to 64 thousand dollars from individual victims at once.
- Following the emergence of the SamSam attack, new versions were also developed, more complex attack methods were used in each new version, and it was observed that more competent measures were taken to protect from operational security measures in order not to leave traces. [19]
- SamSam attackers targeted medium to large-sized public sector institutions in the fields of health, education and government at 50 percent, and private sector companies at 50 percent.
- The attackers' preparation for the attack is meticulous. SamSam attackers waited for the opportune moment; they initiated encryption commands at midnight when most users were asleep, or in the early morning hours of the victim's local time zone. In the SamSam example, after attackers had successfully infected a server, they also created additional victimization by stealing network mapping and credentials. It would be appropriate to interpret this attack as a professional diamond theft rather than a simple theft. Because both the attack method and the targeted critical institutions are the basic foundations of this determination.
Stuxnet
Stuxnet, a malicious computer worm that was made for attacking Iran’s nuclear facilities, the specific target was hardware and crippling it, by taking control and changing PLCs (Programmable Logic Controllers) that were used to automate the machine processes that took place in the facilities. The worm was initially discovered in 2010, but which had been evolving and spreading ever since it’s discovery.
Workings of Stuxnet
Composition
Stuxnet is composed of three components: a worm, a link file and a rootkit.
The link file automatically executes the copies the worm, which exploits a vulnerability in the way Windows displays the icons of shortcut files.
The worm executes all routines related to the main payload of the attack. It implements a Microsoft Remote Procedure Call to execute certain functions, effectively enabling affected systems to communicate with one another. With the inclusion of tests, that check for an active Internet connection on the affected system to communicate with a remote server, which holds the copies of the worm. [21]
The rootkit is the main component responsible for hiding all the malicious files and processes, to stay undetected by the user and anti-virus software.
Use of P2P
Stuxnet installs both server and client components for a Microsoft Remote Procedure Call in all infected systems and versions. After connecting to a system, it would do the following procedure: Getting malware version, receiving module and injecting it, send the malware file, create a process that would be command shell or a file, create a file, delete a file and then read a file. [22]
All affected systems would have a UUID (Universally Unique Identifier) to use for communication between systems for updating each other.
The remote server
Firstly it tries to connect with a URL: "www.windowsupdate.com" or "www.msn.com". Then after it has identified that internet connection is available, it would connect with a user with a URL: "www.{BLOCKED}erfutbol.com" or "www.{BLOCKED}futbol.com". After it has connected with the malicious user, a URL is generated “http://www.{BLOCKED}erfutbol.com/index.php?data={data}”, where {data} is an encrypted hex value that contains the IP address of the machine, computer name, and domain.
History
The earlier versions of Stuxnet could spread only by infecting Step7 project files, which were the files that were used to program the PLCs, but later versions could also spread via USB flash drives, using a Windows feature called “Autorun” or through a local network with print-spooler exploit. The reasoning for adding increased spreadability of Stuxnet by the creators was to increase the odds of a successful attack on companies related to Iran’s nuclear production, from manufacture to installment side of things. The companies provided a gateway via infected employees for the worm to enter Natanz, which was the location of the Iran’s uranium-enrichment plant or Būshehr, which was the location of a nuclear reactor. The attack took place in June 2009, with the first company to get infected was Follad Technic, then a week after Behpajooh was hit and then another nine days for Neda Industrial Group to also get struck. The size of the worm was 500KB and infected the software of at least 14 industrial sites. [23] The reason for the virus to be unnoticed for about a year after the initial attack was due to the fact that it was also giving false data, in the sense that the data indicated that everything was running fine and smoothly, when in truth it was not. While there were early notifications about the Step 7.DLL file producing errors and that the problem was consistent when using a flash drive to transfer files, when before it was a clean computer, there were no errors. The biggest giveaway was when new machines were being installed about five months after the early notifications, none of the newer machines were being fed gas as they were in the process of being installed, but the systems monitors SCADA (Supervisory Control and Data Acquisition), were showing data, as if gas was being fed into the machines. While the Iranian nuclear program continued to suffer technical difficulties, people were speculating that the worm originated as a co-op program by United States and Israel, called “Olympic Games”. The virus started spreading on a global scale via employees and the general public, targeting industrial control systems and causing massive damages, data showed that approximately 100k computers were infected by the end of 2010, with more than 60% allocated in Iran. The damages were only increasing, due to the sheer number of people plugging USB flash drivers into multiple storage devices, effectively re-infecting and spreading systems around the globe. No infrastructure was safe and targets were any and all industrial control systems.
Stuxnet family
In the following years after the initial attack in 2009 and the continuous damages throughout until late 2010, many related malwares were developed from the same type of worm virus as the original Stuxnet. [24]
Duqu (2011)
Being nearly identical to Stuxnet, but having a different purpose. Based on original code (Stuxnet) main function was to capture and log information, such as keystrokes, mining data and system information from industrial facilities, presumably to launch an attack at a later date. Reported cases have been in at least eight countries.
Flame (2012)
Flame module exploits the same vulnerabilities for spreading as Stuxnet did. It was a sophisticated spyware that logged keystrokes, recorded conversations (e.g. Skype), gathered screenshots and many other data collection activities. Main targets of Flame were government and educational organizations and some private individuals mostly in Iran and other Middle Eastern countries. [25]
Havex (2013)
Havex was used in a widespread espionage campaign targeting energy, aviation, pharmaceutical, defense and petrochemical sectors, with the primary targets being in the United States, Europe and Canadian organizations. [26]
Industroyer (2016)
The only targets for Industroyer was power facilities. Cyberattack on Ukraine’s power grid, casuing a power outage in December.
Triton (2017)
Was discovered in Saudi Arabia, when it made safety systems defective in a petrochemical plant. Increasing the odds of physical injury to workers.
Stuxnet 2.0 (2018)
The target was Iran, as with original Stuxnet, but this time the target was the telecom infrastructure. [27]
“Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon”, written by Kim Zetter, explains the events regarding Stuxnet in further detail.
Melissa
Back in the day, not much information was known to an average computer user about computer viruses and their methods of spreading. However, in March 1999 [28], that would be changed forever. A programmer named David Lee Smith [29] hacked into an America Online (AOL) [30] account and used it to post a file on a newsgroup page, named “alt.sex”, which promised a list of many passwords for otherwise fee-based websites with adult content. This was one of the first massive-scale phishing [31] attacks that are known to us today. When a user
took the bait by downloading the attached file, it unleashed a virus into their computers. The Melissa virus, reportedly named by Smith after the name of a stripper he met in Florida, begun by taking over victims’ Microsoft Word program. It at that point utilized a macro Microsoft Outlook mail framework and sent messages to the first 50 addresses in their mailing records. Those messages, in turn, tempted receivers to open an attachment with a virus. The message of the e-mail read “Here is the document you requested ... don’t show anyone else ;-):” people trusted the sender and thus were willing to download the attachment, but the senders had no idea that their mail contacts had received the message. The virus was not aiming to steal money or data, but it damaged systems, nonetheless. E-mail servers at more than 300 organizations and government agencies around the world got to be overloaded, and a few had to be closed down totally, including Microsoft. Within a few days, cybersecurity specialists had for the most part contained the spread of the virus and reestablished the functionality of their networks, in spite of the fact that it took some time to remove the contaminations totally. Still, the collective damage was colossal: an evaluated $80 million for the cleanup and repair of affected computer frameworks.
The Legacy Of Melissa Worm
- Love Bug (2000) [32] - The Love Bug, also known as ILOVEYOU, LoveLetter or VBS/LoveLet, spread itself via email using the subject line “ILOVEYOU” and the message body “Kindly check the attached LOVELETTER coming from me”. It overwrote files and hid some Mp3 files as well.
- Anna Kournikova (2001) [33] - The Anna Kournikova worm wasn’t especially sophisticated in design. It was a standard e-mail worm composed in Visual Basic Script (VBS), which sent itself through emails utilizing details it collected from your Microsoft Outlook address book.
- Netsky (2004) [34] - The worm was sent out as an e-mail, enticing recipients to open an attachment. Once opened, the attached program would scan the computer for e-mail addresses and e-mail itself to all addresses found. It contained a 22,016 byte file attachment and was reportedly causing Denial of Service (DoS) attacks because networks got clogged and couldn’t handle the traffic
Zeus Trojan
While talking about the top malware attacks in history, the Zeus Malware is one of those which cannot be omitted. The Zeus Trojan is a malicious software aiming to harm the gadgets having the operating system Microsoft Windows by stealing financial data. Its first detection dates back to 2007. This virus is also known for its other name, Zbot. [35] The Zeus Trojan has obtained great success in terms of thieving information. According to the researches, millions of systems have been damaged by this Trojan, and billions of dollars were stolen. [36] After providing this primary information about the above-mentioned malware, it’s time to dive deeper and learn much more.
Initially, let’s take a look at what it executes on the gadgets. The 2 main features of the Zeus Trojan are always underlined; the creation of Botnets and thieving financial data. To begin with, The Zbot establishes botnets. The Botnet is considered the network of the infected nodes. By setting up such botnets, the Zbot owner obtains control over all those nodes. More precisely, with the help of Botnets, their owner becomes capable of collecting data and operating attacks. Secondly, the Zbot is counted as also a Trojan being able to steal the banking credentials. Keylogging and Monitoring are the methods it uses to reach to having stolen the banking data. Acting as a financial Trojan makes Zbot a Crimeware. [37]
ZBOT Spreading Methods
Time to explore how Zbot works. There are 2 main ways that the Zbot uses for spreading; spam messages, and drive-by downloads. Likewise the other malware forms, spam messages are preferred also by the Zbot. The hackers send thousands of spam e-mails or compose social media campaigns that redirect the users to websites in which the Trojan is automatically installed on the user’s computer. Despite the fact that the Zbot had mainly been used for obtaining banking credentials, its ability to steal can also be used to hijack other users’ social media accounts and e-mails. As mentioned above, there is another method called “Drive-by downloads” that the Zbot uses to spread. The hackers can infect some legitimate and quite reliable websites by inserting the Trojan into them. In case of visiting or downloading a file from such websites, the malware would be installed on the user gadget. [38]
Famous Zeus Variants
Although there are thousands of Zeus Trojan variants, some of them are more popular due to their characteristics and the damage they caused. Floki Bot, Gameover Zeus, and Zeus Atmos are some of those noteworthy variations.
Floki Bot takes its name from a Brazilian hacker with the username “flokibot”. This form of Zeus was detected for the first time in 2016. Evasion techniques, and using of the Tor browser are some features that Floki Bot obtained while it was gradually developing in its first months. The foremost factor making Floki Bot irregular is its ability to target the POS (Point of Sale) systems. It is reported that the malware has been targeting the Canadian, American and Brazilian banks, and insurance companies. [39]
Gameover or Gameover P2P is another Zeus variant to study. As its name suggests, this Zeus variation is mainly famous for using P2P (peer-to-peer) connections. Once it finds out what it is looking for in the infected computers, it shares that data with the other nodes, and of course the control server too. Apart from the data transmission, Gameover is also able to install other malwares, and interrupt some operations. [40]
Citadel is also quite a dangerous variation of the Zeus Trojan. It is even able to create an IoT botnet. This variant mainly targets Password managers. In most cases, Citadel is installed through drive-by-downloads. It was first detected in 2011 and has infected about 11 million systems in the next 6 years. The total damage it brought about is approximately 500 million dollars. [41]
The recent years have witnessed a new variant of Zeus, called Atmos. This is a pretty new version of Zeus and has deployed a feature – dropping Ransomware. Just after this Zeus variant steals the data, it installs Ransomware. Like the other Zeus forms, it also majorly aimed at stealing banking credentials. Despite the fact that Atmos attacks were operated against banks, this is also expected that other industries be subjected to similar attacks in the future. [42]
Damage of the ZBOT
While analyzing the damage Zbot has caused, it’s better to study the periods in which the malware has obtained its peak performance – from its first detection (2007) to the times its source code was leaked out (2011). According to the data, approximately 44% of the malware attacks in the banking sector in 2010 were Zeus-based. The same report says a total of 960 banks were subjected to Zbot attacks. In addition, over 3.6 million computers were infected only in the USA. This is estimated that in the first 3 years of Zbot, the damage it caused was approximately 100 million US dollars. The anti-malware tools used at these times were mainly ineffective against the Zbot. So that they could block Zbot only in 23% of total cases.[43]
Prevention methods from the Zeus Trojan
In fact, one of the best courses of one’s action on securing own gadget should be increasing Internet awareness. Taking the Zbot’s spreading ways into account, it becomes blatant why the internet awareness or in other words, safe internet practices are that important. A prime example would be deviating from unsafe websites that in most cases offer illegitimate software/ downloads/ bet, and adult content, and so on. As a matter of fact, internet awareness is not only about websites containing malicious content. Phishing e-mails should also be taken into account. Omitting the e-mails while not expecting any from anyone is also a good practice since the e-mails sent from even quite trusted sources can also be infected with the Zeus Trojan.
Secondly, considering the fact that the Zeus Trojan has generally been developed for stealing banking data, this is also recommended to use 2-factor authentication for banking logins. In such cases, a confirmation code is sent to the smartphone having a pre-registered sim card. This feature is today offered by many bank websites and definitely increases security against such financial malwares.
Next and most importantly, there have to be installed antiviruses on the computer. In case of being infected, such antimalware tools are able to contribute throughout the whole life span of malware. Initially, antiviruses do not allow the user to visit malicious websites. If the user somehow does, then the antiviruses halt the malware to be downloaded and installed, and even if it infects the gadget, then the antivirus detects and removes the malware. Hence, making use of antivirus must be a foremost option for an end-user in the terms of protecting their own gadget. [44]
Is Zeus till a threat?
In fact, the developer who created Zbot is not currently making use of it. However, since its source code is on the internet, it is gradually upgraded by the other hackers and newer variations continue emerging. Hence, it can be said that the Zeus Malware is alive. Despite the fact that Ransomware has gained more popularity in recent years, Zbot and its variants are still active. [45] Taking the threats that may potentially stem from the above-mentioned malwares into consideration, it again becomes clear why measurement actions, like safe Internet practices, and implementing Safeguards play a vital role in the prevention of such malware attacks.
WannaCry
On May 12, 2017, the WannaCry ransomware (also known as Wana Decrypt0r, WCry, WannaCry, WannaCrypt, and WanaCrypt0r) was discovered during a large-scale assault affecting numerous nations. WannaCry is a crypto worm cyber-attack that was targeted to computer, laptops, and devices running the Microsoft Windows operating system.
On 13 May, 2017 hackers started to spread a ransomware to computers around the globe. According to Europol, more than 300,000 computers in 150 countries have been victims of the cyberattack, which involved the request of a 300$ ransom in order to return control of the encrypted files. The WannaCry ransomware took advantage of an inherent vulnerability. [46]
How does it considered as a crypto–worm?
It is considered as a worm because it included a transport mechanism to automatically spread itself. Wannacry malware could spread from computer to computer and from network to network. That’s how it was spread over the world. [47]
How does transport mechanism worked?
The transport mechanism used transport code which scans for vulnerable systems, and then it uses the EternalBlue exploit to gain the access. After that it used DoublePulsar tool to install and copy itself.
What is EternalBlue and DoublePulsar?
EternalBlue is a Windows exploit created by the US National Security Agency. The main function of EternalBlue was to exploit a vulnerabilities in the Microsoft implementation of the Server Message Block (SMB) Protocol. The SMB protocol is a standard, generally secure system that creates a connection between servers and end users by sending responses and requests.
Doublestar is a backdoor tool. IT runs in kernel mode, which grants cybercriminals a high level of control over the computer system. Once it is installed, it uses three commands: ping – which sends a request to a server and checks it’s response, kill and exec, the latter of which can be used to load malware onto the server. [48]
WannaCry Static Analysis:
We present our discoveries, which are based on our static assessment of WannaCry. The host system has an Intel Core i7-4700MQ 2.40 GHz processor and 16 GB of RAM. The first VM was infected with WannaCry and ran Windows 7 SP1. The second virtual machine was set up to run REMnux, a free Linux toolset for reverse engineering and malware assessment. WannaCry samples were gathered from VirusShare. The worm component and the encryption component were both examined as executable files (Table I).
Tables II and III indicate that the worm and encryption components comprise dynamic-link libraries (DLLs), as determined by the Pestudio tool. During its execution, the worm accesses iphlpapi.dll to get the infected host's network configuration details. The encryption component uses the kernel32.dll and msvcrt.dll libraries the most. This might mean that these two libraries implemented the primary WannaCry encryption mechanism. The imported functions of the libraries were inspected using Pestudio to confirm this. WannaCry utilizes Microsoft's encryption, file management, and C runtime file application programming interfaces in general, as revealed in Tables IV and V. (APIs). To produce and maintain random symmetric and asymmetric cryptographic keys, the Crypto API library is utilized.
WannaCry dynamic analysis:
In this part, we provide the results of our WannaCry dynamic analysis. To this goal, the Fig.1 virtual test bed was created. With the Virtual Network Editor function in VMWare hypervisor, a custom network VMnet 5 -192.168.180.0/24 was established. This approach allows the worm component of WannaCry to monitor domain name system (DNS) requests made by WannaCry throughout the infection and replication phase via port 445 of the SMBv1 protocol across internal and external networks.
The REMnux system serves as a DNS and HTTP server, as well as intercepting all network traffic with Wireshark. The FakeDNS and HTTP Daemon tools were used to enable DNS and HTTP services in REMnux, respectively. Our dynamic analysis has revealed that, upon startup, the worm component tries to connect to the following domain, using the InernetOpenUrl function:
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
The domain in question is a kill-switch domain. The worm component stops executing if the domain is active. If the worm component is unable to connect to this domain (for example, if the domain is not operational or if connectivity is unavailable), it continues to operate and registers itself as a "Microsoft Security Center (2.0) Service" mssecsvs2.0 process on the infected computer. The malicious DNS request on port 80 is captured by the FakeDNS software at REMnux (Fig. 2), while the DNS packet query field from the infected computer (IP 192.168.180.130) to the REMnux DNS server is shown by Wireshark (Fig. 3). (IP192.168.180.128). The worm component extracts the hardcoded R resource and transfers it to C:Windowstaskche.exe after installing itself as a service. The R resource represents the binary of the WannaCry encryption component. During its execution the encryption component checks if one of the following mutual exclusion objects (mutexes) exists:
GlobalnM sW inZ onesCacheC ounterM utexA
GlobalnM sW inZ onesCacheC ounterM utexW
M sW inZonesC acheCounterM utexA
If the mutex is present on the system, the encryption component will freeze working and will not take any further actions. The encryption procedure will begin if this is not the case. The CryptGenRandom method is used to produce a unique 16-byte symmetric AES key for each file. Then, starting with the "WANACRY!" text value, each produced AES key is encrypted using the public RSA key (which is part of the encryption component) and saved within the file header. Encrypted files are renamed and given the extension .WNCRY. A password-protected ZIP archive is included in the encryption component. By dissecting the encrypter using the IDA Pro program, we were able to retrieve the password, [49] "WNcry@2ol7." (Fig.4)
References
- ↑ Definition for Malware from Cisco https://www.cisco.com/c/en/us/products/security/advanced-malware-protection/what-is-malware.html
- ↑ Available at https://www.bbc.com/news/technology-40497026
- ↑ Available at https://fortune.com/2017/06/27/petya-ransomware-ukraine-medoc/
- ↑ Available at https://www.proofpoint.com/us/threat-reference/petya
- ↑ Available at https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/petya.html
- ↑ Available at https://www.theguardian.com/technology/2017/jun/27/petya-ransomware-cyber-attack-who-what-why-how
- ↑ Available at https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/petya-ransomware-wiper
- ↑ Available at http://services.nwu.ac.za/it-news/latest-cyber-attack-petya-ransomware
- ↑ Available at https://www.inverse.com/article/33469-petya-ransomware-attack-united-states
- ↑ Available at https://thehackernews.com/2017/06/petya-ransomware-decryption-key.html
- ↑ Available at https://www.nomios.com/resources/what-is-samsam-ransomware/
- ↑ Available at
- ↑ Available at https://blog.malwarebytes.com/cybercrime/2018/05/samsam-ransomware-need-know/
- ↑ Available at https://heimdalsecurity.com/blog/samsam-ransomware/
- ↑ Available at https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/samsam-targeted-ransomware-attacks
- ↑ Available at https://blogs.blackberry.com/en/2018/11/pro-tips-on-how-to-avoid-a-samsam-ransomware-infection
- ↑ Available at https://www.securityweek.com/dhs-says-samsam-ransomware-targeting-critical-infrastructure-entities
- ↑ Available at https://www.tzcert.go.tz/wp-content/uploads/2018/12/SamSam-Ransomware-Security-Notice.pdf
- ↑ Available at https://blog.knowbe4.com/samsam-ransomware-infected-thousands-of-labcorp-systems-via-brute-force-rdp
- ↑ Available at https://www.lepide.com/blog/how-can-hospitals-protect-themselves-from-samsam-ransomware-attacks/
- ↑ Available at https://www.wired.com/2014/11/countdown-to-zero-day-stuxnet/
- ↑ Available at https://spectrum.ieee.org/the-real-story-of-stuxnet/
- ↑ Available at https://www.britannica.com/technology/Stuxnet
- ↑ Available at https://www.britannica.com/technology/Stuxnet
- ↑ Available at https://arstechnica.com/tech-policy/2012/06/confirmed-us-israel-created-stuxnet-lost-control-of-it/
- ↑ Available at https://web.archive.org/web/20170904015230/https://www.mac-solutions.net/en/news/129-sheep-dip-your-removable-storage-devices-to-reduce-the-threat-of-cyber-attacks
- ↑ Available at https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/what-is-stuxnet.html
- ↑ Available at https://en.wikipedia.org/wiki/Portal:Current_events/March_1999
- ↑ Available at https://en-academic.com/dic.nsf/enwiki/732114
- ↑ Available at https://www.aol.com/?guccounter=1&guce_referrer=aHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS8&guce_referrer_sig=AQAAAEqgHrJ4kQ8wKq0IQkqZlaGRluN3Lm_hIyBY_2QCZT9cZQCtb2P0IlngfiR4QtSx3jEM3QhUkBDsFtj-04EKUviBY2qVuM_5HP7AFxB8F5YzBYidTYosRJ7xlQcZJoWwl0NMdSjNaVmdlzqPvLAiirBg3A0ukMHaARtVHZu9oFdM
- ↑ https://csrc.nist.gov/glossary/term/phishing
- ↑ Available at https://www.wired.com/story/the-20-year-hunt-for-the-man-behind-the-love-bug-virus/
- ↑ Available at https://nakedsecurity.sophos.com/2011/02/11/memories-anna-kournikova-worm/
- ↑ Available at https://malwiki.org/index.php?title=Netsky
- ↑ Available at https://www.digitaldefense.com/blog/zeus-trojan-what-it-is-how-to-prevent-it-digital-defense/
- ↑ Available at https://blog.malwarebytes.com/101/2021/07/the-life-and-death-of-the-zeus-trojan/
- ↑ Available at https://usa.kaspersky.com/resource-center/threats/zeus-virus
- ↑ Available at https://usa.kaspersky.com/resource-center/threats/zeus-virus
- ↑ Available at https://www.cyber.nj.gov/threat-center/threat-profiles/trojan-variants/floki-bot
- ↑ Available at https://www.ryadel.com/en/zeus-malware-what-how-prevent/
- ↑ Available at https://www.wallarm.com/what/what-is-citadel-malware
- ↑ Available at https://www.kaspersky.com/blog/atmos-yet-another-zeus-variant-is-threatening-businesses/5476/
- ↑ Available at https://botnetlegalnotice.com/citadel/files/Guerrino_Decl_Ex1.pdf
- ↑ Available at https://usa.kaspersky.com/resource-center/threats/zeus-virus
- ↑ Available at https://blog.malwarebytes.com/101/2021/07/the-life-and-death-of-the-zeus-trojan/
- ↑ Available at https://ieeexplore.ieee.org/document/8260673
- ↑ Available at https://asia.nikkei.com/Politics-Economy/International-Relations/North-Korea-capable-of-hacking-with-WannaCry-ransomware
- ↑ Available at https://www.sciencedirect.com/science/article/pii/S0045790618323164
- ↑ Available at https://www.researchgate.net/publication/332144343_Static_and_Dynamic_Analysis_of_WannaCry_Ransomware