Logging&monitoring: Difference between revisions
From ICO wiki
Jump to navigationJump to search
No edit summary |
|||
| Line 30: | Line 30: | ||
<span style="color:#FF0000"> | <span style="color:#FF0000"> | ||
'''Server machine ip address 192.168.56.200''' | '''Server machine ip address 192.168.56.200''' | ||
*Can be connected over ssh with student@192 | *Can be connected over ssh with student@192.168.56.200 | ||
<span style="color:#FF0000"> | <span style="color:#FF0000"> | ||
'''IDS ip address 192.168.56.201''' | '''IDS ip address 192.168.56.201''' | ||
Revision as of 17:18, 24 September 2016
Team Artur Ovtsinnikov Etienne Barrier Meelis Hass Mohanad Aly
Group : Cyber Security Engineering (C21)
Page Created: 18 September 2016
Last modified:
Aim of this page
- logging and monitoring.
- The best solution for logging
- Threats.
- Securing during logging
Topology of the system
Desktop machine
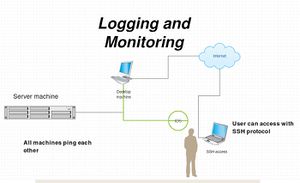
Begin with the basic setup, network configuration and make the machine has internet access which the ip address of the machine is 192.168.56.100
Server machine ip address 192.168.56.200
- Can be connected over ssh with student@192.168.56.200
IDS ip address 192.168.56.201
Starting to update an upgrade for all machines
- First be super user
sudo -i
apt-get update
apt-get upgrade