Hiring a Cyber Security Incident Analyst: Difference between revisions
| Line 337: | Line 337: | ||
but readiness to learn and moderate knowledge of different operation | but readiness to learn and moderate knowledge of different operation | ||
systems is enough to start the career. <ref name="cv">cv.ee, "SEIRESPETSIALIST - tule Eesti küberruumi valvuriks!". Available: https://www.cv.ee/en/vacancy/792782/riigi-infosusteemi-amet/seirespetsialist-tule-eesti-kuberruumi-valvuriks [Accessed 28 April 2022].</ref> | systems is enough to start the career. <ref name="cv">cv.ee, "SEIRESPETSIALIST - tule Eesti küberruumi valvuriks!". Available: https://www.cv.ee/en/vacancy/792782/riigi-infosusteemi-amet/seirespetsialist-tule-eesti-kuberruumi-valvuriks [Accessed 28 April 2022].</ref> | ||
[[File:Analystimage7.png|500px|thumb|Comparison degree vs Certificate <ref>"Comparison Table". Available at https://www.franklin.edu/blog/is-a-masters-degree-in-cyber-security-worth-it</ref>]] | |||
Nevertheless, like most other high qualification careers jobs falling | Nevertheless, like most other high qualification careers jobs falling | ||
under the cybersecurity specialist category require some form of formal | under the cybersecurity specialist category require some form of formal | ||
| Line 351: | Line 352: | ||
benefits and/or drawbacks of each type of credential. | benefits and/or drawbacks of each type of credential. | ||
<ref name="franklin">Franklin University, "Is Getting a Master's Degree in Cyber Security Worth It?". Available: https://www.franklin.edu/blog/is-a-masters-degree-in-cyber-security-worth-it [Accessed 28 April 2022].</ref> | <ref name="franklin">Franklin University, "Is Getting a Master's Degree in Cyber Security Worth It?". Available: https://www.franklin.edu/blog/is-a-masters-degree-in-cyber-security-worth-it [Accessed 28 April 2022].</ref> | ||
Certifications are generally good for people with little practical | Certifications are generally good for people with little practical | ||
experience because they are known quantities in the industry and can | experience because they are known quantities in the industry and can | ||
Revision as of 17:35, 1 May 2022
A Cyber Security Incident Analyst
Cyber security incident analyst in SOC/CSIRT/CERT
This article delves into the job title of Cyber Security Incident Analyst and provides an overview of the acronyms SOC/CSIRT/CERT. A brief history of the job is discussed here, as well as a possible career path, education, experience, and other characteristics required for work in computer security-related organizations. The article also provides a brief history of SOC/CSIRT/CERT, as well as a comparison of their differences and similarities.
Cyber Security Incident Analyst Skill Set
What skill set is expected from the Cyber Security Incident Analyst? Below written lines are taken from the same job advertisement depicted on the left side of this article: As a Security Incident Analyst your responsibilities will include:
- Continuous monitoring of security tooling
- Performing regular and ad-hoc vulnerability assessments
- Carrying out ‘spot checks’
- Reporting vulnerabilities to the PVG via the alerts system
- Maintaining and documenting logging systems
- Developing centralized logging, reporting and intelligence platforms
- ‘Light touch’ penetration testing with open source tooling (Metasploit)
Knowledge & Experience required:
- SOC, CSIRT or CERT operational environment experience
- Windows / Linux experience
- TCP /IP networking protocol knowledge
- Experience reviewing and analyzing Security Events from various monitoring and logging sources
- Experience in website and web application security assessment or penetration testing
- Experience of using Metasploit
- Scripting knowledge using BASH, Python, Perl, Ruby
- Skills in Host and Network Forensics
As one can see the description of the duties is wide and also the knowledge and experience that is required is noteworthy. So, where to start to find out the way to get this kind of knowledge and expertize.
Possible career path
Next part of the paper is aiming to depict a possible ways, how to develop oneself, and move along the career pathway in cybersecurity field. Topics of development, education, experience and certification are covered.
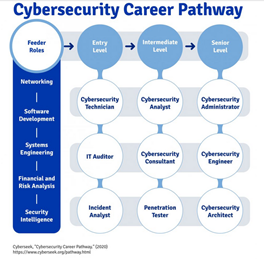
Junior/Senior
Start with an entry-level job in IT. Hands-on experience is often the most effective way to prepare for certification exams. Start accumulating work experience with an entry-level role as a cybersecurity analyst. Many cybersecurity professionals start off in more general IT roles. The skills, practices, and technologies you’ll use as a cybersecurity professional will continue to evolve along with computer and network technology. The desire to learn, ability to problem solve, and attention to detail will serve you well in this field. Other, more technical skills and technologies to learn include:[3]
SIEM tools (security information and event management)
Security Information and Event Management (SIEM) is a set of tools and services offering a holistic view of an organization’s information security. SIEM works by combining two technologies:
Firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems(IPS)
Firewalls can be two types, hardware and software firewalls. Software firewall is a firewall that is installed on a computer or server, and tasked with network security. It works with a wide variety of other technology security solutions to provide more robust and cohesive security for enterprises of all sizes. When a software firewall is installed on a server, it opens up like an umbrella of protection over all other computers connected to the network. It is able to monitor both incoming and outgoing traffic for potential risk or suspicious user behavior, and also makes setting security policies much easier, faster and more flexible. Hardware firewall is positioned between the network and devices, allowing traffic to funnel through the firewall for a close inspection and analysis. A hardware firewall, a term often interchangeable with network or next-generation firewall, protects the network gateways for an enterprise. Hardware firewall is physical hardware, installed between network elements and connected devices, and is tasked with filtering traffic for cyber threat to the network or devices. Filtering out unauthorized or suspicious users based on traffic analysis is one of the biggest benefits of hardware firewall. [5]
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are both parts of the network infrastructure. IDS/IPS compare network packets to a cyberthreat database containing known signatures of cyberattacks — and flag any matching packets. IDS doesn’t alter the network packets in any way, whereas IPS prevents the packet from delivery based on the contents of the packet, much like how a firewall prevents traffic by IP address. [6]
Digital forensics
Digital forensics is a branch of forensic science that focuses on identifying, acquiring, processing, analyzing, and reporting on data stored electronically. Electronic evidence is a component of almost all criminal activities and digital forensics support is crucial for law enforcement investigations. Electronic evidence can be collected from a wide array of sources, such as computers, smartphones, remote storage, unmanned aerial systems, shipborne equipment, and more.[7] Investigative process of digital forensics can be divided into several stages. There are four major stages: preservation, collection, examination, and analysis. All these four stages need a deep understanding of computers, technology across a broad spectrum, and cybersecurity principles and practices, a working knowledge of computers, networks, and coding, in-depth investigative abilities, critical-thinking skills and analytical talent the ability to effectively communicate and work with a wide range of people. [8]
Mobile device management
Mobile device management (MDM) is software that allows IT administrators to control, secure and enforce policies on smartphones, tablets and other endpoints. Mobile device management software emerged in the early 2000s as a way to control and secure the personal digital assistants and smartphones that business workers began to use. The consumer smartphone boom that started with the launch of the Apple iPhone in 2007 led to the bring your own device (BYOD) trend, which fueled further interest in MDM.[9]
Data management
Sometimes the data management is neglected, but this part has a crucial role when learning for good cyber security practices. Majority of cyber security programs include a special courses on data management. Data management is a method of organizing and maintaining data processes that are required in almost every business operations. The benefits of data management can be found accounting, statistics, logistics planning and other disciplines including corporate computing.[10] Data governance (and management) play a fundamental role in protecting an organization’s data. Ensuring that the right people have the right access and that appropriate security controls are in place to protect each system or service, based on the criticality or sensitivity of the data sets these contain. [11]
Application security development
Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked. It encompasses the security considerations that happen during application development and design, but it also involves systems and approaches to protect apps after they get deployed. Application security may include hardware, software, and procedures that identify or minimize security vulnerabilities.[12] Application security development is important to ensure that your application is free from coding errors and bugs. And controls the risk and helps safeguard against security vulnerabilities. Application security development is the process of making applications more secure by finding and fixing security vulnerabilities. This is often done by enforcing software security best practices and using application security testing tools. [13]
Audit and compliance knowledge
A cyber security audit is designed to be a comprehensive review and analysis of your business’s IT infrastructure. It identifies threats and vulnerabilities, exposing weaknesses and high-risk practices. Regulations such as the EU GDPR (General Data Protection Regulation) can impose hefty penalties in the event of a breach that results in exploited data. A cyber security audit will help mitigate the consequences of a breach and demonstrate that your organization has taken the necessary steps to protect client and company data. [14]
Cybersecurity compliance is the organizational risk management method aligned with pre-defined security measures & controls on how data confidentiality is ensured by its administrative procedures.[15] All needed skills are developed through courses and certification.
Entry-Level Incident Response Positions
It is not always possible to advance to the position of incident
responder in a straight line. Many professionals advance from entry- to
mid-level positions before becoming a real incident responder or a
member of a computer emergency response team (CERT).
These are some examples: [16]
Network administrator
This position’s experience will help potential incident responders develop networking skills. Attention to detail, as well as the ability to sift through system configurations, site layouts, and general network and communication setups, are essential in this field.
System administrator
Another crucial beginning point for an incident responder is to learn how to manage resources inside your organization as well as user behavior. Understanding the potential damage that users, inadequate security setups, and ineffective IT policies and procedures can cause on your network can provide prospective candidates with insight into the human component of an incident.
Security administrator
In such a position, basic hacking skills, penetration testing, and intrusion detection are all learned, which are crucial incident responder skills when trying to replicate a breach or attack. Understanding the paths a cybercriminal will take when attempting to damage or obtain access to a system can greatly simplify the work of reverse engineering the incident.
Mid-Level Incident Response Positions
Computer security incident response team (CSIRT) engineer
Cyber incident responder
Incident response engineer
While each of these positions is different, they generally require very similar skills and characteristics in a candidate. At this level, personal characteristics such as problem solving, time management, and even presentation skills become more crucial as one’s career evolves into a management-facing role.
Technical skills include the ability to identify and minimize threats while maintaining communication with management and the rest of your team. Data analysis and evidence gathering become increasingly crucial, and the circumstances in which your services are deployed get more serious.
Problem-solving skills are crucial at this level of incident response, and as the stakes rise, so does the pressure in each situation. At this level, programming abilities are essential since incident responders may be needed to reverse engineer malicious code or even create patches for vulnerable network applications or services. [17]
Senior-Level Incident Response Positions
Intrusion detection specialist:
A CISSP certification might help a potential candidate in preparing for the profession. The role of an intrusion detection specialist is to find and stop any unwanted communications.
Incident manager:
Expected to plan, oversee, manage, and supervise all incident response team actions. Is in charge of reporting all current events to senior management and stakeholders, as well as acting as the technical lead on active incidents for incident responders. Prepares threat and impact assessments and reports them known to management.[17]
Certificates
There is a vast number of different certificates and the road map to being a certified professional could be very different[18] [19] . One possible approach is to start with basic certificates from the different branches of service and move to more specific and demanding focused certification. Also, some jobs require certain clearances, either from industry, or from the government. One small selection of different possible certificates is brought out in following paragraphs.
Security+ is a CompTIA certification that is considered a basic cert among cybersecurity professionals. It covers the topics of risk management and threat assessment. Network+ is also offered by CompTIA this certification (like the name implies) focuses on networking infrastructure and operations. It is considered a foundational certification. The Certified Information Systems Security Professional (CISSP) is a more advanced certification designed for cybersecurity professionals with at least five years of work experience. The certification covers
topics such as architecture, engineering, and management.
The Certified Ethical Hacker (CEH) certification is also considered a more advanced cert because it generally requires that applicants have multiple years of work experience. The goal of an ethical hacker certification is to be able to understand how cyber attacks unfold in order to improve threat assessment and mitigation skills.[20] This is definitely not all, when one looks for more information, following link could be searched, to get more in depth knowledge about different possibilities. Hereby, with the help of this matrix a possible taxonomy of different 436 listed certificates in branches are presented.[21]
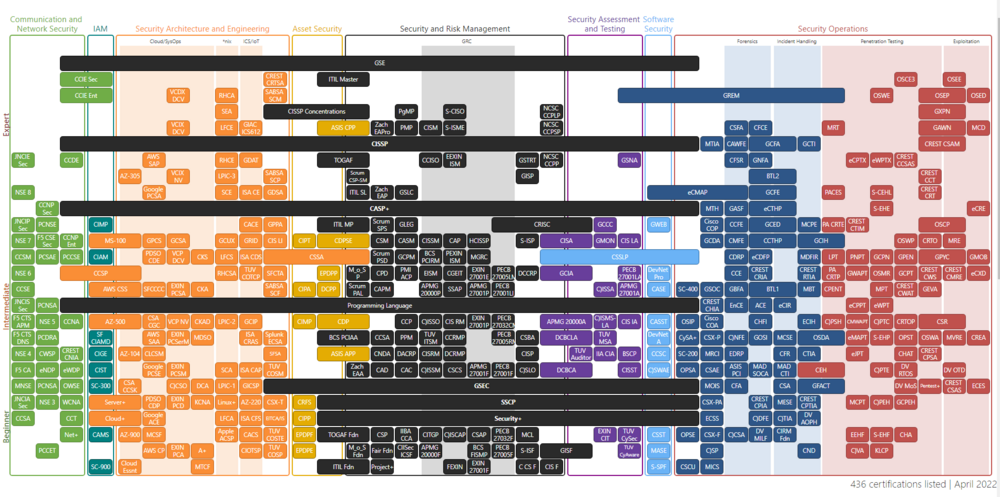
Communication and Network Security
Communication and network security covers the ability to secure communication channels and networks. Topics include secure and converges protocols, wireless networks, cellular networks, hardware operations (warranty and redundant power), and third-party connectivity. IP networking are also included in this domain.
Identity and Access Management
The identity and access management domain covers the attacks that target the human gateway to gain access to data. Other topics include ways to identify users with rights to access the information and servers. Identity and access management covers the topics of applications, Single sign-on authentication, privilege escalation, Kerberos, rule-based or risk-based access control, proofing and establishment of identity.
Security Architecture and Engineering
The security architecture and engineering domain covers important topics concerning security engineering plans, designs and principles, Topics include assessing and mitigating information system vulnerabilities, fundamental concepts of security models and security architectures in critical areas like access control. Cloud systems, cryptography, system infiltrations (ransomware, fault-injection and more) and virtualized systems are also covered in this domain.
Asset Security
The Asset Security domain deals with the issues related to the collection, storage, maintenance, retention and destruction of data. It also covers knowledge of different roles regarding data handling (owner, controller and custodian) as well as data protection methods and data states. Other topics include resource provision, asset classification and data lifecycle management.
Security and Risk Management
The security and risk management domain covers general on skills related to the implementation of user awareness programs as well as security procedures. Emphasis is also placed on risk management concerning the acquisition of new services, hardware and software (supply chain). Other skills include social engineering defense mechanisms.
Security Assessment and Testing
The security assessment and testing domain deals with all the techniques and tools used to find system vulnerabilities, weaknesses and potential areas of concern not addressed by security procedures and policies. Attack simulations, vulnerability assessment, compliance checks, and ethical disclosure also fall under this domain.
Software Security
The software development security domain deals with implementing software-based security protocols within environment for which the IT professional is responsible. Risk analysis, vulnerability identification and auditing of source codes are all covered in this subset. Additional topics include software-designed security, maturity models, development methodologies, open-source and third-party development security.
Security operations
The security operations domain covers topics ranging from investigations and digital forensic to detection and intrusion prevention tools, sandboxing and firewalls. Topics include user and entity behavior analytics, threat intelligence (threat hunting and threat feeds) log management, artifacts (mobile, computer and network), machine learning and AI-based tools, penetration testing, and
exploitation development. These for sub-domains are lister here.
Education
The entry level monitoring specialist is hired by Estonian Information System Authority even if there is no formal IT education, but readiness to learn and moderate knowledge of different operation systems is enough to start the career. [23]
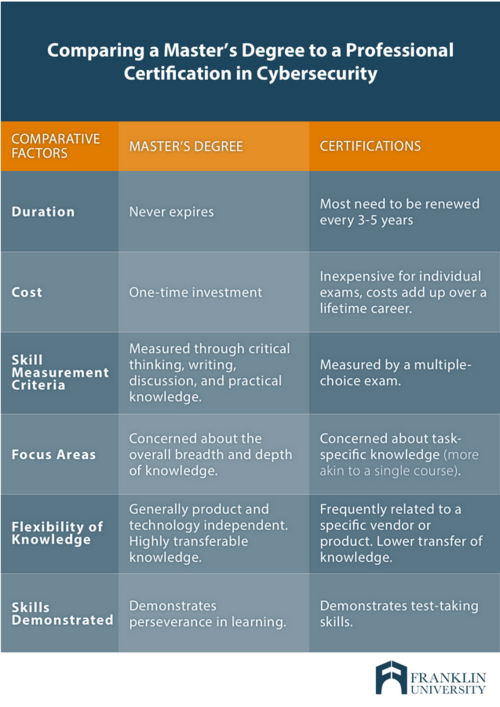
Nevertheless, like most other high qualification careers jobs falling under the cybersecurity specialist category require some form of formal education. However, since cybersecurity specialist jobs can fall across a wide spectrum of job descriptions and responsibilities, it is possible to obtain a specialist job after completing many levels of different computer related education. If one is looking for a cybersecurity related education, for example in EU, 137 courses/programs could be found that relate to keyword IT or cybersecurity. [25] Also, there is a great amount of discussion, if cyber security professional should have a degree or would be certification just enough. One interesting table is produces by Franklin University that compares benefits and/or drawbacks of each type of credential. [26] Certifications are generally good for people with little practical experience because they are known quantities in the industry and can help you get your foot in the door. They set a minimum knowledge bar. But some certifications are viewed more favorably than others. Certifications with renewal requirements are viewed better by hiring managers, but they also more costly in the long run because of the need for continuing education. Certifications are also good for showing in-depth expertise in a specialization within cybersecurity. Depending on your career goals, it may be advantageous to have a master’s degree—which shows your breadth of knowledge, critical thinking and leadership skills—and a certificate—which shows specific skill competency.[26] As IT (Cyber) Security is still a relatively young discipline, universities and colleges are still figuring out which is the best approach for their degrees. Study programmes and curricula in Cyber Security are different. In general, here are the duration of Cyber Security degrees: [27]
Bachelor’s degrees in Cyber Security take 3 or 4 years in most countries.
Master’s courses in Cyber Security take between 1-2 years to complete.
PhD programmes in Cyber Security last 3-5 years. Some only take 1 or 2 years, but they are less common.
Generalization could me made that on bachelor level the general knowledge about the cyber issues are obtained. On master level the specialization courses are taken and the person can choose more specific topics to study. It is on master level where strengths of the cyber specialist can be developed further and up-do date knowledge obtained in specifics. PhD is serious science and involves teaching, lot of scientific work and writing for publications.
Salary
Even if the salary can be very different, compared to the skills and experience, an generalization can be made. Cyber Security professionals in CSIRT, and in other entities earn quite well, from the start. First, some comparison from the United States. The average CSIRT analyst salary in the USA is $97,500 per year or $50 per hour. Entry level positions start at $48,875 per year while most experienced workers make up to $135,373 per year.
https://www.talent.com/salary?job=csirt+analyst
There are multiple positions you can occupy in this field. They have in common great salaries and high demand for technical skills, attention to details, problem-solving mentality, and the ability to analyze risks. Here are the average annual salaries in the United States, according to Payscale:
Cryptographer – 100,000 USD
Information Security Officer – 91,000 USD
Security Assessor – 90,000 USD
Security Engineer – 88,000 USD
Penetration Tester – 81,000 USD
Forensics Expert – 71,000 USD
Security Administrator – 65,000 USD
When looking into salaries in Estonia, one can find that there is a discussion that private sector is taking a toll from the public sector, and that the salaries in important agencies, as Information System Authority loose their employees to the better paid positions in private sector.
https://digi.geenius.ee/rubriik/uudis/kui-palju-riigi-jaoks-olulised-it-tootajad-tegelikult-palka-saavad/ https://tehnika.postimees.ee/6887428/riigi-it-tootajate-palgamaarad-kasvasid
But there is also a different view that average private sector worker could be hired as a top specialist in public sector and then the payment is higher. Nevertheless, it seems that the average payment in cyber security sector is any way higher that in other parts of the e-services.
https://digi.geenius.ee/rubriik/uudis/5000-eurostest-palkadest-it-tootajad-saavadki-palju-palka/
SOC
A SOC is a facility where an organization’s network, applications, and endpoints are monitored and defended. The term was adapted from network operations centers (NOCs), where large telecommunication or corporate networks are monitored. When network security became more of a concern, security teams were formed within the NOCs, and eventually spun off into larger organizations of their own as the responsibilities of security teams grew increasingly complex and specialized. The security staff working in a security operations center are often called the SOC team.
https://www.exabeam.com/incident-response/csirt/
Functions of the SOC team include, but are not limited to:
- Taking inventory of resources, to get a better understanding of the structure they are protecting.
- Maintanence of the system, by constantly making updates and adding safeguards.
- Monitoring the network for abnormalities with special tools.
- Threat analysis of new attacks and vulnerabilities.
- Responding to attacks, by acting as “first responders”. The SOC team will shut down and/or isolate endpoints, deleting files and lowering the impact as fast as possible.
- Recovery of system stability and lost data. This may be done using backups, restarting endpoints or reconfiguring systems.
- Logging all actions on the system, to be later used for analysis or forensics after an attack.
- Investigating the root cause of an attack.
- Auditing their own actions, to be in line with regulations of the organization, industry or governing body.
https://www.trellix.com/en-us/security-awareness/operations/what-is-soc.html
CSIRT
A CSIRT is a group that responds to security incidents when they occur. Key responsibilities of a CSIRT include:
https://www.exabeam.com/incident-response/csirt/
- ↑ "Job Advertisement". Available at https://www.projectpeople.com/jobs/
- ↑ "Possible Career Path". Available at https://www.cyberseek.org/pathway.html
- ↑ Popular Cyber Security Certificates [Online]. Available: https://www.coursera.org/articles/popular-cybersecurity-certifications [Accessed 25 April 2022].
- ↑ Application security, SIEM [Online]. Available: https://www.imperva.com/learn/application-security/siem/. [Accessed 27 4 2022].
- ↑ Sangfor, "What is Software Firewall? Difference between Hardware Firewall and Software Firewall, [Online]. Available: https://www.sangfor.com/blog/cybersecurity/what-is-software-firewall-difference-between-hardware-firewall-and-software-firewall [Accessed 26 4 2022].
- ↑ Varonis, "What is Software Firewall? IDS vs. IPS: What is the Difference?, [Online]. Available: https://www.varonis.com/blog/ids-vs-ips [Accessed 26 4 2022].
- ↑ Interpol, "Digital forensics". Available: https://www.interpol.int/How-we-work/Innovation/Digital-forensics. [Accessed 28 4 2022].
- ↑ "Digital forensics". Available: https://www.ecpi.edu/blog/what-is-digital-forensics-in-cybersecurity-is-this-a-good-career-for-me. [Accessed 26 4 2022].
- ↑ Techtarget, "Mobile Device Management". Available: https://www.techtarget.com/searchmobilecomputing/definition/mobile-device-management [Accessed 27 4 2022].
- ↑ Global Universities, "MSc Data Management and Cyber Security". Available: https://globaluniversities.in/msc-data-management-cyber-security. [Accessed 26 Apr 2022].
- ↑ Cyber Security Magazine, "The Role of Data Governance in Cybersecurity". Available: https://cybersecurity-magazine.com/the-role-of-data-governance-in-cybersecurity/?utm_source=rss&utm_medium=rss&utm_campaign=the-role-of-data-governance-in-cybersecurity. [Accessed 26 Apr 2022].
- ↑ VmWare, "What is application security?". Available: https://www.vmware.com/topics/glossary/content/application-security.html [Accessed 28 April 2022].
- ↑ Perforce, "Application Security Development Best Practices". Available: https://www.perforce.com/blog/kw/application-security-development-best-practices. [Accessed 28 April 2022].
- ↑ Cyfor Secure, "What is a Cyber Security Audit and how can it help your organisation?". Available: https://cyforsecure.co.uk/services/cyber-assessment/cyber-security-audit/. [Accessed 28 April 2022].
- ↑ NordLayer, "Cybersecurity compliance: Everything you need to know". Available: https://nordlayer.com/blog/cybersecurity-compliance-everything-you-need-to-know/. [Accessed 28 April 2022].
- ↑ Infosec, "Incident Responder Career Roadmap: From Entry Level to Executive". Available: https://resources.infosecinstitute.com/topic/incident-responder-career-roadmap-entry-level-executive/ [Accessed 28 April 2022].
- ↑ 17.0 17.1 Coursera, "10 Popular Cybersecurity Certifications [2022 Updated]". Available: https://www.coursera.org/articles/popular-cybersecurity-certifications [Accessed 28 April 2022].
- ↑ Coursera, "10 Popular Cybersecurity Certifications [2022 Updated]," [Online]. Available: https://www.coursera.org/articles/popular-cybersecurity-certifications. [Accessed 30 Apr 2022].
- ↑ NICCS, "Cybersecurity Certifications," [Online]. Available: hhttps://niccs.cisa.gov/about-niccs/cybersecurity-certifications. [Accessed 30 Apr 2022].
- ↑ Cybersecurity Guide, "How to become a cybersecurity specialist", [Online]. Available: https://cybersecurityguide.org/careers/security-specialist/. [Accessed 27 April 2022].
- ↑ "Cybersecurity Roadmap," [Online]. Available: https://pauljerimy.com/2020/10/12/scr-oct-2020-update/. [Accessed 30 Apr 2022].
- ↑ "Certification roadmap". Available at https://pauljerimy.com/security-certification-roadmap
- ↑ cv.ee, "SEIRESPETSIALIST - tule Eesti küberruumi valvuriks!". Available: https://www.cv.ee/en/vacancy/792782/riigi-infosusteemi-amet/seirespetsialist-tule-eesti-kuberruumi-valvuriks [Accessed 28 April 2022].
- ↑ "Comparison Table". Available at https://www.franklin.edu/blog/is-a-masters-degree-in-cyber-security-worth-it
- ↑ ENISA (European Union Agency for Cybersecurity), "Cybersecurity Education-Cybersecurity Higher Education Database". Available: https://www.enisa.europa.eu/topics/cybersecurity-education/education-map/education-courses [Accessed 26 April 2022].
- ↑ 26.0 26.1 Franklin University, "Is Getting a Master's Degree in Cyber Security Worth It?". Available: https://www.franklin.edu/blog/is-a-masters-degree-in-cyber-security-worth-it [Accessed 28 April 2022].
- ↑ Studyportals, "Why You Should Study a Cyber Security Degree in 2022". Available: https://www.mastersportal.com/articles/2722/why-you-should-study-a-cyber-security-degree-in-2022.html [Accessed 28 April 2022].
- ↑ Logsign, "What-is-remediation-in-cyber-security". Available: https://www.logsign.com/blog/what-is-remediation-in-cyber-security/. [Accessed 28 Apr 2022].
- ↑ Exabeam, "CSIRT". Available: https://www.exabeam.com/incident-response/csirt/ [Accessed 28 APr 2022].
Creating and maintaining an incident response plan (IRP)
An incident response plan (IRP) is a set of written instructions for detecting, responding to and limiting the effects of an information security event. Incident response plans provide instructions for responding to many potential scenarios, including data breaches, denial of service/distributed denial of service attacks, firewall breaches, virus or malware outbreaks or insider threats. Without an incident response plan in place, organizations may either not detect the attack in the first place, or not follow proper protocol to contain the threat and recover from it when a breach is detected.
https://www.stratacore.com/incidentresponseplan
Investigating and analyzing incidents
CSIRTs are also involved in improvement activities. After major computer security incidents occur, or when incidents are not handled in a timely or effective manner, a CSIRT will generally perform a postmortem of the incident and its response. This postmortem will identify the strengths and weakness of the response effort. Such reviews can identify weaknesses and holes in systems, infrastructure defenses, or policies that allowed the incident to take place. It can also identify problems with communication channels, interfaces, and procedures that inhibited the efficient resolution of the reported problem.
Managing internal communications and updates during or immediately after incidents occur
Communicating with employees, shareholders, customers, and the press about incidents as needed
There are various services within the CSIRT Services Framework that address communications, as they relate to security operations and incident response services. Some of these include Information Security Incident Coordination, Crisis Management Support, Vulnerability Disclosure, Situational Awareness Communication, and Awareness Building, to name a few. Sharing information and communicating with the general public and/or your constituency is appropriate in many different scenarios. These can range from proactive communications to reactive communications. Each scenario may be unique, and careful consideration should be given to when to release information to the public and what information should be released.
https://resources.sei.cmu.edu/asset_files/Handbook/2021_002_001_651819.pdf
Remediating incidents
Threat remediation is a strong and capable tool for fighting the cyber security compromises. As the word ‘remedy’ suggests, remediation process involves the treatment of a security breach. With the remediation practices, your cyber security team is able to eliminate suspicious activities and malicious attacks in the form of malware, ransomware, phishing and such. Even if you ‘kill’ the suspicious activity, the attackers can remain in your systems. If you want to contaminate and end the problem for good, your remediation processes must involve the detection of the cause. [28]
Recommending technology, policy, governance, and training changes after security incidents
After all these actions, the SCIRT must contribute to the development of better policies, practices and has to recommend improvements. They are not working in the vacuum and their work has to create new and better standards for cyber security. [29]
CERT
The term “computer emergency response team” was coined in 1988. In response to the Morris worm attack that impacted thousands of servers on the Internet, DARPA funded the formation of the Computer Emergency Response Team Coordination Center (CERT-CC) at Carnegie Mellon University. The goal of CERT-CC was to help protect the internet by collecting and disseminating information on critical security vulnerabilities. Several other countries formed similar centers using the same acronym (despite threats of legal action by Carnegie Mellon for trademark infringement). Now the term CERT refers to any emergency response team that deals with cyber threats. Many people use CERT-CC interchangeably with CSIRT, though the charter of a CERT is information sharing in order to help other response teams respond to threats against their own infrastructure.
https://www.exabeam.com/incident-response/csirt/
In general, the designation of CERT is helpful in applying real-world solutions to various cybersecurity problems. They may be government contractors or employees of a major corporation. For example, the U.S. Computer Emergency Readiness Team (US-CERT) operates under the U.S. Department of Homeland Security.
https://www.techopedia.com/definition/31003/computer-emergency-response-team-cert
In Estonia CERT is designated as CERT-EE. It was established in 2006, as an organization responsible for the management of security incidents in .ee computer networks. It is also a national contact point for international co-operation in the field of IT security.
https://www.ria.ee/en/cyber-security/cert-ee.html
Difference between SOC/CSIRT/CERT
How CSIRTs differ from CERTs and SOCs There are overlapping responsibilities between a community emergency response team (CERT), computer security incident response team (CSIRT), and security operations center (SOC). To add to this confusion, frequently, the terms CERT and CSIRT are used interchangeably, despite the important differences.
<figure> <img src="images/image3.png" alt="Overlapping in images/image3.png" /> <figcaption aria-hidden="true">Overlapping in images/image3.png</figcaption> </figure>
Understand the primary roles and characteristics of a CERT, CSIRT, and SOC.
So, using strict definitions, a CERT collects and disseminates security information, typically for the benefit of a country or an industry. A CSIRT is a cross-functional team that responds to incidents on behalf of a country or an organization. A SOC is where a country or organization monitors and defends its network, servers, applications, and endpoints.
<figure> <img src="images/image4.png" alt="table of explanation images/image4" /> <figcaption aria-hidden="true">table of explanation images/image4</figcaption> </figure>
https://www.exabeam.com/incident-response/csirt/
Future
And the Cyber security problem is only getting bigger. According to a report published by Accenture, the number of cyber security breaches increased by 11 percent from 2017 to 2018. The cost of such breaches is astronomical–about $600 billion worldwide, according to the Economic Impact of Cybercrime report.
https://www.ecpi.edu/blog/what-is-digital-forensics-in-cybersecurity-is-this-a-good-career-for-me
Job projections for cybersecurity are staggering. The Bureau of Labor Statistics in US predicts that careers in the cybersecurity field will grow by 32% by 2028. That makes cybersecurity one of the top 10 fastest-growing jobs in the country. In the United States alone, jobs for Information Security Analysts are expected to grow by 15% by 2024.
https://www.franklin.edu/blog/is-a-masters-degree-in-cyber-security-worth-it
Most likely this trend is also similar in other countries.
When checking Estonian job portals, there is a constant need for people for cyber security related positions. Also, linkedin search gives approximately 30 vacancies immediately. There are banks, logistics companies, e-shops, and software producers.
https://ee.linkedin.com/jobs/cyber-security-jobs?countryRedirected=1&position=1&pageNum=0
Trends that affect companies create need for constant cyber security services. Increasing number of home/remote offices require secure corporate networks and security of remote devices. One example is from this year, when sloppy remote desktop set-up paralyzed systems of 17 companies.
Also, no service can exists without robust infrastructure - servers, databases, applications. As all previously mentioned devices and services are at constant scanning and surveillance. So, the breach detection and immediate action demands 24/7 services. Even if lot of things could be automated, there is a need for human specialists (at least, at the moment). Third growing field is also a forensic investigation, as every attack must be investigated in order to be ready to repel next attacks. So data recovery and evidence collection is another important field of work that need skilled and professional workers.
Even, if the specifics of the entity, be it CSIRT, CERT or SOC, are different, the fundamentals of the work are the same. Professional knowledge of the networks, operational systems, hardware, scripting, and several other wider IT related knowledge is needed. As there is no single way to reach to it, every single person can find one’s strongest sides and develop them with knowledge of weaker side, in order to know, when to as for help.
</body> </html>