ISPConf 3 Ubuntu serverile 13.04: Difference between revisions
| Line 491: | Line 491: | ||
nano /etc/fail2ban/filter.d/pureftpd.conf | nano /etc/fail2ban/filter.d/pureftpd.conf | ||
sisuga | |||
<div style="border: 1px solid #aaa;background-colo r:#f9efef; width:100%; height:100px; overflow:auto; color:#FFF;"><p> | <div style="border: 1px solid #aaa;background-colo r:#f9efef; width:100%; height:100px; overflow:auto; color:#FFF;"><p> | ||
[Definition] | [Definition] | ||
| Line 498: | Line 498: | ||
</p> | </p> | ||
</div> | </div> | ||
ja | |||
nano /etc/fail2ban/filter.d/dovecot-pop3imap.conf | nano /etc/fail2ban/filter.d/dovecot-pop3imap.conf | ||
sisuga | |||
<div style="border: 1px solid #aaa;background-colo r:#f9efef; width:100%; height:100px; overflow:auto; color:#FFF;"><p> | <div style="border: 1px solid #aaa;background-colo r:#f9efef; width:100%; height:100px; overflow:auto; color:#FFF;"><p> | ||
[Definition] | [Definition] | ||
Revision as of 01:36, 10 January 2014
Juhendi koostasid:
Aare Uibomäe
Ülo Vardja
Grupp: AK31
Sissejuhatus
ISPConf 3 on veebiliidese kaudu kasutatav veebimajutuse kontrollkeskkond, mis võimaldab hallata ja konfigigureerida mitmeid teenuseid nagu näiteks: apache2 või nginx veebiserver, Postfix meiliserver, Courier või Dovecot IMAP/POP3 server, MySQL, BIND või MyDNS nimeserver, PureFTPd, SpamAssasin jms.
Eelkõige on ISPConf suunatud veebimajutus teenuse pakkujatele.
Veebiliidesele juurdepääs on võimalik 3-l tasemel:
- administraatoritel
- edasimüüjatel
- klientidel.
Internetis on tutvumiseks olemas ka juurdepääs demoversioonile aadressil: http://demo3.ispconfig.org/
Administraatorina saad siseneda, kasutades login: admin ja password: demo
Edasimüüjana sisenedes kasuta: login: reseller ja password: demo
Kliendina kasuta: login: client ja password: demo.
Alljärgnev juhend õpetab teid, kuidas Ubuntu serveriga (13.04) virtuaalmasinat ettevalmistada ISPConf 3 installeerimiseks. Veebiserverina kasutame apache2-te, nimeserverina BIND-i ja IMAP/POP3 serverina Dovecot-i.
Virtuaalmasina ettevalmistus ISPConf 3 installeerimiseks
Kõigepealt installeerime Ubuntu serveri (ver. 13.04) Virtualboxi. Virtualboxis eraldame loodavale serverile 1024 MB mälu, loome virtuaalse dünaamilise kõvaketta ja 2 võrguadapterit. Esimese võrguadapteri ühendame NAT võrguga ja teine host-only adapter virtuaalsete ühenduste tarvis. Serveri paigaldamise käigus paigaldame ühtlasi ka OpenSSH serveri, et hiljem oleks lihtsam desktop arvutilt serveriga ühendust luua. Allpool kõik seadistused teeme juurkasutaja õigustes.
Võrgu seadistus
Kuna server vajab püsivat IP aadressi, siis teeme meie võrguadapterite seadistustes järgmised muudatused. Kõigepealt muudame /etc/network/interfaces faili sisu. Meie kasutasime selleks tekstiredaktorit nano.
nano /etc/network/interfaces
Selline peab olema faili /etc/network/interfaces sisu.
The loopback network interface
auto lo
iface lo inet loopback
The primary network interface
auto eth0
iface eth0 inet dhcp
auto eth1
iface eth1 inet static
address 192.168.0.100
netmask 255.255.255.0
network 192.168.0.0
broadcast 192.168.0.255
gateway 192.168.0.1
dns-nameservers 8.8.8.8 8.8.4.4
Peale võrgu seadistuse muutmist, tuleb teha restart võrguseadistustele. Selleks sisestame terminali
/etc/init.d/networking restart
Järgnevalt teeme muudatused /etc/hosts faili. Kuna andsime oma serveri nimeks server1 ja domeeninimeks pingviin.com, siis peame lisama /etc/hosts faili rea 192.168.0.100 --->server1.pingviin.com---> server1.
nano /etc/hosts
/etc/hosts faili sisu on järgmine
127.0.0.1 localhost.localdomain localhost 192.168.0.100 server1.pingviin.com server1 # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters
Muudame failis /etc/hostname järgmise käsuga masina nime
echo server1.pingviin.com > /etc/hostname
Seejärel teeme teenusele restardi
/etc/init.d/hostname restart
Järgnevate käskudega saame kontrollida, kas kõik siiamaani toimib.
hostname hostname –f
Mõlema käsu puhul peab väljundiks tulema
server1.pingviin.com
/etc/apt/sources.list faili modifitseerimine
Kontrollime, et failis /etc/apt/sources.list oleksid lubatud universe and multiverse repositooriumid.
nano /etc/apt/sources.list
# #deb cdrom:[Ubuntu-Server 13.04 _Raring Ringtail_ - Release amd64 (20130423.1)]/ raring main restricted #deb cdrom:[Ubuntu-Server 13.04 _Raring Ringtail_ - Release amd64 (20130423.1)]/ raring main restricted # See http://help.ubuntu.com/community/UpgradeNotes for how to upgrade to # newer versions of the distribution. deb http://de.archive.ubuntu.com/ubuntu/ raring main restricted deb-src http://de.archive.ubuntu.com/ubuntu/ raring main restricted ## Major bug fix updates produced after the final release of the ## distribution. deb http://de.archive.ubuntu.com/ubuntu/ raring-updates main restricted deb-src http://de.archive.ubuntu.com/ubuntu/ raring-updates main restricted ## N.B. software from this repository is ENTIRELY UNSUPPORTED by the Ubuntu ## team. Also, please note that software in universe WILL NOT receive any ## review or updates from the Ubuntu security team. deb http://de.archive.ubuntu.com/ubuntu/ raring universe deb-src http://de.archive.ubuntu.com/ubuntu/ raring universe deb http://de.archive.ubuntu.com/ubuntu/ raring-updates universe deb-src http://de.archive.ubuntu.com/ubuntu/ raring-updates universe ## N.B. software from this repository is ENTIRELY UNSUPPORTED by the Ubuntu ## team, and may not be under a free licence. Please satisfy yourself as to ## your rights to use the software. Also, please note that software in ## multiverse WILL NOT receive any review or updates from the Ubuntu ## security team. deb http://de.archive.ubuntu.com/ubuntu/ raring multiverse deb-src http://de.archive.ubuntu.com/ubuntu/ raring multiverse deb http://de.archive.ubuntu.com/ubuntu/ raring-updates multiverse deb-src http://de.archive.ubuntu.com/ubuntu/ raring-updates multiverse ## N.B. software from this repository may not have been tested as ## extensively as that contained in the main release, although it includes ## newer versions of some applications which may provide useful features. ## Also, please note that software in backports WILL NOT receive any review ## or updates from the Ubuntu security team. deb http://de.archive.ubuntu.com/ubuntu/ raring-backports main restricted universe multiverse deb-src http://de.archive.ubuntu.com/ubuntu/ raring-backports main restricted universe multiverse deb http://security.ubuntu.com/ubuntu raring-security main restricted deb-src http://security.ubuntu.com/ubuntu raring-security main restricted deb http://security.ubuntu.com/ubuntu raring-security universe deb-src http://security.ubuntu.com/ubuntu raring-security universe deb http://security.ubuntu.com/ubuntu raring-security multiverse deb-src http://security.ubuntu.com/ubuntu raring-security multiverse ## Uncomment the following two lines to add software from Canonical's ## 'partner' repository. ## This software is not part of Ubuntu, but is offered by Canonical and the ## respective vendors as a service to Ubuntu users. # deb http://archive.canonical.com/ubuntu raring partner # deb-src http://archive.canonical.com/ubuntu raring partner ## Uncomment the following two lines to add software from Ubuntu's ## 'extras' repository. ## This software is not part of Ubuntu, but is offered by third-party ## developers who want to ship their latest software. # deb http://extras.ubuntu.com/ubuntu raring main # deb-src http://extras.ubuntu.com/ubuntu raring main
Peale seda värskendame repositooriumid käsuga:
apt-get update
ja paigaldame viimased uuendused:
apt-get upgrade
Peale uuenduste paigaldamist, tuleb teha serverile restart
reboot
Shelli vahetamine
Kuna meil on vaja serveris kasutada /bin/bash-i, mitte /bin/dash-i , siis shelli vahetamiseks kasutame käsku.
dpkg-reconfigure dash
Vastus küsimusele on värviliselt välja toodud.
Use dash as the default system shell (/bin/sh)? <--No
Kui me shelli ei vahetaks, siis ISPConfig`i install ei õnnestu, sest ISPConfigi paigaldamisel kasutatakse skripte, mis /bin/dash-iga ei käivitu või siis põhjustavad hiljem süsteemi ebastabiilsust.
AppArmor`i väljalülitamine
AppArmor on turvalisuse suurendamiseks loodud moodul (samalaadne SELinuxi-ga). Kuid tihti põhjustab just see süsteemis anomaaliaid, millede tuvastamine võtab kaua aega. Sellepärast on vajalik AppArmor väljalülitada ja ka eemaldada.
/etc/init.d/apparmor stop update-rc.d -f apparmor remove apt-get remove apparmor apparmor-utils
Süsteemi kella sünroniseerimine
On hea tava, et süsteemi kell oleks alati õige, selleks sisestame terminali
apt-get install ntp ntpdate
Postfix, Dovecot, MySQL, phpMyAdmin, rkhunter, binutils paigaldamine
Järgmisena saame paigaldada Postfix-i, MySQL-i, Dovecot-i, rkhunter-i, binutils ja muu vajaliku käsuga
apt-get install postfix postfix-mysql postfix-doc mysql-client mysql-server openssl getmail4 rkhunter binutils
dovecot-imapd dovecot-pop3d dovecot-mysql dovecot-sieve sudo
Peale käsu sisestamist vasta alljärgnevatele küsimustele:
New password for the MySQL "root" user: <-- sinurootSQLparool Repeat password for the MySQL "root" user: <-- sinurootSQLparool General type of mail configuration: <-- Internet Site System mail name: <-- server1.pingviin.com
Järgmiseks tuleb Postfix`i master.cf failis submission ja smtps sektsioonides trellid eest ära võtta. Read mille ees trelle olla ei tohi on rohelised.
nano /etc/postfix/master.cf
... submission inet n - - - - smtpd -o syslog_name=postfix/submission -o smtpd_tls_security_level=encrypt -o smtpd_sasl_auth_enable=yes # -o smtpd_reject_unlisted_recipient=no # -o smtpd_client_restrictions=$mua_client_restrictions # -o smtpd_helo_restrictions=$mua_helo_restrictions # -o smtpd_sender_restrictions=$mua_sender_restrictions -o smtpd_recipient_restrictions=permit_sasl_authenticated,reject # -o milter_macro_daemon_name=ORIGINATING smtps inet n - - - - smtpd -o syslog_name=postfix/smtps -o smtpd_tls_wrappermode=yes -o smtpd_sasl_auth_enable=yes # -o smtpd_reject_unlisted_recipient=no # -o smtpd_client_restrictions=$mua_client_restrictions # -o smtpd_helo_restrictions=$mua_helo_restrictions # -o smtpd_sender_restrictions=$mua_sender_restrictions -o smtpd_recipient_restrictions=permit_sasl_authenticated,reject # -o milter_macro_daemon_name=ORIGINATING ...
Peale muudatuste tegemist tuleb Postfix`ile teha restart
/etc/init.d/postfix restart
Selleks, et MySQL kuulaks kõiki liideseid, mitte ainult 127.0.0.1, tuleb väljakommenteerida bind-address = 127.0.0.1 , nagu allpool näidatud...
nano /etc/mysql/my.cnf
... # Instead of skip-networking the default is now to listen only on # localhost which is more compatible and is not less secure. # bind-address = 127.0.0.1 ...
Seejärel taaskäivitame MySQL`i
/etc/init.d/mysql restart
Selleks, et kontrollida võrk on töökorras siseta käsk
netstat -tap | grep mysql
Väljund peaks välja nägema umbes selline:
root@server1:~# netstat -tap | grep mysql tcp 0 0 *:mysql *:* LISTEN 21298/mysqld root@server1:~#
Amavisd-new, SpamAssassin, Clamav paigaldamine
Selleks, et paigaldada amavisd-new, SpamAssasin ja Clamav sisestame käsu
apt-get install amavisd-new spamassassin clamav clamav-daemon zoo unzip bzip2 arj nomarch lzop cabextract
apt-listchanges libnet-ldap-perl libauthen-sasl-perl clamav-docs daemon libio-string-perl libio-socket-ssl-perl
libnet-ident-perl zip libnet-dns-perl
Apache2, PHP5, phpMyAdmin, FCGI, suExec, Pear ja mcrypt paigaldamine
Apache2, PHP5, phpMyAdmin, FCGI, suExec, Pear ja mcrypt istallime järgmise käsuga
apt-get install apache2 apache2.2-common apache2-doc apache2-mpm-prefork apache2-utils libexpat1 ssl-cert
libapache2-mod-php5 php5 php5-common php5-gd php5-mysql php5-imap phpmyadmin php5-cli php5-cgi
libapache2-mod-fcgid apache2-suexec php-pear php-auth php5-mcrypt mcrypt php5-imagick imagemagick
libapache2-mod-suphp libruby libapache2-mod-ruby libapache2-mod-python php5-curl php5-intl php5-memcache
php5-memcached php5-ming php5-ps php5-pspell php5-recode php5-snmp php5-sqlite php5-tidy php5-xmlrpc
php5-xsl memcached
Paigalduse käigus näed küsimusi, mille vastused on ära toodud värvilisena.
Web server to reconfigure automatically: <-- apache2
Configure database for phpmyadmin with dbconfig-common? <-- No
Seejärel siseta järgmine käsk, et aktiveerida Apache mooduleid suexec, rewrite, ssl, actions, ja include
a2enmod suexec rewrite ssl actions include
ja kui soovid kasutada WebDAV-i, siis tuleb aktiveerida ka moodulid dav, dav_fs ja auth_digest
a2enmod dav_fs dav auth_digest
Järgmiseks tuleks avada fail /etc/apache2/mods-available/suphp.conf
nano /etc/apache2/mods-available/suphp.conf
ja selles failis tuleks välja kommenteerida rida <FilesMatch "\.ph(p3?|tml)$">
ja lisame rea AddType application/x-httpd-suphp .php .php3 .php4 .php5 .phtml , vastasel juhul hakkaks iga PHP fail käivituma suPHP all.
... <IfModule mod_suphp.c> # <FilesMatch "\.ph(p3?|tml)$"> # SetHandler application/x-httpd-suphp #</FilesMatch> AddType application/x-httpd-suphp .php .php3 .php4 .php5 .phtml suPHP_AddHandler application/x-httpd-suphp ...
Teeme Apache`le restardi, et tehtud muudatused saaksid jõustuda
/etc/init.d/apache2 restart
Nüüd muudame /etc/mime.types faili selleks, et Ruby failid laiendiga .rb oleksid samuti toetatud.
nano /etc/mime.types
Selleks peame failis välja kommentaarima järgmise rea application/x-ruby
...
# application/x-ruby rb
...
Teeme Apache`le uuesti restardi, et tehtud muudatused saaksid jõustuda
/etc/init.d/apache2 restart
Xcache
Xcache on PHP koodi kiirendi selleks, et kiirendada ja optimeerida PHP koodi. See on vägagi soovitatud, et oleks installeeritud PHP kiirendaja selleks et PHP lehed kiiremini laeksid. Selleks sisestame terminalis
apt-get install php5-xcache
ja teeme Apache`le restardi
/etc/init.d/apache2 restart
PHP-FPM
Alates ISPConfig 3.0.5 versioonist kasutatakse seal koos apachega eraldi PHP modulit : PHP-FPM.
Et seda PHP-FPM moodulit koos Apachega kasutada, vajame apache moodulit mod_fastcgi
PHP-FPM ja apache mooduli mod_fastcgi saame installida käsuga:
apt-get install libapache2-mod-fastcgi php5-fpm
Aktiveerime mooduli
a2enmod actions fastcgi alias
Teeme Apache`le restardi.
/etc/init.d/apache2 restart
Mailman
Alates versioonist 3.0.4, ISPConfig võimaldab ka hallata (luua/muuta/kustutada) Mailman maili nimekirju. Kui soovid seda võimalust kasutada, siis saad paigaldada Mailman'i järgneva käsuga:
apt-get install mailman
Installi käigus tuleb valida keel
Languages to support: <-- en Missing site list <-- Ok
Selleks, et saaks Mailman`i käivitada tuleb luua maili nimekiri nimega mailman
newlist mailman
Terminal väljastab järneva jutu, kus pead sisestama ka mailmani listi haldava administraatori emaili aadressi ja ka salasõna
root@server1:~# newlist mailman
Enter the email of the person running the list: <-- administaatori emaili aadress, näit. listadmin@pingviin.com
Initial mailman password: <-- administraatori password mailmani listi jaoks
To finish creating your mailing list, you must edit your /etc/aliases (or
equivalent) file by adding the following lines, and possibly running the
`newaliases' program:
## mailman mailing list
mailman: "|/var/lib/mailman/mail/mailman post mailman"
mailman-admin: "|/var/lib/mailman/mail/mailman admin mailman"
mailman-bounces: "|/var/lib/mailman/mail/mailman bounces mailman"
mailman-confirm: "|/var/lib/mailman/mail/mailman confirm mailman"
mailman-join: "|/var/lib/mailman/mail/mailman join mailman"
mailman-leave: "|/var/lib/mailman/mail/mailman leave mailman"
mailman-owner: "|/var/lib/mailman/mail/mailman owner mailman"
mailman-request: "|/var/lib/mailman/mail/mailman request mailman"
mailman-subscribe: "|/var/lib/mailman/mail/mailman subscribe mailman"
mailman-unsubscribe: "|/var/lib/mailman/mail/mailman unsubscribe mailman"
Hit enter to notify mailman owner... <-- ENTER
root@server1:~#
Avame faili /etc/aliases
nano /etc/aliases
ja lisame sinna vajalikud read
... ## mailman mailing list mailman: "|/var/lib/mailman/mail/mailman post mailman" mailman-admin: "|/var/lib/mailman/mail/mailman admin mailman" mailman-bounces: "|/var/lib/mailman/mail/mailman bounces mailman" mailman-confirm: "|/var/lib/mailman/mail/mailman confirm mailman" mailman-join: "|/var/lib/mailman/mail/mailman join mailman" mailman-leave: "|/var/lib/mailman/mail/mailman leave mailman" mailman-owner: "|/var/lib/mailman/mail/mailman owner mailman" mailman-request: "|/var/lib/mailman/mail/mailman request mailman" mailman-subscribe: "|/var/lib/mailman/mail/mailman subscribe mailman" mailman-unsubscribe: "|/var/lib/mailman/mail/mailman unsubscribe mailman"
Käivitame lisatud aliased
newaliases
ja teeme Postfix`ile restardi
/etc/init.d/postfix restart
Aktiveerime Mailman`i Apache konfiguratsiooni.
ln -s /etc/mailman/apache.conf /etc/apache2/conf.d/mailman.conf
seejärel teeme Apache`le restardi
/etc/init.d/apache2 restart
ning käivitame Mailman deemoni.
/etc/init.d/mailman start
PureFTPd ja Quota
PureFTP ja Quota paigaldame järgmise käsuga
apt-get install pure-ftpd-common pure-ftpd-mysql quota quotatool
Modifitseerime /etc/default/pure-ftpd-common faili
nano /etc/default/pure-ftpd-common
ja veendume, et failis oleksid järgmised kirjed STANDALONE_OR_INETD=standalone ja VIRTUALCHROOT=true
... STANDALONE_OR_INETD=standalone ... VIRTUALCHROOT=true ...
Järgmiseks konfigureerime PureFTPd, et lubada FTP ja TLS sessioone. FTP on väga ebaturvaline protoko, sest kõik salasõnad ja kogu andmevahetus toimub avatekstiga. Kasutades TLS protokolli saame andmevahetuse muuta turvaliseks, sest kogu andmevahetus krüpteeritakse.
Et seadistada PureFTPd, kasutama TLS sesioone anname terminali käsu
echo 1 > /etc/pure-ftpd/conf/TLS
Selleks, et kasutada TLS`i tuleb luua SSL sertifikaat ja koht kuhu sertifikaat salvestada. Selleks loome kõigepealt vajaliku kausta
mkdir -p /etc/ssl/private/
ja seejärel genereerime SSL sertifikaadi sisestades terminali:
openssl req -x509 -nodes -days 7300 -newkey rsa:2048 -keyout /etc/ssl/private/pure-ftpd.pem -out
/etc/ssl/private/pure-ftpd.pem
Sertifikaati luues küsitakse teilt andmeid. Näidis vastused küsimustele allpool värviliselt:
Country Name (2 letter code) [AU]: <-- EE State or Province Name (full name) [Some-State]: <-- Harju Locality Name (eg, city) []: <-- Tallinn Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- Pingviin AS Organizational Unit Name (eg, section) []: <-- IT Common Name (eg, YOUR name) []: <-- server1.pingviin.com Email Address []: <-- nimi@pingviin.com
SSL sertifikaadi õiguste muutmine
chmod 600 /etc/ssl/private/pure-ftpd.pem
Teeme PureFTPd`le restardi
/etc/init.d/pure-ftpd-mysql restart
Et saaks kasutada Quota't peame muutma /etc/fstab faili.
nano /etc/fstab
# /etc/fstab: static file system information.
#
# Use 'blkid' to print the universally unique identifier for a
# device; this may be used with UUID= as a more robust way to name devices
# that works even if disks are added and removed. See fstab(5).
#
# <file system> <mount point> <type> <options> <dump> <pass>
/dev/mapper/server1--vg-root / ext4 errors=remount-ro,usrjquota=quota.user,grpjquota=quota.group,jqfmt=vfsv0 0 1
# /boot was on /dev/sda1 during installation
UUID=9b8299f1-b2a2-4231-9ba1-4540fad76b0f /boot ext2 defaults 0 2
/dev/mapper/server1--vg-swap_1 none swap sw 0 0
Aktiveerime quota järgnevate käskudega
mount -o remount / quotacheck -avugm quotaon –avug
BIND DNS Server
BIND9 nimeserveri saame paigaldada järgneva käsuga
apt-get install bind9 dnsutils
Vlogger, Webalizer ja AWstats
Vlogger, Webalizer ja AWstats installitakse järgmiselt:
apt-get install vlogger webalizer awstats geoip-database libclass-dbi-mysql-perl
Seejärel avame faili /etc/cron.d/awstats ja kommenteerime välja kogu sisu.
nano /etc/cron.d/awstats
#MAILTO=root #*/10 * * * * www-data [ -x /usr/share/awstats/tools/update.sh ] && /usr/share/awstats/tools/update.sh # Generate static reports: #10 03 * * * www-data [ -x /usr/share/awstats/tools/buildstatic.sh ] && /usr/share/awstats/tools/buildstatic.sh
Jailkit
Jailkit on vajalik üksnes siis kui tahetakse SSH kasutajaid chroot'ida ehk muuta nende kasutajate root directory 't.
TÄHTIS! - Jailkit tuleb paigaldada enne ISPConfig 3 paigaldust. Kui ISPConfig on juba paigaldatud, siis Jailkiti paigaldamine ei õnnestu!
Jailkit saab paigaldada viies läbi järgmised operatsioonid.
apt-get install build-essential autoconf automake1.9 libtool flex bison debhelper binutils-gold
cd /tmp wget http://olivier.sessink.nl/jailkit/jailkit-2.15.tar.gz tar xvfz jailkit-2.15.tar.gz cd jailkit-2.15 ./debian/rules binary
cd .. dpkg -i jailkit_2.15-1_*.deb rm -rf jailkit-2.15*
fail2ban
Fail2ban'i paigaldamine on kasutaja äranägemisel, kuid soovitatav, sest ISPConfig proovib monitoorida neid logisid.
apt-get install fail2ban
Selleks, et fail2ban monitooriks PureFTPd ja Dovecot`i, loome faili /etc/fail2ban/jail.local
nano /etc/fail2ban/jail.local
järgmise sisuga
[pureftpd] enabled = true port = ftp filter = pureftpd logpath = /var/log/syslog maxretry = 3 [dovecot-pop3imap] enabled = true filter = dovecot-pop3imap action = iptables-multiport[name=dovecot-pop3imap, port="pop3,pop3s,imap,imaps", protocol=tcp] logpath = /var/log/mail.log maxretry = 5 [sasl] enabled = true port = smtp filter = sasl logpath = /var/log/mail.log maxretry = 3
Loome järgmised 2 filterfaili.
nano /etc/fail2ban/filter.d/pureftpd.conf
sisuga
[Definition] failregex = .*pure-ftpd: \(.*@<HOST>\) \[WARNING\] Authentication failed for user.* ignoreregex =
ja
nano /etc/fail2ban/filter.d/dovecot-pop3imap.conf
sisuga
[Definition] failregex = (?: pop3-login|imap-login): .*(?:Authentication failure|Aborted login \(auth failed|Aborted login \(tried to use disabled|Disconnected \(auth failed|Aborted login \(\d+ authentication attempts).*rip=(?P<host>\S*),.* ignoreregex =
Seejärel teeme fail2ban`ile restardi
/etc/init.d/fail2ban restart
SquirrelMail
Et paigaldada SquirrelMail'i Webmail klienti anname terminalis käsu:
apt-get install squirrelmail
Seejärel seadistame SquirrelMail`i
squirrelmail-configure
Peame SquirreMaili seadistama, et kasutada Dovecote-IMAP/POP3 serverit.
Main Menu -- 1. Organization Preferences 2. Server Settings 3. Folder Defaults 4. General Options 5. Themes 6. Address Books 7. Message of the Day (MOTD) 8. Plugins 9. Database 10. Languages D. Set pre-defined settings for specific IMAP servers C Turn color on S Save data Q Quit Command >> <-- D SquirrelMail Configuration : Read: config.php --------------------------------------- While we have been building SquirrelMail, we have discovered some preferences that work better with some servers that don't work so well with others. If you select your IMAP server, this option will set some pre-defined settings for that server. Please note that you will still need to go through and make sure everything is correct. This does not change everything. There are only a few settings that this will change. Please select your IMAP server: bincimap = Binc IMAP server courier = Courier IMAP server cyrus = Cyrus IMAP server dovecot = Dovecot Secure IMAP server exchange = Microsoft Exchange IMAP server hmailserver = hMailServer macosx = Mac OS X Mailserver mercury32 = Mercury/32 uw = University of Washington's IMAP server gmail = IMAP access to Google mail (Gmail) accounts quit = Do not change anything Command >> <-- dovecot SquirrelMail Configuration : Read: config.php --------------------------------------------------------- While we have been building SquirrelMail, we have discovered some preferences that work better with some servers that don't work so well with others. If you select your IMAP server, this option will set some pre-defined settings for that server. Please note that you will still need to go through and make sure everything is correct. This does not change everything. There are only a few settings that this will change. Please select your IMAP server: bincimap = Binc IMAP server courier = Courier IMAP server cyrus = Cyrus IMAP server dovecot = Dovecot Secure IMAP server exchange = Microsoft Exchange IMAP server hmailserver = hMailServer macosx = Mac OS X Mailserver mercury32 = Mercury/32 uw = University of Washington's IMAP server gmail = IMAP access to Google mail (Gmail) accounts quit = Do not change anything Command >> dovecot imap_server_type = dovecot default_folder_prefix = <none> trash_folder = Trash sent_folder = Sent draft_folder = Drafts show_prefix_option = false default_sub_of_inbox = false show_contain_subfolders_option = false optional_delimiter = detect delete_folder = false Press any key to continue... <-- vajuta Enter SquirrelMail Configuration : Read: config.php (1.4.0) --------------------------------------------------------- Main Menu -- 1. Organization Preferences 2. Server Settings 3. Folder Defaults 4. General Options 5. Themes 6. Address Books 7. Message of the Day (MOTD) 8. Plugins 9. Database 10. Languages D. Set pre-defined settings for specific IMAP servers C Turn color on S Save data Q Quit Command >> <-- S SquirrelMail Configuration : Read: config.php (1.4.0) --------------------------------------------------------- Main Menu -- 1. Organization Preferences 2. Server Settings 3. Folder Defaults 4. General Options 5. Themes 6. Address Books 7. Message of the Day (MOTD) 8. Plugins 9. Database 10. Languages D. Set pre-defined settings for specific IMAP servers C Turn color on S Save data Q Quit Command >> <-- Q
Nüüd seadistame SquirrelMail`i selliselt, et seda saaks kasutada kas squirrelmail või webmail aliastega.
cd /etc/apache2/conf.d/ ln -s ../../squirrelmail/apache.conf squirrelmail.conf /etc/init.d/apache2 reload
Avame faili /etc/apache2/conf.d/squirrelmail.conf
nano /etc/apache2/conf.d/squirrelmail.conf
Lisada sinna read, mis on märgitud punase kirjaga
... <Directory /usr/share/squirrelmail>
Options FollowSymLinks
<IfModule mod_php5.c>
application/x-httpd-php .php
php_flag magic_quotes_gpc Off
php_flag track_vars On
php_admin_flag allow_url_fopen Off
php_value include_path .
php_admin_value upload_tmp_dir /var/lib/squirrelmail/tmp
php_admin_value open_basedir /usr/share/squirrelmail:/etc/squirrelmail:/var/lib/squirrelmail:/etc/hostname:/etc/mailname
php_flag register_globals off
</IfModule>
<IfModule mod_dir.c>
DirectoryIndex index.php
</IfModule>
# access to configtest is limited by default to prevent information leak
<Files configtest.php>
order deny,allow
deny from all
allow from 127.0.0.1
</Files>
</Directory>
...
Loome kausta /var/lib/squirrelmail/tmp ja lisame omanikuks www-data
mkdir /var/lib/squirrelmail/tmp chown www-data /var/lib/squirrelmail/tmp
Teeme Apache`l restardi
/etc/init.d/apache2 reload
Nüüd saad SquirrelMail`i kätte kui sisestad brauserisse
http://192.168.0.100/squirrelmail
Kui soovid kasutada /webmail, mitte /squirrelmail, tuleb lisada alias vastavalt all toodud näitele.
nano /etc/apache2/conf.d/squirrelmail.conf
Alias /squirrelmail /usr/share/squirrelmail Alias /webmail /usr/share/squirrelmail ...
Teeme Apache`le restardi
/etc/init.d/apache2 reload
Nüüd saad Squirrelmail`i siseneda
http://192.168.0.100/webmail
Kui soovida teha virtual host nimega webmail.pingviin.com, toimi järgmiselt.
nano /etc/apache2/conf.d/squirrelmail.conf
... <VirtualHost 192.168.0.100:80> DocumentRoot /usr/share/squirrelmail ServerName webmail.pingviin.com </VirtualHost>
Teeme Apache`le restardi
/etc/init.d/apache2 reload
Nüüd saad SquirrelMail`i siseneda.
http://webmail.pingviin.com
ISPConfig 3 paigaldamine
Laeme internetist alla ISPConfig 3 viimase stabiilse versiooni. Selleks sisestame:
cd /tmp wget http://www.ispconfig.org/downloads/ISPConfig-3-stable.tar.gz tar xfz ISPConfig-3-stable.tar.gz cd ispconfig3_install/install/
Järgmiseks anname terminalis käsu,
php -q install.php
mis käivitab ISPConfig 3 installatsiooni. Paigaluse käigus on vajalikud sisestamised värviliselt tähistatud.
root@server1:/tmp/ispconfig3_install/install# php -q install.php
--------------------------------------------------------------------------------
_____ ___________ _____ __ _ ____
|_ _/ ___| ___ \ / __ \ / _(_) /__ \
| | \ `--.| |_/ / | / \/ ___ _ __ | |_ _ __ _ _/ /
| | `--. \ __/ | | / _ \| '_ \| _| |/ _` | |_ |
_| |_/\__/ / | | \__/\ (_) | | | | | | | (_| | ___\ \
\___/\____/\_| \____/\___/|_| |_|_| |_|\__, | \____/
__/ |
|___/
--------------------------------------------------------------------------------
>> Initial configuration
Operating System: 13.04 UNKNOWN
Following will be a few questions for primary configuration so be careful.
Default values are in [brackets] and can be accepted with <ENTER>.
Tap in "quit" (without the quotes) to stop the installer.
Select language (en,de) [en]: <-- ENTER
Installation mode (standard,expert) [standard]: <-- ENTER
Full qualified hostname (FQDN) of the server, eg server1.domain.tld [server1.pingviin.com]: <-- ENTER
MySQL server hostname [localhost]: <-- ENTER
MySQL root username [root]: <-- ENTER
MySQL root password []: <-- sinuSQLsalasõna
MySQL database to create [dbispconfig]: <-- ENTER
MySQL charset [utf8]: <-- ENTER
Generating a 4096 bit RSA private key
............................................................................++
.....................++
writing new private key to 'smtpd.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: <-- ENTER
State or Province Name (full name) [Some-State]: <-- ENTER
Locality Name (eg, city) []: <-- ENTER
Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- ENTER
Organizational Unit Name (eg, section) []: <-- ENTER
Common Name (e.g. server FQDN or YOUR name) []: <-- ENTER
Email Address []: <-- ENTER
Configuring Jailkit
Configuring Dovecot
Configuring Spamassassin
Configuring Amavisd
Configuring Getmail
Configuring Pureftpd
Configuring BIND
Configuring Apache
Configuring Vlogger
Configuring Apps vhost
Configuring Bastille Firewall
Configuring Fail2ban
Installing ISPConfig
ISPConfig Port [8080]: <-- ENTER
Do you want a secure (SSL) connection to the ISPConfig web interface (y,n) [y]: <-- ENTER
Generating RSA private key, 4096 bit long modulus
..........++
......++
e is 65537 (0x10001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: <-- ENTER
State or Province Name (full name) [Some-State]: <-- ENTER
Locality Name (eg, city) []: <-- ENTER
Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- ENTER
Organizational Unit Name (eg, section) []: <-- ENTER
Common Name (e.g. server FQDN or YOUR name) []: <-- ENTER
Email Address []: <-- ENTER
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: <-- ENTER
An optional company name []: <-- ENTER
writing RSA key
Configuring DBServer
Installing ISPConfig crontab
no crontab for root
no crontab for getmail
Restarting services ...
Rather than invoking init scripts through /etc/init.d, use the service(8)
utility, e.g. service mysql restart
Since the script you are attempting to invoke has been converted to an
Upstart job, you may also use the stop(8) and then start(8) utilities,
e.g. stop mysql ; start mysql. The restart(8) utility is also available.
mysql stop/waiting
mysql start/running, process 2817
* Stopping Postfix Mail Transport Agent postfix
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
...done.
* Starting Postfix Mail Transport Agent postfix
postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
/usr/sbin/postconf: warning: /etc/postfix/main.cf: undefined parameter: virtual_mailbox_limit_maps
...done.
Stopping amavisd: amavisd-new.
Starting amavisd: amavisd-new.
* Stopping ClamAV daemon clamd
...done.
* Starting ClamAV daemon clamd
...done.
Rather than invoking init scripts through /etc/init.d, use the service(8)
utility, e.g. service dovecot restart
Since the script you are attempting to invoke has been converted to an
Upstart job, you may also use the stop(8) and then start(8) utilities,
e.g. stop dovecot ; start dovecot. The restart(8) utility is also available.
dovecot stop/waiting
dovecot start/running, process 3962
* Restarting web server apache2
[Fri Jan 03 00:55:00 2014] [warn] NameVirtualHost *:443 has no VirtualHosts
[Fri Jan 03 00:55:00 2014] [warn] NameVirtualHost *:80 has no VirtualHosts
[Fri Jan 03 00:55:01 2014] [warn] NameVirtualHost *:443 has no VirtualHosts
[Fri Jan 03 00:55:01 2014] [warn] NameVirtualHost *:80 has no VirtualHosts
... waiting ...done.
Restarting ftp server: Running: /usr/sbin/pure-ftpd-mysql-virtualchroot -l mysql:/etc/pure-ftpd/db/mysql.conf -l pam -A -b -u 1000 -D - H -Y 1 -E -8 UTF-8 -O clf:/var/log/pure-ftpd/transfer.log -B
Installation completed.
root@server1:/tmp/ispconfig3_install/install#
Installeerimise käigus seadistatakse kõik alamteenused automaatselt, seega eraldi konfiguratsiooni pole tarvis teha.
Kui soovid luua SSL ühendust virtuaalhostiga, et saaksid ISPConfig kontrollpaneeli siseneda turvaliselt, siis piisab järgmisele küsimusele ENTER vajutamisest, kuna vaikimisi valikuks on [y] ehk nõusolek.
Do you want a secure (SSL) connection to the ISPConfig web interface (y,n) [y]: ENTER
Nüüd saad ISPConfig kontrollpaneeli siseneda.
https://192.168.0.100:8080/
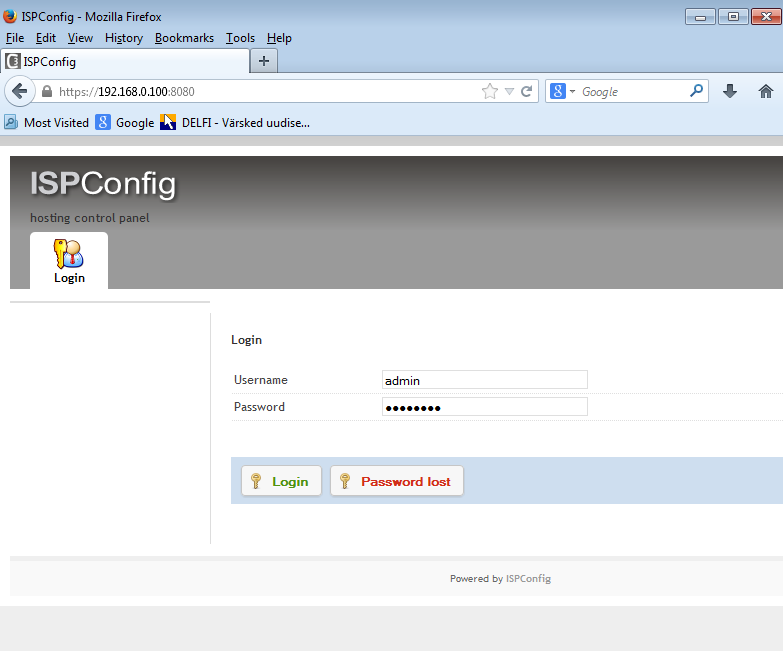
Sisse logimiseks on kasutajaks admin ja parooliks admin. Süsteemi logimise vaade näha on allpool pildil. Peale keskkonda sisenemist vaheta kindlasti ära parool !!!
Pilt.1 - Sisselogimise aken.
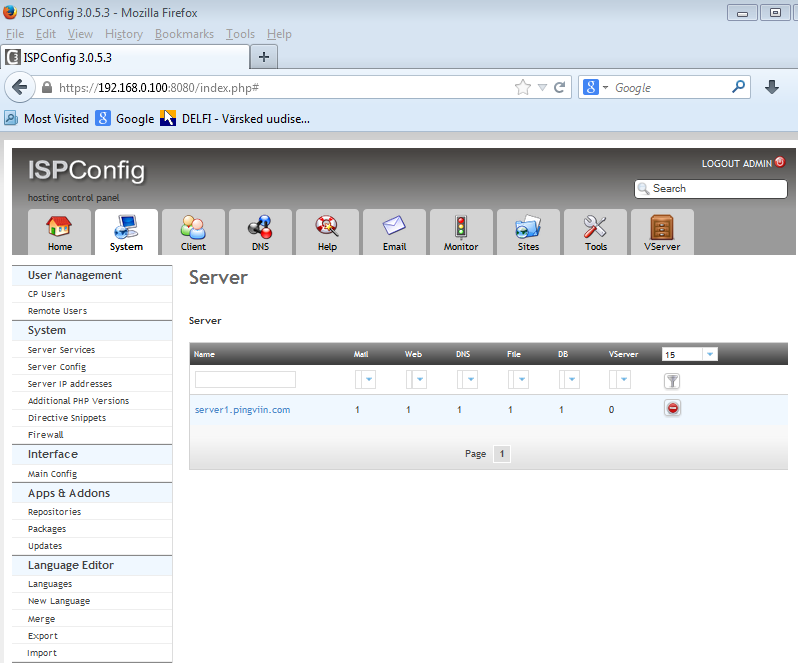
Panime välja ka mõned ekraanittõmmised ISPconfig veebiliidesest.
Pilt.2 - Vaade systeemile...
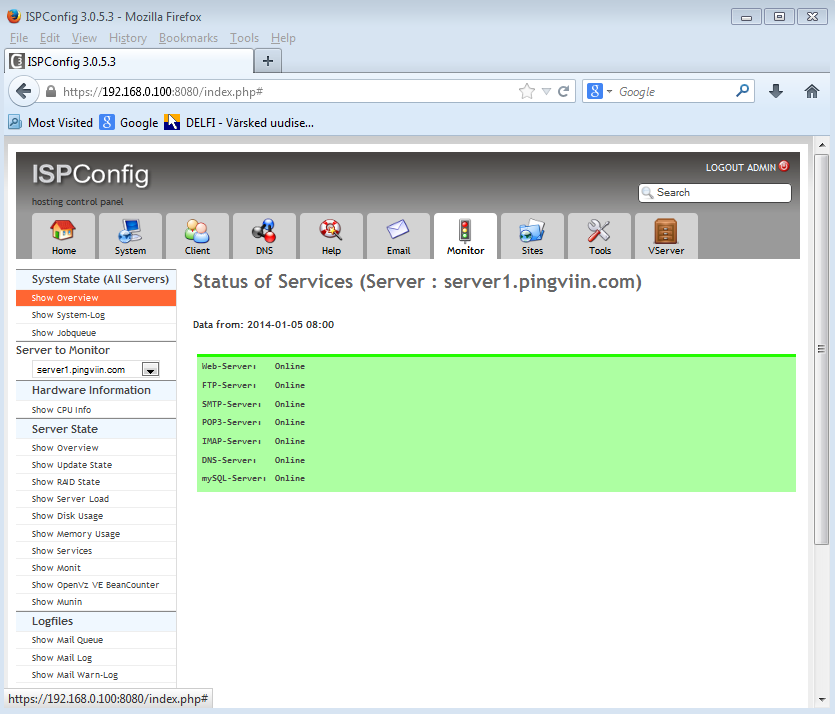
Pilt.3 Süsteemi monitoorimise vaade.
Kokkuvõte
Ülo
Kokkuvõtteks võib öelda, et ISPConf on maailmas päris laialt kasutusel ja infot selle kohta saab kasutajate foorumitest. Kuna kasutajate kommuune on palju, siis võib uskuda, et probleemi tekkides leiab vastuse alati. Mis aga on pisut kummastav, on see, et ISPConfigi seadistamise manuaal on küll netist allalaetav, kuid 1 allalaadimine maksab 5.- €.
Kogu süsteemi installeerimine võtab küll aega, aga kui teha täpselt juhendi järgi, siis ei peaks eriti probleeme tekkima. Kuna antud viki sai koostatud õppimise eesmärkidel, siis võib küll öelda, et selle projekti käigus sai vähemalt mulle selgeks, et selline süsteem koosneb väga paljudest erinevatest tarkvaradest ja nende omavaheline sobivus on häireteta töö aluseks. Seetõttu peab alati enne taolise süsteemi installeerimist kindlaks tegema oma vajadused ning seejärel uurima, kuidas antud süsteem saab sinu vajadused kõiga paremini rahuldatud.
Aare
ISPConf puhul oli tegemist meie jaoks väga mahuka väljakutsega ja sellele kulus ka omajagu aega. Lõpuks õnnestus teenus ka ilusti tööle saada. Suur abi oli grupitööst meile mõlemile, mõne asja peale tulin mina, mõne asja peale Ülo. Üldiselt oli väga sobilik grupitöö variant, kuna üksinda tehes oleksin valinud vähem mahukama teenuse. Julgeksin soovitada seda meie koostatud juhendit inimesele, kes pole antud teenusega kursis, kuna kõik on väga üksikasjalikult lahtikirjutatud ja peaks olema mõistetav kõigile. Üks asi mis mind üllatas oli see, kui paljudest väikestest ja suurtest osadest mingi teenus kokku tuleb panna, et kõik töötaks ja midagi omavahel konflikti ei läheks. Seega kõik sellised suure teenuse paigaldused peaksid jälgima kindlat paikapandud süsteemi, et saavutada korduvalt sama tulemus, näiteks süsteemi taaste või teisele serverile kolimise korral. Sellise mahuga teenuse puhul, kui seda on vaja korduvalt paigaldada, tuleks kindlasti eelistad scripti, mis lühendaks paigalduseks kuluvat aega ja samuti välistaks inimlikud eksimused, näiteks kirjavigade näol.
Kasutatud kirjandus
http://www.ispconfig.org/page/home.html
http://www.howtoforge.com/perfect-server-ubuntu-13.04-apache2-bind-dovecot-ispconfig-3