Auditd: Difference between revisions
| Line 55: | Line 55: | ||
==Audit system architecture== | ==Audit system architecture== | ||
[[File:audit_components1.png|right|thumb|Audit components]] | [[File:audit_components1.png|right|thumb|Audit components]] | ||
===Audit System components=== | |||
The following list describes Audit system components and their functionalities: | |||
;auditd | |||
:The audit daemon is responsible for writing the audit messages that were generated through the audit kernel interface and triggered by application and system activity to disk. The way the audit daemon is started is controlled by its configuration file, '''/etc/sysconfig/auditd'''. The audit system functions (once started) are controlled by '''/etc/audit/auditd.conf'''. | |||
;auditctl | |||
:The '''auditctl''' utility controls the audit system. It controls the log generation parameters and kernel settings of the audit interface as well as the rule sets that determine which events are tracked. | |||
;audit rules | |||
:The file '''/etc/audit/audit.rules''' contains a sequence of '''auditctl''' commands that are loaded at system boot time immediately after the audit daemon is started. | |||
;aureport | |||
:The '''aureport''' utility allows you to create custom reports from the audit event log. This report generation can easily be scripted, and the output can be used by various other applications, for example, to plot these results. | |||
;ausearch | |||
:The '''ausearch''' utility can search the audit log file for certain events using various keys or other characteristics of the logged format. | |||
;audispd | |||
:The audit dispatcher daemon ('''audispd''') can be used to relay event notifications to other applications instead of (or in addition to) writing them to disk in the audit log. | |||
;autrace | |||
:The '''autrace''' utility traces individual processes in a fashion similar to '''strace'''. The output of autrace is logged to the audit log. | |||
==Installation of Audit packages== | ==Installation of Audit packages== | ||
Revision as of 22:25, 11 March 2017
Auditd - is the userspace component of the Linux Auditing System[1]. It is responsible for writing audit records to the disk. The Linux Auditing System helps system administrators to create an audit trail, a log for every action on the server. Since Auditd operates at the kernel level, this gives system administrators an opportunity to get detailed information about any system operation. The Linux Audit System provides a way to track security-relevant information on the system. Based on pre-configured rules, Auditd generates log entries to record as much information about the events that are happening on the system as possible. System administrators can choose which actions on the server should be monitored and to what extent. This information is crucial for mission-critical environments to determine the violator of the security policy and the actions they performed. Auditd does not provide additional security to the system, rather it can be used to discover violations of security policies used on the system. These violations can further be prevented by additional security measures such as SELinux. The Linux Audit System is developed and maintained by RedHat[2].
Usage and use cases
Usage
Auditd is a powerful tool for system administrators as it allows them to monitor access to any file, network traffic and almost everything they would need. The level of detail is phenomenal, since the daemon operates at kernel level and the granularity of the information has been proven to be very useful. The following list summarizes some of the information that Audit can record in its log files[2]:
- Date and time, type, and outcome of an event.
- Sensitivity labels of subjects and objects.
- Association of an event with the identity of the user who triggered the event.
- All modifications to Audit configuration and attempts to access Audit log files.
- All uses of authentication mechanisms, such as SSH, Kerberos, and others.
- Changes to any trusted database, such as /etc/passwd.
- Attempts to import or export information into or from the system.
- Include or exclude events based on user identity, subject and object labels, and other attributes.
The use of Audit system is also a requirement for a number of security related certifications[2]:
- Controlled Access Protection Profile (CAPP)
- Labeled Security Protection Profile (LSPP)
- Rule Set Base Access Control (RSBAC)
- National Industrial Security Program Operating Manual (NISPOM)
- Federal Information Security Management Act (FISMA)
- Payment Card Industry — Data Security Standard (PCI-DSS)
- Security Technical Implementation Guides (STIG)
Use cases
Watching file access
Audit can track whether a file or a directory has been accessed, modified, executed, or the file's attributes have been changed. This is useful, for example, to detect access to important files and have an Audit trail available in case one of these files is corrupted.
Monitoring system calls
Audit can be configured to generate a log entry every time a particular system call is used. This can be used, for example, to track changes to the system time by monitoring the settimeofday, clock_adjtime, and other time-related system calls.
Recording commands run by a user
Because Audit can track whether a file has been executed, a number of rules can be defined to record every execution of a particular command. For example, a rule can be defined for every executable in the /bin directory. The resulting log entries can then be searched by user ID to generate an audit trail of executed commands per user.
Recording security events
The pam_faillock authentication module is capable of recording failed login attempts. Audit can be set up to record failed login attempts as well, and provides additional information about the user who attempted to log in.
Searching for events
Audit provides the ausearch utility, which can be used to filter the log entries and provide a complete audit trail based on a number of conditions.
Running summary reports
The aureport utility can be used to generate, among other things, daily reports of recorded events. A system administrator can then analyze these reports and investigate suspicious activity furthermore.
Monitoring network access
The iptables and ebtables utilities can be configured to trigger Audit events, allowing system administrators to monitor network access.
Audit system architecture
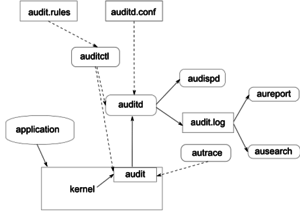
Audit System components
The following list describes Audit system components and their functionalities:
- auditd
- The audit daemon is responsible for writing the audit messages that were generated through the audit kernel interface and triggered by application and system activity to disk. The way the audit daemon is started is controlled by its configuration file, /etc/sysconfig/auditd. The audit system functions (once started) are controlled by /etc/audit/auditd.conf.
- auditctl
- The auditctl utility controls the audit system. It controls the log generation parameters and kernel settings of the audit interface as well as the rule sets that determine which events are tracked.
- audit rules
- The file /etc/audit/audit.rules contains a sequence of auditctl commands that are loaded at system boot time immediately after the audit daemon is started.
- aureport
- The aureport utility allows you to create custom reports from the audit event log. This report generation can easily be scripted, and the output can be used by various other applications, for example, to plot these results.
- ausearch
- The ausearch utility can search the audit log file for certain events using various keys or other characteristics of the logged format.
- audispd
- The audit dispatcher daemon (audispd) can be used to relay event notifications to other applications instead of (or in addition to) writing them to disk in the audit log.
- autrace
- The autrace utility traces individual processes in a fashion similar to strace. The output of autrace is logged to the audit log.