NSA - MS17-010
Microsoft Security Bulletin MS17-010 - NSA Tool leak
Introduction
At last April 8, TheShadowBrokers has published a bunch of tools that was stolen from the NSA Arsenal Hacker Tools. A Github repository is the following: https://github.com/misterch0c/shadowbroker. In this paper, we’ll focus on ETERNALBLUE exploit for Microsoft Windows and the plugin DOUBLEPULSAR. To leverage these “fantastic” codes, we’ll be using FUZZBUNCH, The NSA’s “Metasploit”
Why Eternalblue & DoublePulsar?
ETERNALBLUE is the only one that can be used to attacking Windows 7 and Windows Server 2008 without needing authentication. After that, we can use the plugin DOUBLEPULSAR in order that injecting remotely a malicious DLL on the target machine.We wi ll make a malicious DLL using Empire to get a reverse connection from the target to the attacker machine.
Setting up Environment
Attacker:
- Windows 7 ( To execute NSA tool ): 192.168.0.106
- Kali Linux ( To generate DLL file and being a listener https://github.com/EmpireProject/Empire ): 192.168.0.109
Victim:
- Windows 7/SVR2008 : 192.168.0.107
Setting up the FuzzBunch
We are going to use FUZZBUNCH, the NSA’s “Metasploit”. As mentioned above, this framework was coded with Python 2.6 and it uses an old version of PyWin32: v2.12.
Knowing that, we must install the following tools in our Windows XP attacker machine:
- Python 2.6: https://www.python.org/download/releases/2.6/ (add it to the Windows’ PATH environment variable)
- PyWin32 v2.12: https://sourceforge.net/projects/pywin32/files/pywin32/Build%20212/
- Notepad++: https://notepad-plus-plus.org/download/ (You can also use Notepad).
All of them are executable installers so we can just press “next, next, next, accept, next…”.
When we finish our installations, we must open a cmd.exe and move to the folder where the tool was downloaded, punctually where the FUZZBUNCH: “fb.py” is (inside the folder shadowbrokermaster/Windows) and then execute “python fb.py”.
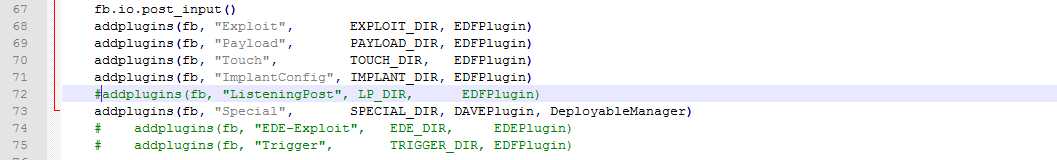
You will see that it won’t run correctly, the script will show you an error because it’s not finding the directory named “ListeningPost”. This happens because inside the leak that specific folder is empty. So, to avoid that error we edit “fb.py” and simply comment the line number 72: