Local Attacks: Difference between revisions
| Line 42: | Line 42: | ||
u: owner (owner) | u: owner (owner) | ||
g: group ownership (group) | g: group ownership (group) | ||
o: the ordinary users (other) | o: the ordinary users (other) | ||
Revision as of 22:24, 11 April 2016
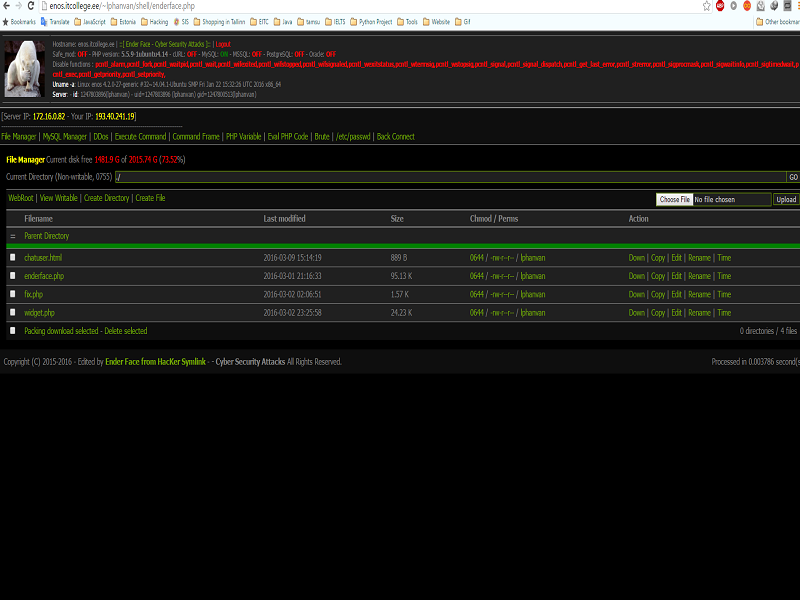
Attack A Website by Using Local Method (Local Attack)
What is Local Attack?
In generally, once we host the website to server, after that the user will be provided an " user account" and the directory/folder to mange their website. For instance, the user 1 has a website "A" and one directory/folder : /home/user1 to manage user 1. Similarly, the user 2 has a website "B" and one directory/folder /home/user2 to manage.
Local attack is the the method which is applied to hack a website in the same server. For example, I want to attack website "A" from user 1, but unfortunately I could not find out the vulnerabilities to exploit and get an lien from it, that means I have no way to attack based on this site "A". So, I will look for the websites which are being on the same server with "A", could be website "B" or "C".
Based on site "B" or "C", the both of them are getting some vulnerabilities or another words is " hackable ". After getting the authorities on those site "B" or "C", I will upload the php file named " Shell " to the server of "B" or "C" it's also the server of website "A". The hacking process is starting from now.....
Pros and Cons of Local Attack
Pros:
*This way could be the good way to attack a website through the web same server with it once we can not find any vulnerabilities to hack.
*Nowadays, in order to save the money to buy the private server, the host should hire the server in which belong with other host. The Local attack should be common way.
Cons:
*The administrator could find out how the access come from
*Local attack will not be successful when the targets are not being in the same server with other ones.
*Demand to know enough about " shell, linux command line, website development and networking as well"
What we need to know?
Normally for web site, its data must be stored on one server (server) is always active and connected to the internet. Storage space on the server used to store the data of the website is called the host. For a number of agencies and organizations, the hired one server for data storage is not practical website. Due to their needs is simply stored, further 1 server rental price is not cheap. Therefore, shared hosting is a reasonable choice. With shared hosting, server memory space is divided into many small hosts, and are separate from each rental. So on one server will contain data for multiple websites, and there is also a source of security for developing local attack.
Decentralized system
Unlike Windows, Linux operating system has a decentralized system is complicated and strict. Linux supports three basic working :
r: read access (read)
w: right to record (write)
x: right to execute (execute)
-: not allowed
These rights are assigned to three subjects:
u: owner (owner)
g: group ownership (group)
o: the ordinary users (other)
Character One: identify the type of file.
-: regular files (text, binary, executed file) d: folder c / b: device file l: file link next 9 characters: define permissions to read, write, execute for the owner, ownership and user groups remaining.
Change group / owner: chown, chgrp Performed by root or their respective owners.
Change of ownership:
chown user_name file_name
Change the ownership group:
GROUP_NAME chgrp file_name