OSSEC: Difference between revisions
No edit summary |
|||
| Line 71: | Line 71: | ||
The following operating systems are supported by the OSSEC agent: | The following operating systems are supported by the OSSEC agent: | ||
GNU/Linux (all distributions, including RHEL, Ubuntu, Slackware, Debian, etc) | |||
Windows 7, XP, 2000 and Vista | |||
Windows Server 2003 and 2008 | |||
VMWare ESX 3.0,3.5 (including CIS checks) | |||
FreeBSD (all versions) | |||
OpenBSD (all versions) | |||
NetBSD (all versions) | |||
Solaris 2.7, 2.8, 2.9 and 10 | |||
AIX 5.3 and 6.1 | |||
HP-UX 10, 11, 11i | |||
MacOSX 10 | |||
===Devices support via Syslog=== | ===Devices support via Syslog=== | ||
| Line 87: | Line 87: | ||
These systems/devices are also supported via remote syslog: | These systems/devices are also supported via remote syslog: | ||
Cisco PIX, ASA and FWSM (all versions) | |||
Cisco IOS routers (all versions) | |||
Juniper Netscreen (all versions) | |||
SonicWall firewall (all versions) | |||
Checkpoint firewall (all versions) | |||
Cisco IOS IDS/IPS module (all versions) | |||
Sourcefire (Snort) IDS/IPS (all versions) | |||
Dragon NIDS (all versions) | |||
Checkpoint Smart Defense (all versions) | |||
McAfee VirusScan Enterprise (v8 and v8.5) | |||
Bluecoat proxy (all versions) | |||
Cisco VPN concentrators (all versions) | |||
===Agentless=== | ===Agentless=== | ||
| Line 104: | Line 104: | ||
Using OSSEC agentless options, the following systems are also supported (for log analysis and file integrity checking): | Using OSSEC agentless options, the following systems are also supported (for log analysis and file integrity checking): | ||
Cisco PIX, ASA and FWSM (all versions) | |||
Cisco IOS routers (all versions) | |||
Juniper Netscreen (all versions) | |||
SonicWall firewall (all versions) | |||
Checkpoint firewall (all versions) | |||
All operating systems specified in the “operating systems” section | |||
==Database monitoring=== | |||
Database monitoring is available for the following systems: | Database monitoring is available for the following systems: | ||
MySQL (all versions) | |||
PostgreSQL (all versions) | |||
Oracle, MSSQL (to be available soon) | |||
===Individual log formats and application support=== | ===Individual log formats and application support=== | ||
Unix-only: | Unix-only: | ||
Unix Pam | |||
sshd (OpenSSH) | |||
Solaris telnetd | |||
Samba | |||
Su | |||
Sudo | |||
Xinetd | |||
Adduser/deluser/etc | |||
Cron/Crontab | |||
Solaris BSM Auditing | |||
Dpkg (Debian package) logs | |||
Yum logs | |||
FTP servers: | FTP servers: | ||
Proftpd | |||
Pure-ftpd | |||
vsftpd | |||
wu-ftpd | |||
Microsoft FTP server | |||
Solaris ftpd | |||
Mac OS FTP server | |||
Mail servers: | Mail servers: | ||
Imapd and pop3d | |||
Postfix | |||
Sendmail | |||
vpopmail | |||
Microsoft Exchange | |||
Courier imapd/pop3d/pop3-ssl | |||
vm-pop3d | |||
SMF-SAV (Sendmail Sender Address Validator) | |||
Procmail | |||
Mailscanner | |||
Web servers: | Web servers: | ||
Apache web server (access log and error log) | |||
IIS 5/6 web server (NSCA and W3C extended) | |||
Zeus web server | |||
Web applications: | Web applications: | ||
Horde imp | |||
Modsecurity | |||
Firewalls: | Firewalls: | ||
Iptables firewall | |||
Shorewall (iptables-based) firewall | |||
Solaris ipfilter firewall | |||
AIX ipsec/firewall | |||
Netscreen firewall | |||
Windows firewall | |||
Cisco PIX/ASA/FWSM | |||
SonicWall firewall | |||
Checkpoint firewall | |||
Databases: | Databases: | ||
MySQL | |||
PostgreSQL | |||
NIDS: | NIDS: | ||
Cisco IOS IDS/IPS module | |||
Snort IDS (snort full, snort fast and snort syslog) | |||
Dragon NIDS | |||
Checkpoint Smart defense | |||
Security tools: | Security tools: | ||
Symantec Anti Virus | |||
Symantec Web Security | |||
Nmap | |||
Arpwatch | |||
McAfee VirusScan Enterprise (v8 and v8.5) | |||
Others: | Others: | ||
Named (bind) | |||
Squid proxy | |||
Bluecoat proxy | |||
Cisco VPN Concentrator | |||
Cisco IOS routers | |||
Asterisk | |||
Vmware ESX | |||
Windows event logs (logins, logouts, audit information, etc) | Windows event logs (logins, logouts, audit information, etc) | ||
Windows Routing and Remote Access logs | Windows Routing and Remote Access logs | ||
Generic unix authentiction (adduser, logins, etc) | Generic unix authentiction (adduser, logins, etc) | ||
Revision as of 15:43, 9 January 2015
Autor Oliver Karjane AK31 2014
Mis on OSSEC?
OSSEC (Open Source Host-based Intrusion Detection System) on hostipõhine sissemurdmise avastamise süsteem, mis tegeleb logide analüüsi, failide tervikluse kontrolli, süsteemipoliitika jälgimise, rootkit'ide avastamise ja reaalajas alarmide andmise ja neile aktiivselt vastamisega.
Tegemist on tervikliku platvormiga süssteemi jälgimiseks ja kontrollimiseks.
Tarkvara töötab enamustel operatsioonisüsteemidel, kaasarvatud Linux, MacOS, Solaris, HP-UX, AIX ja Windows.
OSSEC omadused ja võimalused.
- Süsteemi turvastandardite nõuetele vastavuse tagamine
- Multiplatvormne
- Reaalaja ja seadistatavad alarmid
- Olemasoleva taristuga integreerimine
- Keskhaldus
- Monitoorimine agentprogrammi abil ja ilma
- Failide tervikluse kontrollimine
- Logide jälgimine
- Rootkit avastamine
- Aktiivne reageerimine
Kuidas OSSEC töötab?
OSSEC koosneb mitmest osast, kesksest haldusserverist, mis jälgib kogu süsteemi ja kogub infot agentprogrammidelt, süsteemi logidest, andmebaasidest ja agentideta seadmetest.
Keskne haldusserver
OSSEC paigalduse süda, siin talletatakse failide tervikluse kontrolli andmabaasid, logid, juhtumid ja süsteemi auditeerimie sissekanded. Kõik reeglid, dekooderid ja peamised seadistuste valikud on samuti salvestatud siia, mis muudab lihtsaks korraga paljude agentprogrammide haldamise.
Agentprogrammid
Agentprogramm on väike tükk tarkvara, mis paigaldatakse süsteemi mida soovitakse jälgida. Agent korjab reaalajas informatsiooni ja edastab selle kesksele haldussserverile. Vaikimisi kasutab väga vähe resursse (mälu ja CPU).
Agentprogrammi turvalisus: agent töötab madala privileegiga kasutaja õigustes, mis luuakse paigalduse käigus ning süsteemist eraldatuna (chroot jail). Enamus agendi seadistusetest antakse keskse haldusserveri poolt ja ainult mõned neist salvetatakse lokaalselt. Juhul kui lokaalseid seadistusi muudetakse saab haldusserver sellekohase info ja tekitab alarmi.
Agentideta seadmed
Süsteemide jaoks, kuhu ei ole võimalik paigaldada agentprogrammi, pakub OSSEC võimalust failide terviklust jälgida ka ilma selleta. Kasulik on see näiteks võrguseadmete või UNIX süsteemide jälgimiseks, kuhu kas pole võimalik või puudub õigus agentprogrammi paigaldada.
Virtualiseerimine/Vmware
OSSEC lubab paigaldada agentprogrammi nii virtualiseeritud süsteemidele kui ka Vmware serverile (Vmware ESX) endale. Serverile paigaldatuna saadab agent teateid virtualiseeritud süsteemide paigaldamise, eemaldamise, käivitamise jne. kohta. Samuti jälgib agent serverisse sisse logimisi, välja logimisi ja veateateid. Lisaks sellele teeb OSSEC CIS (Center for Internet Security) kontrolli Vmware serverile, andes häiret kui avastatakse ebaturvaline seadistus või mingi muu probleem.
Tulemüürid, switch'id, ruuterid
OSSEC oskab vastu võtta ja analüüsida paljude võrguseadmete süsteemi logisid.
Arhitektuur
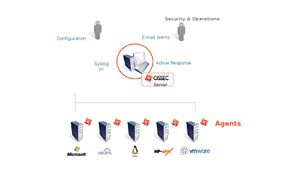
Kõrvalolev diagramm näitab keskset haldusserverit vastu võtmas infot agentidelt ja süsteemi logisid seadmetelt võrgus. Kui midagi avastatakse on võimalik aktiivselt reageerida ning administratorile saadetakse teavitus.
Tarkvara tugi
Kuigi OSSEC on avatud koodiga tarkvara, on võimalik sellele saada tasulist tuge. Seda teenust pakub firma nimega Trend Micro, mis on selle projekti toetajaks. Täpsemat infot tugiteenuse kohta saab siit.
Supported Systems
OSSEC supports the following operating systems and log formats:
Operating systems
The following operating systems are supported by the OSSEC agent:
GNU/Linux (all distributions, including RHEL, Ubuntu, Slackware, Debian, etc) Windows 7, XP, 2000 and Vista Windows Server 2003 and 2008 VMWare ESX 3.0,3.5 (including CIS checks) FreeBSD (all versions) OpenBSD (all versions) NetBSD (all versions) Solaris 2.7, 2.8, 2.9 and 10 AIX 5.3 and 6.1 HP-UX 10, 11, 11i MacOSX 10
Devices support via Syslog
These systems/devices are also supported via remote syslog:
Cisco PIX, ASA and FWSM (all versions) Cisco IOS routers (all versions) Juniper Netscreen (all versions) SonicWall firewall (all versions) Checkpoint firewall (all versions) Cisco IOS IDS/IPS module (all versions) Sourcefire (Snort) IDS/IPS (all versions) Dragon NIDS (all versions) Checkpoint Smart Defense (all versions) McAfee VirusScan Enterprise (v8 and v8.5) Bluecoat proxy (all versions) Cisco VPN concentrators (all versions)
Agentless
Using OSSEC agentless options, the following systems are also supported (for log analysis and file integrity checking):
Cisco PIX, ASA and FWSM (all versions) Cisco IOS routers (all versions) Juniper Netscreen (all versions) SonicWall firewall (all versions) Checkpoint firewall (all versions) All operating systems specified in the “operating systems” section
Database monitoring=
Database monitoring is available for the following systems:
MySQL (all versions) PostgreSQL (all versions) Oracle, MSSQL (to be available soon)
Individual log formats and application support
Unix-only:
Unix Pam
sshd (OpenSSH)
Solaris telnetd
Samba
Su
Sudo
Xinetd
Adduser/deluser/etc
Cron/Crontab
Solaris BSM Auditing
Dpkg (Debian package) logs
Yum logs
FTP servers:
Proftpd
Pure-ftpd
vsftpd
wu-ftpd
Microsoft FTP server
Solaris ftpd
Mac OS FTP server
Mail servers:
Imapd and pop3d
Postfix
Sendmail
vpopmail
Microsoft Exchange
Courier imapd/pop3d/pop3-ssl
vm-pop3d
SMF-SAV (Sendmail Sender Address Validator)
Procmail
Mailscanner
Web servers:
Apache web server (access log and error log)
IIS 5/6 web server (NSCA and W3C extended)
Zeus web server
Web applications:
Horde imp
Modsecurity
Firewalls:
Iptables firewall
Shorewall (iptables-based) firewall
Solaris ipfilter firewall
AIX ipsec/firewall
Netscreen firewall
Windows firewall
Cisco PIX/ASA/FWSM
SonicWall firewall
Checkpoint firewall
Databases:
MySQL
PostgreSQL
NIDS:
Cisco IOS IDS/IPS module
Snort IDS (snort full, snort fast and snort syslog)
Dragon NIDS
Checkpoint Smart defense
Security tools:
Symantec Anti Virus
Symantec Web Security
Nmap
Arpwatch
McAfee VirusScan Enterprise (v8 and v8.5)
Others:
Named (bind)
Squid proxy
Bluecoat proxy
Cisco VPN Concentrator
Cisco IOS routers
Asterisk
Vmware ESX
Windows event logs (logins, logouts, audit information, etc) Windows Routing and Remote Access logs Generic unix authentiction (adduser, logins, etc)