Windows juhend: Kuidas kasutada Microsoft BitLocker Administration and Monitoring-t
Mis on Microsoft Bitlocker Administration and Monitoring
Microsoft Bitlocker Administration and Monitoring (MBAM)pakub lihtsalt hallatava kasutajaliidese Bitlockeri kasutamiseks. MBAM laseb haldajal valida Bitlockeri krüpteerimise reegleid vastavalt organisatsiooni vajadustele, et kooskõlastada asutuse arvutitete reeglite ja teavitada serverile, kui asutuse arvuti krüpteerimise seisundiga on toiminud mingi lubamatu muudatus. Lisaks sellele saab MBAM-i abil pääseda ligi taastus võtmele, isegi siis kui arvuti kasutaja on oma PIN koodi ära unustanud, või kui tema BIOS või bootimis mälus on toimunud mingisugune muudatus.
Eesmärk
Organisatsioonid üle maailma kasutavad Bitlocker Drive Encryption ja Bitlocker To Go, et kaitsta enda olulisi andmeid, kuna suurtes organisatsioonides ja firmades on palju arvuteid siis paljud suur firmad kasutavad Bitlocker Administration and Monitoringut (MBAM), et muuta Bitlockeri haldamine hõlpsamaks. Firma administraatoril on kõikide arvutite Bitlockeri andmed serveris olemas. Kui mõni töötaja unustab oma PIN koodi ära saab hõlpsasti kõvaketta lukust lahti teha, kuid kui puuduks selline süsteem siis võib jääda väga vajalikest andmedest ilma.
Nõudmised
Server
Serveri operatsioonis süsteem: Windows Server 2008 sp2 või uuem.
Et kasutada Bitlockeri Administreerimist ja monitoorimist on vajalik, et serveril oleks installeeritud järgmised serveri rollid ja funktsioonid: • • Windows Server Web Server Role • • Web Server Role Services Common HTTP Features: • • Static Content • • Default Document Application Development: • • ASP.NET • • .NET Extensibility • • ISAPI Extensions • • ISAPI Filters Security: • • Windows Authentication • • Request Filtering • • Windows Server Features • • .NET Framework 3.5.1 features • • .NET Framework 3.5.1 • • WCF Activation • • HTTP Activation • • Windows Process Activation Service • • Process Model • • .NET Environment Configuration APIs
Klient
MBAM Kliendi operatsioonisüsteem: Operating System Edition Service Pack System Architecture Windows 7 Enterprise Edition None, SP1 x86 or x64 Windows 7 Ultimate Edition None, SP1 x86 or x64
• Trusted Platform Module (TPM) v1.2 • The TPM chip must be turned on in the BIOS and be resettable from the operating system. Look in the BIOS documentation for more information.
Serveri Installeerimine
Bitlockeri Administreerimine ja monitoorimise installeerimiseks on kolm varianti:
1)Ühe arvuti konfiguratsioon:
Kõik MBAM-i vajalikud funktsioonid installeritakse ühe serveri peale, see konfiguratsioon on toetatud, kuid soovitatud vaid testimis eesmärkidel.
2) Kolme arvuti konfiguratsioon
Serveri rollid ja lisad installeritakse järgnevalt:
• Recovery and Hardware Database, Compliance and Audit Reports, and Compliance and Audit Reports installeritakse ühele serverile
• Administration and Monitoring Server feature installeritakse teisele serverile
• Group Policy template installeeritakse serverile või kasutaja arvutisse
3) Viie arvuti konfiguratsioon
Igale arvutile installeeritakse üks funktsioon.
· Recovery and Hardware Database
· Compliance Status Database
· Compliance and Audit Reports
· Administration and Monitoring Server
· Group Policy Template is installed on a server or client computer
Soovitatav on kasutada 3 arvuti konfiguratsiooni.
Installeerimise algus:
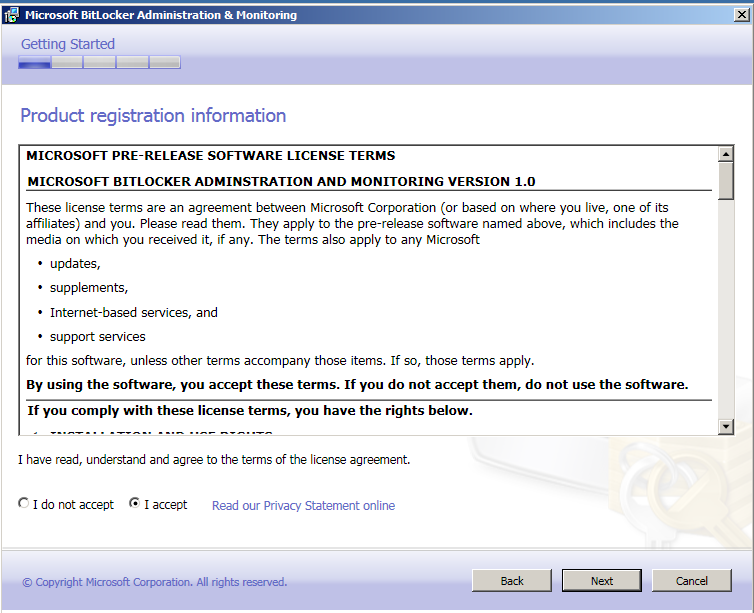
Esmalt tuleb läbi lugeda litsents tingimused ning nõustuda (accept).
Selle juhendi läbimiseks kasutame me ühe arvuti konfiguratsiooni, mis reaalsuses on soovitatav vaid testimis eesmärkidel.
Järgnevalt kontrollib installer kas kõik vajalikud komponendid serveri installerimiseks on olemas
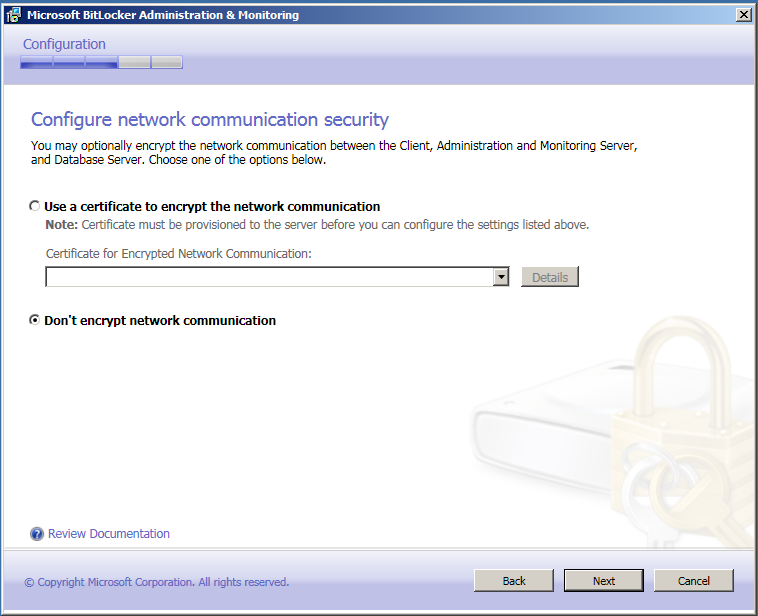
Kuna hetkel toimub see kinnises keskkonnas, siis me ei krüpteeri võrku, kuid kui tegu oleks mõne firma või organisatsiooni võrguga siis peab seda kindlasti tegema.
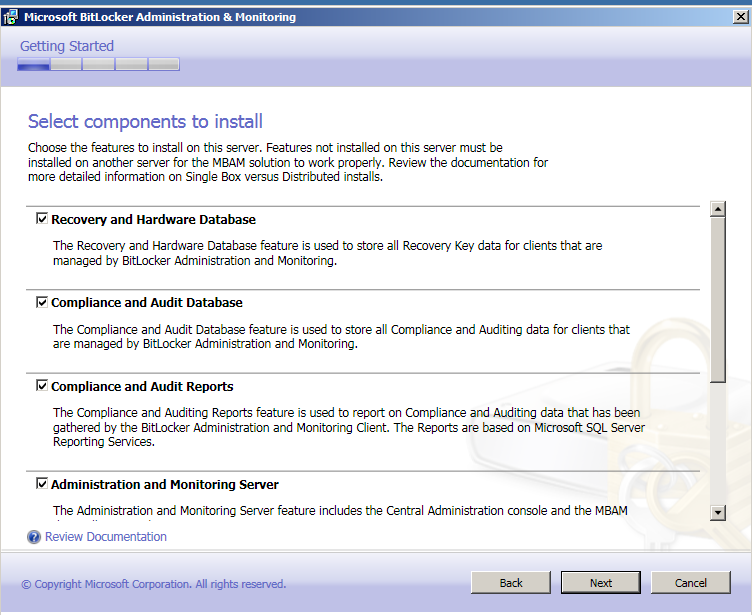
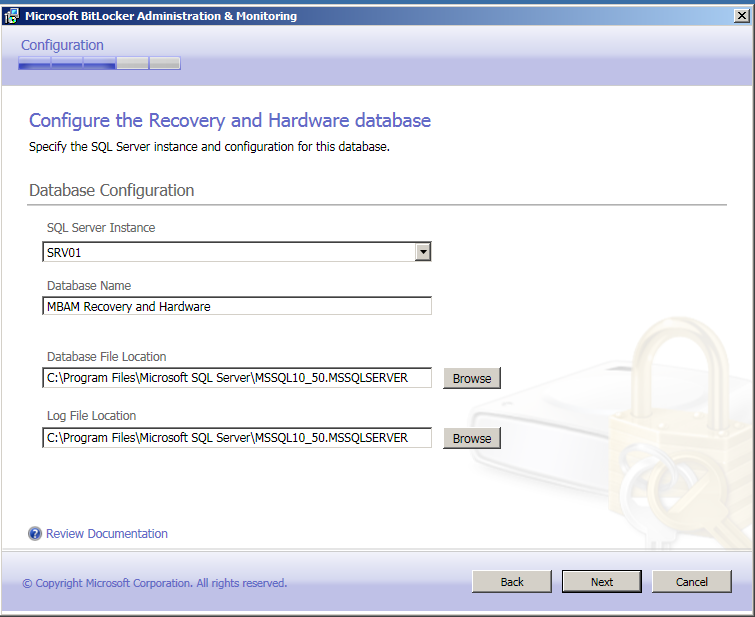
Valige riistvara ja taastus andmebaas
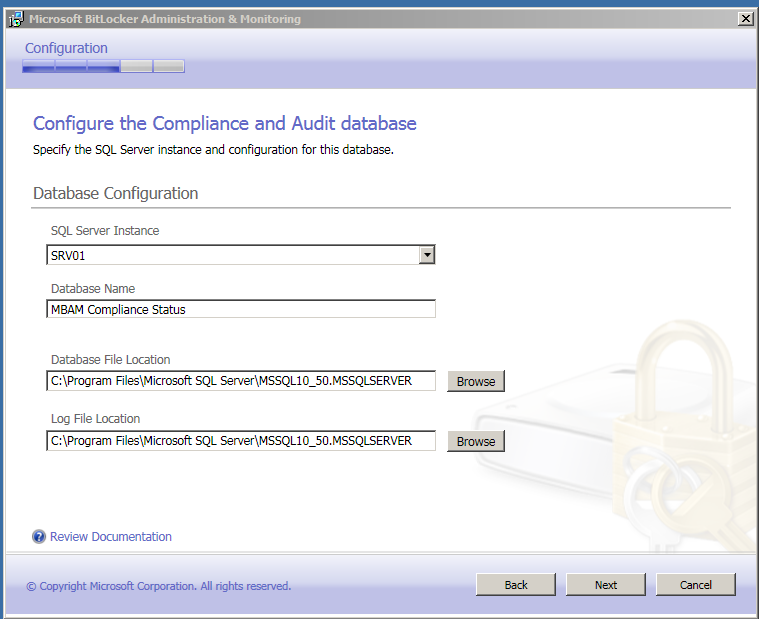
Compliance audit andmebaas
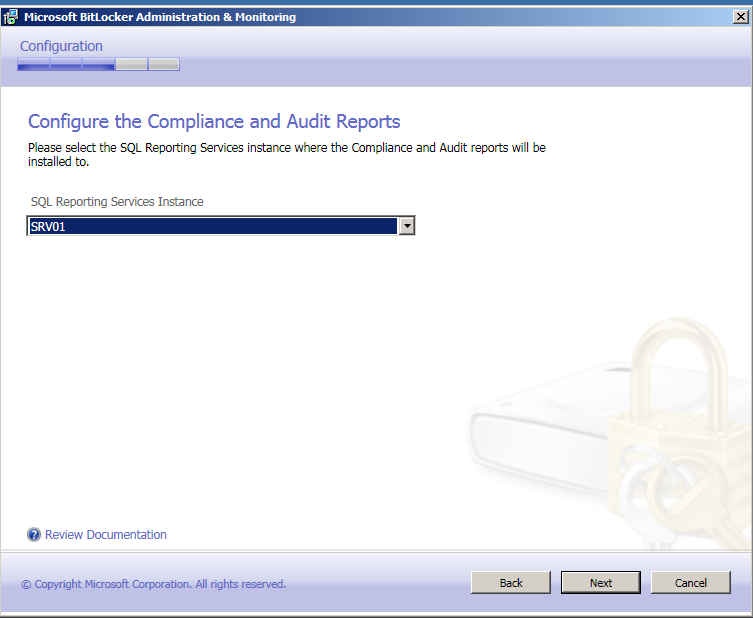
Valige server kuhu rapordid esitatakse
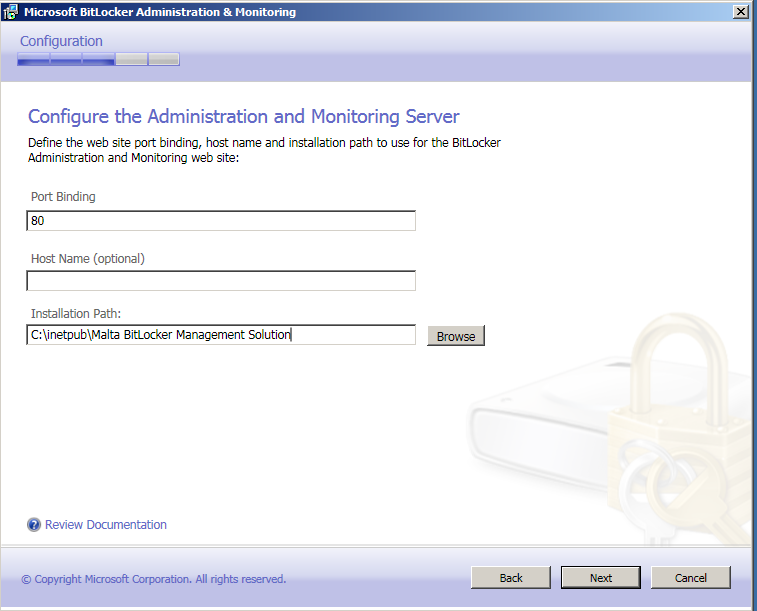
Järgmisena peate seadistama MBAM-i veebilehe
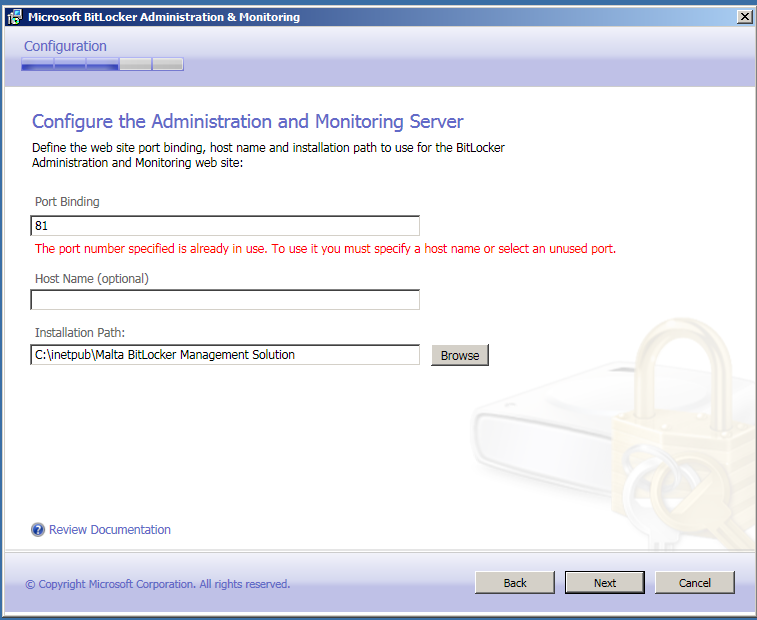
Kui mõni teine programm kasutab juba sellist porti, peate valima muu pordi.
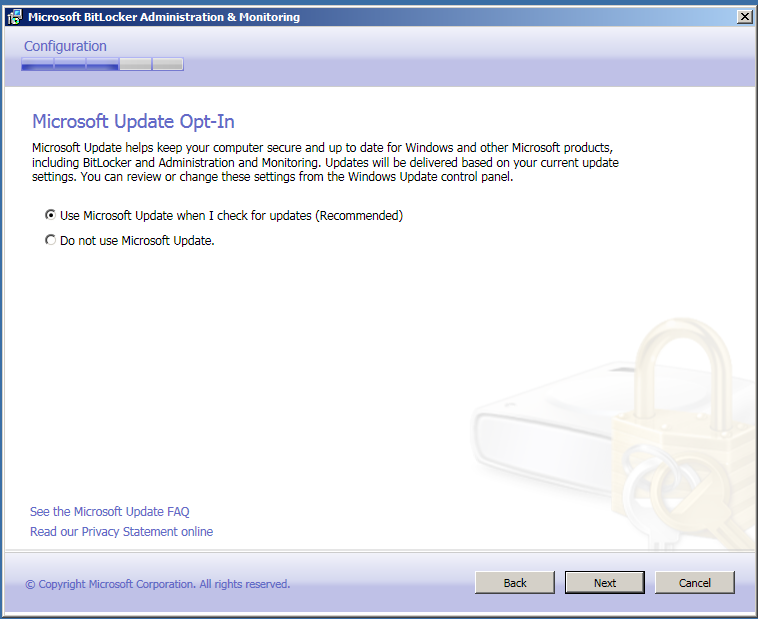
Seejärel valiga kas soovite, et MBAM uuendaks ennast automaatselt või mitte.
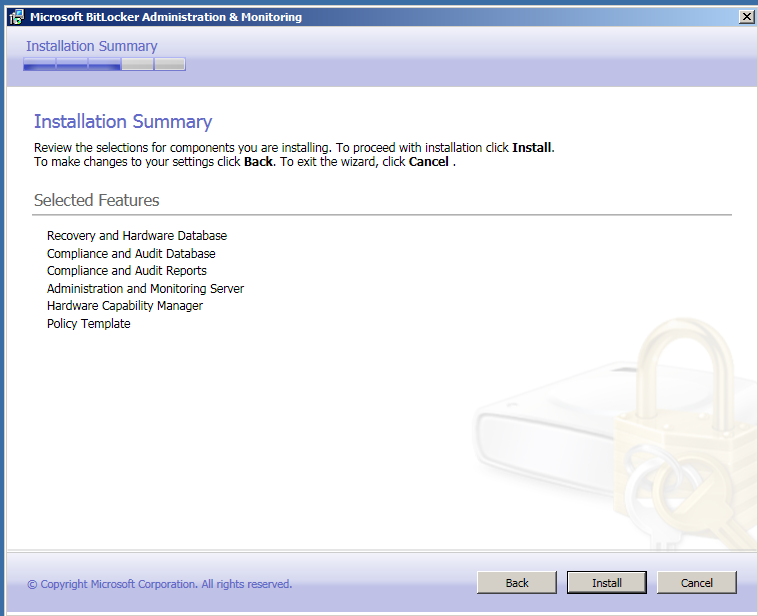
Kui kõik eelnev tehtud, võib hakata programmi installeerima.
Serveri installeering on edukalt tehtud.
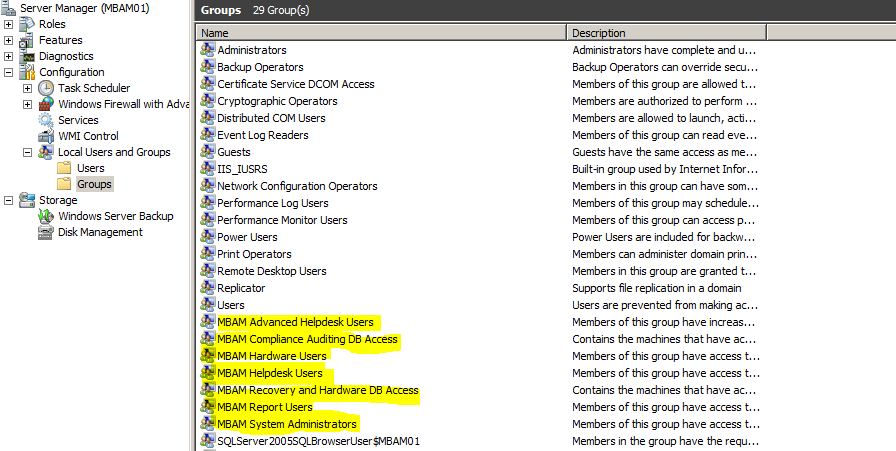
Kasutajagruppide loomine
Loome süsteemi järgnevad kasutajagrupid:
Assign administrative users to groups in Active Directory Domain Services.
Add security groups to the roles for MBAM on the Microsoft BitLocker Administration and Monitoring server for the respective features.
MBAM System Administrators have access to all Microsoft BitLocker Administration and Monitoring features in the MBAM Management Console
MBAM Hardware Users have access to the Hardware Compatibility features in the MBAM Management Console
MBAM Helpdesk Users have access to the Manage TPM and Drive Recovery options in the MBAM Management Console, but must fill in all fields when they use either option
MBAM Report Users have access to the Compliance and Audit reports in the MBAM Management Console
MBAM Advanced Helpdesk Uses have access to the Manage TPM and Drive Recovery options in the MBAM Management Console but are not required to fill in all fields when they use either option
Kliendi installeerimine
Kliendi installeerimiseks kasutame GPO-d ja konfiguratsioon saabub läbi grupi poliiside
MBAMClient-32bit.msi
MBAMClient-64bit.msi
Operations for MBAM
How to Determine BitLocker Encryption State of Lost Computers
Microsoft BitLocker Administration and Monitoring (MBAM) sisaldab võimalust jälgida viimast teadaolevat krüptimisolekut arvutitel, mis on kadunud või varastatud. Järgmisena selgitatakse, kuidas määrata, kas mahud arvutis on krüpteeritud, kui on kadunud või varastatud. Et teha kindlaks, BitLocker krüpteerimine olekut kaotatud arvutites:
Avage veebibrauser ja navigeerige BitLocker Administration and Monitoring juhtimis konsooli.
Märkus: vaikimisi on juhtimis konsooli aadress http:// <arvutinimi>.
Valige "Report" navigeerimispaanil ja seejärel valige Computer Compliance Report. Kasutage otsingufiltreid et kitsendada otsingutulemusi ja seejärel vajutage nuppu Search.
Leitud tulemusi näidatakse allpool. Valige seejärel käsk mida soovite teha kaotatud seadme puhul.
Märkus seadme compliance määratakse vastavalt BitLockeri poliitikale, seega kontrollimise kasutusele poliitika on soovitatav, kui sa üritad teha kindlaks BitLocker krüpteerimist seadme olekut.
How to Recover an Encrypted Drive
The Encrypted Drive Recovery features of Microsoft BitLocker Administration and Monitoring (MBAM) ensure the capture and storage of data and availability of tools required to access a BitLocker-protected volume when BitLocker goes into recovery mode, is moved, or becomes corrupted. Use the following procedures to recover a BitLocker-protected drive. To Recover a Locked Drive
The Encrypted Drive Recovery features of Microsoft BitLocker Administration and Monitoring ensure the capture and storage of data and availability of tools required to access a BitLocker-protected volume when BitLocker goes into recovery mode. A BitLocker-protected volume goes into recovery mode when a PIN or password is lost or forgotten, or when the Trusted Module Platform (TPM) chip detects changes to the BIOS or startup files of a computer. Use this procedure to access the centralized key recovery data system that can provide a recovery password, as long as a recovery password ID and associated user identifier are supplied. Open a web browser and navigate to the Microsoft BitLocker Administration and Monitoring website. In the navigation pane, click Drive Recovery. This opens the “Recover access to an encrypted drive” webpage. Enter the Window Logon domain and user name of the user to view recovery information and the first eight digits of the recovery key ID to receive a list of possible matching recovery keys or the entire recovery key ID to receive the exact recovery key. Select one of the predefined options in the Reason for Drive Unlock drop-down list, and then click Submit. Note If you are an MBAM Advanced Helpdesk user, the user domain and user ID entries are not required. Microsoft BitLocker Administration and Monitoring returns the following: An error message if no matching recovery password is found Multiple possible matches if the user has multiple matching recovery passwords The recovery password and recovery package for the submitted user Note If you are recovering a damaged drive, the recovery package option provides BitLocker with critical information necessary to attempt to recover the drive. After the recovery password and recovery package are retrieved, the recovery password is displayed. To copy the password, click Copy Key, and then paste the recovery password into an email message. Or, to save the recovery password to a file, click Save. When the user types the recovery password into the system or uses the recovery package, the drive is unlocked. To Recover a Moved Drive
When you move an operating system drive that is encrypted by usingMicrosoft BitLocker Administration and Monitoring, the drive will not accept the PIN used in previous computer because of the change to the Trusted Platform Module (TPM) chip. You will need a way to obtain the recovery key ID to retrieve the recovery password in order to use the moved drive. Use the following procedure to recover a drive that has moved. Start the computer that contains the moved drive in Windows recovery environment (WinRE) mode, or start the computer by using Microsoft Diagnostic and Recovery Tool 6.5 (MS DaRT). As soon as the computer has been started with WinRE or MS DaRT, MBAM will treat the moved operating system drive as a data drive. MBAM will then display the drive’s recovery password ID and ask for the recovery password. Note In some cases, you may click I forget the PIN during the startup process and enter the recovery mode. This also displays the recovery key ID. Use the recovery key ID to retrieve the recovery password and unlock the drive from the MBAM console website. If the moved drive was configured to use a TPM chip on the original computer, you must take additional steps after unlocking the drive and completing the start process. In WinRE mode, open a command prompt and use the ‘manage-bde’ tool to decrypt the drive, this is the only way to remove the TPM plus PIN protector without the original TPM chip. As soon as this is completed, start the system normally. The MBAM agent will now enforce the policy to encrypt the drive with the new computer’s TPM plus PIN. To Recover a Corrupted Drive
To recover a corrupted drive protected by BitLocker, a Microsoft BitLocker Administration and Monitoring help desk user will need to create a recovery key package file. This package file can then be copied to the computer that contains the corrupted drive, and then used to recover the drive. Use the following procedure for the steps needed to do this. To create the recovery key package necessary to recover a corrupted drive, start a web browser and open the MBAM console webpage. Select Drive Recovery from the left-side navigation pane. Enter the user’s domain name, user name, reason for unlocking the drive, and the user’s recovery password ID. Note If you are a member of the Help Desk Administrators role, you do not have to enter the user’s domain name or user name. Click Submit. The recovery key will be displayed. Click Save and then select Recovery Key Package. The recovery key package will be created on your computer. Copy the recovery key package to the computer that has the corrupted drive. Open an elevated command prompt. To do this, click Start and type cmd in the Search programs and files box. Rightclick cmd.exe and select Run as Administrator. At the command prompt, type the following: repair-bde <fixed drive> <corrupted drive> -kp <location of keypackage> -rp <recovery password> Note Replace <fixed drive> with an available hard disk drive that has free space equal to or larger than the data on the corrupted drive. Data on the corrupted drive is recovered and moved to the specified hard disk drive.
How to Reset a TPM Lockout
A TPM lockout can occur if a user enters the incorrect PIN too many times. The number of times that a user can enter an incorrect PIN before the TPM locks varies from manufacturer to manufacturer. To reset a TPM lockout
Open a web browser and navigate to the MBAM Management website. In the left-side navigation pane, select Manage TPM. This will display the Manage TPM page. Enter the fully qualified domain name for the computer and the computer name and enter the user’s Windows logon domain and user name of the user to retrieve the TPM owner password file. Select one of the predefined options in the Reason for requesting TPM owner password file drop-down menu. Click Submit. Microsoft BitLocker Administration and Monitoring will return one of the following: An error message if no matching TPM owner password file is found The TPM owner password file for the submitted computer Note If you are an Advanced Helpdesk user, the user domain and user ID fields are not required After the TPM owner password is retrieved, the owner password will be displayed. The password can be saved to a .tpm file by clicking the Save button. The user will run the TPM management console and select the Reset TPM lockout option and provide the TPM owner password file to reset the TPM lockout.
TPM töösulg võib juhtuda, kui kasutaja sisestab vale PIN koodi liiga palju kordi.
Et nullida TPM töösulg avage veebibrauser ja navigeerida MBAM juhtimine veebilehel.
Vasakul navigeerimispaanil, valige Manage TPM. See avab Manage TPM lehel. Sisesta täielikult kvalifitseeritud domeeninimi ja arvuti nimi ja sisestage kasutaja Windowsi sisselogimisel domeeni ja kasutaja nime et alla laadida TPM-i õiguste parool.
Valige üks eelmääratud valikutest et saada TPM-i õiguste parool. Klõpsake nuppu Esita.
Peale esitamist Microsoft BitLocker Administration and Monitoring naaseb üks järgmistest:
veateade, kui ei leidnud TPM-i õiguste parooli valitud arvutile
leitakse TPM-i õiguste parool valitud arvutile
How to Manage Hardware Compatibility
Microsoft BitLocker Administration and Monitoring (MBAM) can collect information on both make and model of client computers if you deploy the “Allow Hardware Compatibility Checking” Group Policy. If this policy is configured, then as soon as the MBAM client is deployed on a client computer, the MBAM agent will report the make and model information for the computer to the MBAM server. Note The MBAM Hardware Compatibility feature is not enabled by default. It can be enabled by selecting the Hardware Compatibility sub feature under the Administration and Monitoring Server feature during setup. For more information about how to set up and configure Hardware Compatibility, see Planning Hardware Management for MBAM. How to Manage Hardware Compatibility
Open a web browser and navigate to the Microsoft BitLocker Administration and Monitoring website. Select Hardware in the left menu bar. On the right-side pane, click Advanced Search and filter to display a list of all computer models that have a Capability status of Unknown. This returns a list of computer models matching the search criteria. Administrators can add, edit, or remove new computer types from this page. Review each unknown hardware configuration to determine whether the configuration should be set to Compatible or Incompatible. Select one or more rows, and then click either Set Compatible or Set Incompatible to set the BitLocker compatibility, as appropriate, for the selected computer models. If set to Compatible, BitLocker tries to enforce drive encryption policy on computers that match the supported model. If set to Incompatible, BitLocker will not enforce drive encryption policy on those computers.
Administrators should monitor regularly the hardware compatibility list to review new models discovered by the Microsoft BitLocker Administration and Monitoring agent, and then update their compatibility setting to Compatible or Incompatible as appropriate.
Microsoft BitLocker Administration and Monitoring (MBAM) koguda teavet nii mark ja mudel kliendi arvutis, kui sa kasutada "Luba riistvara ühilduvuse kontrollimine" Group Policy. Kui see poliitika on konfigureeritud, siis niipea kui MBAM klient on juurutatud kliendi arvutisse, MBAM esindaja esitab mark ja mudel informatsiooni arvuti MBAM server. Märkus MBAM riistvara ühilduvuse funktsioon ei ole vaikimisi lubatud. Seda saab sisse lülitada menüükäsuga riistvara ühilduvuse all funktsioon all haldamiseks ja jälgimiseks Server funktsiooni seadistamise ajal. Lisateavet selle kohta, kuidas luua ja seadistada riistvara ühilduvuse kohta vt planeerimine Riistvara Management MBAM. Kuidas hallata riistvara ühilduvuse Avage veebibrauser ja navigeerida Microsoft BitLocker Administration and Monitoring veebilehel. Vali Riistvara vasakul menüüribal. Paremal poolel paanil Täpsem Otsing ja filtreerida kuvada nimekirja kõikide arvuti mudeleid, mis on suuteline staatus teadmata. See tagastab loendi arvuti mudelid vastavad otsingukriteeriumitele. Administraatorid saavad lisada, muuta või eemaldada uue arvuti tüüpe siit lehelt. Kontrollige iga tundmatu riistvara konfiguratsiooni kas konfiguratsioon tuleks määrata kooskõlas või mitte. Valige üks või mitu rida ja seejärel kas Määra Compatible või Määra Kokkusobimatud seada BitLocker ühilduvus vastavalt vajadusele valitud arvuti mudelid. Kui seatud Compatible, BitLocker püüab jõustada Drive Encryption poliitika arvutid loend, kes toetas mudel. Kui seatud Kokkusobimatud, BitLocker ei jõustada Drive Encryption poliitika nendes arvutites.
Administraatorid peaksid jälgima regulaarselt riistvara ühilduvuse loend vaadata uusi mudeleid avastas Microsoft BitLocker Administration and Monitoring agent, ja seejärel ajakohastada nende kooskõla, milles on kooskõlas või kui see on asjakohane.
How use the MBAM Client Control Panel
To open BitLocker Encryption Options, click Start and then select Control Panel. As soon as Control Panel opens, select System and Security. You can also right-click a drive in Windows Explorer and select BitLocker Encryption Options to open Control Panel Double-click BitLocker Encryption Options to open the customized MBAM control panel. You will see a list of all the hard disk drives on the computer and their encryption status, in addition to an option to manage your PIN or passwords. The list of hard disk drives on the computer can be used to verify encryption status, unlock a drive, or request an exemption for BitLocker protection if the User and Computer Exemption policies have been deployed. The BitLocker Encryption Options control panel also allows for non-administrator users to manage their PIN or passwords. By selecting Manage PIN, the user is prompted to enter both a current PIN and a new PIN (in addition to confirming the new PIN). Selecting Update PIN will reset the PIN to the new one selected by the user. To manage your password, select Unlock drive and enter your current password. As soon as the drive is unlocked, select Reset Password to change your current password.