VPN (English version): Difference between revisions
| (117 intermediate revisions by the same user not shown) | |||
| Line 5: | Line 5: | ||
Individual Internet users may secure their wireless transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and location. However, some Internet sites block access to known VPN technology to prevent the circumvention of their geo-restrictions. | Individual Internet users may secure their wireless transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and location. However, some Internet sites block access to known VPN technology to prevent the circumvention of their geo-restrictions. | ||
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, virtual tunneling protocols, or traffic encryption. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely.[http://technet.microsoft.com/en-us/library/bb742566.aspx] | A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, virtual tunneling protocols, or traffic encryption. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely. <ref>[http://technet.microsoft.com/en-us/library/bb742566.aspx] Microsoft Technet. "Virtual Private Networking: An Overview".</ref> | ||
==VPN solution | ==VPN solution benefits== | ||
Some VPN advantages are: | Some VPN advantages are: | ||
* can be used to safely transfer data between different public networks, being independent from the data transmission protocol; | * can be used to safely transfer data between different public networks, being independent from the data transmission protocol; | ||
* ensure that the data is supported by encryption and authentication protocol; | * ensure that the data is supported by encryption and authentication protocol; | ||
* remote users can connect across a company's network; | * remote users can connect across a company's network; | ||
* can be ordered from the relevant service providers, however it is important to make sure the reliability of the service. | * can be ordered from the relevant service providers, however it is important to make sure the reliability of the service. <ref>[http://www.brighthub.com/computing/hardware/articles/62501.aspx] www.brighthub.com - "Understanding VPN - Advantages and Benefits Part 1" by Steve McFarlane.</ref> | ||
== | ==VPN Tunnel== | ||
A virtual private network is a secure solution for exchanging information between trusted parties, which are not open to public traffic. Remote users and different applications are able to connect through a private tunnel. | |||
A VPN tunnel allows a network user to access or provide a network service that the underlying network does not support or provide directly. | |||
One important use of a tunneling protocol is to allow a foreign protocol to run over a network that does not support that particular protocol; for example, running IPv6 over IPv4. | |||
VPN supports two types of tunneling - voluntary and compulsory. Both types of tunneling are commonly used. | |||
In '''voluntary tunneling''', the VPN client manages connection setup. The client first makes a connection to the carrier network provider (an ISP in the case of Internet VPNs). Then, the VPN client application creates the tunnel to a VPN server over this live connection. | |||
VPN | In '''compulsory tunneling''', the carrier network provider manages VPN connection setup. When the client first makes an ordinary connection to the carrier, the carrier in turn immediately brokers a VPN connection between that client and a VPN server. From the client point of view, VPN connections are set up in just one step compared to the two-step procedure required for voluntary tunnels. <ref>[https://www.lifewire.com/vpn-tunneling-explained-818174] www.lifewire.com - "VPN Tunnels Tutorial - Types of VPNS, Protocol, and More".</ref> | ||
Some protocols to create VPN tunnels are: | Some protocols to create VPN tunnels are: | ||
* IPsec (Internet Protocol Security) - developed by the IETF and implemented at the network layer of the OSI model (Network Layer). This is a collection of various security measures, which uses a variety of cryptographic protocols for data confidentiality, integrity, authentication and key management reasons; | * IPsec (Internet Protocol Security) - developed by the IETF and implemented at the network layer of the OSI model (Network Layer). This is a collection of various security measures, which uses a variety of cryptographic protocols for data confidentiality, integrity, authentication and key management reasons; | ||
* GRE (Genaral Routing Encapsulation) - | * GRE (Genaral Routing Encapsulation) - originally developed by Cisco protocol which is able to encapsulate several different protocols packages; | ||
* PPTP (Point-to-Point Tunneling Protocol) - acts as a transmission layer of the OSI model (the Data Link Layer). The data is encapsulated in the PPP (Point to Point Protocol) packets, which are encapsulated into IP packets. PPTP supports data encryption and packing and use the GRE protocol to transfer data; | * PPTP (Point-to-Point Tunneling Protocol) - acts as a transmission layer of the OSI model (the Data Link Layer). The data is encapsulated in the PPP (Point to Point Protocol) packets, which are encapsulated into IP packets. PPTP supports data encryption and packing and use the GRE protocol to transfer data; | ||
* L2F (Layer2 Forwarding) - acts as a transmission layer of the OSI model. L2F does not have the encryption option and has been replaced by L2TP; | * L2F (Layer2 Forwarding) - acts as a transmission layer of the OSI model. L2F does not have the encryption option and has been replaced by L2TP; | ||
* L2TP (Layer2 Tunneling Protocol) - acts as a layer of the OSI model, data transfer, a Microsoft PPTP and Cisco L2F protocols properties. | * L2TP (Layer2 Tunneling Protocol) - acts as a layer of the OSI model, data transfer, a Microsoft PPTP and Cisco L2F protocols properties. <ref>[http://www.comptechdoc.org/independent/networking/protocol/prottunnel.html] http://www.comptechdoc.org - "Tunneling protocols".</ref> | ||
==Server and Client== | |||
A VPN connection requires a '''VPN Server''', the machine where to connect to, and a '''VPN Client''', the computer that connects to the server. | |||
The server is the gatekeeper at one end of the tunnel, the client at the other. The main difference between the server and the client is that it’s the client that initiates the connection with the server. A VPN client can establish a connection with just one server at a time. However, a server can accept connections from many clients. | |||
Typically, the VPN server is a separate hardware device, most often a security appliance such as a Cisco ASA security appliance. VPN servers can also be implemented in software. <ref>[http://www.dummies.com/programming/networking/network-administration-vpn-servers-and-clients/] Network Administration: VPN Servers and Clients.</ref> | |||
==VPN types== | ==VPN types== | ||
| Line 40: | Line 54: | ||
* L2TP over IPsec encapsulated; | * L2TP over IPsec encapsulated; | ||
* SSL encryption. | * SSL encryption. | ||
'''Hybrid VPN''', it is possible to transmit encrypted data through a leased line. Since the trusted and secure the use of a VPN are not mutually exclusive, the VPN is a hybrid of the technologies for making a parallel implementation. <ref>[https://networkingexchangeblog.att.com/enterprise-business/what-is-a-hybrid-vpn/] Networking Exchange Blog "What is an hybrid VPN"</ref> | |||
====Usage==== | ====Usage==== | ||
| Line 45: | Line 61: | ||
The two most common types of VPN use is the Remote-Access VPN and Site-to-Site VPN. | The two most common types of VPN use is the Remote-Access VPN and Site-to-Site VPN. | ||
Entrance VPN (Remote Access VPN), sometimes known as a virtual private dial-up (virtual private dial-up network, VPDN), is the user and the LAN connection between organizations, which are used to connect remote users to the network. Entrance VPN uses a client-server architectures, in which a remote user VPN client acquires the rights to the entrance to a network through a network of peripheral areas of the VPN server | '''Entrance VPN (Remote Access VPN)''', sometimes known as a virtual private dial-up (virtual private dial-up network, VPDN), is the user and the LAN connection between organizations, which are used to connect remote users to the network. Entrance VPN uses a client-server architectures, in which a remote user VPN client acquires the rights to the entrance to a network through a network of peripheral areas of the VPN server. | ||
Site-to-Site solution, is mounted between the networks and the static VPN connection NETWORK terminal devices are not aware of the existence of the VPN. VPN gateway is responsible for the TCP / IP packet encapsulation and encryption for. Site-to-Site VPN is divisible into two: | '''Site-to-Site solution''', is mounted between the networks and the static VPN connection NETWORK terminal devices are not aware of the existence of the VPN. VPN gateway is responsible for the TCP / IP packet encapsulation and encryption for. Site-to-Site VPN is divisible into two: | ||
* intranet VPN, mainly for the larger companies and is designed to connect the company's departments, secure channel using a single network headquarters; | * intranet VPN, mainly for the larger companies and is designed to connect the company's departments, secure channel using a single network headquarters; | ||
* extranet VPN, for customers and partners to secure the connection to companies place by linking networks. | * extranet VPN, for customers and partners to secure the connection to companies place by linking networks. <ref>[http://computer.howstuffworks.com/vpn3.htm] computer.howstuffwork.com - "How VPNs Work" by Jeff Tyson & Stephanie Crawford.</ref> | ||
=VPN solutions= | |||
Solutions that creates virtual private networks are generally divided into two categories: software and hardware. | |||
A universal solutions by software means that can be realized in different hardware assets. | |||
Building a hardware VPNs requires specialized equipment, for which, however, runs on software. | |||
=VPN | ==Software solutions== | ||
There are many different VPN software solutions available, which come as free, open-source or proprietary. | |||
Each of them is different from the other to some extent and are aimed at different target groups. | |||
'''Standard and on-demand VPN''' | |||
On-demand means that a machine connects to network then is reachable. Using same software you can either set up a connection - this means act like a server and at the other side you can connect into such machine and act as a client. | |||
===OpenVPN=== | ===OpenVPN=== | ||
| Line 68: | Line 89: | ||
OpenVPN uses UDP by default and the user's request, the TCP protocol. The solution also acts as a proxy, through most of -serverite. | OpenVPN uses UDP by default and the user's request, the TCP protocol. The solution also acts as a proxy, through most of -serverite. | ||
OpenVPN is known to have written a number of third-party client programs (such as Windows OpenVPN GUI) and its support has been integrated into some | OpenVPN is known to have written a number of third-party client programs (such as Windows OpenVPN GUI) and its support has been integrated into some routers (such as tomato, Vyatta, DD-WRT). <ref>[https://openvpn.net/index.php/open-source.html] OpenVPN project homepage.</ref> | ||
===SoftEther VPN=== | |||
SoftEther VPN ("SoftEther" means "Software Ethernet") is an open-source, available under GPL license, VPN software. | |||
It was developed by Daiyuu Nobori's Master Thesis research in the University. | |||
It is an optimum alternative to OpenVPN and Microsoft's VPN servers and can be used for any personal or commercial use for free charge. | |||
It supports multiple VPN protocols, including OpenVPN, L2TP/IPsec and SSTP and runs on Windows, Linux, Mac, FreeBSD and Solaris. | |||
The data is secured with AES 256-bit and RSA 4096-bit encryption. | |||
<ref>[https://www.softether.org] SoftEther VPN homepage.</ref> | |||
====OpenVPN vs SoftEther comparison==== | |||
Since SoftEther is a newer technology, it has implemented a different approach that aims not only to offer a high level of security, but also to ensure that users can enjoy extended compatibility. | |||
Unlike OpenVPN, which only supports its own protocol, SoftEther works with SSTP, L2TP/IPsec, SSTP and more. | |||
Speed: OpenVPN only manages to reach 100Mbps, but SoftEther is capable of going up to 900Mbps and in some cases, it can even reach higher speeds. | |||
Since OpenVPN has been available for longer, it is supported by more platforms than SoftEther, like QNX and NetBSD. | |||
SoftEther gets ahead in terms of speed and it also offers greater flexibility. | |||
OpenVPN is a stable, reliable and highly secure option that hasn’t been compromised by the likes of the NSA. <ref>[http://vpnpick.com/openvpn-vs-softether/] vpnpick.com - "OpenVPN and SoftEther comparison"</ref> | |||
===Hamachi=== | ===Hamachi=== | ||
'''Hamachi''' is a section of a proprietary VPN solution, which is primarily known for its simplicity in terms of configuration and is therefore particularly popular among the fans of computer games. Hamachi manufacturer also uses the advertising slogan "Finally, a VPN that just works" (Eventually VPN that just works). | '''Hamachi''' is a section of a proprietary VPN solution, which is primarily known for its simplicity in terms of configuration and is therefore particularly popular among the fans of computer games. Hamachi manufacturer also uses the advertising slogan "Finally, a VPN that just works" (Eventually VPN that just works). | ||
Hamachi supports VPN '''on-demand''' for networks that use certificated-based authentication, so the VPN connection is made whenever the device tries to connect to certain domains and as soon as they try to access such a server the VPN connection is initiated. | |||
Hamachi is a centrally managed VPN system that consists of a server cluster, which is managed by the producer and the client program that is installed on the end user's computer. The client program will install a new virtual network adapter to which outgoing packets are transmitted to Hamachi program, which in turn transmits them over the Internet through a UDP connection. Incoming packets are sent Hamachi program that sends them to the virtual network card. | Hamachi is a centrally managed VPN system that consists of a server cluster, which is managed by the producer and the client program that is installed on the end user's computer. The client program will install a new virtual network adapter to which outgoing packets are transmitted to Hamachi program, which in turn transmits them over the Internet through a UDP connection. Incoming packets are sent Hamachi program that sends them to the virtual network card. | ||
| Line 79: | Line 129: | ||
Hamachi uses the IP address allocation 5.0.0.0 255.0.0.0 network mask, which is not the moment for public use and therefore eliminates potential conflicts with other computers on the Internet with the address. However, it is expected to take the address range in the near future, and in this case, may use Hamachi users conflicts arise. | Hamachi uses the IP address allocation 5.0.0.0 255.0.0.0 network mask, which is not the moment for public use and therefore eliminates potential conflicts with other computers on the Internet with the address. However, it is expected to take the address range in the near future, and in this case, may use Hamachi users conflicts arise. | ||
Hamachi is available in two versions. The free version is designed for home users and supports a maximum of | Hamachi is available in two versions. The free version is designed for home users and supports a maximum of 5 computers/networs. The commercial version supports up to 256 simultaneously connected clients, but it is necessary to pay an annual fee. Hamachi is available for Windows, Mac and Linux. <ref>[https://secure.logmein.com/welcome/documentation/EN/pdf/Hamachi/LogMeIn_Hamachi_UserGuide.pdf?_ga=2.71392784.2079510906.1494096193-904917205.1494096137] LogMeIn_Hamachi_UserGuide.pdf</ref> | ||
How to install Hamachi Client on Ubuntu via the command line: | |||
* download: | |||
<pre>wget http://www.vpn.net/installers/logmein-hamachi_2.1.0.165-1_amd64.deb</pre> | |||
* install the package: | |||
<pre>sudo dpkg -i logmein-hamachi_2.1.0.165-1_amd64.deb</pre> | |||
===Shrew Soft VPN Client=== | ===Shrew Soft VPN Client=== | ||
'''Shrew Soft VPN Client''' is | '''Shrew Soft VPN Client''' is an IPsec Remote Access VPN Client for Windows and Linux. It was originally developed to provide secure communications between mobile hosts and open source VPN gateways that utilize standards compliant software such as ipsec-tools, OpenSWAN, StrongSWAN, Libreswan, isakmpd. It now offers many of the advanced features only found in expensive commercial software and provides compatibility for VPN appliances produced by vendors such as Cisco, Juniper, Checkpoint, Fortinet, Netgear, Linksys, Zywall and many others. <ref>[http://www.shrew.net/software] Shrew Software homepage.</ref> | ||
===Linux built-in VPN=== | |||
Linux OS desktop distributions have usually a built-in VPN Client and the VPN connectivity could be possible even using the CLI. | |||
For instance, the command-line '''VPN client VPNC''' is a good solution to that can quickly and easily establish a VPN connection, bypassing the GUI entirely. | |||
Installing vpnc in Debian / Ubuntu: | |||
<pre># apt-get install vpnc</pre> | |||
===Windows built-in VPN=== | ===Windows built-in VPN=== | ||
Although this property has been barely publicized, there already quite many Windows versions that had their built-in VPN client. Although Windows Vista became a built-in client with many criticism, the chances are now higher. | Although this property has been barely publicized, there already quite many Windows versions that had their built-in VPN client. Although Windows Vista became a built-in client with many criticism, the chances are now higher. | ||
VPN server for the matching funds available for Windows servers, but "leaner" home user server can be set up in a desktop version. [http://lifehacker.com/5487500/five-best-vpn-tools] | VPN server for the matching funds available for Windows servers, but "leaner" home user server can be set up in a desktop version. <ref>[http://lifehacker.com/5487500/five-best-vpn-tools] lifehacker.com - "Five Best VPN Tools" by Jason Fitzpatrick.</ref> | ||
=Hardware solutions= | ==Hardware solutions== | ||
As the name suggests, it is a special independent network devices, which implement a virtual private network. It may be a single device, which customers will connect to your computer using custom software (Remote Access), but also, for example, two devices that are constantly over a public network through a tunnel in the Community and combine thus together, for example, the various branches to local area networks (site-to-site). | As the name suggests, it is a special independent network devices, which implement a virtual private network. It may be a single device, which customers will connect to your computer using custom software (Remote Access), but also, for example, two devices that are constantly over a public network through a tunnel in the Community and combine thus together, for example, the various branches to local area networks (site-to-site). | ||
Hardware VPN has many advantages: higher security, load-balancing, capability to withstand a heavy load (ie, a large number of customers). Management is generally realized by means of a web interface. | Hardware VPN has many advantages: higher security, load-balancing, capability to withstand a heavy load (ie, a large number of customers). Management is generally realized by means of a web interface. | ||
Hardware VPN solutions offer a number of different manufacturers. [http://searchnetworking.techtarget.com/dictionary/definition/1099664/hardware-VPN.html] | Hardware VPN solutions offer a number of different manufacturers. <ref>[http://searchnetworking.techtarget.com/dictionary/definition/1099664/hardware-VPN.html] www.techtarget.com - "Hardware VPN".</ref> | ||
=How to ensure that your VPN is actually secure= | |||
A trusted virtual private network is a great tool for security and privacy, but if it's not configured correctly it may not be so private. | |||
A recent review of over 200 VPN apps on the Google Play store showed that most are not truly secure, using weak methods or no methods at all to ensure a user’s privacy and security. | |||
The most technical methods to use are packet capture tools. For the Mac there is '''Cocoa Packet Analyzer''' and for Windows there is '''Wireshark'''. Those tools allow to capture packets from your network interface and show you if they are encrypted or not. <ref>[https://binaryblogger.com/2017/01/27/ensure-vpn-actually-secure/] BinaryBlogger.com.</ref> | |||
==How to check if your VPN is leaking private data== | |||
One simple way to see if the VPN is working is to search for '''what is my IP''' <ref>[https://www.google.com/search?q=whatsmyip&oq=whatsmyip] Google whatsmyip.</ref> on Google. At the top of the search results, Google will report back your current public Internet Protocol (IP) address. If you’re on a VPN, it should show the VPN’s IP. If it doesn’t, you know you have a problem. | |||
To see how fully private you are visit '''IPLeak.net''' <ref>[https://ipleak.net/] IPLeak.net.</ref>. This website checks a number of ways that your IP address and other information can leak, including over WebRTC (an up-and-coming browser-based chat technology), DNS leaks, torrenting, and geolocation. | |||
The most likely culprit in leaked information, however, is via the '''Domain Name System (DNS)'''. To navigate the web, your machine requires contact with DNS servers to help translate website addresses from names to numeric IP addresses. Typically a PC automatically uses the DNS servers of your internet service provider. The problem is that if you’re using a VPN and leaking DNS through a local service provider, you can reveal enough information to point anyone spying on you in the right direction. | |||
A way to address this issue is to permanently switch to an alternative DNS provider such as Google, OpenDNS, or Comodo Secure DNS. <ref>[http://www.pcworld.com/article/3150256/internet/how-to-check-if-your-vpn-is-leaking-private-data.html] www.pcworld.com - "How to check if your VPN is leaking private data" by Ian Paul.</ref><br><br> | |||
[[Image:what-is-a-dns-leak.png|center|www.dnsleaktest.com]] | |||
<br> | |||
==What can you do to prevent and improve your VPN security if you find gaps?== | |||
The first step is to look at your VPN client and the options provided by them. For example, here are the options provided by '''Private Internet Access VPN'''<ref>[https://www.privateinternetaccess.com/] Private Internet Access VPN.</ref>. This client allows to control how strong your VPN encryption is to how the VPN behaves and what it blocks. | |||
Another easy way is to disable WebRTC. | |||
WebRTC is enabled in Chrome, FireFox and Opera by default. Safari and Internet Explorer don’t have WebRTC and are thus not affected. <ref>[https://www.purevpn.com/blog/is-your-vpn-leaking-your-ip-address/] www.purevpn.com - "How to Check If Your VPN is Leaking Your IP Address" by Sheheryar Khan.</ref> | |||
=Summary= | |||
Using a VPN can certainly increase security on the internet, specially when using a free open wi-fi network. However security leakings are always possible. | |||
Another popular advantage that a VPN can provide is having an IP located in a different location than the actual location. | |||
This can be handy when travelling abroad and wanting to access certain local online service that are not allowed in other countries (ie services like Netflix or local online TVs like the UK's BBC TV iPlayer). | |||
Many companies provide for this reason a paid service, starting from ca. €5 a month (ie PureVPN, which claims itself to be the world's safest VPN). Other similar but free services might be often not secure and reliable. | |||
=References= | =References= | ||
<references/> | |||
[ | =Internal links= | ||
[https://wiki.itcollege.ee/index.php/Virtuaalsed_privaatv%C3%B5rgud Estonian version of this article] | |||
[https://wiki.itcollege.ee/index.php/OSadmin_wiki_article I800 OSadmin wiki article] | |||
=External links= | =External links= | ||
[http://openvpn.net/ OpenVPN] <br /> | [https://www.google.com/search?q=whatsmyip&oq=whatsmyip Google WhatsMyIp] <br> | ||
[https://www.privateinternetaccess.com/ Private Internet Access]<br> | |||
[http://openvpn.net/ OpenVPN] <br> | |||
[https://www.softether.org/ SoftEther] <br> | |||
[https://www.vpn.net/ LogMeIn Hamachi] <br/> | [https://www.vpn.net/ LogMeIn Hamachi] <br/> | ||
[http://www.shrew.net/ Shrew Soft] <br/> | [http://www.shrew.net/ Shrew Soft] <br/> | ||
[http://www.bbc.co.uk/iplayer UK's BBC TV iPlayer] <br> | |||
[https://www.purevpn.com PureVPN] | |||
=Author= | =Author= | ||
Author: Christian Cataldo | Author: Christian Cataldo | ||
Curriculum: Cyber Security Engineering | Curriculum: Cyber Security Engineering <br> | ||
Group: C11 | Group: C11 | ||
Date created: 9 April 2017 | Date created: 9 April 2017 <br> | ||
Last update: 6 May 2017 | |||
=Category= | |||
[[Category:Operatsioonisüsteemide administreerimine ja sidumine]] | |||
Latest revision as of 08:53, 15 May 2017
VPN (Virtual Private Network)
A VPN or Virtual Private Network enables users to send and receive data across shared or public networks as if their computing devices were directly connected to a private network. It is a method used to add security and privacy to private and public networks, like WiFi Hotspots and the Internet. VPNs are most often used by corporations to protect sensitive data.
Individual Internet users may secure their wireless transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and location. However, some Internet sites block access to known VPN technology to prevent the circumvention of their geo-restrictions.
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, virtual tunneling protocols, or traffic encryption. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely. [1]
VPN solution benefits
Some VPN advantages are:
- can be used to safely transfer data between different public networks, being independent from the data transmission protocol;
- ensure that the data is supported by encryption and authentication protocol;
- remote users can connect across a company's network;
- can be ordered from the relevant service providers, however it is important to make sure the reliability of the service. [2]
VPN Tunnel
A virtual private network is a secure solution for exchanging information between trusted parties, which are not open to public traffic. Remote users and different applications are able to connect through a private tunnel.
A VPN tunnel allows a network user to access or provide a network service that the underlying network does not support or provide directly.
One important use of a tunneling protocol is to allow a foreign protocol to run over a network that does not support that particular protocol; for example, running IPv6 over IPv4.
VPN supports two types of tunneling - voluntary and compulsory. Both types of tunneling are commonly used.
In voluntary tunneling, the VPN client manages connection setup. The client first makes a connection to the carrier network provider (an ISP in the case of Internet VPNs). Then, the VPN client application creates the tunnel to a VPN server over this live connection.
In compulsory tunneling, the carrier network provider manages VPN connection setup. When the client first makes an ordinary connection to the carrier, the carrier in turn immediately brokers a VPN connection between that client and a VPN server. From the client point of view, VPN connections are set up in just one step compared to the two-step procedure required for voluntary tunnels. [3]
Some protocols to create VPN tunnels are:
- IPsec (Internet Protocol Security) - developed by the IETF and implemented at the network layer of the OSI model (Network Layer). This is a collection of various security measures, which uses a variety of cryptographic protocols for data confidentiality, integrity, authentication and key management reasons;
- GRE (Genaral Routing Encapsulation) - originally developed by Cisco protocol which is able to encapsulate several different protocols packages;
- PPTP (Point-to-Point Tunneling Protocol) - acts as a transmission layer of the OSI model (the Data Link Layer). The data is encapsulated in the PPP (Point to Point Protocol) packets, which are encapsulated into IP packets. PPTP supports data encryption and packing and use the GRE protocol to transfer data;
- L2F (Layer2 Forwarding) - acts as a transmission layer of the OSI model. L2F does not have the encryption option and has been replaced by L2TP;
- L2TP (Layer2 Tunneling Protocol) - acts as a layer of the OSI model, data transfer, a Microsoft PPTP and Cisco L2F protocols properties. [4]
Server and Client
A VPN connection requires a VPN Server, the machine where to connect to, and a VPN Client, the computer that connects to the server.
The server is the gatekeeper at one end of the tunnel, the client at the other. The main difference between the server and the client is that it’s the client that initiates the connection with the server. A VPN client can establish a connection with just one server at a time. However, a server can accept connections from many clients.
Typically, the VPN server is a separate hardware device, most often a security appliance such as a Cisco ASA security appliance. VPN servers can also be implemented in software. [5]
VPN types
Technology
Trusted VPN transfers encrypted data through your ISP for leased lines. Privacy ensures the service promise that through rented channels provide a single customer data. Thus, depending on the data confidentiality and integrity of customer data against the service provider's discretion. One of the best known solutions is the VPN protocols entrusted MPLS (Multi-Protocol Label Switching).
Secure VPN transmits encrypted data over public networks. The data is encrypted in the device or the home network gateway, and the encryption is removed according to the destination gateway or terminal equipment. Encryption behaves destinations between the tunnel, even if a third party to connect monitors, they lack the ability to read and modify data. Some secure VPN protocols to be used are:
- IPsec with encryption;
- L2TP over IPsec encapsulated;
- SSL encryption.
Hybrid VPN, it is possible to transmit encrypted data through a leased line. Since the trusted and secure the use of a VPN are not mutually exclusive, the VPN is a hybrid of the technologies for making a parallel implementation. [6]
Usage
The two most common types of VPN use is the Remote-Access VPN and Site-to-Site VPN.
Entrance VPN (Remote Access VPN), sometimes known as a virtual private dial-up (virtual private dial-up network, VPDN), is the user and the LAN connection between organizations, which are used to connect remote users to the network. Entrance VPN uses a client-server architectures, in which a remote user VPN client acquires the rights to the entrance to a network through a network of peripheral areas of the VPN server.
Site-to-Site solution, is mounted between the networks and the static VPN connection NETWORK terminal devices are not aware of the existence of the VPN. VPN gateway is responsible for the TCP / IP packet encapsulation and encryption for. Site-to-Site VPN is divisible into two:
- intranet VPN, mainly for the larger companies and is designed to connect the company's departments, secure channel using a single network headquarters;
- extranet VPN, for customers and partners to secure the connection to companies place by linking networks. [7]
VPN solutions
Solutions that creates virtual private networks are generally divided into two categories: software and hardware. A universal solutions by software means that can be realized in different hardware assets. Building a hardware VPNs requires specialized equipment, for which, however, runs on software.
Software solutions
There are many different VPN software solutions available, which come as free, open-source or proprietary. Each of them is different from the other to some extent and are aimed at different target groups.
Standard and on-demand VPN
On-demand means that a machine connects to network then is reachable. Using same software you can either set up a connection - this means act like a server and at the other side you can connect into such machine and act as a client.
OpenVPN
OpenVPN is a free and open source solution that allows you to create secure remote access - and site-to-site virtual private type. Encryption is performed using OpenVPN SSL / TLS protocol and is distributed under the GNU GPL. OpenVPN network allows two endpoints to authenticate each other in a pre-shared cryptographic key, certificate or username and password.
The application is available in a very wide variety of operating systems, including Windows, Linux and Mac OS X. Thus, both the client and the VPN server on your network is a software stack that runs on a desired mode according to the configuration.
OpenVPN uses UDP by default and the user's request, the TCP protocol. The solution also acts as a proxy, through most of -serverite. OpenVPN is known to have written a number of third-party client programs (such as Windows OpenVPN GUI) and its support has been integrated into some routers (such as tomato, Vyatta, DD-WRT). [8]
SoftEther VPN
SoftEther VPN ("SoftEther" means "Software Ethernet") is an open-source, available under GPL license, VPN software.
It was developed by Daiyuu Nobori's Master Thesis research in the University. It is an optimum alternative to OpenVPN and Microsoft's VPN servers and can be used for any personal or commercial use for free charge.
It supports multiple VPN protocols, including OpenVPN, L2TP/IPsec and SSTP and runs on Windows, Linux, Mac, FreeBSD and Solaris.
The data is secured with AES 256-bit and RSA 4096-bit encryption. [9]
OpenVPN vs SoftEther comparison
Since SoftEther is a newer technology, it has implemented a different approach that aims not only to offer a high level of security, but also to ensure that users can enjoy extended compatibility.
Unlike OpenVPN, which only supports its own protocol, SoftEther works with SSTP, L2TP/IPsec, SSTP and more.
Speed: OpenVPN only manages to reach 100Mbps, but SoftEther is capable of going up to 900Mbps and in some cases, it can even reach higher speeds.
Since OpenVPN has been available for longer, it is supported by more platforms than SoftEther, like QNX and NetBSD.
SoftEther gets ahead in terms of speed and it also offers greater flexibility.
OpenVPN is a stable, reliable and highly secure option that hasn’t been compromised by the likes of the NSA. [10]
Hamachi
Hamachi is a section of a proprietary VPN solution, which is primarily known for its simplicity in terms of configuration and is therefore particularly popular among the fans of computer games. Hamachi manufacturer also uses the advertising slogan "Finally, a VPN that just works" (Eventually VPN that just works).
Hamachi supports VPN on-demand for networks that use certificated-based authentication, so the VPN connection is made whenever the device tries to connect to certain domains and as soon as they try to access such a server the VPN connection is initiated.
Hamachi is a centrally managed VPN system that consists of a server cluster, which is managed by the producer and the client program that is installed on the end user's computer. The client program will install a new virtual network adapter to which outgoing packets are transmitted to Hamachi program, which in turn transmits them over the Internet through a UDP connection. Incoming packets are sent Hamachi program that sends them to the virtual network card.
Each customer can either create a virtual network or join an existing one. When a client joins a network or leaving, tells the central server to all other customers to either create or remove the VPN tunnel client A. The manufacturer claims that nearly 95% of cases to establish a peer-to-peer tunnel between the two on the client computer. If it fails, a connection is established through a proxy, which is managed by the manufacturer.
Hamachi uses the IP address allocation 5.0.0.0 255.0.0.0 network mask, which is not the moment for public use and therefore eliminates potential conflicts with other computers on the Internet with the address. However, it is expected to take the address range in the near future, and in this case, may use Hamachi users conflicts arise.
Hamachi is available in two versions. The free version is designed for home users and supports a maximum of 5 computers/networs. The commercial version supports up to 256 simultaneously connected clients, but it is necessary to pay an annual fee. Hamachi is available for Windows, Mac and Linux. [11]
How to install Hamachi Client on Ubuntu via the command line:
- download:
wget http://www.vpn.net/installers/logmein-hamachi_2.1.0.165-1_amd64.deb
- install the package:
sudo dpkg -i logmein-hamachi_2.1.0.165-1_amd64.deb
Shrew Soft VPN Client
Shrew Soft VPN Client is an IPsec Remote Access VPN Client for Windows and Linux. It was originally developed to provide secure communications between mobile hosts and open source VPN gateways that utilize standards compliant software such as ipsec-tools, OpenSWAN, StrongSWAN, Libreswan, isakmpd. It now offers many of the advanced features only found in expensive commercial software and provides compatibility for VPN appliances produced by vendors such as Cisco, Juniper, Checkpoint, Fortinet, Netgear, Linksys, Zywall and many others. [12]
Linux built-in VPN
Linux OS desktop distributions have usually a built-in VPN Client and the VPN connectivity could be possible even using the CLI. For instance, the command-line VPN client VPNC is a good solution to that can quickly and easily establish a VPN connection, bypassing the GUI entirely.
Installing vpnc in Debian / Ubuntu:
# apt-get install vpnc
Windows built-in VPN
Although this property has been barely publicized, there already quite many Windows versions that had their built-in VPN client. Although Windows Vista became a built-in client with many criticism, the chances are now higher.
VPN server for the matching funds available for Windows servers, but "leaner" home user server can be set up in a desktop version. [13]
Hardware solutions
As the name suggests, it is a special independent network devices, which implement a virtual private network. It may be a single device, which customers will connect to your computer using custom software (Remote Access), but also, for example, two devices that are constantly over a public network through a tunnel in the Community and combine thus together, for example, the various branches to local area networks (site-to-site).
Hardware VPN has many advantages: higher security, load-balancing, capability to withstand a heavy load (ie, a large number of customers). Management is generally realized by means of a web interface.
Hardware VPN solutions offer a number of different manufacturers. [14]
How to ensure that your VPN is actually secure
A trusted virtual private network is a great tool for security and privacy, but if it's not configured correctly it may not be so private. A recent review of over 200 VPN apps on the Google Play store showed that most are not truly secure, using weak methods or no methods at all to ensure a user’s privacy and security.
The most technical methods to use are packet capture tools. For the Mac there is Cocoa Packet Analyzer and for Windows there is Wireshark. Those tools allow to capture packets from your network interface and show you if they are encrypted or not. [15]
How to check if your VPN is leaking private data
One simple way to see if the VPN is working is to search for what is my IP [16] on Google. At the top of the search results, Google will report back your current public Internet Protocol (IP) address. If you’re on a VPN, it should show the VPN’s IP. If it doesn’t, you know you have a problem.
To see how fully private you are visit IPLeak.net [17]. This website checks a number of ways that your IP address and other information can leak, including over WebRTC (an up-and-coming browser-based chat technology), DNS leaks, torrenting, and geolocation.
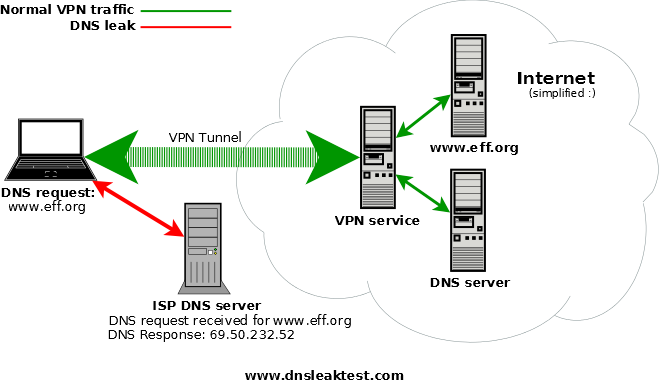
The most likely culprit in leaked information, however, is via the Domain Name System (DNS). To navigate the web, your machine requires contact with DNS servers to help translate website addresses from names to numeric IP addresses. Typically a PC automatically uses the DNS servers of your internet service provider. The problem is that if you’re using a VPN and leaking DNS through a local service provider, you can reveal enough information to point anyone spying on you in the right direction.
A way to address this issue is to permanently switch to an alternative DNS provider such as Google, OpenDNS, or Comodo Secure DNS. [18]
What can you do to prevent and improve your VPN security if you find gaps?
The first step is to look at your VPN client and the options provided by them. For example, here are the options provided by Private Internet Access VPN[19]. This client allows to control how strong your VPN encryption is to how the VPN behaves and what it blocks.
Another easy way is to disable WebRTC.
WebRTC is enabled in Chrome, FireFox and Opera by default. Safari and Internet Explorer don’t have WebRTC and are thus not affected. [20]
Summary
Using a VPN can certainly increase security on the internet, specially when using a free open wi-fi network. However security leakings are always possible.
Another popular advantage that a VPN can provide is having an IP located in a different location than the actual location.
This can be handy when travelling abroad and wanting to access certain local online service that are not allowed in other countries (ie services like Netflix or local online TVs like the UK's BBC TV iPlayer).
Many companies provide for this reason a paid service, starting from ca. €5 a month (ie PureVPN, which claims itself to be the world's safest VPN). Other similar but free services might be often not secure and reliable.
References
- ↑ [1] Microsoft Technet. "Virtual Private Networking: An Overview".
- ↑ [2] www.brighthub.com - "Understanding VPN - Advantages and Benefits Part 1" by Steve McFarlane.
- ↑ [3] www.lifewire.com - "VPN Tunnels Tutorial - Types of VPNS, Protocol, and More".
- ↑ [4] http://www.comptechdoc.org - "Tunneling protocols".
- ↑ [5] Network Administration: VPN Servers and Clients.
- ↑ [6] Networking Exchange Blog "What is an hybrid VPN"
- ↑ [7] computer.howstuffwork.com - "How VPNs Work" by Jeff Tyson & Stephanie Crawford.
- ↑ [8] OpenVPN project homepage.
- ↑ [9] SoftEther VPN homepage.
- ↑ [10] vpnpick.com - "OpenVPN and SoftEther comparison"
- ↑ [11] LogMeIn_Hamachi_UserGuide.pdf
- ↑ [12] Shrew Software homepage.
- ↑ [13] lifehacker.com - "Five Best VPN Tools" by Jason Fitzpatrick.
- ↑ [14] www.techtarget.com - "Hardware VPN".
- ↑ [15] BinaryBlogger.com.
- ↑ [16] Google whatsmyip.
- ↑ [17] IPLeak.net.
- ↑ [18] www.pcworld.com - "How to check if your VPN is leaking private data" by Ian Paul.
- ↑ [19] Private Internet Access VPN.
- ↑ [20] www.purevpn.com - "How to Check If Your VPN is Leaking Your IP Address" by Sheheryar Khan.
Internal links
Estonian version of this article
External links
Google WhatsMyIp
Private Internet Access
OpenVPN
SoftEther
LogMeIn Hamachi
Shrew Soft
UK's BBC TV iPlayer
PureVPN
Author
Author: Christian Cataldo
Curriculum: Cyber Security Engineering
Group: C11
Date created: 9 April 2017
Last update: 6 May 2017