Linux File Permissions: Difference between revisions
No edit summary |
|||
| (52 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
Author: Sheela Raj | Author : Sheela Raj | ||
Group: Cyber Security Engineering | Group : Cyber Security Engineering | ||
Created on:29-04-2016 | Created on : 29-04-2016 | ||
Last Modified on : 01-06-2016 | |||
| Line 14: | Line 16: | ||
=== Users === | === Users === | ||
In Linux, there are two types of users: ''system users'' and ''regular users''. Traditionally, system users are used to run non-interactive or background processes on a system, while regular users used for logging in and running processes interactively. When you first log in to a Linux system, you may notice that it starts out with many system users that run the services that the OS depends on--this is completely normal. [ | In Linux, there are two types of users: ''system users'' and ''regular users''. Traditionally, system users are used to run non-interactive or background processes on a system, while regular users used for logging in and running processes interactively. When you first log in to a Linux system, you may notice that it starts out with many system users that run the services that the OS depends on--this is completely normal.<ref name=LFP> [https://www.digitalocean.com/community/tutorials/an-introduction-to-linux-permissions] Linux File Permissions | ||
</ref> | |||
An easy way to view all of the users on a system is to look at the contents of the /etc/passwd file. Each line in this file contains information about a single user, starting with its ''user name'' [the name before the first <code> : </code> ]. Print the passwd file with this command: | An easy way to view all of the users on a system is to look at the contents of the /etc/passwd file. Each line in this file contains information about a single user, starting with its ''user name'' [the name before the first <code> : </code> ]. Print the passwd file with this command: | ||
| Line 24: | Line 27: | ||
Groups are collections of zero or more users. A user belongs to a default group, and can also be a member of any of the other groups on a server. | Groups are collections of zero or more users. A user belongs to a default group, and can also be a member of any of the other groups on a server. | ||
An easy way to view all the groups and their members is to look in the /etc/group file on a server. | An easy way to view all the groups and their members is to look in the /etc/group file on a server <ref name=LFP/>. The following command can be run, if you are curious about your groups: | ||
<code> cat /etc/group </code> | <code> cat /etc/group </code> | ||
| Line 63: | Line 66: | ||
In some special cases, there may be a different character here | In some special cases, there may be a different character here | ||
A hyphen '''(-)''' in the place of one of these characters indicates that the respective permission is not available for the respective class. For example, if the ''group'' triad for a file is '''r--''', the file is "'''read-only'''" to the group that is associated with the file. | A hyphen '''(-)''' in the place of one of these characters indicates that the respective permission is not available for the respective class. For example, if the ''group'' triad for a file is '''r--''', the file is "'''read-only'''" to the group that is associated with the file.<ref name=LFP/> | ||
= Checking the Permissions = | = Checking the Permissions = | ||
One can view the permissions by checking the file or directory permissions in any GUI File Manager or also by reviewing the output of the ''''' <code> ls -l </code>''''' command in the terminal and while working in the directory which contains the file or folder. [ | One can view the permissions by checking the file or directory permissions in any GUI File Manager or also by reviewing the output of the ''''' <code> ls -l </code>''''' command in the terminal and while working in the directory which contains the file or folder. <ref name=CP>[https://support.rackspace.com/how-to/checking-linux-file-permissions-with-ls/]Checking File Permissions</ref> | ||
The permission in the command line is displayed as: '''''_rwxrwxrwx 1 owner:group''''' | The permission in the command line is displayed as: '''''_rwxrwxrwx 1 owner:group''''' | ||
| Line 82: | Line 85: | ||
[[File:Checking Permissions.gif|thumb|center|alt = Checking premissions Image.| Image1:Checking Permissions [ | [[File:Checking Permissions.gif|thumb|center|alt = Checking premissions Image.| Image1:Checking Permissions [6]]] | ||
= Modifying the Permissions = | = Modifying the Permissions = | ||
| Line 94: | Line 97: | ||
Now to remove the read and write permissions from the all users group, '''''<code> chmod a-rw filename </code>''''' should be executed. | Now to remove the read and write permissions from the all users group, '''''<code> chmod a-rw filename </code>''''' should be executed. | ||
To add the above permissions again, the command: '''''<code> chmod a+rw filename </code>''''' should be used. [ | To add the above permissions again, the command: '''''<code> chmod a+rw filename </code>''''' should be used. <ref name=UP> [https://www.linux.com/learn/understanding-linux-file-permissions]Understanding File Permissions</ref> | ||
|} | |} | ||
| Line 106: | Line 109: | ||
Considering a file where the owner has read and write permissions, the group has read permissions, and all other user have no rights to the file. | Considering a file where the owner has read and write permissions, the group has read permissions, and all other user have no rights to the file. | ||
This scenario can be represented by ''''' <code> chmod 640 filename </code>''''' in binary references. | This scenario can be represented by ''''' <code> chmod 640 filename </code>''''' in binary references. <ref name=UP/> | ||
The numbers should be added to get the binary representation to set the permission. | The numbers should be added to get the binary representation to set the permission. | ||
| Line 132: | Line 135: | ||
The setuid/setgid bit can be assigned only by explicitly defining permissions. The character for the setuid/setguid bit is "'''s"'''. | The setuid/setgid bit can be assigned only by explicitly defining permissions. The character for the setuid/setguid bit is "'''s"'''. | ||
To set the setuid/setguid bit on filename.sh, the command '''''<code> chmod g+s filename.sh </code>''''' should be used | To set the setuid/setguid bit on filename.sh, the command '''''<code> chmod g+s filename.sh </code>''''' should be used <ref name=UP/>. | ||
= Sticky Bit Special Permissions = | = Sticky Bit Special Permissions = | ||
| Line 140: | Line 143: | ||
The sticky bit can only be assigned by explicitly defining permissions. The character for the sticky bit is "'''t"'''. | The sticky bit can only be assigned by explicitly defining permissions. The character for the sticky bit is "'''t"'''. | ||
To set the sticky bit on a directory, the command ''''' <code> chmod +t directoryname </code>''''' should be issued | To set the sticky bit on a directory, the command ''''' <code> chmod +t directoryname </code>''''' should be issued <ref name=UP/>. | ||
= Examples of Modes and Permissions = | = Examples of Modes and Permissions = | ||
[[File:Calculating Permissions in Binary.gif|thumb|right|alt=Calculating Permissions.| Image2: Calculating Permissions in Binary [ | [[File:Calculating Permissions in Binary.gif|thumb|right|alt=Calculating Permissions.| Image2: Calculating Permissions in Binary [6] ]] | ||
{| class="wikitable" | {| class="wikitable" | ||
| Line 196: | Line 199: | ||
|} | |} | ||
The above table illustrates the permissions and explanations of specific | The above table illustrates the permissions and explanations of specific mode. <ref name=LC> [http://linuxcommand.org/lts0070.php] Linux Commands</ref> | ||
A list of all numeric permissions from 0000 to 0777 can be found from the ''chmod'' ''commands'' referred below. [ | A list of all numeric permissions from 0000 to 0777 can be found from the ''chmod'' ''commands'' referred below. <ref name=CC> [http://www.askapache.com/security/chmod-stat.html#chmod-0-to-7777]chmod commands</ref> | ||
Image2 illustrates how the permissions are calculated in binary. [ | Image2 illustrates how the permissions are calculated in binary. <ref name=FFP> [http://www.firewall.cx/linux-knowledgebase-tutorials/introduction-to-linux/299-linux-file-folder-permissions.html]File and folder permissions</ref> | ||
=The dangers of 777 = | =The dangers of 777 = | ||
| Line 225: | Line 228: | ||
Often the Apache server is 'owned' by the '''www-data''', '''dhapache''' or '''nobody''' user accounts. These accounts have a limited amount of access to files on the server, for a very good reason. By setting your personal files and folders owned by your user account to be World-Writable, you are literally making them World Writable. Now the www-data, dhapache and nobody users that run your server, serving pages, executing php interpreters, etc.. will have full access to your user account files. | Often the Apache server is 'owned' by the '''www-data''', '''dhapache''' or '''nobody''' user accounts. These accounts have a limited amount of access to files on the server, for a very good reason. By setting your personal files and folders owned by your user account to be World-Writable, you are literally making them World Writable. Now the www-data, dhapache and nobody users that run your server, serving pages, executing php interpreters, etc.. will have full access to your user account files. | ||
This provides an avenue for someone to gain access to your files by hijacking basically any process on your server, this also includes any other users on your machine. So you should think carefully about modifying permissions on your machine. Generally its not required more than 767, so when you see 777 ask why its necessary. [ | This provides an avenue for someone to gain access to your files by hijacking basically any process on your server, this also includes any other users on your machine. So you should think carefully about modifying permissions on your machine. Generally its not required more than 767, so when you see 777 ask why its necessary. <ref name=CFP> [http://codex.wordpress.org/Changing_File_Permissions]Changing File Permissions</ref> | ||
=== The Worst Outcome === | === The Worst Outcome === | ||
The worst that can happen as a result of using 777 permissions on a folder or even a file, is that if a malicious cracker or entity is able to upload a unethical file or modify a current file to execute code, they will have complete control over your blog, including having your database information and password. | The worst that can happen as a result of using 777 permissions on a folder or even a file, is that if a malicious cracker or entity is able to upload a unethical file or modify a current file to execute code, they will have complete control over your blog, including having your database information and password.<ref name=CFP/> | ||
=Summary= | |||
Though there are many security attributes inherent in Linux based system, any dormant vulnerability can be induced by issuing local access grant to the files and directories. Proper permissions should be assigned based on the need and it should be administrated on regular basis to avoid security issues. Understanding file permissions is an easy concept, and I hope this article would help in knowing the basic of it. | |||
= | = See Also = | ||
[ | [https://en.wikipedia.org/wiki/File_system_permissions File System Permissions] | ||
==References== | |||
{{Reflist|30em}} | |||
[[Category:Operatsioonisüsteemide administreerimine ja sidumine]] | [[Category:Operatsioonisüsteemide administreerimine ja sidumine]] | ||
Latest revision as of 16:24, 16 May 2017
Author : Sheela Raj
Group : Cyber Security Engineering
Created on : 29-04-2016
Last Modified on : 01-06-2016
Genuine access permissions on files and directories are the most important part of ensuring a secured website. An important security measure for systems on which multiple users (e.g. various clients on a shared server) run their websites is to make sure that one user cannot access files in another client’s web root. Determining the correct file permissions for any specific file requires one to know what type of information contained in the file and the purpose of that information.
Linux File Permission
Linux is a multi-user OS that is based on the Unix concepts of file ownership and permissions to provide security, at the file system level.Though there are already a lot of good security features built into Linux based systems, one very important potential vulnerability can exist when local access is granted - that is file permission based issues resulting from a user not assigning the correct permissions to the files and directories.
Users
In Linux, there are two types of users: system users and regular users. Traditionally, system users are used to run non-interactive or background processes on a system, while regular users used for logging in and running processes interactively. When you first log in to a Linux system, you may notice that it starts out with many system users that run the services that the OS depends on--this is completely normal.[1]
An easy way to view all of the users on a system is to look at the contents of the /etc/passwd file. Each line in this file contains information about a single user, starting with its user name [the name before the first : ]. Print the passwd file with this command:
cat /etc/passwd
Groups:
Groups are collections of zero or more users. A user belongs to a default group, and can also be a member of any of the other groups on a server.
An easy way to view all the groups and their members is to look in the /etc/group file on a server [1]. The following command can be run, if you are curious about your groups:
cat /etc/group
Permission Classes
Each file and directory has three user based permission groups:
Owner
The Owner permissions (u) apply only the owner of the file or directory, they will not impact the actions of other users.
Group
The Group permissions (g) apply only to the group that has been assigned to the file or directory, they will not affect the actions of other users.
All users
The All Users permissions (o or a) apply to all other users on the system, this is the permission group that you want to watch the most.
Symbolic Permissions
There are sets of three characters, or triads, as they denote the permissions, in symbolic form, that each class has for a given file.
In each triad, read, write, and execute permissions are represented in the following way:
Read
The Read permission refers to a user's capability to read the contents of the file.
Indicated by "r" in the first position.
Write
The Write permissions refer to a user's capability to write or modify a file or directory.
Indicated by "w" in the second position.
Execute
The Execute permission affects a user's capability to execute a file or view the contents of a directory.
Indicated by "x" in the third position.
In some special cases, there may be a different character here
A hyphen (-) in the place of one of these characters indicates that the respective permission is not available for the respective class. For example, if the group triad for a file is r--, the file is "read-only" to the group that is associated with the file.[1]
Checking the Permissions
One can view the permissions by checking the file or directory permissions in any GUI File Manager or also by reviewing the output of the ls -l command in the terminal and while working in the directory which contains the file or folder. [2]
The permission in the command line is displayed as: _rwxrwxrwx 1 owner:group
·The first character that is marked with an underscore is the special permission flag that can vary. ·The following set of three characters "rwx" is for the owner permissions. ·The second set of three characters "rwx" is for the group permissions. ·The third set of three characters "rwx" is for the All Users permissions. ·Following that grouping since the integer/number displays the number of hard links to the file. ·The last piece is the Owner and Group assignment formatted as Owner:Group. .Image1 illustrates well about understanding how permission is assigned.
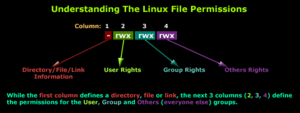
Modifying the Permissions
When in the command line, the permissions are edited by using the command chmod . One can assign the permissions explicitly or also by using a binary reference.
| Example:
Considering a file with permissions set to _rw_rw_rw, which means that the owner, group and all users have read and write permission. Now to remove the read and write permissions from the all users group, To add the above permissions again, the command: |
Setting permissions using Binary References
Binary representation of the string rwx: r = 4 w = 2 x = 1
| Example:
Considering a file where the owner has read and write permissions, the group has read permissions, and all other user have no rights to the file. This scenario can be represented by The numbers should be added to get the binary representation to set the permission. |
Advanced Permissions
The special permissions flag can be marked with any of the following:
_ - no special permissions
d - directory
l- The file or directory is a symbolic link
s - This indicated the setuid/setgid permissions. This is not set displayed in the special permission part of the permissions display, but is represented as a s in the read portion of the owner or group permissions.
t - This indicates the sticky bit permissions. This is not set displayed in the special permission part of the permissions display, but is represented as a t in the executable portion of the all users permissions
Setuid/Setgid Special Permissions
The setuid/setguid permissions are used to tell the system to run an executable as the owner with the owner\'s permissions.
The setuid/setgid bit can be assigned only by explicitly defining permissions. The character for the setuid/setguid bit is "s".
To set the setuid/setguid bit on filename.sh, the command chmod g+s filename.sh should be used [3].
Sticky Bit Special Permissions
The sticky bit can be very useful in shared environment because when it has been assigned to the permissions on a directory it sets it so only file owner can rename or delete the said file.
The sticky bit can only be assigned by explicitly defining permissions. The character for the sticky bit is "t".
To set the sticky bit on a directory, the command chmod +t directoryname should be issued [3].
Examples of Modes and Permissions
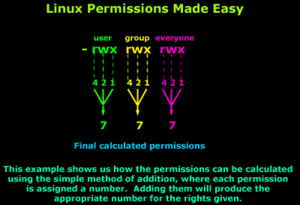
| Mode | Permissions | Explanation |
| 0477 | -r--rwxrwx | owner has read only, other and group has rwx |
| 0677 | -rw-rwxrwx | owner has rw only, other and group has rwx |
| 0444 | -r--r--r-- | all have read only |
| 0666 | -rw-rw-rw- | all have rw only |
| 0400 | -r-------- | owner has read only, group and others have no permission |
| 0600 | -rw------- | owner has rw only, group and others have no permission |
| 0470 | -r--rwx--- | owner has read only, group has rwx, others have no permission |
| 0407 | -r-----rwx | owner has read only, other has rwx, group has no permission |
| 0670 | -rw-rwx--- | owner has rw only, group has rwx, others have no permission |
| 0607 | -rw----rwx | owner has rw only, group has no permission and others have rwx |
| 0777 | rwxrwxrwx | No restrictions on permissions. Anybody may do anything. Generally not a desirable setting. |
The above table illustrates the permissions and explanations of specific mode. [4]
A list of all numeric permissions from 0000 to 0777 can be found from the chmod commands referred below. [5]
Image2 illustrates how the permissions are calculated in binary. [6]
The dangers of 777
The importance of this permission issue is how your server is configured. The username you use to FTP or SSH into your server is most likely not the username used by the server application itself to serve pages.
| 7 | 7 | 7 |
| User | Group | World |
| r+w+x | r+w+x | r+w+x |
| 4+2+1 | 4+2+1 | 4+2+1 |
Often the Apache server is 'owned' by the www-data, dhapache or nobody user accounts. These accounts have a limited amount of access to files on the server, for a very good reason. By setting your personal files and folders owned by your user account to be World-Writable, you are literally making them World Writable. Now the www-data, dhapache and nobody users that run your server, serving pages, executing php interpreters, etc.. will have full access to your user account files.
This provides an avenue for someone to gain access to your files by hijacking basically any process on your server, this also includes any other users on your machine. So you should think carefully about modifying permissions on your machine. Generally its not required more than 767, so when you see 777 ask why its necessary. [7]
The Worst Outcome
The worst that can happen as a result of using 777 permissions on a folder or even a file, is that if a malicious cracker or entity is able to upload a unethical file or modify a current file to execute code, they will have complete control over your blog, including having your database information and password.[7]
Summary
Though there are many security attributes inherent in Linux based system, any dormant vulnerability can be induced by issuing local access grant to the files and directories. Proper permissions should be assigned based on the need and it should be administrated on regular basis to avoid security issues. Understanding file permissions is an easy concept, and I hope this article would help in knowing the basic of it.