DirectAccess serveri paigaldamine ja haldamine Windows Server operatsioonisüsteemis: Difference between revisions
No edit summary |
No edit summary |
||
| (31 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
'''DirectAccess''' on uus võimalus Windows 7 (Ultimate ja Enterprise versioonid ainult) ja Windows Server 2008 R2 operatsiooni süsteemidel, mis pakub ühendust sisevõrguga kõikidele arvutitele, mis omavad DirectAccess kliendi ja asuvad interneti võrgus. Võrredes tavapärasega VPN ühendusega, kus kasutaja peab seda ise aktiveerima ja lõpetama, DirectAccess konfigureeritud sellisel moel, et ühendust luuakse automaatselt, kui arvuti saab interneti ühendust. | |||
'''DirectAccess''' on uus võimalus Windows 7 (Ultimate ja Enterprise versioonid ainult) ja Windows Server 2008 R2 operatsiooni süsteemidel. | |||
==Tehnoloogia== | |||
DirectAccess tekitab [[IPSec]] tunneli kliendilt DirectAccess serverisse ja kasutab IPv6 protokolli, et jõuda DirectAccess serverisse või teiste DirectAccess klientideni. See tehnoloogia kasutab IPv6 traffikut läbi IPv4 võrgu, et jõuda sisevõrku läbi interneti, mis endiselt baseerub IPv4 protokollil. | |||
[[File:da9.png]] | |||
==Nõudmised== | ==Nõudmised== | ||
DirectAccess vajab: | DirectAccess vajab: | ||
* Ühe või mitme DirectAccess servereid, mis töötavad Windows Server 2008 R2 peal koos kahte võrguadapteriga, millest 1 ühendust otse internetti ja teine otse sisevõrku. | * Ühe või mitme DirectAccess servereid, mis töötavad Windows Server 2008 R2 peal koos kahte võrguadapteriga, millest 1 ühendust otse internetti ja teine otse sisevõrku. | ||
* DirectAccess serveril kaks järjestiku määratud IPv4 aadressi, need peavad olema määratud adapterile, mis on ühendatud interneti | * DirectAccess serveril kaks järjestiku määratud IPv4 aadressi, need peavad olema määratud adapterile, mis on ühendatud interneti j ei tohi olla NAT! | ||
* DirectAccess klient, mis jookseb Windows7 peal (ainult Ultimate või Entreprise versioonid) | * DirectAccess klient, mis jookseb Windows7 peal (ainult Ultimate või Entreprise versioonid) | ||
* Vähemalt 1 domeeni kontroller ja DNS server, mis jookseb Windows Server 2008 SP2 või Windows 2008 R2 peal. | * Vähemalt 1 domeeni kontroller ja DNS server, mis jookseb Windows Server 2008 SP2 või Windows 2008 R2 peal. | ||
* Public key infrastructure (PKI), mis annab välja arvutile sertifikaati. | * Public key infrastructure (PKI), mis annab välja arvutile sertifikaati. | ||
==DirectAccess paigaldamine== | |||
Teie saate paigaldada, konfigureerida ja jälgida ühenduste liiklust DirectAccess managment konsooli abil, mida Teie peate installeerima spetsiaalse lisana, kui paigaldate Server Managment osa. | |||
Et paigaldada DirectAccessi võimalust Server Managmenti alt tehke järgmist: | |||
*DirectAccess serveril, vajutage Start, valige Run, trükkige sisse servermanager.msc, ja siis vajutage ENTER. | |||
*Põhiaknas Featurues Summary alt vajutage Add features. | |||
*Select Features lehel valige DirectAccess Management Console. | |||
*Add Features Wizard aknas vajutage Add Required Features. | |||
*Select Features lehel, vajutage Next. | |||
*Confirm Installation Selections lehel, vajutage Install. | |||
*On the Installation Results lehel vajutage Close. | |||
==DirectAccess haldamine== | |||
=== Konfigureerimise viisard: Client === | |||
The first Wizard in configuring DirectAccess is pretty straight forward and asks only one question: What groups of computers do you want to enable for DirectAccess? | |||
I find it most useful to create one active directory security group called “DirectAccess Enabled Computers” that can be used for actually enabling DirectAccess. You can then add Computers or even other Groups of Computers as members of this group. This allows you to manage who has DirectAccess from within Active Directory and you won’t need to revisit this wizard or modify Group Policy later. You should note that once you add a computer to this group they will need to process group policy in order to become DirectAccess enabled. This means they will need to be connected to the domain for the first time in order to come online. | |||
To get started click the Edit button in the Clients group. | |||
[[File:da7.png]] | |||
Now click the Add button and select the AD Security Group that you want to use to enable DirectAccess for it’s member computers. | |||
[[File:da8.png]] | |||
You can enter several groups here but I like to enter just the one “DirectAccess Enabled Computers” and then mange membership of that group from Active Directory. | |||
Click finish and you’re done! Keep in mind that if you already have a configuration in place then changing this setting will not automatically enable a new group for DirectAccess. The configuration will need to be Generated AND Activated, then the client computers will also need to fetch the new policy, as is the case with any other changes to the UAG configuration. If this is the first time you’re running through this configuration don’t worry about activating the configuration just yet. You have pleanty more to run through first. | |||
=== Konfigureerimise viisard: DirectAccess server === | |||
Getting through the DirectAccess Server wizard might be the most challenging becuase it’s behaviour and what it asks for is determined by some dependancy checks that the wizard does in the background. To get started, click the Edit button in the DirectAccess Server group. | |||
NOTE: At the time of this writting, Forefront UAG Update 1 and earlier has a known bug in this particular wizard that can appear when you reach the page about selecting certificates. Microsoft delevopers are aware of the issue as discussed here in the Microsoft Forefront forum but I have been told that there won’t be a fix until UAG Service Pack 1 due for release around the end of 2010. It seems to be fine the first time you go through the wizard but if you select one certificate type and then rerun the wizard and select the other type the wizard will peg the CPU at 100% on the third and any subsequent times that you run the wizard. So the moral of the story here is to get it right the first time and you’ll be fine. Otherwise you may need to wipe the entire UAG Configuration (by running configmgrutil -del) and start all over. | |||
[[File:da1.png]] | |||
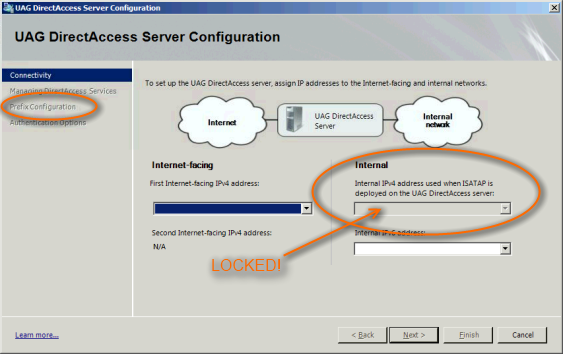
Remember, I am assuming that your internal network infrastructure is running purely IPv4. With that in mind, the first page of this wizard will sort of tell you if you have things set up right…but you have to know what you are looking for. If you notice that the dropdown list for IPv4 is disabled, then you’re missing something. It looks like this: | |||
[[File:da2.png]] | |||
This usually means the wizard was unable to find an ISATAP router and assumes you are using IPv6 on your internal network becuase, well, without ISATAP to convert IPv6 into IPv4 you would need native IPv6 for DirectAccess to work. Since we do not have IPv6 internally and we want to use ISATAP, there are two things to check in order to correct this: | |||
1.Make sure ISATAP has been removed from the DNS Global Block List (here’s how) | |||
2.Make sure you have an “A record” in DNS for “ISATAP” that points to the internal IP address of your UAG server. | |||
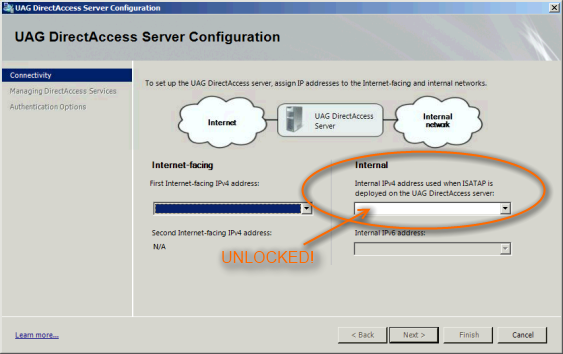
Once you have the DNS considerations for ISATAP taken care of you should see that IPv6 is now grey’d out and the IPv4 dropdown is enabled. | |||
[[File:da3.png]] | |||
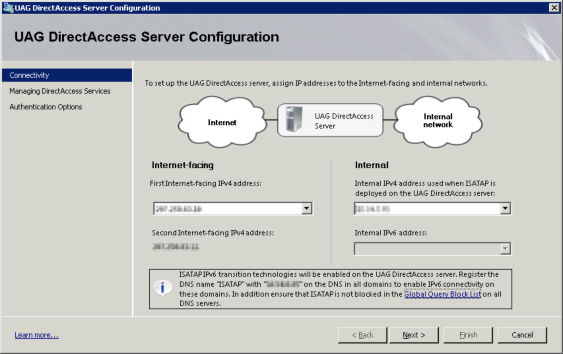
The two dropdown lists should be populated with only one option in each. In the left DDL for the Internet-facing IPv4 address select the first public IP on your server and then you should see the second address appear underneath the drop-down. In the right DDL for the Internal IPv4 address select the server’s intranet address and then the wizard should tell you that it will be enabling ISATAP and that you should create the DNS record for ISATAP. Of course that’s a little ironic being that you needed to do that beforehand. | |||
[[File:da4.png]] | |||
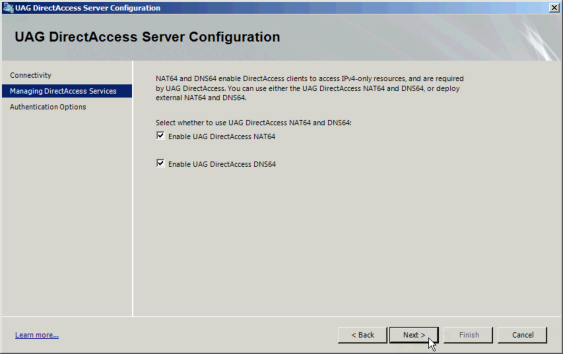
Next leave both NAT64 and DNS64 checked. If you don’t you will either need to configure your own services or be unable to connect to IPv4 targets. So, yeah, leave those checked. | |||
[[File:da5.png]] | |||
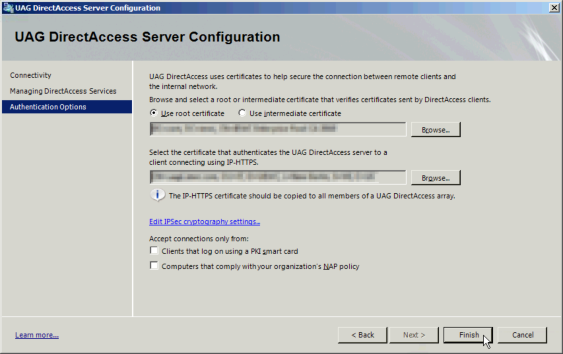
Finally, you need to select the select the certificate for the server that is issuing the certs to your enterprise. At this point you should have already generated a web certificate to be used for IP-HTTPS and imported it into the Computer account’s Personal Certificates store of the UAG server. Select both certificates and click Finish. | |||
[[File:da6.png]] | |||
It may be appropriate to point out here that IP-HTTPS, while it is the least desierable connection method due to it’s overhead, it is incredibly useful since it is the option most likely to work in “unusual” scenarios due to popular support for connecting to secure web sites through firewalls. When it comes to the configuration of the UAG server, it does proxy all IP-HTTPS trafic through a local instance of IIS. To accomplish this the UAG Wizard seems to wipe and re-write the IIS settings when activating the UAG configuration. Why is that important? Well, you should not expect to be able to use the IIS installation on the UAG server for anything other than IP-HTTPS. So don’t bother adding another site or try to bind one to a different IP or even make some subdirectories in any existing site. UAG will destroy it and it doesn’t tell you about it either. | |||
===Mõned näidis laborid Microsofti veebist:=== | |||
[http://technet.microsoft.com/en-us/edge/Video/ff710879 DirectAccess Configuration - Windows 7 Demo Screencast esimene osa viiest - videomaterjaal DirectAccess konfigureerimisest] | |||
[http://www.microsoft.com/downloads/en/details.aspx?FamilyID=8d47ed5f-d217-4d84-b698-f39360d82fac Test Lab Guide: Demonstrate DirectAccess - allalaetav DOCX fail, kust saab lugeda näidis konfiguratsiooni] | |||
==Allikad== | ==Allikad== | ||
*[http://technet.microsoft.com/en-us/library/ee649180%28WS.10%29.aspx Install DirectAccess feature] | |||
*[http://blog.concurrency.com/infrastructure/uag-directaccess-configuration-guide/ UAG DirectAccess: Configuration Guide] | |||
==Välised lingid== | ==Välised lingid== | ||
| Line 26: | Line 98: | ||
*[http://msdn.microsoft.com/en-us/library/dd358571%28PROT.13%29.aspx MS-IPHTTPS on MSDN]: includes PDF with specification. | *[http://msdn.microsoft.com/en-us/library/dd358571%28PROT.13%29.aspx MS-IPHTTPS on MSDN]: includes PDF with specification. | ||
*[http://refraction.co.uk/blog/2009/07/23/directaccess-ipv6-and-ipv4-networks/ Blogger's posting on DirectAccess] | *[http://refraction.co.uk/blog/2009/07/23/directaccess-ipv6-and-ipv4-networks/ Blogger's posting on DirectAccess] | ||
==Autor== | |||
Artur Kulikov, AK11 | |||
Latest revision as of 21:50, 1 April 2011
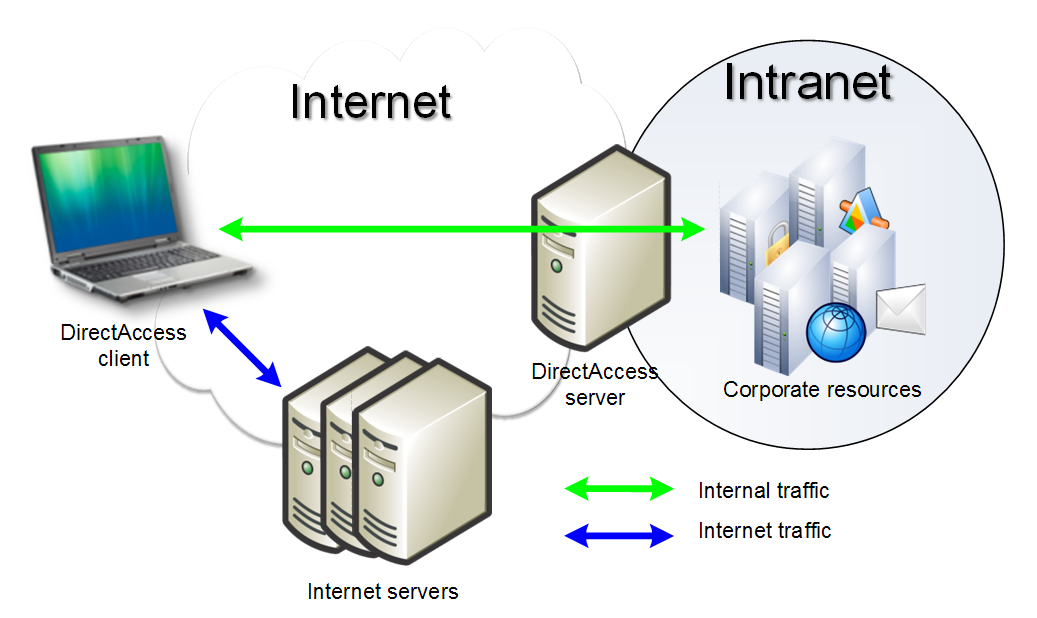
DirectAccess on uus võimalus Windows 7 (Ultimate ja Enterprise versioonid ainult) ja Windows Server 2008 R2 operatsiooni süsteemidel, mis pakub ühendust sisevõrguga kõikidele arvutitele, mis omavad DirectAccess kliendi ja asuvad interneti võrgus. Võrredes tavapärasega VPN ühendusega, kus kasutaja peab seda ise aktiveerima ja lõpetama, DirectAccess konfigureeritud sellisel moel, et ühendust luuakse automaatselt, kui arvuti saab interneti ühendust.
Tehnoloogia
DirectAccess tekitab IPSec tunneli kliendilt DirectAccess serverisse ja kasutab IPv6 protokolli, et jõuda DirectAccess serverisse või teiste DirectAccess klientideni. See tehnoloogia kasutab IPv6 traffikut läbi IPv4 võrgu, et jõuda sisevõrku läbi interneti, mis endiselt baseerub IPv4 protokollil.
Nõudmised
DirectAccess vajab:
- Ühe või mitme DirectAccess servereid, mis töötavad Windows Server 2008 R2 peal koos kahte võrguadapteriga, millest 1 ühendust otse internetti ja teine otse sisevõrku.
- DirectAccess serveril kaks järjestiku määratud IPv4 aadressi, need peavad olema määratud adapterile, mis on ühendatud interneti j ei tohi olla NAT!
- DirectAccess klient, mis jookseb Windows7 peal (ainult Ultimate või Entreprise versioonid)
- Vähemalt 1 domeeni kontroller ja DNS server, mis jookseb Windows Server 2008 SP2 või Windows 2008 R2 peal.
- Public key infrastructure (PKI), mis annab välja arvutile sertifikaati.
DirectAccess paigaldamine
Teie saate paigaldada, konfigureerida ja jälgida ühenduste liiklust DirectAccess managment konsooli abil, mida Teie peate installeerima spetsiaalse lisana, kui paigaldate Server Managment osa.
Et paigaldada DirectAccessi võimalust Server Managmenti alt tehke järgmist:
- DirectAccess serveril, vajutage Start, valige Run, trükkige sisse servermanager.msc, ja siis vajutage ENTER.
- Põhiaknas Featurues Summary alt vajutage Add features.
- Select Features lehel valige DirectAccess Management Console.
- Add Features Wizard aknas vajutage Add Required Features.
- Select Features lehel, vajutage Next.
- Confirm Installation Selections lehel, vajutage Install.
- On the Installation Results lehel vajutage Close.
DirectAccess haldamine
Konfigureerimise viisard: Client
The first Wizard in configuring DirectAccess is pretty straight forward and asks only one question: What groups of computers do you want to enable for DirectAccess?
I find it most useful to create one active directory security group called “DirectAccess Enabled Computers” that can be used for actually enabling DirectAccess. You can then add Computers or even other Groups of Computers as members of this group. This allows you to manage who has DirectAccess from within Active Directory and you won’t need to revisit this wizard or modify Group Policy later. You should note that once you add a computer to this group they will need to process group policy in order to become DirectAccess enabled. This means they will need to be connected to the domain for the first time in order to come online.
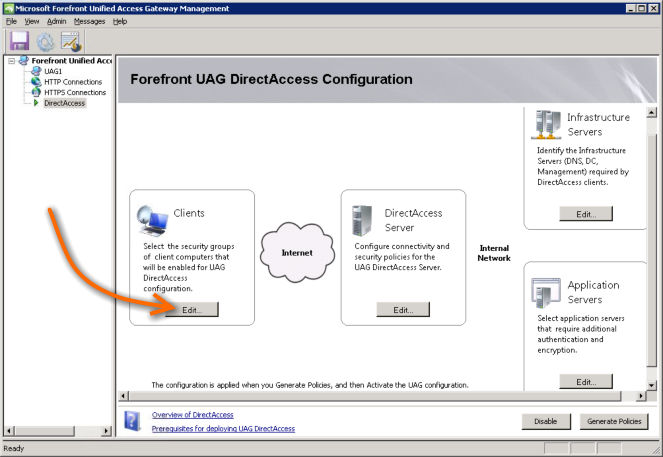
To get started click the Edit button in the Clients group.
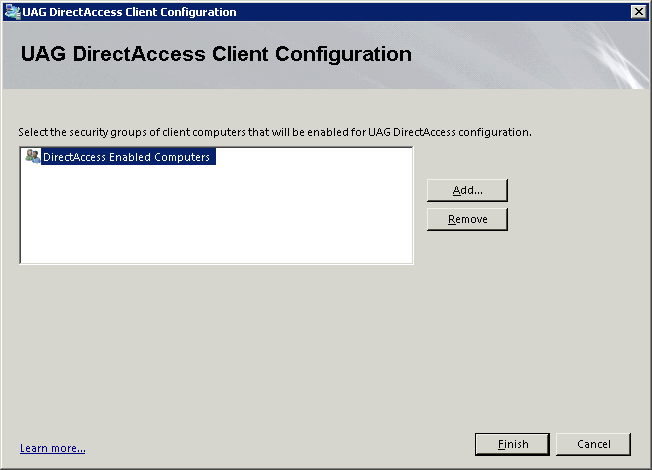
Now click the Add button and select the AD Security Group that you want to use to enable DirectAccess for it’s member computers.
You can enter several groups here but I like to enter just the one “DirectAccess Enabled Computers” and then mange membership of that group from Active Directory.
Click finish and you’re done! Keep in mind that if you already have a configuration in place then changing this setting will not automatically enable a new group for DirectAccess. The configuration will need to be Generated AND Activated, then the client computers will also need to fetch the new policy, as is the case with any other changes to the UAG configuration. If this is the first time you’re running through this configuration don’t worry about activating the configuration just yet. You have pleanty more to run through first.
Konfigureerimise viisard: DirectAccess server
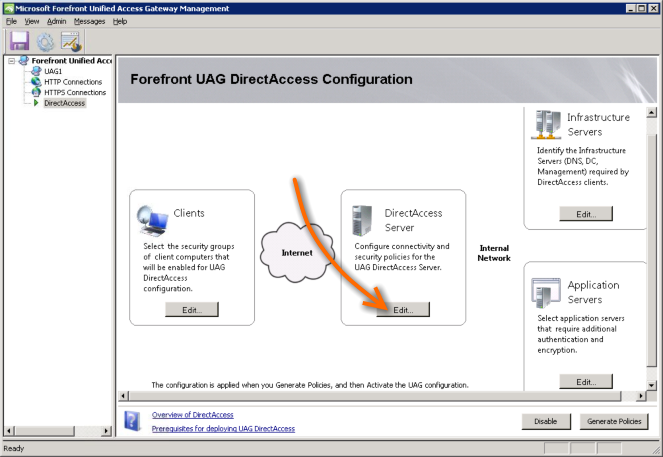
Getting through the DirectAccess Server wizard might be the most challenging becuase it’s behaviour and what it asks for is determined by some dependancy checks that the wizard does in the background. To get started, click the Edit button in the DirectAccess Server group.
NOTE: At the time of this writting, Forefront UAG Update 1 and earlier has a known bug in this particular wizard that can appear when you reach the page about selecting certificates. Microsoft delevopers are aware of the issue as discussed here in the Microsoft Forefront forum but I have been told that there won’t be a fix until UAG Service Pack 1 due for release around the end of 2010. It seems to be fine the first time you go through the wizard but if you select one certificate type and then rerun the wizard and select the other type the wizard will peg the CPU at 100% on the third and any subsequent times that you run the wizard. So the moral of the story here is to get it right the first time and you’ll be fine. Otherwise you may need to wipe the entire UAG Configuration (by running configmgrutil -del) and start all over.
Remember, I am assuming that your internal network infrastructure is running purely IPv4. With that in mind, the first page of this wizard will sort of tell you if you have things set up right…but you have to know what you are looking for. If you notice that the dropdown list for IPv4 is disabled, then you’re missing something. It looks like this:
This usually means the wizard was unable to find an ISATAP router and assumes you are using IPv6 on your internal network becuase, well, without ISATAP to convert IPv6 into IPv4 you would need native IPv6 for DirectAccess to work. Since we do not have IPv6 internally and we want to use ISATAP, there are two things to check in order to correct this:
1.Make sure ISATAP has been removed from the DNS Global Block List (here’s how) 2.Make sure you have an “A record” in DNS for “ISATAP” that points to the internal IP address of your UAG server.
Once you have the DNS considerations for ISATAP taken care of you should see that IPv6 is now grey’d out and the IPv4 dropdown is enabled.
The two dropdown lists should be populated with only one option in each. In the left DDL for the Internet-facing IPv4 address select the first public IP on your server and then you should see the second address appear underneath the drop-down. In the right DDL for the Internal IPv4 address select the server’s intranet address and then the wizard should tell you that it will be enabling ISATAP and that you should create the DNS record for ISATAP. Of course that’s a little ironic being that you needed to do that beforehand.
Next leave both NAT64 and DNS64 checked. If you don’t you will either need to configure your own services or be unable to connect to IPv4 targets. So, yeah, leave those checked.
Finally, you need to select the select the certificate for the server that is issuing the certs to your enterprise. At this point you should have already generated a web certificate to be used for IP-HTTPS and imported it into the Computer account’s Personal Certificates store of the UAG server. Select both certificates and click Finish.
It may be appropriate to point out here that IP-HTTPS, while it is the least desierable connection method due to it’s overhead, it is incredibly useful since it is the option most likely to work in “unusual” scenarios due to popular support for connecting to secure web sites through firewalls. When it comes to the configuration of the UAG server, it does proxy all IP-HTTPS trafic through a local instance of IIS. To accomplish this the UAG Wizard seems to wipe and re-write the IIS settings when activating the UAG configuration. Why is that important? Well, you should not expect to be able to use the IIS installation on the UAG server for anything other than IP-HTTPS. So don’t bother adding another site or try to bind one to a different IP or even make some subdirectories in any existing site. UAG will destroy it and it doesn’t tell you about it either.
Mõned näidis laborid Microsofti veebist:
Allikad
Välised lingid
- Microsoft's DirectAccess Getting Started page
- Microsoft's DirectAccess TechNet page
- MS-IPHTTPS on MSDN: includes PDF with specification.
- Blogger's posting on DirectAccess
Autor
Artur Kulikov, AK11