BackBox OS
BackBox Linux
What is BackBox
BackBox is an open source Ubuntu based Linux distribution. Its main purpose is to provide a desktop environment for network and systems analysis, penetration and security assessment. It is a community project and full of some of the most commonly used security and analysis tools. It runs a desktop environment based on the XFCE window manager, which makes it very easy to use.
BackBox Features
- Forensic Analysis
- Information Gathering
- Vulnerability Assessment
- Exploitation
- Privilege Escalation
- Maintaining Access
- Social Engineering
- Wireless Analysis
- Documentation and Reporting
- Reverse Engineering
- VoIP Analysis
Installing and Tuning
System requirements for the latest version (4.7):
- 32-bit or 64-bit processor
- 1024 MB of system memory (RAM)
- 10 GB of disk space for installation
- Graphics card capable of 800×600 resolution
- DVD-ROM drive or USB port (3 GB)
Since this is a free and open sourced project, BackBox Linux .iso file can be downloaded from the projects homepage. The installation and tweaking of the system follows up the usual Ubuntu/Debian guide lines. To access the security applications, use the 'Auditing' option.

After the installation, the user can start configuring and using the services available in this operating system. This can be achieved by simply left-clicking on the blue 'B' button on the upper-left corner.
To manage applications, Synaptic Package Manager or Ubuntu Software Center can be used.
Securing BackBox itself
Anyone wanting to use this OS for security purposes should start off by securing BackBox itself first. As it is an Ubuntu based Linux OS, the foundation for basic OS security should be:
- Strong passwords
- Immediate and frequent security updates
- Usage of official repositories, as much as possible
- Enable firewall (UFW is integrated but disabled by default in BB)
- Disk encryption and backups
- Common sense
One good eye should always be on user privileges as well, although BackBox does make extra sure to warn the user every time a security issue might arise with this (like warning users about consequences of using certain programs with root, or making sure the programs can only be used by users in certain groups).
There is no need for antivirus software in BlackBox, unless file sharing with other operating systems, like Windows, is active.
When using a web-browser like Mozilla, add-ons like Adguard, No-Script, BetterPrivacy should be installed.
Java and Flash should be disabled.
There is also an alternative to UFW - FirewallD, which has to be downloaded manually. It is more complex and has extra features, like Network Zone Management.
This OS also has AppArmor, an application-level firewall. It confines programs to a limited set of resources.
Disclaimer
ALL THE COMMANDS USED IN THIS ARTICLE ARE MEANT TO BE USED FOR EDUCATIONAL PURPOSES AND SHOULD NOT BE USED WITHOUT PERMISSION FROM THE TARGET!
Information Gathering
Gathering information should be the first step in any security project. Without it, it would be hard to evaluate any system.
Some of the tools used in BackBox for information gathering are:
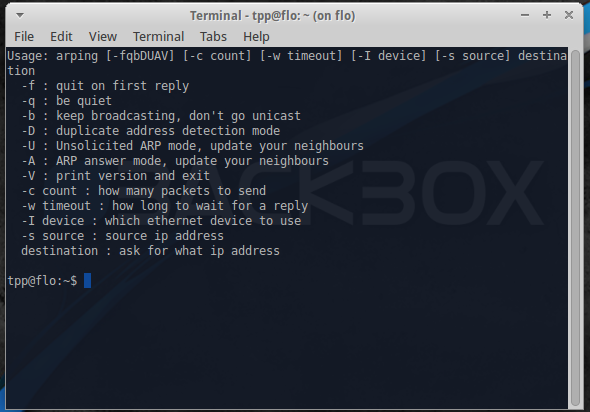
Arping
This utility sends ARP requests to the hosts on a specific subnet.
Example command:
sudo arping -I eth0 -c 3 192.168.1.1
This finds out the reachability of an IP on the local Ethernet. The '-I' identifies the intended interface, the '-c' is the count of the ARP requests taken.
Arp-scan
This is a simple but very powerful command-line tool that can be used for system discovery and fingerprinting. It assembles and sends ARP requests to specified IP addresses, displaying any responses that are received.
Example use is finding all local IP's and MAC addresses with this command:
sudo arp-scan -l
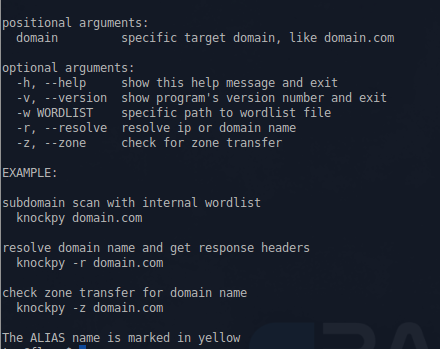
Knock
This is a Python script, written by Gianni 'guelfoweb' Amato, designed to enumerate sub-domains on a target domain through a word-list.
Example command would be this:
knockpy domain.com
This would start looking for the aforementioned site's subdomains. This is helpful if you are looking for subdomain takeover vulnerabilities.
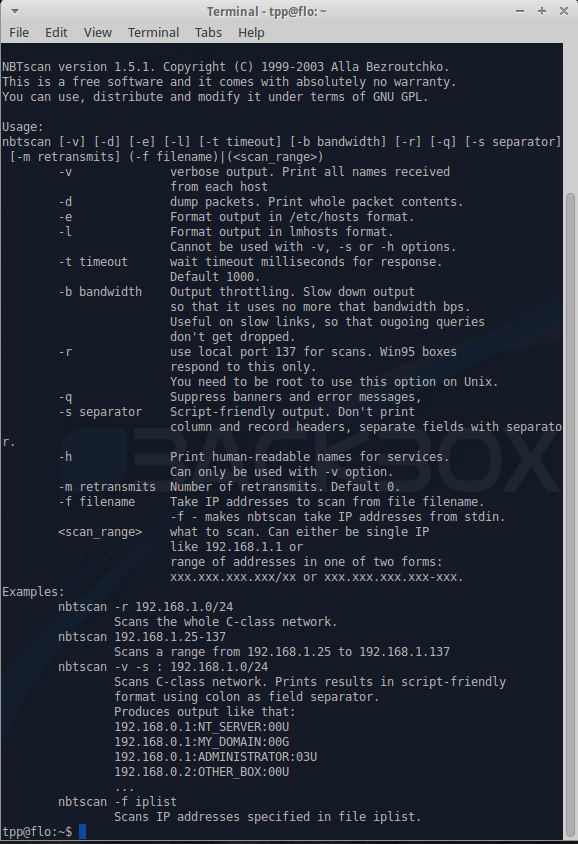
Nbtscan
This is an application to scan and get information about IP networks for NetBIOS name information.
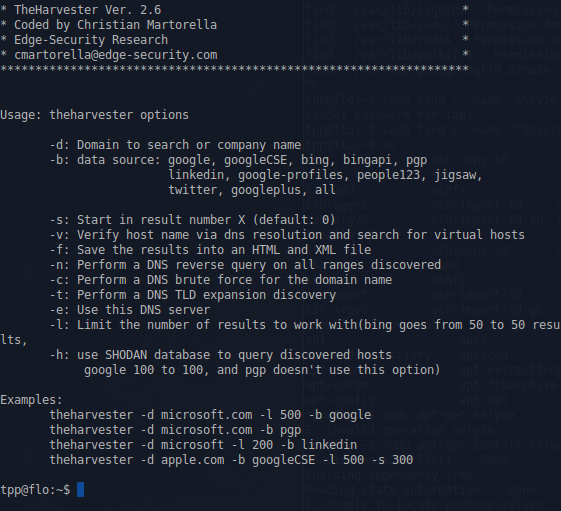
theHarvest
This is an information collector used to harvest e-mails, subdomains, hosts, and personal information about individuals.
Example command:
theharvester -d domain.com -b google
This would print all the email addresses in the site 'domain.com' that can be found by the google search engine.
Zenmap
Zenmap is a multi-platform graphical Nmap frontend and results viewer. This GUI is designed to make Nmap - Network Mapper, an open source tool for network exploration and security auditing - easy for beginners while also giving experienced Nmap users advanced features.
Zenmak can be started by searching for it from the services menu or typing it in the command line:
sudo zenmap
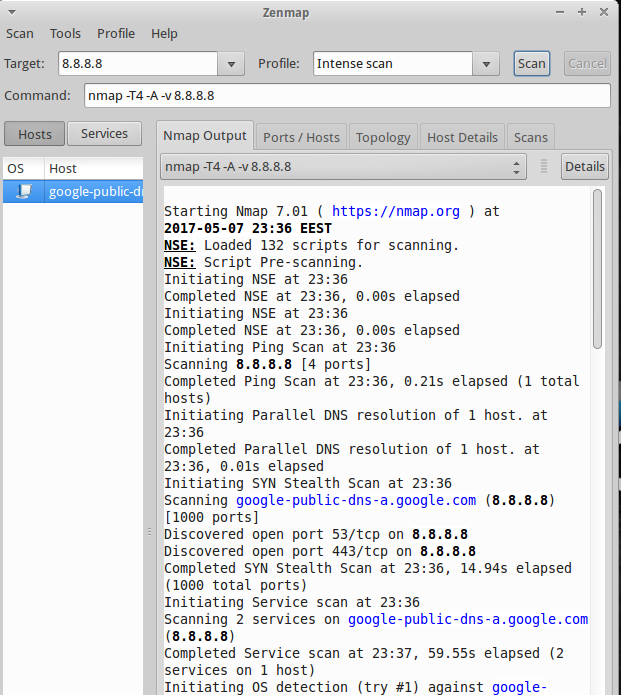
In the opened window, type the ip address of the host that you want to scan in the Target field and select the desired profile from the Profile drop-down box:
To find the scanned host’s list of open ports, port states, the services corresponding to the ports and it’s version details etc., click on the Ports/Hosts tab.
Also it will get you the host details as well. Click on the Host Details tab in the Zenmap main interface.
To scan your entire network, just enter the ip address series (ex. 192.168.1.0/24) of your network in the Target field of the Zenmap window. Click on Scan to start scanning your whole network.
The types of scans are:
- Intense scan
Quickly scans the most common TCP ports. Will also try to determine the type of OS and services running.
- Intense scan plus UDP
Same as the regular Intense scan, just that we will also scan UDP ports.
- Intense scan, all TCP ports
Normally Nmap scans a list of 1000 most common protocols, but this will leave no TCP ports (from 1 to 65535) unchecked.
- Intense scan, no ping
This scan will not ping the host and assumes it is up. Will be useful if the target has blocked ping requests.
- Ping scan
Pings the target, no port scanning.
- Quick scan
Scans only the 100 most common TCP ports.
- Quick scan plus
Quick scan with OS and version detection.
- Quick traceroute
Scan that can be used if it is nescessary to determine hosts and routers in a network scan. It does so by tracerouting and pinging all hosts defined in the target.
- Regular scan
A scan that will issue a TCP SYN scan for the most common 1000 TCP ports, using ICMP Echo request (ping) for host detection.
- Slow comprehensive scan
Command: nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY -g 53 –script “default or (discovery and safe)” <target>
Works similarly to 'Intense scan plus UDP' only with some extra features.
A lot of focus will be put into host detection, continuing even if the initial ping request fails. Three different protocols will be used to detect the hosts - TCP, UDP and SCTP. If host detection has succeeded, it will do its best to determine what OS, services and versions the host are running based on the most common TCP and UDP services. Also the scan camouflages itself as source port 53 (DNS).
Other
Other Information gathering tools in BackBox are:
- Recon-ng: This is a full-featured Web Reconnaissance framework.
- WhatWeb: This is an application that recognizes web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices.
- Creepy: This is a web application security assessment report generator.
Vulnerability Assessment
After the information is gathered, the next step should be to analyze it. That's where vulnerability Assessment tools come into play. With them, you can identify the vulnerabilities present in systems and prioritize them.
OpenVAS
This is a framework composed of several services and tools to deliver a comprehensive, powerful vulnerability scanning management solution.
To start off, a new admin account user should be created:
openvasmd --user=admin --new-password=new_password
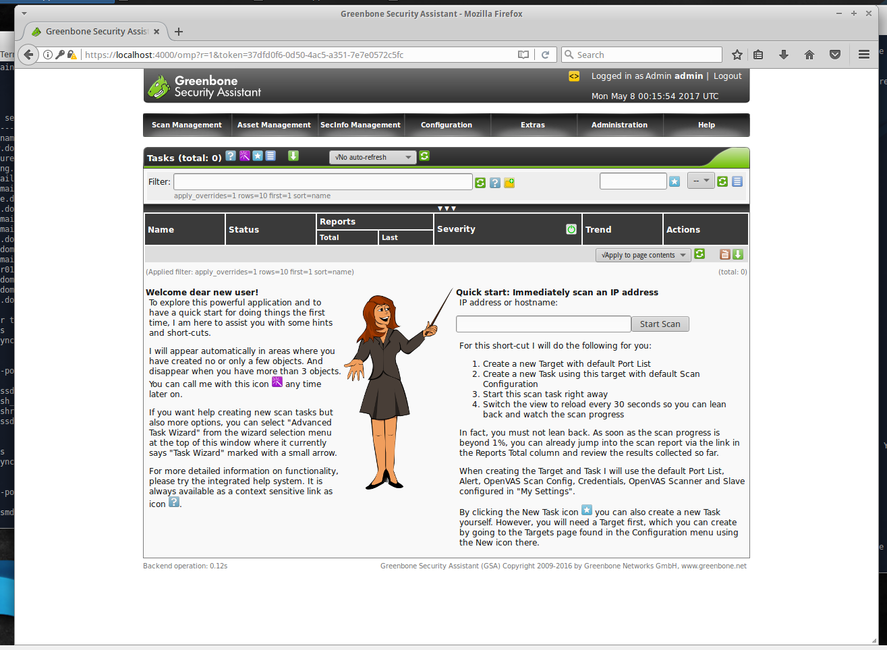
To run OpenVAS, simply choose 'OpenVAS GSA' on the menu list or go to your localhost with the port given to OpenVAS (default is 9392).
You will be promted with a login screen (Accept the self-signed SSL certificate). From there, enter the details of the user you created above and the OpenVAS web interface will open:
In the opened window, create a new task and fill in the information required - type in either the name or the IP of the domain you want to target for the scan. Then click start. Once it has finished, a report will be created. You can better analyze it by exporting it to different main popular file formats such as .pdf, .txt or .html.
OpenVAS will have grouped the possible vulnerabilities into high-, medium-, low- and log-level (information). These reports are not false proof but they help with simplifying the security assessment.
Nikto
This is an open-sourced web server scanner. It performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software.
Example commands:
nikto -h 10.0.2.15
This scans the target host with the ip '10.0.2.15'.
nikto -T x 6 -h http://site.com
This performs only a specific type of check against the target. In this case, a denial-of-service check. The types (and more) are written in the man file of nikto.
nikto -Display V -o results.txt -Format txt -Tuning 4 -h 10.0.2.15
This performs an injection test and saves the result as a plain text file while also displaying a Verbose output in the terminal.
Skipfsh
This is an active web application security reconnaissance tool. It prepares an interactive sitemap for a targeted site by undertaking a recursive crawl and dictionary-based probes.
Example command:
Skipfish –o /user/desktop http://targetwebsite.com
This scnas the target website and creates an output file on the location specified by '-o'.
To get a list of which tests Skipfish does, visit the Google Code Archive Wiki.
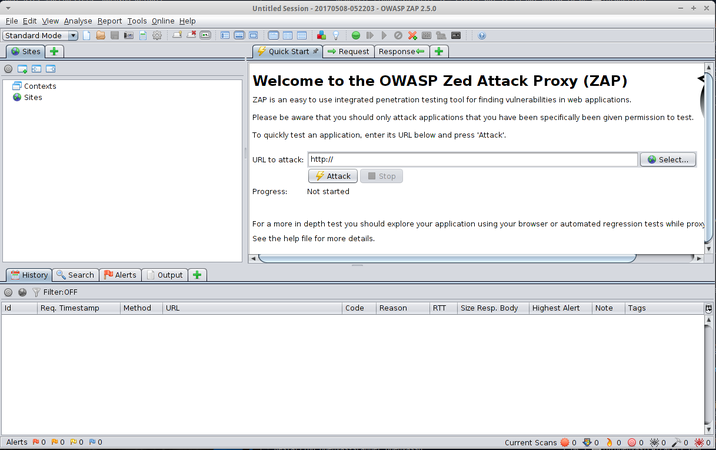
ZAP
OWASP Zed Attack Proxy tool is one of the most popular web application vulnerability finders. The main features of this tool are:
- Proxy intercepting - Configuring your browser so that it sends all the requests and responses through ZAP. The responses and requests can also be intercepted and changed.
- Active scanners - Performs wide range of scans on the application.
- Passive scanners - Examines requests and responses and sometimes detects problems from doing this. It is 'safe' to use and it runs all the time.
- Spider - Crawls the application to find links that are usually hidden.
- Report Generation - Generates reports of the issues found and directs to helpful pages from where you can learn how to solve them.
- Brute Force - Using OWASP Dirbuster Tool, this feature can find files even if there are no links to them.
- Fuzzing - For finding more subtle vulnerabilities that the automated scanners cannot usually find (using fuzzdb and OWASP JBroFuzz)
- Extensibility - Adding additional functionalities to ZAP (code.google.com/p/zap-extensions)
To use it, type in the website you want to test on the 'URL attack' bar and press 'attack':
Other
- RIPS: This is a static source code analyzer for finding vulnerabilities in PHP web applications.
- Cvechecker: The main purpose of this tool is to automatize security check by generating reports about possible vulnerabilities in your system by comparing the result with the information in its common vulnerability environment (CVE) database.
Exploitation
This is the process of where the weakness found in the system is penetrated. This is achieved by using exploit, an automated script designed to attack the target system.
Sqlmap
This is an automated tool to detect SQL flaws. SQL-Injection is usually the most common forms of attacks and usually very effective in getting data from the target.
Example commands:
sqlmap -u http://www.examplesite.com --dbs
This command tries to find databases in the specified site.
sqlmap -u ”http://www.examplesite.com" --cookie="security=low; PHPSESSID=l0ng4m0un10fnumb3rs4ndl3tt3rs" --dbs
This command tries to find databases from the specific site while keeping the session active using the mentioned cookie.
BeEF
Short for The Browser Exploitation Framework, it is a penetration testing tool that focuses on the web browser. It allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors.
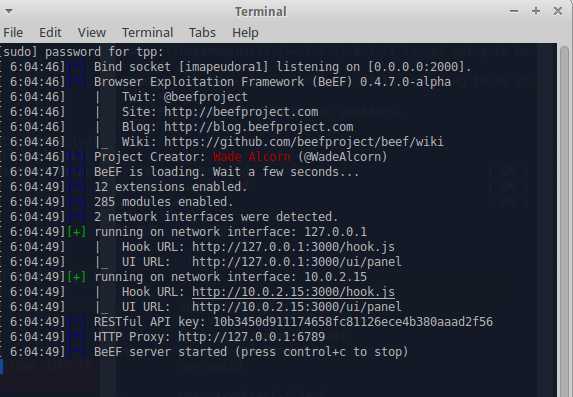
BeEF can be started from the services > auditing > exploitation menu
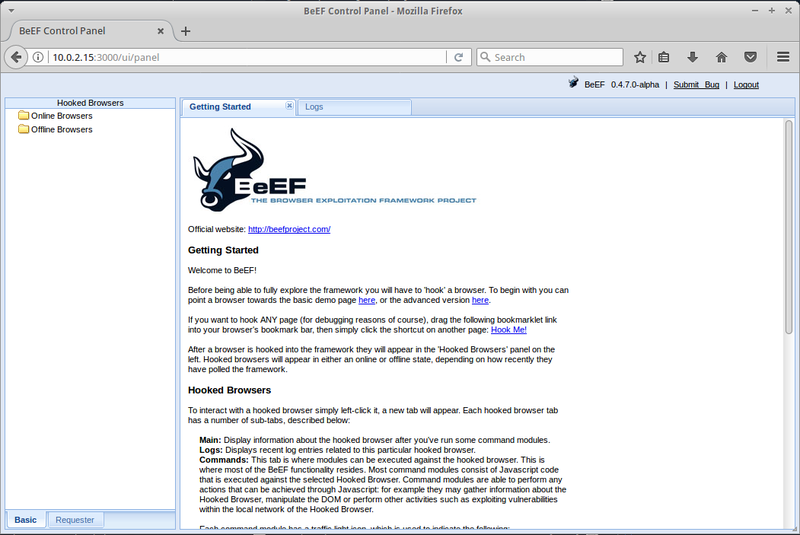
You need to click on one of the UI URL-s, which will open the BeEF login page on your browser.
Type in the default username and password (beef & beef). This will open the startup page, where you can get the overview of the tool.
You can test this program out by running an apache server on your BackBox and creating a a simple script to hook a the intended website with BeEf. The result of this would make information about the browser used available to the BeEF user, like the browser components, the running scripts and hardware information. On the 'commands' tab in the BeEF GUI (after you chose the active IP address from the left menu), you can extract even more data and manipulate the ongoing browser session. For example, you can redirect the intended URL to another site.
Armitage
This is the graphical frontend of the Metasploit Framework. It is a scriptable red team collaboration tool. It has a server component to allow a team of hackers to share their accesses to compromised hosts.
To start it, type 'armitage' in your terminal. This will open up a new window:
Click connect and if the tool asks you if you want to start Metasploit RPC server, click 'yes'. This will open the Armitage GUI:
From this, you can create custom attacks against a host. For example, you can test out yous skills on a virtual machine maintained by the Metasploit project team.
Fimap
This is a python tool which can find, prepare, audit and exploit bugs in webapps.
Example command:
sudo fimap -u "http://IpOfWebApp/index.php"
Others
- This is a useful auditing tool that contains a lot of exploits and a development environment to modify or create them.
- Htexploit: This is a useful tool to exploit the .htaccess files
- Joomscan: This is a tool that detects file inclusion, SQL injection, and command execution vulnerabilities of a targeted website that uses Joomla.
- W3af: This is a GUI-based web application attack and audit framework to fnd and exploit the vulnerabilities detected.
- Wpscan: This is a BackBox WordPress vulnerability scanner.
Privilege Escalation
John
This (also known as John the Ripper) is a password cracking software tool.
Xhydra
This is a parallelized login cracker that can attack protocols such as TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, LDAP, SMB, SMBNT, MS-SQL, MySQL, REXEC, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, Cisco auth, Cisco enable, and Cisco AAA by using the Telnet module.
Ettercap
This is a comprehensive suite for man-in-the-middle attacks. It has a user-friendly GUI interface and supports passive and active dissection of the amount of protocols.
Tcpdump
A command line packet sniffer that prints out a description of the contents of packets on a network interface that match the boolean expression.
Command to capture data from a certain interface:
sudo tcpdump -i eth0
Commant that prints out all packets arriving or departing from host PC1:
sudo tcpdump host PC1
Command that prints all IP packets between PC1 and not PC2:
sudo tcpdump host PC1 and not PC2
Wireshark
Formerly known as Etheral, it is the world's foremost network protocol analyzer.
To start capturing packets with your user, first you need to make sure that your user belongs to the usergroup named 'wireshark'. To be sure of that, use this command:
grep 'wireshark' /etc/group
If your username does not appear in the following output, it is not part of the group. To add your user to the group, use the following command:
sudo usermod -a -G wireshark yourusername
Now you can oped the Wireshark GUI, choose the network interface that is functional and start capturing and analyzing packets.
Tshark
A terminal oriented version of Wireshark. For example, to start off, you would want to know the available interfaces you can use with the command:
sudo tshark -D
An example of capturing network data with tshark:
tshark -eth0 -c 100 -w log.pcap
This will capture 100 network packets and save them into a file called log.pcap.
With the following example, we extract data from any HTTP request. The '-Y' is used to request filters, '-T' is used to specify the extract process and the '-e' is used to identify the wanted fields:
tshark -i eth0 -Y HTTP.request -T fields -e http.host -e http.user_agent
This command basically prints out the same output as Wireshark GUI:
tshark -r ~/dhcp.pcap -V frame.number == 1
Other
- Dictstat: This is a password profling tool.
- Maskgen: This is an analyzer for output fle produced by DictGen to generate optimal password mask collection for input to the Hashcat password cracker.
- Policygen: This tool helps to generate passwords to be compliant for many policies.
- Rulegen: This implements password analysis and rule generation for the Hashcat password cracker.
- Hashcat: This is incredibly the fastest CPU-based password recovery tool.
- Chntpw: This is a utility used for resetting or blanking local passwords in Wintel systems.
- Crunch: This is a wordlist generator where you can specify a standard character set.
- Fcrackzip: This is a fast password cracker partly written in assembler.
- Ophcrack: This is a Windows password cracker based on rainbow tables.
- Pdfcrack: This is a tool for recovering passwords and content from PDF fles.
- Truecrack: This is a brute-force password cracker for TrueCrypt (Copyright) volume fles.
- Fang: This is a multiservice threaded MD5 cracker.
- Medusa: This is a speedy, massively parallel, modular, login brute-force attacker, supporting many protocols.
- Driftnet: This is an application that listens to network traffc and picks out images from the TCP streams it observes.
- Dsniff: This is a network traffc sniffer that analyzes and parses different application protocols by extracting the relevant information.
- Ngrep: This (also known as network grep) is a network packet analyzer.
- Sslsniff: This is an SSL traffc sniffer.
- Sslstrip: This is a sniffer against secure socket layer protocol.
- arpspoof: This tool redirects packets from a target host (or all hosts) on the LAN intended for another host on the LAN by forging ARP replies.
Documentation and Reporting
Dradis
This is an open source information sharing framework especially designed for security assessments.
MagicTree
This is a penetration test productivity tool. This is designed to allow easy and straightforward data consolidation, querying, external command execution, and report generation.
Social Engineering
Honeyd
This is a small daemon that creates virtual hosts on a network.
Thpot
This is a tiny honeypot to set up simple and fake services.
SET
This (also known as Social-Engineer Toolkit) is designed to perform attacks against human interaction.
BeEF
This is a penetration testing tool that focuses on web browsers.
Websploit
This is used to scan and analyze remote systems in order to fnd various types of vulnerabilities.
Maintaining Access
Iodine
This is a free (ISC licensed) tunnel application to forward IPv4 traffc through DNS servers.
Ptunnel
This is an application that allows you to reliably tunnel TCP connections to a remote host using ICMP echo request and reply packets, commonly known as ping requests and replies
Weevely
This is a stealth PHP web shell that simulates a telnet-like connection
Reverse Engineering
==== Bokken ==== This is a GUI for the Pyew and Radare projects, so it offers almost all the same features that Pyew has and some features of Radare as well. It's intended to be a basic disassembler, mainly to analyze malware and vulnerabilities.
Dissy
This is a graphical frontend to the objdump disassembler.
Flasm
This is a command-line assembler/disassembler of Flash ActionScript bytecode.
Ghex
This is a simple binary GUI hex editor.
Nasm
This is a network wide assembler tool.
Ndisasm
This is a Netwide Disassembler, an 80 x 86 binary fle disassembler.
Wireless Analysis
Aircrack-ng
This is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs.
Mdk3
This is a proof-of-concept tool to exploit common IEEE 802.11 protocol weaknesses.
Pyrit
This is an application GPGPU-driven WPA/WPA2-PSK key cracker.
Reaver
This is an application to perform brute-force attacks against Wi-Fi Protected Setup (WPS)
Wifte
This is an automated wireless auditing tool.
Wirouterkeyrec
This is a tool to recover the default WPA passphrases of supported router models.
Kismet
This is an 802.11 layer2 wireless network identifer and passive data package collector
Other Useful Features
Anonymous mode
This feature allows the use of Tor as an integrated feature, so the users are guaranteed anonymity when they surf the web.
To achieve this, push the blue button on the upper left corner, search 'tor' and then choose 'tor start' (or use the terminal command 'sudo service tor start'). After this, start the anonymous application, located at anonymous > anonymous start (or run terminal command 'anonymous start'). When this is done, you need to configure (with admin privileges) your /etc/tor/torrc file and add the following to it:
VirtualAddrNetwork 10.192.0.0/10 AutomapHostsOnResolve 1 TransPort 9040 DNSPort 53
After this, restart the tor service:
sudo service tor restart
Then start the anonymous application again. In the opened terminal window, the application will let you know that it has stopped the service network-manager, killed certain processes to prevent leaks and changed your MAC address (anonymous cannot change the MAC address in a virtual machine). Then it will ask weather the local hostname should be changed and if traffic should be transparently routed through tor. After this, you can check your settings with the command:
anonymous status
You can check weather your tor service is operable by going to check.torproject.org. You can also check weather your IP address has changed by going to whatismyipaddress website.
RAM wiping
BackBox also offers it's users the option to wipe the computer's RAM at shutdown/reboot. Simply search for 'RAM Wiping' on the services menu and turn it on. Pulling the PC's cord usually does the trick, but this feature makes extra sure that no data can be recovered.
Sipcrack
This is a set of utilities to perform sniffng and cracking of SIP protocols.
References
BackBox Script for Anonymous Internet Navigation
Using tshark to watch and inspect network-traffic
Tshark tutorial and filter examples
Zenmap: A GUI Frontend For Nmap Network Scanning Tool
INSTALLATION INSTRUCTIONS FOR OPENVAS-MANAGER
OWASP Zed Attack Proxy Project