Ipkungfu Tulemüür: Difference between revisions
No edit summary |
|||
| (8 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
=Sissejuhatus= | =Sissejuhatus= | ||
Artikli eesmärgiks on tutvustada ipkungfu tulemüüri, anda ülevaade rakenduse paigaldamisest, konfigureerimisest | Artikli eesmärgiks on tutvustada ipkungfu tulemüüri, anda ülevaade rakenduse paigaldamisest, konfigureerimisest ning haldamisest. | ||
=Eeldused= | =Eeldused= | ||
Artikli koostamisel on testimiseks kasutatud Ubuntu v.12.04 LTS | Artikli koostamisel on testimiseks kasutatud Ubuntu v.12.04 LTS tarkvara. | ||
=Mis on | =Mis on Ipkungfu= | ||
Tegemist on iptables[http://linux.die.net/man/8/iptables] baasil loodud, kuid lihtsustatud Linuxi tulemüüriga mis hõlbustab võrguliikluse administreerimist. Rakendus töötab iptables ja sysctl baasil. Võib öelda, et tegemist on iptables liidesega mis on omakorda kerneli tulemüürimooduli Netfilter'i kasutajaliides. Tänu lihtsale menüüle sobib rakendus nii algajale kui eksperdile. | Tegemist on iptables[http://linux.die.net/man/8/iptables] baasil loodud, kuid lihtsustatud Linuxi tulemüüriga mis hõlbustab võrguliikluse administreerimist. Rakendus töötab iptables ja sysctl baasil. Võib öelda, et tegemist on iptables liidesega mis on omakorda kerneli tulemüürimooduli Netfilter'i kasutajaliides. Tänu lihtsale menüüle sobib rakendus nii algajale kui eksperdile. | ||
Toote trumpideks peetakse: [ | Toote trumpideks peetakse: [http://www.adercon.com/ac/node/93] | ||
*Turvalisust | *Turvalisust | ||
*Lihtsat hallatavust | *Lihtsat hallatavust | ||
| Line 13: | Line 13: | ||
Tänu Linuxi kerneli võimekusele leiab tarkvara laialdast rakendust ning toetab [ | Tänu Linuxi kerneli võimekusele leiab tarkvara laialdast rakendust ning toetab [http://www.adercon.com/ac/node/93] | ||
*Võrguühenduse jagamist | *Võrguühenduse jagamist | ||
*Virtualhoste | *Virtualhoste | ||
| Line 27: | Line 27: | ||
= | =Paigaldamine= | ||
Tulemüür töötab iptables ja sysctl baasil. Võib öelda, et tegemist on iptables liidesega mis on kerneli tulemüürimooduli Netfilter'i kasutajaliides. Konfiguratsiooni failid asuvad kaustas /etc/ipkungfu (lisa conf fail?) mida on võimalik vastavalt soovile muuta.[http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html] | Tulemüür töötab iptables ja sysctl baasil. Võib öelda, et tegemist on iptables liidesega mis on kerneli tulemüürimooduli Netfilter'i kasutajaliides. Konfiguratsiooni failid asuvad kaustas /etc/ipkungfu (lisa conf fail?) mida on võimalik vastavalt soovile muuta.[http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html] | ||
| Line 43: | Line 43: | ||
ipkungfu -d | ipkungfu -d | ||
= | =Seadistamine= | ||
Konfiguratsiooni failid asuvad kaustas /etc/ipkungfu mida on võimalik vastavalt soovile muuta.[http://www.adercon.com/ac/node/93] | Konfiguratsiooni failid asuvad kaustas /etc/ipkungfu mida on võimalik vastavalt soovile muuta.[http://www.adercon.com/ac/node/93] | ||
*Ava fail /etc/ipkungfu/ipkungfu.conf [ | *Ava fail /etc/ipkungfu/ipkungfu.conf [https://wiki.itcollege.ee/images/a/ac/Ipkungfu.conf.pdf] | ||
nano /etc/ipkungfu/ipkungfu.conf | nano /etc/ipkungfu/ipkungfu.conf | ||
Muudan faili vastavalt soovile. Testis tegin järgmised muudatused failis: | *Muudan faili vastavalt soovile. Testis tegin järgmised muudatused failis:[https://wiki.itcollege.ee/images/f/f7/Ipkungfu.conf_changed.pdf] | ||
# Set the path to ipkungfu's runtime error log. | # Set the path to ipkungfu's runtime error log. | ||
# Default: /var/log/ipkungfu.log | # Default: /var/log/ipkungfu.log | ||
| Line 90: | Line 89: | ||
KNOWN_BAD="REJECT" | KNOWN_BAD="REJECT" | ||
*Keelan portide | *Keelan portide skaneeringu: | ||
# What to do with port scans | # What to do with port scans | ||
#PORT_SCAN="REJECT" | #PORT_SCAN="REJECT" | ||
| Line 96: | Line 95: | ||
*Tulemüüri automaatseks käivitamiseks ava järgnev fail ning muuda seadistust: | *Tulemüüri automaatseks käivitamiseks ava järgnev fail ning muuda seadistust: [http://www.adercon.com/ac/node/93] | ||
nano /etc/default/ipkungfu | nano /etc/default/ipkungfu | ||
| Line 157: | Line 156: | ||
*Konfiguratsioonifailide asukohad [http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html] | *Konfiguratsioonifailide asukohad: [http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html] | ||
**/etc/ipkungfu/ipkungfu.conf | **/etc/ipkungfu/ipkungfu.conf | ||
**/etc/ipkungfu/advanced.conf | **/etc/ipkungfu/advanced.conf | ||
| Line 167: | Line 166: | ||
**/etc/ipkungfu/services.conf | **/etc/ipkungfu/services.conf | ||
**/usr/sbin/ipkungfu | **/usr/sbin/ipkungfu | ||
*ReadMe ja FAQ dokumendid leiab kaustast: [http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html] | |||
**/usr/share/doc/ipkungfu | |||
**/usr/share/doc/ipkungfu/AUTHORS | **/usr/share/doc/ipkungfu/AUTHORS | ||
**/usr/share/doc/ipkungfu/README | **/usr/share/doc/ipkungfu/README | ||
| Line 174: | Line 177: | ||
*Lisainfo [http://manpages.ubuntu.com/manpages/trusty/man8/iptables.8.html] | |||
*Lisainfo [ | |||
There are several configuration files, each one corresponding to a specific | There are several configuration files, each one corresponding to a specific | ||
function or set of functions. | function or set of functions. | ||
| Line 186: | Line 183: | ||
all of these files. They are located in /etc/ipkungfu/ and are: | all of these files. They are located in /etc/ipkungfu/ and are: | ||
accept_hosts.conf : IP addresses of hosts or nets to always ACCEPT and | |||
optionally the ports they are allowed to access | |||
advanced.conf : Configuration settings for advanced users. | |||
custom.conf : Here you will find sample rules several sample rules already | |||
predefined. This is where you would add any custom rules you want applied | |||
to your firewall. This file is parsed first, before any other rules are | |||
added by ipkungfu, to ensure that none of ipkungfu's rules override the | |||
rules in this file. | |||
deny_hosts.conf : You can list IP addresses/subnets:ports:protocols you wish | |||
to block completely. This file is parsed before accept_hosts.conf and takes | |||
precedence over it. | |||
ipkungfu.conf : This is the main configuration file. Edit this file, if | |||
nothing else. For most people, this is the only file that needs to be | |||
edited to set up a decent firewall, with or without Internet connection | |||
sharing. | |||
WARNING: ALLOW_TCP_IN and ALLOW_UDP_IN are now deprecated and mantained only | |||
for backward compatability. Now use services.conf. | |||
log.conf : This file specifies what the firewall will log and the rate at | |||
which it is logged. By default, nearly all dropped packets are logged. | |||
To turn logging off on a particular item, change the 1 (log) to a | |||
0 (don't log). The default location of the log on most systems is | |||
/var/log/syslog. Consult your syslogd configuration to find out where | |||
kernel logs are stored. | |||
redirect.conf : Use this file to specify where certain traffic should be | |||
routed on the SAME machine. If you want to redirect ports that come in on | |||
one port, and should go to another, set them up here. There is a single | |||
entry here that is commented out by default- tcp:443:10000 which | |||
redirects incoming https traffic on port 443 to webmin on port 10000. | |||
Please see the file for more information. | |||
vhosts.conf : If you have virtual hosts, (servers on machines behind your | |||
gateway), define the routing rules here. This file makes it possible to | |||
have servers behind the firewall, with private IP addresses, accessible | |||
from the Internet. | |||
pre.conf : This is parsed and executed as a bash script prior to running | |||
ipkungfu. | |||
post.conf : This is parsed and executed as a bash script after ipkungfu | |||
has completed execution. | |||
services.conf : Here you keep all of your rules previously defined in | |||
ipkungfu.conf as ALLOW_TCP_IN and ALLOW_UDP_IN, plus more. Edit the file, | |||
it's self explanatory. | |||
Most people, especially those with very simple configurations, will only | |||
need to edit /etc/ipkungfu/ipkungfu.conf if anything at all. As of 0.5.1 | |||
ipkungfu does a lot of detecting and guessing for the main configuration | |||
parameters unless you specify their values in ipkungfu.conf. This should | |||
work for most people. To go over the list of variables as ipkungfu | |||
knows them, run ipkungfu --show-vars. If anything looks wrong, edit the | |||
appropriate configuration file accordingly. | |||
A "#" is a comment. When a line begins with #, the whole line is ignored. If | |||
you want enable an option in a configuration file that is commented out, | |||
simply remove the leading #. If you wish to remove an option, place a # | |||
in front of that line. | |||
Note that anytime you edit a configuration file, you MUST rerun the ipkungfu | |||
as outlined below in order for changes to take effect. | |||
ipkungfu | |||
Most problems can be resolved by checking your settings in your configuration | |||
files. | |||
Many users overlook certain settings, so you may want to double-check them to | |||
be sure. | |||
Remember to run ipkungfu again (/usr/local/sbin/ipkungfu) after making any | |||
changes to the configuration files (located in /etc/ipkungfu/). | |||
Please see the FAQ for more troubleshooting issues and resolutions. | |||
=Testimine= | =Testimine= | ||
*Ühenduste testimiseks kasutasin ShieldUP-i[https://www.grc.com/x/ne.dll?bh0bkyd2] | *Ühenduste testimiseks kasutasin ShieldUP-i[https://www.grc.com/x/ne.dll?bh0bkyd2] | ||
[[File:ExposureTest.jpg|800px|]] | |||
=Kokkuvõte= | =Kokkuvõte= | ||
Ipkungfu on linuxi tulemüür mille konfigureerimine käib tabelite baasil, mis | Ipkungfu on linuxi tulemüür mille konfigureerimine käib tabelite baasil, mis sisaldavad endas pakettide filtreerimiseks ning suunamiseks vajalike reegleid. Seadistamine võttis vähe aega ning oli arusaadav. | ||
=Kasutatud kirjandus= | =Kasutatud kirjandus= | ||
*http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html | *http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html | ||
*http://teqnix.blogspot.com/2006/06/ipkungfu-kicks-firestarter-out-of-my.html | *http://teqnix.blogspot.com/2006/06/ipkungfu-kicks-firestarter-out-of-my.html | ||
*http://www.adercon.com/ac/node/93 | *http://www.adercon.com/ac/node/93 | ||
*http://www.linuxkungfu.org/ | *http://www.linuxkungfu.org/ | ||
*http://manpages.ubuntu.com/manpages/trusty/man8/iptables.8.html | *http://manpages.ubuntu.com/manpages/trusty/man8/iptables.8.html | ||
Latest revision as of 12:59, 22 May 2015
Sissejuhatus
Artikli eesmärgiks on tutvustada ipkungfu tulemüüri, anda ülevaade rakenduse paigaldamisest, konfigureerimisest ning haldamisest.
Eeldused
Artikli koostamisel on testimiseks kasutatud Ubuntu v.12.04 LTS tarkvara.
Mis on Ipkungfu
Tegemist on iptables[1] baasil loodud, kuid lihtsustatud Linuxi tulemüüriga mis hõlbustab võrguliikluse administreerimist. Rakendus töötab iptables ja sysctl baasil. Võib öelda, et tegemist on iptables liidesega mis on omakorda kerneli tulemüürimooduli Netfilter'i kasutajaliides. Tänu lihtsale menüüle sobib rakendus nii algajale kui eksperdile. Toote trumpideks peetakse: [2]
- Turvalisust
- Lihtsat hallatavust
- Jõudlust
Tänu Linuxi kerneli võimekusele leiab tarkvara laialdast rakendust ning toetab [3]
- Võrguühenduse jagamist
- Virtualhoste
- IP suunamist
- IP maskimist
- Logide jälgmist ning kontrollimist
Eelised: [4]
- Võimalik kiiresti paigaldada ning koheselt kasutama hakata
- Seadistamine lihtne ning vähe aega nõudev
- Ei vaja töötavat teenust ega erilisi teadmisi
Paigaldamine
Tulemüür töötab iptables ja sysctl baasil. Võib öelda, et tegemist on iptables liidesega mis on kerneli tulemüürimooduli Netfilter'i kasutajaliides. Konfiguratsiooni failid asuvad kaustas /etc/ipkungfu (lisa conf fail?) mida on võimalik vastavalt soovile muuta.[5]
- Enne installimist uuenda olemasolevaid pakette [6]
sudo apt-get update
- Installi tarkvara
sudo apt-get install ipkungfu
- ipkungfu käivitamine
sudo ipkungfu
- ipkungfu rakenduse peatamine
ipkungfu -d
Seadistamine
Konfiguratsiooni failid asuvad kaustas /etc/ipkungfu mida on võimalik vastavalt soovile muuta.[7]
- Ava fail /etc/ipkungfu/ipkungfu.conf [8]
nano /etc/ipkungfu/ipkungfu.conf
- Muudan faili vastavalt soovile. Testis tegin järgmised muudatused failis:[9]
# Set the path to ipkungfu's runtime error log. # Default: /var/log/ipkungfu.log IPKUNGFU_LOG=/var/log/ipconfig.log
- Määran IP vahemiku
# IP Range of your internal network. Use "127.0.0.1" # for a standalone machine. Default is a reasonable # guess. Separate multiple ranges with spaces. LOCAL_NET="192.168.0.0/255.255.0.0"
- Eemaldan kommentaari
# Set this to 0 for a standalone machine, or 1 for # a gateway device to share an Internet connection. # Default is 1. GATEWAY=1
- Määran keelatud pordid
# Temporarily block future connection attempts from an # IP that hits these ports (If module is present) # Hits to these ports will be logged as "BADGUY" hits # regardless of log.conf settings. FORBIDDEN_PORTS="135 137 139"
- Keelan PING paketid:
# Drop all ping packets? # Set to 1 for yes, 0 for no. Default is no. BLOCK_PINGS=1
- Keelan ebaturvalised paketid:
# What to do with 'probably malicious' packets #SUSPECT="REJECT" SUSPECT="DROP"
- Keelan vale liikluse:
# What to do with obviously invalid traffic # This is also the action for FORBIDDEN_PORTS KNOWN_BAD="REJECT"
- Keelan portide skaneeringu:
# What to do with port scans #PORT_SCAN="REJECT" PORT_SCAN="DROP"
- Tulemüüri automaatseks käivitamiseks ava järgnev fail ning muuda seadistust: [10]
nano /etc/default/ipkungfu
#IPKFSTART=0
IPKFSTART=1
Parameetrid
Võimalused:[11]
-c (or --check)
Check whether ipkungfu is loaded, and report any command
line options it may have been loaded with.
-t (or --test)
Runs a configuration test, and displays the results. Note
that this does not test or display all configuration
options. This gives you an opportunity to verify that
major configuration options are correct before putting them
into action.
-l (or --list)
Displays the iptable rule set.
-d (or --disable)
Disables the firewall. It is important to know exactly
what this option does. All traffic is allowed in and out,
and in the case of a gateway, all NATed traffic is
forwarded (the option retains your connection sharing
options). Custom rules are not implemented, and
deny_hosts.conf is ignored.
-f (or --flush)
Disables the firewall COMPLETELY. All rules are flushed,
all chains are removed. Any port forwarding or internet
connection sharing will cease to work.
-h (or --help)
Displays brief usage information and exits.
-v (or --version)
Displays version information and exits.
--quiet Runs ipkungfu with no standard output
--panic Drops ALL traffic in all directions on all network
interfaces. You should probably never use this option.
The --panic option is available for the highly unusual
situation where you know that an attack is underway but you
know of no other way to stop it.
--failsafe If ipkungfu fails, --failsafe will cause all firewall
policies to revert to ACCEPT. This is useful when working
with ipkungfu remotely, to prevent loss of remote access
due to firewall failure.
--no-caching
Disables rules caching feature.
- Konfiguratsioonifailide asukohad: [12]
- /etc/ipkungfu/ipkungfu.conf
- /etc/ipkungfu/advanced.conf
- /etc/ipkungfu/accept_hosts.conf
- /etc/ipkungfu/deny_hosts.conf
- /etc/ipkungfu/custom.conf
- /etc/ipkungfu/log.conf
- /etc/ipkungfu/redirect.conf
- /etc/ipkungfu/services.conf
- /usr/sbin/ipkungfu
- ReadMe ja FAQ dokumendid leiab kaustast: [13]
- /usr/share/doc/ipkungfu
- /usr/share/doc/ipkungfu/AUTHORS
- /usr/share/doc/ipkungfu/README
- /usr/share/doc/ipkungfu/FAQ
- /usr/share/doc/ipkungfu/ChangeLog
- /usr/share/doc/ipkungfu/COPYING
- Lisainfo [14]
There are several configuration files, each one corresponding to a specific function or set of functions. Advanced users or those with more complex networks will want to edit most or all of these files. They are located in /etc/ipkungfu/ and are:
accept_hosts.conf : IP addresses of hosts or nets to always ACCEPT and optionally the ports they are allowed to access
advanced.conf : Configuration settings for advanced users.
custom.conf : Here you will find sample rules several sample rules already predefined. This is where you would add any custom rules you want applied to your firewall. This file is parsed first, before any other rules are added by ipkungfu, to ensure that none of ipkungfu's rules override the rules in this file.
deny_hosts.conf : You can list IP addresses/subnets:ports:protocols you wish to block completely. This file is parsed before accept_hosts.conf and takes precedence over it.
ipkungfu.conf : This is the main configuration file. Edit this file, if nothing else. For most people, this is the only file that needs to be edited to set up a decent firewall, with or without Internet connection sharing. WARNING: ALLOW_TCP_IN and ALLOW_UDP_IN are now deprecated and mantained only for backward compatability. Now use services.conf.
log.conf : This file specifies what the firewall will log and the rate at which it is logged. By default, nearly all dropped packets are logged. To turn logging off on a particular item, change the 1 (log) to a 0 (don't log). The default location of the log on most systems is /var/log/syslog. Consult your syslogd configuration to find out where kernel logs are stored.
redirect.conf : Use this file to specify where certain traffic should be routed on the SAME machine. If you want to redirect ports that come in on one port, and should go to another, set them up here. There is a single entry here that is commented out by default- tcp:443:10000 which redirects incoming https traffic on port 443 to webmin on port 10000. Please see the file for more information.
vhosts.conf : If you have virtual hosts, (servers on machines behind your gateway), define the routing rules here. This file makes it possible to have servers behind the firewall, with private IP addresses, accessible from the Internet.
pre.conf : This is parsed and executed as a bash script prior to running ipkungfu.
post.conf : This is parsed and executed as a bash script after ipkungfu has completed execution.
services.conf : Here you keep all of your rules previously defined in ipkungfu.conf as ALLOW_TCP_IN and ALLOW_UDP_IN, plus more. Edit the file, it's self explanatory.
Most people, especially those with very simple configurations, will only need to edit /etc/ipkungfu/ipkungfu.conf if anything at all. As of 0.5.1 ipkungfu does a lot of detecting and guessing for the main configuration parameters unless you specify their values in ipkungfu.conf. This should work for most people. To go over the list of variables as ipkungfu knows them, run ipkungfu --show-vars. If anything looks wrong, edit the appropriate configuration file accordingly.
A "#" is a comment. When a line begins with #, the whole line is ignored. If you want enable an option in a configuration file that is commented out, simply remove the leading #. If you wish to remove an option, place a # in front of that line.
Note that anytime you edit a configuration file, you MUST rerun the ipkungfu as outlined below in order for changes to take effect. ipkungfu
Most problems can be resolved by checking your settings in your configuration files. Many users overlook certain settings, so you may want to double-check them to be sure. Remember to run ipkungfu again (/usr/local/sbin/ipkungfu) after making any changes to the configuration files (located in /etc/ipkungfu/). Please see the FAQ for more troubleshooting issues and resolutions.
Testimine
- Ühenduste testimiseks kasutasin ShieldUP-i[15]
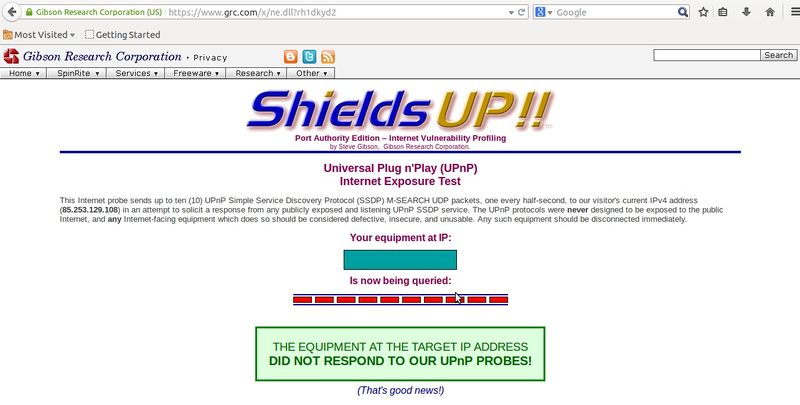
Kokkuvõte
Ipkungfu on linuxi tulemüür mille konfigureerimine käib tabelite baasil, mis sisaldavad endas pakettide filtreerimiseks ning suunamiseks vajalike reegleid. Seadistamine võttis vähe aega ning oli arusaadav.
Kasutatud kirjandus
- http://manpages.ubuntu.com/manpages/trusty/man8/ipkungfu.8.html
- http://teqnix.blogspot.com/2006/06/ipkungfu-kicks-firestarter-out-of-my.html
- http://www.adercon.com/ac/node/93
- http://www.linuxkungfu.org/
- http://manpages.ubuntu.com/manpages/trusty/man8/iptables.8.html
- http://www.zarzax.com/blog/2009/3/4/ipkungfu-easy-iptables-based-server-firewall.html
Koostas
Heiko Niidas AK-31, 2015